A Fortune 500 media and entertainment company transformed the way it handled security alerts by embedding Silent Push Threat Check into its SIEM workflows.
The result: weeks-earlier visibility into attacker infrastructure, streamlined investigations, and measurable outcomes based on their investment in Silent Push.
The Challenge: Alert Noise Without Context
Security teams rely on SIEMs to centralize and correlate alerts. But once those alerts appear, the real challenge begins: determining which ones represent genuine threats.
For this organization, analysts faced:
- High volumes of alerts on suspicious domains and IPs.
- Limited context to distinguish malicious activity from harmless indicators.
- Alert fatigue and slower triage, with time wasted chasing benign indicators.
They needed a way to automatically escalate indicators that were on the Silent Push IOFATM dataset to SOC Tier 2 and Tier 3 support to reduce mean time to response (MTTR).
The Solution: Silent Push Threat Check
Silent Push Threat Check is a lightweight enrichment solution that validates suspicious domains and IPs against Silent Push’s continuously mapped view of attacker infrastructure.
By embedding Threat Check into existing workflows – including SIEM and SOAR environments – organizations can:
- Deliver weeks-earlier visibility into attacker infrastructure compared to traditional detections.
- Provide measurable lead-time metrics to demonstrate ROI.
- Highlight overlaps with real adversary campaigns, reducing false positives and wasted investigation time.
Implementation
The organization integrated Threat Check directly into their SIEM pipeline:
- Every suspicious domain or IP captured by the SIEM was automatically passed to Threat Check.
- Threat Check determined whether indicators overlapped with attacker-controlled infrastructure already tracked by Silent Push.
- Enriched results flowed back into the SIEM, so analysts saw alerts with added context and validation.
This seamless enrichment step meant analysts could immediately understand which alerts were tied to real adversary campaigns, without changing processes.
The Results: Earlier Detection, Smarter Response
The impact was immediate:
- Silent Push identified infrastructure associated with FIN7, Lazarus, Sapphire Sleet, ClickFix, Amos Infostealer, and other threats months before it appeared in the customer’s SIEM.
- On average, Silent Push provided 104 days of detection lead time, with a median lead time of 117 days.
- In some cases, detection lead time exceeded 200 days – giving the organization a substantial head start for their defense.

This measurable advantage allowed the team to:
- Prioritize critical alerts tied to verified attacker infrastructure.
- Accelerate investigations, cutting time spent on manual research.
- Reduce false positives, freeing analysts to focus on genuine threats.
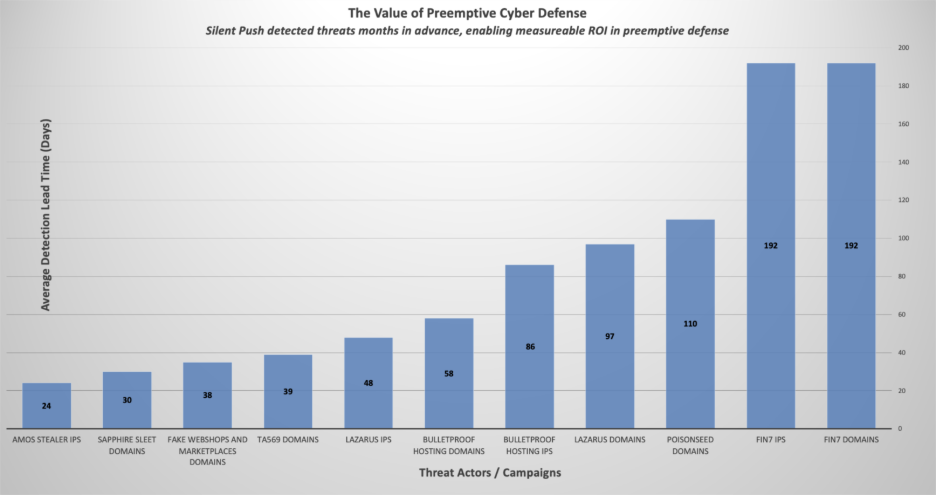
Quantifying ROI
The ability to measure detection lead time turned Threat Check into a tool for proving value to leadership.
By comparing when Silent Push first detected malicious infrastructure against when the same indicators appeared in SIEM alerts, the customer demonstrated that Silent Push consistently delivered weeks of advanced visibility.
This translated to:
- Faster containment opportunities.
- More efficient use of analyst resources.
- Stronger confidence in the SIEM’s alerts, now enriched with external validation.
Accelerating Detection: The Silent Push Advantage
| Indicator | Threat Type | Seen in SIEM | Detected by Silent Push | Detection Lead Time |
| cdnjscloudnetwork[.]co | FIN7 Domain | 2025-05-16 | 2024-07-15 | 305 Days |
| 66.235.175[.]109 | Lazarus IP | 2025-07-05 | 2025-02-13 | 142 Days |
| api.drive-release[.]cloud | Lazarus Domain | 2025-06-19 | 2025-02-13 | 126 Days |
| okta.login-request[.]com | PoisonSeed Domain | 2025-07-24 | 2025-03-14 | 132 Days |
| static.twalls5280[.]com | FakeUpdate Domain | 2025-08-28 | 2025-05-25 | 95 Days |
| hlanstanbak[.]com | KeitaroC2 Domain | 2025-08-29 | 2025-08-13 | 16 Days |
| 82.117.255[.]225 | SecTopRAT IP | 2025-08-29 | 2025-06-18 | 72 Days |
Why Threat Check Works
This success highlights three reasons why Threat Check delivers value across organizations:
- Seamless Integration – A lightweight enrichment step, embedded directly into existing workflows.
- Actionable Outcomes – Clear validation of which indicators map to attacker infrastructure.
- Measurable Advantage – Quantifiable lead-time metrics that demonstrate ROI.
Request A Demo
Silent Push Threat Check is designed to help organizations move from reactive alert-handling to preemptive cyber defense.
Ready to see it in action? Get in touch today for a customized demonstration of how Threat Check can integrate into your workflows and deliver measurable results.


