Silent Push Uncovers Chinese Fake Marketplace e-Commerce Phishing Campaign Using Thousands of Websites to Spoof Popular Retail Brands

Key Findings
- Silent Push Threat Analysts followed a tip from Mexican journalist Ignacio Gómez Villaseñor about a threat actor targeting “Hot Sale 2025,” an annual sales event similar to “Black Friday” in the U.S.
- Our team pivoted from that Mexico-centric campaign into thousands of websites that broadly targeted a more global audience with abundant waves of fake marketplace scams.
- We identified a private technical fingerprint associated with this infrastructure, which contains Chinese words and characters to strongly indicate that the developers of this network are from China.
- Our analysts observed this threat actor group building multiple phishing websites with pages spoofing well-known retailers, including Apple, Harbor Freight Tools, Michael Kors, REI, Wayfair, and Wrangler Jeans.
- The threat actor has also been caught abusing online payment services, including MasterCard, PayPal, and Visa, as well as payment security techniques such as Google Pay, across the campaign’s network of scam websites.
Executive Summary
From a lead gained through a recent X/Twitter post by Mexican journalist Ignacio Gómez Villaseñor, Silent Push Threat Analysts have been investigating a new phishing e-commerce website scam campaign.
The original campaign observed was targeting Spanish-language visitors shopping for the “Hot Sale 2025.” The research by Gómez Villaseñor focused on specific domains found on one IP address targeting Spanish-language audiences; however, it was but one slice of a much larger campaign.
As we began our deeper research, our team soon uncovered a much broader fake marketplace scheme targeting English and Spanish language audiences in many other countries outside of Mexico. After we found a private technical fingerprint associated with the threat actor’s infrastructure, which contained Chinese words and characters, we have high confidence that the developers of this network are from China.
Our team has uncovered thousands of domains spoofing various payment and retail brands in connection to this campaign including (but not limited to): PayPal, Apple, Wayfair, Lane Bryant, Brooks Brothers, Taylor Made, Hermes, REI, Duluth Trading, Omaha Steaks, Michael Kors, and many, many more peddling everything from luxury watches to garage doors.
Table of Contents
- Key Findings
- Executive Summary
- Sign Up for a Free Silent Push Community Edition Account
- Background
- Google Pay Widget Integrated Into Sites to Take Real Payments
- Brands Mixed Between Domains and Sites
- Brands and Organizations Targeted
- Continuing to Track the Mexican Hot Sale / Chinese Fake Marketplace Phishing Campaign
- Mitigation
- Sample Indicators Of Future Attack TM
Sign Up for a Free Silent Push Community Edition Account
Register now for our free Community Edition to use all the tools and queries highlighted in this blog.
Background
Silent Push Threat Analysts have investigated a seemingly endless series of online retail campaigns involving threat actors employing various techniques to scam potential buyers out of their money.
From our blogs on Aggressive Inventory Zombies: A Retail & Crypto Phishing Network and Malvertising Campaigns Abusing Google Search Ads to the most recent GhostVendors Fake Marketplace Campaign that shares our findings on the abuse of a Facebook advertising policy loophole, we share how our technology uncovers thousands of malicious domains spoofing major brands and provides proactive mitigation solutions for our clients.
This latest scam campaign targets English and Spanish language shoppers with fake marketplace ads, which we began investigating following a tip we discovered on journalist Ignacio Gómez Villaseñor’s May 26, 2025, X/Twitter post.
The campaign’s timing took advantage of the recent “Hot Sale 2025,” an annual shopping event sponsored by Asociación Mexicana de Ventas Online (AMVO) (amvo[.]org[.]mx/), which ran from May 26 to June 3, 2025.
Websites in this network don’t appear to actually process transactions or purchases, but instead steal credit card information entered on the (fake) payment page. The write-up from Gómez Villaseñor on Publimetro included this important detail from their testing (translated into English):
“In tests carried out by Publimetro México, by entering false bank card data into these portals, the system reacts as if you were actually processing a payment. A “reserved cart ” timer and platform logos are displayed as Visa, MasterCard, PayPal, Oxxo, and SPEI. This simulation is done to gain user trust and steal your information without raising immediate suspicion.”
Our threat analysts observed that the threat actor had created multiple phishing websites with pages spoofing a wide array of retailers, many of which are well-known brands. The phishing pages feature products that appear to have been scraped from other sites and abuse online payment security techniques to orchestrate scam websites.
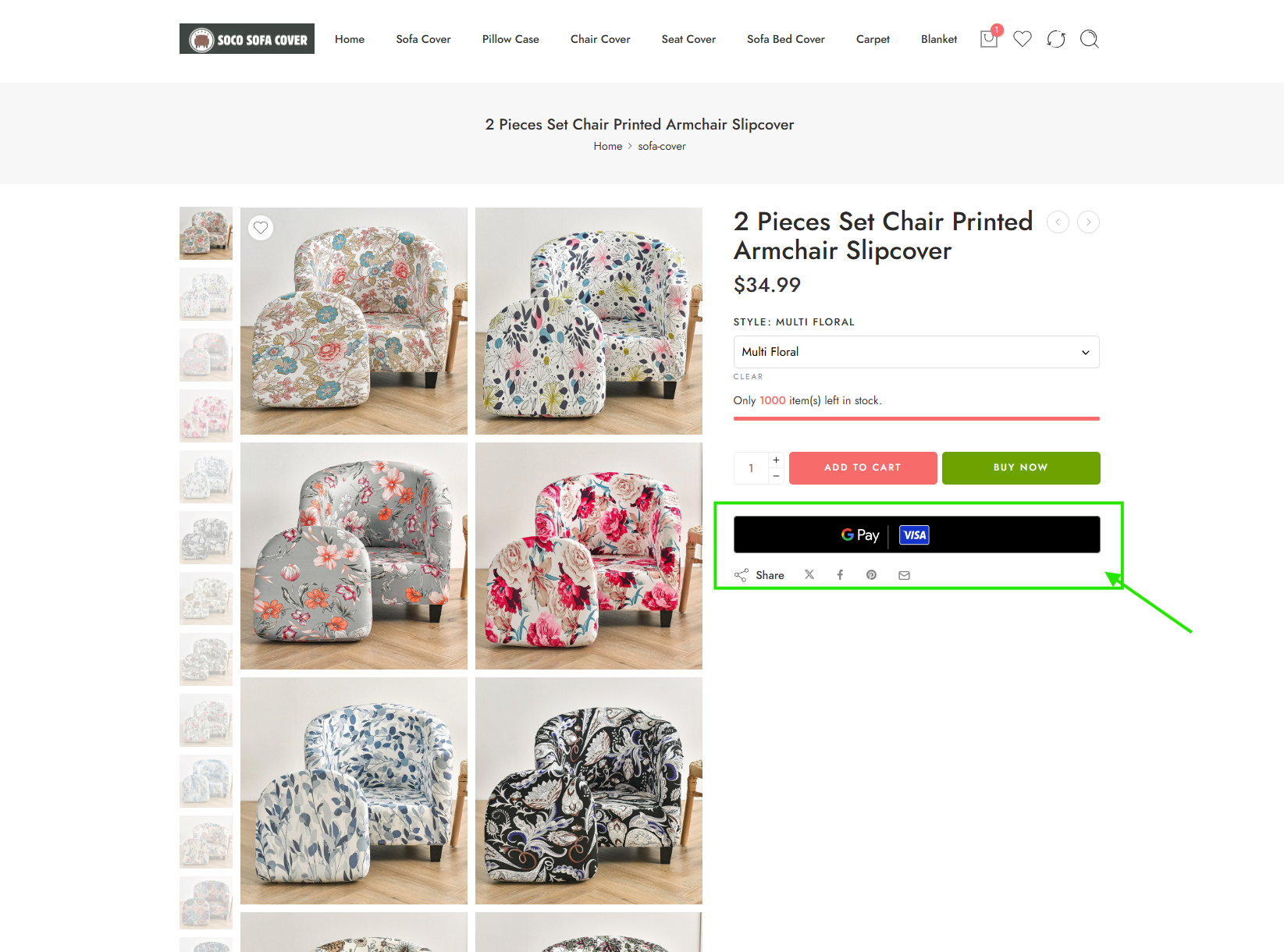
Additionally, as our team has continued to investigate this online scam, we have found multiple suspicious sites using Google Pay, which suggests that this threat actor group is also stealing payments (as Google Pay uses virtual credit card numbers) and then not actually delivering any of the supposedly “purchased” goods.
Google Pay Widget Integrated Into Sites to Take Real Payments
Some of the websites in this network, such as rizzingupcart[.]com, include genuine Google Pay purchase widgets.
These purchase widgets typically offer an extra layer of security protection to online shoppers, as Google Pay has a key security feature that uses virtual card numbers, which are randomly generated, instead of sharing buyers’ actual credit card details. Since credit card data is not accessible to merchants, threat actors behind fraudulent sites cannot typically steal it.
Despite the security of raw credit card information not being shared via this method, a threat actor can often circumvent the protection of virtual card numbers. Even when accepting payments made via this process, a threat actor can still successfully orchestrate its online scam by simply failing to deliver the ordered products after payment.
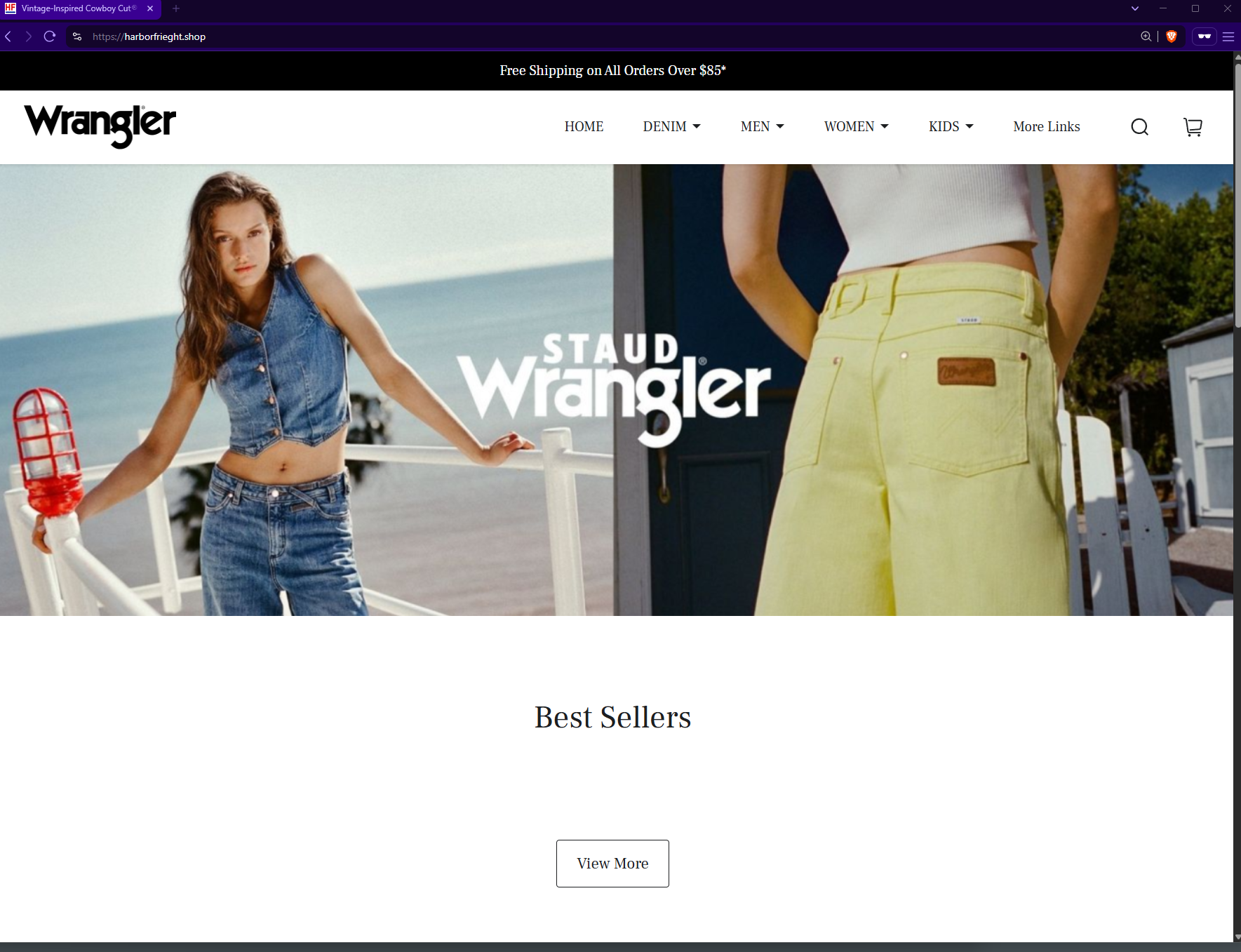
Brands Mixed Between Domains and Sites
Our team found many sloppy deployments on sites such as “harborfrieght[.]shop” (note the misspelling of “freight”), which in theory would be promoting Harbor Freight Tools, yet the website instead featured a clone of the Wrangler jeans site:
Brands and Organizations Targeted
The fake marketplace campaign has targeted numerous well-known brands. We are listing a few of the more popular organizations that have been targeted. We are also including screenshots when we were able to catch the phony sites still being viewable online:
- Harbor Freight Tools
- Wrangler Jeans
- Guitar Center
- Lane Bryant
- Nordstrom
- Omaha Steaks
- REI
- Thousands more…
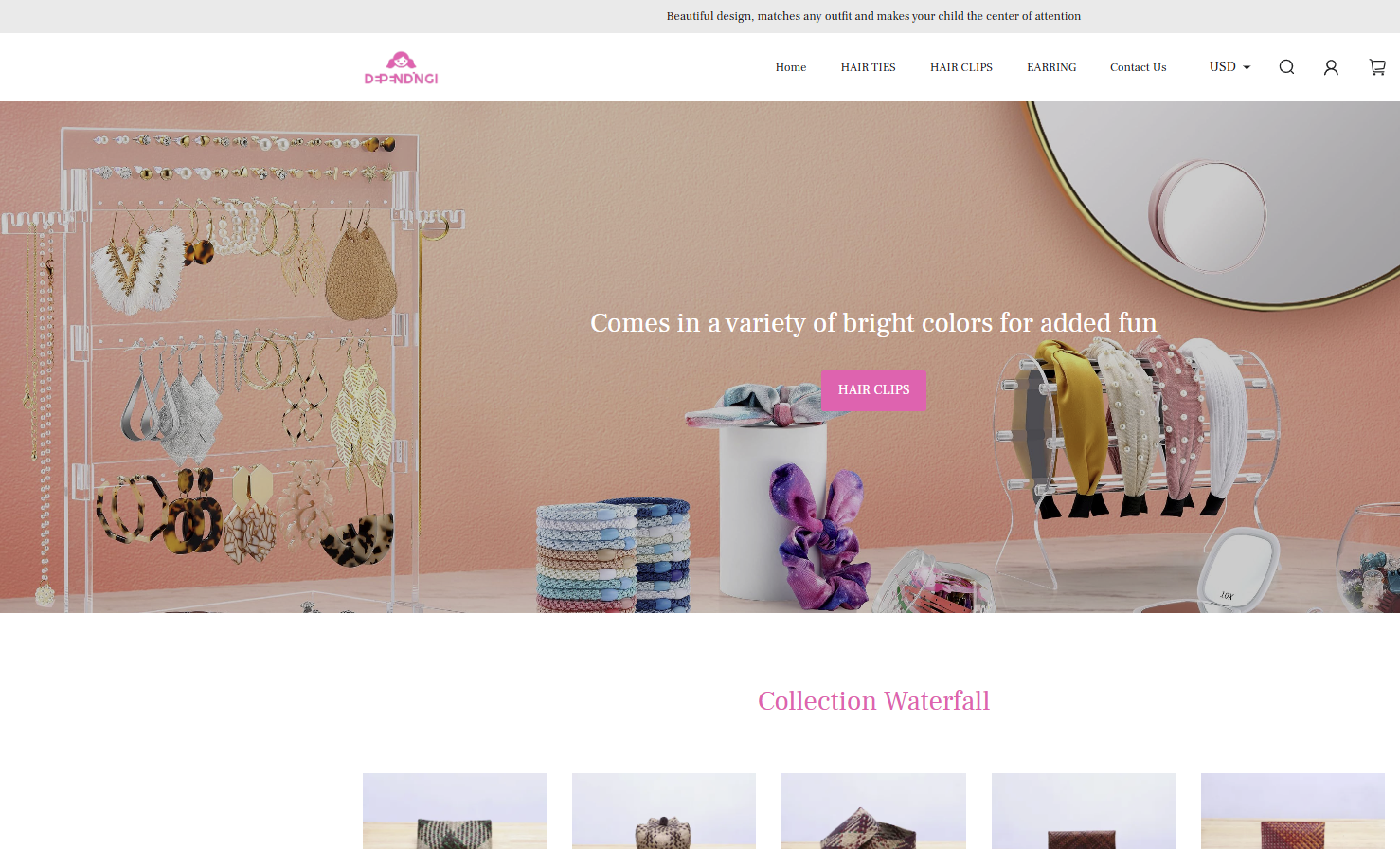
The site “guitarcentersale[.]com” spoofing retailer Guitar Center appears to offer children’s accessories with no sign of any musical instruments for sale.
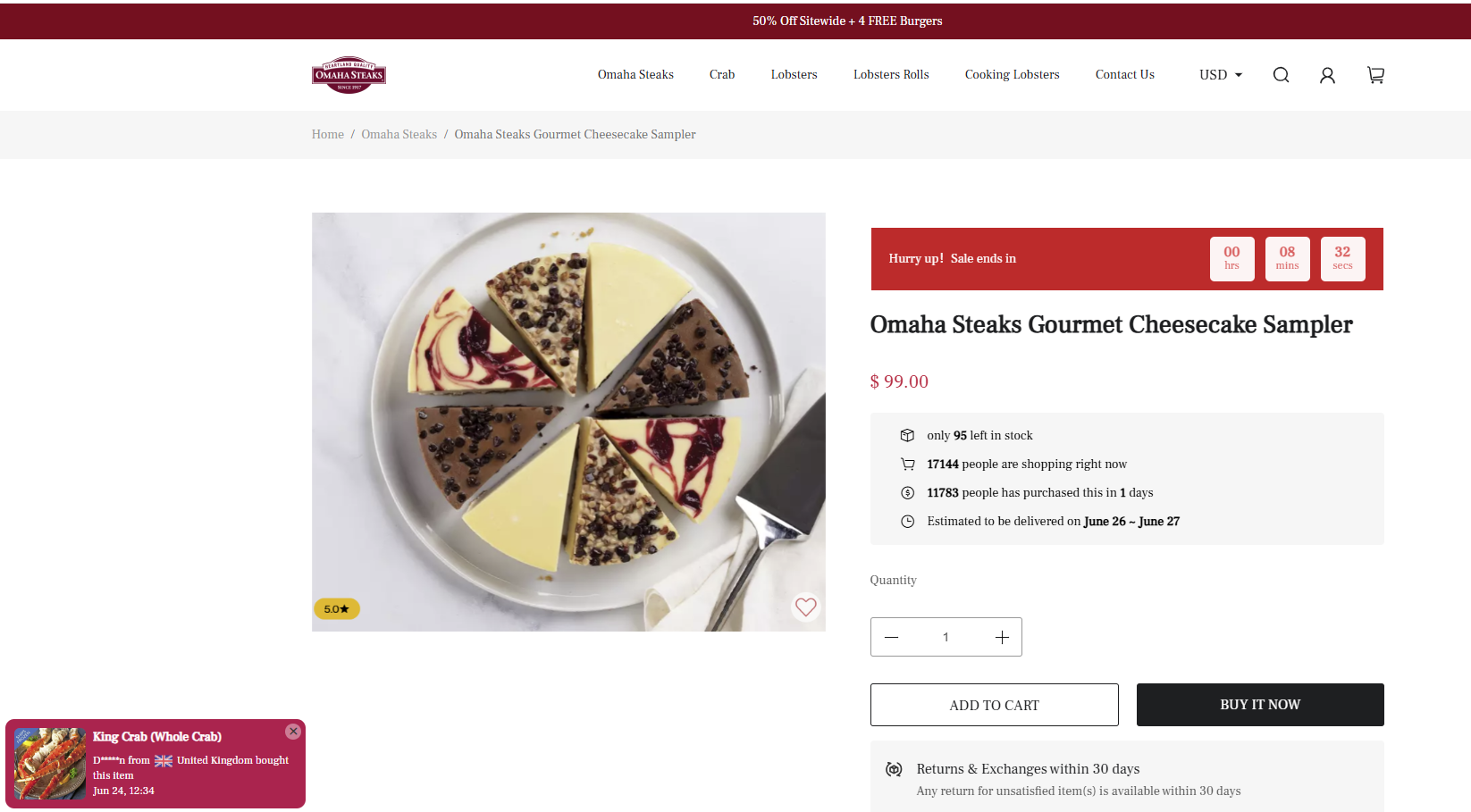
The site “omahasteaksbox[.]com tried to pattern its design on the actual Omaha Steaks’ website in its spoofing attempt by partially copying portions of legitimate content. The phony site appears somewhat convincing at first glance, but on closer inspection, it is a shoddy attempt at emulating the popular brand.
Another fake marketplace site, “nordstromltems[.]com” (note the URL has a lower-case “l” instead of an “i” for the word “items”), attempted to spoof the brand of retailer Nordstrom. This fake site only displayed casual kids’ accessories, rather than the breadth of high-end clothing, accessories, shoes, and cosmetics typically associated with the Nordstrom brand, which caters to women, men, and children.
Our team also noted the phony site builder merely cloned the entire site for “guitarcentersale[.]com” and used it for the “nordstromltems[.]com” site, which further confirmed it was the work of the same threat actor.
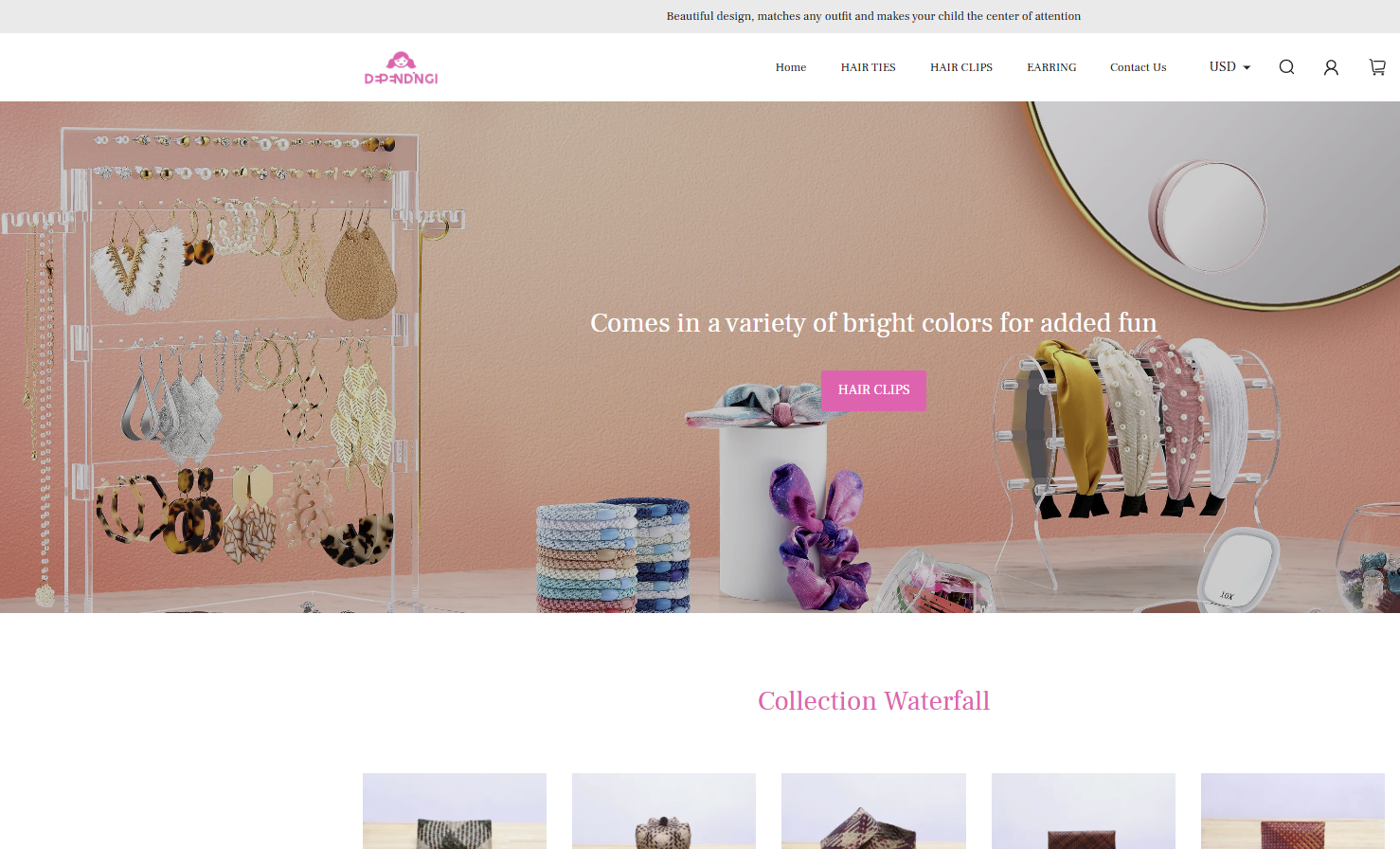
Another site, spoofing the well-known Brooks Brothers brand, scraped parts of the legitimate website but then listed selections of clothing at impossibly low prices—especially for the BB brand.
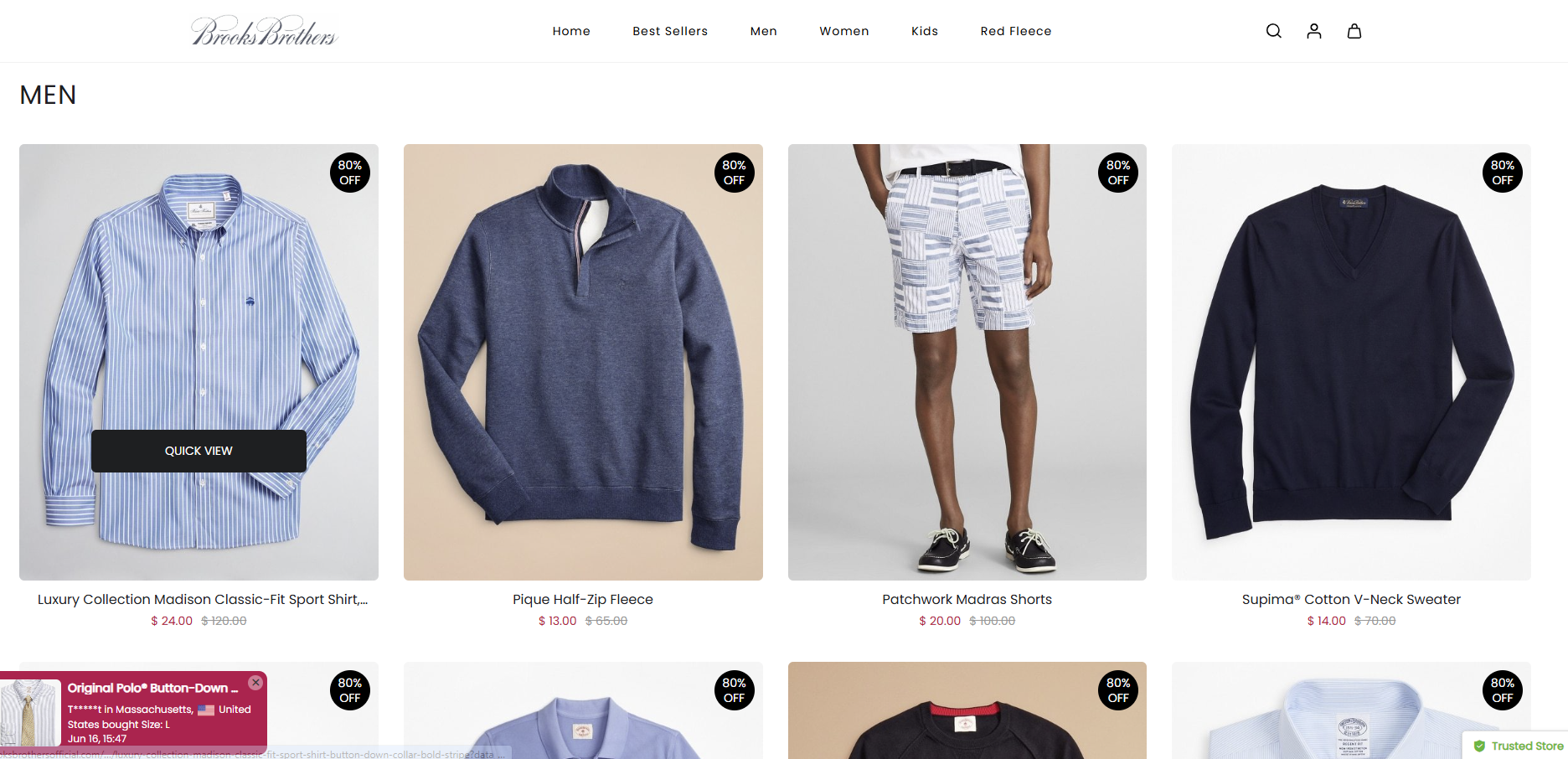
Our team found numerous additional sites abusing clothing brands, including one site “josbankofficial[.]com” that attempted to spoof the historic menswear merchant Jos. A. Bank.

Our team also found a website attempting to spoof the premium clothing brand Tommy Hilfiger. Unlike the typical designer clothing found on the legitimate Tommy Hilfiger site, the spoof site, “tommyilfigershop[.]com” (note the missing “h” for the Hilfiger name and multiple misspellings on the home page) displays a model promoting women’s casual wear advertised by the brand “Autumvwindsss.”
During the course of our research, we determined that many of the fake marketplace sites had been blocked by their hosts once they were discovered (a given site’s fake content was frequently replaced with red warning messages instructing users not to continue browsing on some suspicious domains). However, despite many sites being taken down by both hosts and defenders, thousands remain active as of June 2025. In the face of these types of scaled-up, persistent threats, traditional methods appear unable to hold back the tide.
This is why Silent Push focuses on the value created by our Indicators Of Future AttackTM (IOFATM) feeds—so our customers can act on preemptive threat intelligence, rather than traditional, reactive methods.
Continuing to Track the Mexican Hot Sale / Chinese Fake Marketplace Phishing Campaign
Silent Push Threat Analysts will continue to track this Fake Marketplace Chinese Phishing Campaign and update our findings with future posts and reports as we uncover new developments.
If you or your organization has any information on this threat actor, we would love to hear from you.
Mitigation
Silent Push believes that all websites associated with this campaign represent some level of risk. This fake marketplace campaign primarily targets consumers with a phishing threat that exploits major brands, well-known organizations, and the fame of some political figures.
Our analysts have developed a series of Silent Push IOFATM feeds in response to these types of phishing efforts to best protect our customers from global threats.
Silent Push IOFATM Feeds are available as part of an Enterprise subscription. Enterprise users can ingest IOFATM Feed data into their security stack to inform their detection protocols or use it to pivot across attacker infrastructure using the Silent Push Console and Feed Analytics screen.
Sample Indicators Of Future AttackTM
Silent Push is sharing a small sample of our Indicators Of Future AttackTM (IOFATM) list, which we associate with the Mexican Hot Sale/Chinese fake marketplace phishing campaign to support ongoing efforts within the community. Our enterprise users have access to an IOFATM feed currently containing significantly more indicators from this campaign.
- cotswoldoutdoor-euro[.]shop
- harborfrieght[.]shop
- portal[.]oemsaas[.]shop
- rizzingupcart[.]com
- brooksbrothersofficial[.]com
- josbankofficial[.]com
- nordstromltems[.]com
- guitarcentersale[.]com
- tommyilfigershop[.]com
- tumioutlets[.]com

