Silent Push IOFA™ Feed Detects Aeza Group Infrastructure Shift Following OFAC Sanctions

On July 1, 2025, the U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) designated Aeza Group, two affiliated companies, and four individuals for providing bulletproof hosting services that enabled global cybercriminal activity — including ransomware operations, data theft, and darknet drug trafficking.
Bulletproof hosting (BPH) refers to resilient server infrastructure used by threat actors to operate outside the reach of law enforcement. In response to the sanctions, the U.S. government froze Aeza Group’s U.S.-based assets and prohibited U.S. persons from engaging in transactions with them.
Silent Push Detects ASN Migration in Real Time
Silent Push Threat Analysts identified Aeza Group (AS216246 and AS210644) as a bulletproof hosting provider in early 2025. On July 20, 2025, Silent Push’s IOFA (Indicators of Future Attack)™ feed automatically detected a significant infrastructure shift: IP ranges from Aeza’s AS210644 began migrating to AS211522, a new autonomous system operated by Hypercore LTD.
This shift suggests an attempt to evade sanctions enforcement and continue malicious operations under new infrastructure.
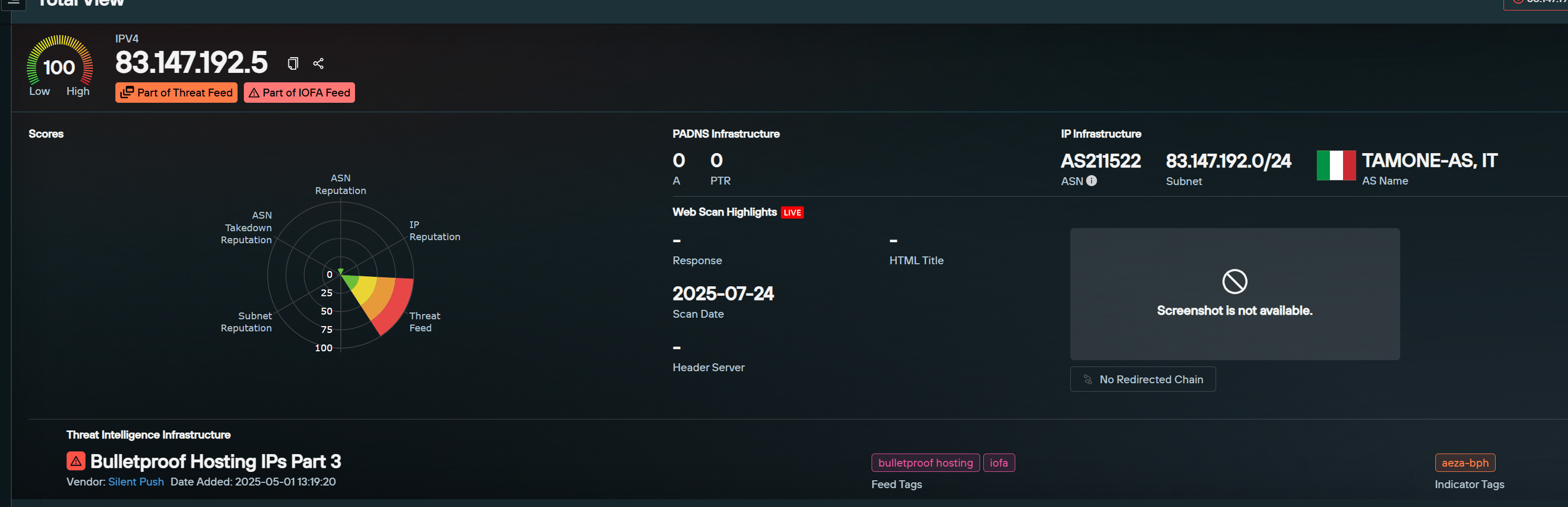
One such example is IP address 83.147.192[.]5, which was previously associated with AS210644. On July 20, this IP was automatically reclassified in the Bulletproof Hosting IOFA™ feed to reflect its new association with AS211522.
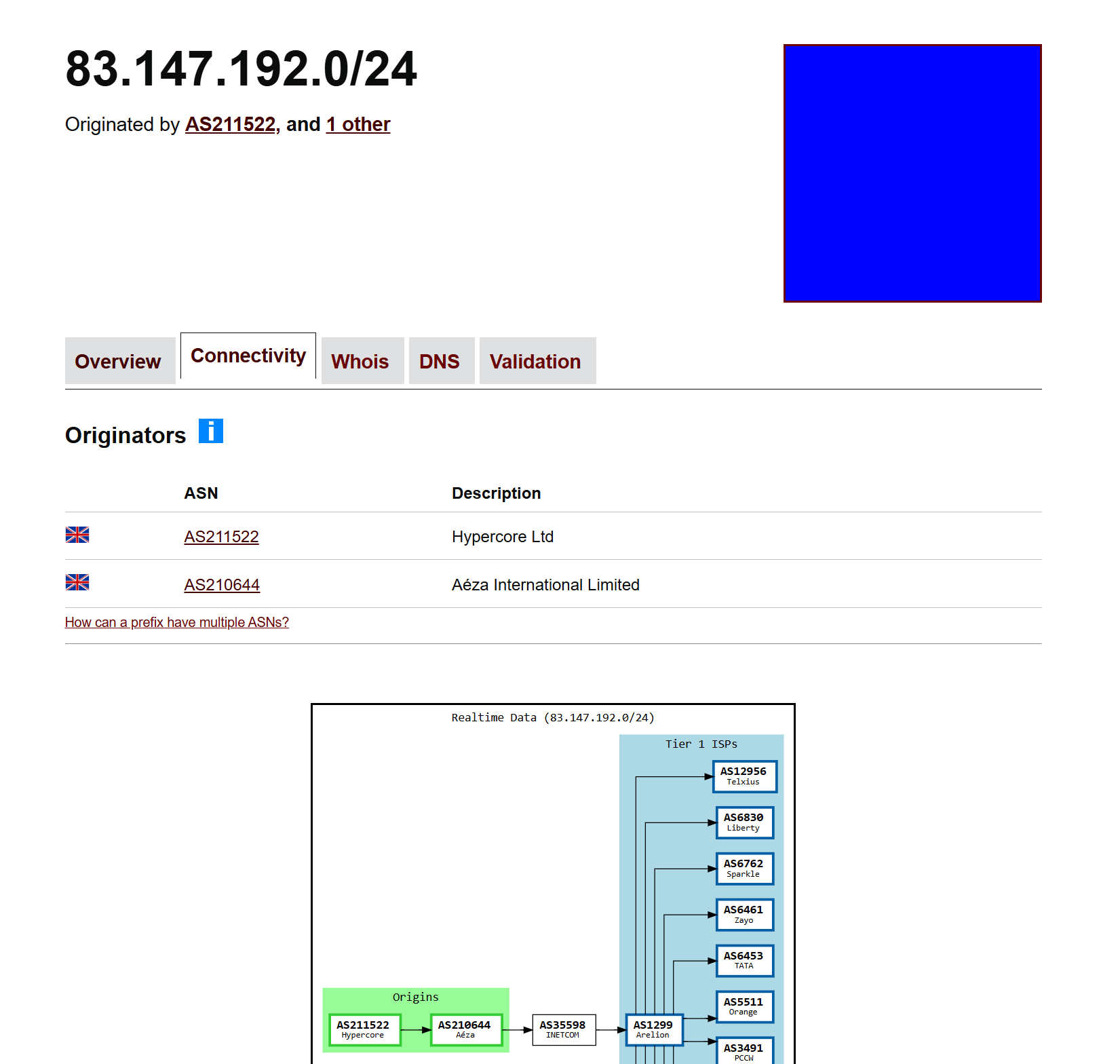
BGP data from bgp.tools confirms that the 83.147.192.0/24 subnet has been announced by both ASNs, supporting the attribution.
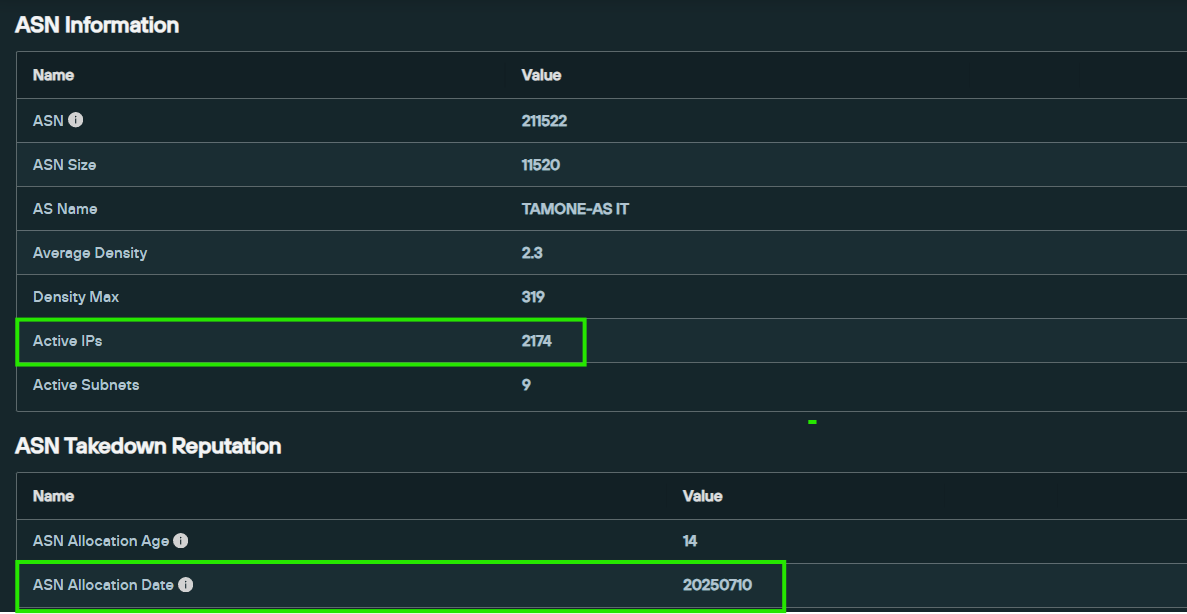
According to Silent Push data, ASN 211522 was allocated on July 10, 2025, as confirmed by a search within the Total View platform. The data also shows that the ASN already contains over 2,100 IP addresses, indicating an unusually rapid ramp-up for a newly allocated ASN — a pattern not typically observed.
Silent Push Threat Analysts will continue to investigate ASN 211522 and welcome any leads related to suspicious bulletproof hosting infrastructure or additional context surrounding the Aeza Group IP migration.
Tracking Infrastructure Before It’s Weaponized
Through continuous infrastructure monitoring, Silent Push is able to detect and track emerging BPH providers before they’re widely used in active campaigns. The migration to AS211522 is likely either a rebrand by Aeza or a handoff to a closely aligned cybercriminal entity.
Silent Push IOFA™ feeds are designed to identify attacker infrastructure — before it’s operationalized. From bulletproof hosting to phishing domains, malware C2s, and more, Silent Push provides security teams with early, actionable visibility into the infrastructure behind tomorrow’s threats.
Missed our recent webinar on Bulletproof Hosting?
It’s now available on-demand. Access it here.
Want to explore Silent Push IOFA™ feeds?

