Security analysts face the constant challenge of gaining immediate and accurate context on IP addresses that pop up during an investigation, to minimize risk and prevent loss.
We’ve solved this problem by introducing an IP tagging system that categorizes every scanned IPv4 address as a residential VPN, proxy, or sinkhole, with detailed sub-categories available for each.
Tagging data is passed onto Community and Enterprise users via the Total View screen, within threat feed searches, and made available as a filterable bulk download for Enterprise users only.
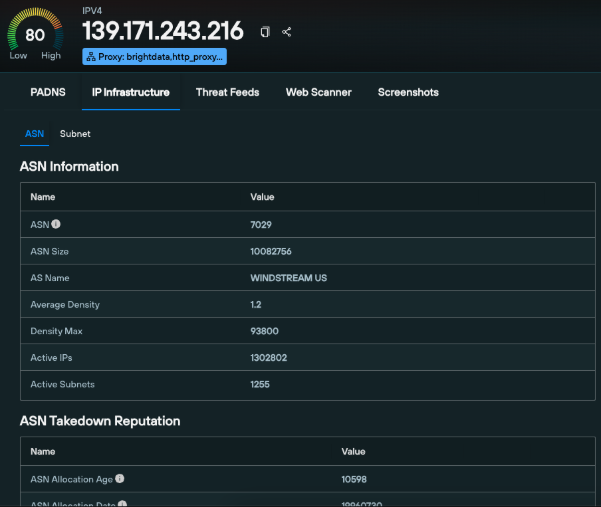
What Is IP tagging in Silent Push?
We flag IPs across our global IPv4 datasets as belonging to one of the below categories:
- Residential VPN – including attribution to the commercial provider
- Proxy services – with subcategories for residential, open, HTTP, SOCKS4/5, or requiring authentication
- Sinkhole – typically operated by security researchers or defenders attempting to neutralize malicious infrastructure
How can I access IP tagging data?
IP tagging is designed to work wherever analysts work. Users can access the data in the following locations:
Total View
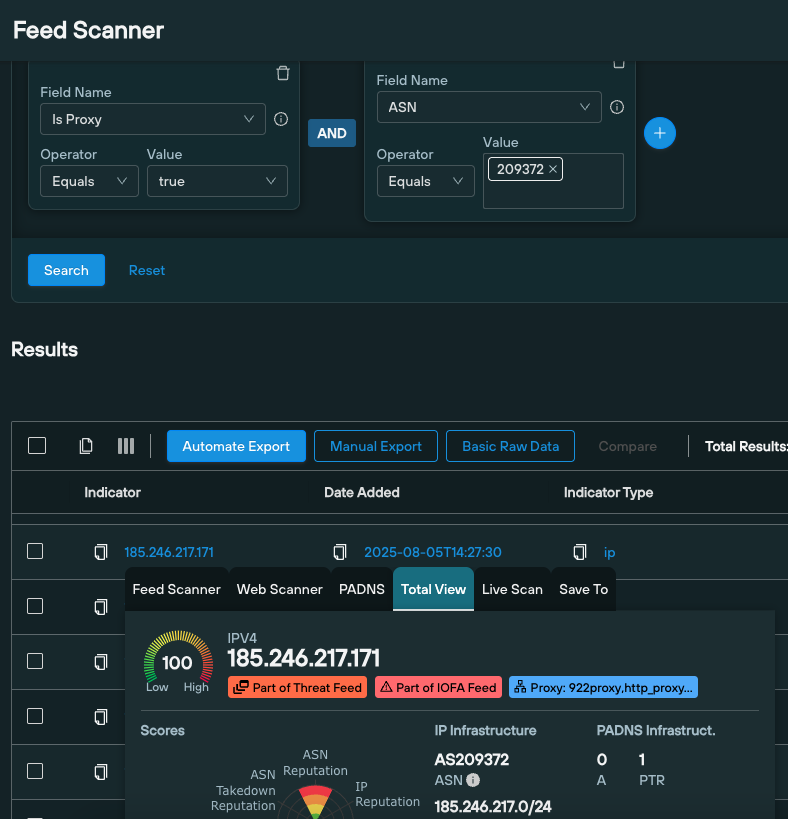
Total View is the platform’s central interface, and a CTI landing page for gaining instant insight into unknown indicators.
From this screen, users can view tagging information on any IPs they come across alongside:
- Historical DNS records
- Hosting details
- Campaign associations
- Silent Push proprietary enrichment data
- The IP’s presence in any threat feeds.
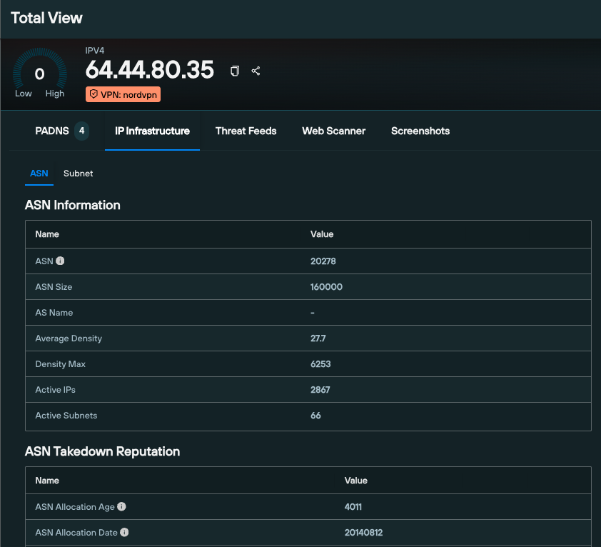
Daily bulk download (‘IP Context’)
Enterprise users have access to an ‘IP Context’ option, under the ‘Data Export’ menu, which acts as a central hub for bulk downloads of all tagged IPs per category, and their ‘last seen’ date.
From here, users can export all our tag data, or drill down into individual VPN providers and proxy services (including free proxies), allowing teams to feed tags into their SIEM/SOAR workflows via the Silent Push API, based on their unique operational requirements.
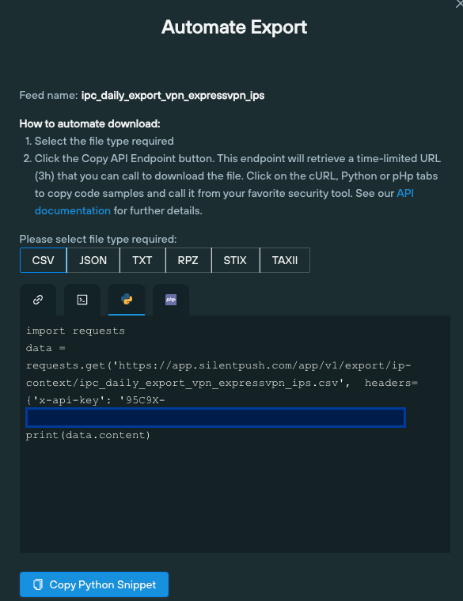
Data is available as an automated export via code snippets, or as a one-click CSV download.
Feed Scanner queries
Our Feed Scanner is a syntax-based search of all the data contained in threat feeds that are visible on a user’s Silent Push account – including any third-party feeds.
For example, the ‘Is Proxy’ field can be used to identify all proxied IPs on AS209372 that appear as malicious.
Why Contextual IP Tagging Data Matters
To evade detection, attackers rely on infrastructure that blends in with legitimate activity. VPNs and residential proxies help threat actors bypass geo-filters, rate limits, and detection logic.
Without context, defenders waste time chasing false positives and missing subtle links between malicious assets.
IP tagging reduces that uncertainty. It adds a functional layer to observed IPs that would otherwise appear generic or ambiguous, giving defenders a quick way to assess risk and relevance.
Enterprise Use Cases for IP Tagging
Credential stuffing and account takeover detection
Automated login attempts often originate from residential proxies, in order to appear as legitimate users. With IP tagging, SOC teams can flag or filter such IPs during authentication events and respond before credentials are compromised.
Infrastructure discovery
During investigations, unknown IPs sometimes emerge without clear ownership. Flagging suspect infrastructure helps identify whether these IPs belong to everyday users, anonymous VPNs, or proxy services – refining triage decisions and improving accuracy.
Threat Actor clustering
Attackers reuse infrastructure across campaigns. By identifying shared VPN or proxy use, teams can correlate threat activity and block related assets earlier in the kill chain.
Incident Response and malware triage
Sinkholes generate alerts that distract from active threats. Identifying sinkholes early on in an investigation helps responders recognize benign IPs, reducing noise and allowing teams to focus on containment and root cause analysis.
Advertising fraud and traffic manipulation
Proxied IPs play a central role in ad fraud, bot traffic, and coordinated inauthentic behavior. Tagging allows security and ad tech teams to identify suspicious sources, monitor patterns and build targeted defenses against fraudulent schemes.
Book a Demo
Contextual IP data helps answer the essential question that every defender asks themselves: what am I looking at?
IP tagging in Silent Push is a critical enabler for teams trying to detect fraud, uncover hidden attacker infrastructure, and slash false positives in noisy environments.
Get in touch with our team today, and let us show you how much more we know about the Internet than any other cybersecurity vendor.