Advanced Queries For Real Malware Detection in Silent Push

Getting Started
The Silent Push platform is capable of powerful queries for threat hunting and preemptive discovery of malicious infrastructure. Our team uses this platform every day to proactively hunt and discover infrastructure for our customers, enabling blocking and discovery of threats before they are fully operationalized.
Some of our readers know that we also have a free Community Edition, which provides introductory access to the same core capabilities used by our threat analyst team. As a way of giving back, we’re sharing some detection logic for users in our Community Edition, with our more advanced detections remaining exclusive to users of our Enterprise Edition.
So let’s go ahead and show the detections for some of the most prominent malware loaders, infostealers and phishing campaigns for 2025.
Sign Up for a Free Silent Push Community Edition Account
All of the queries shared below are supported in our free Community Edition. We’ve included a short link below if you’d like to sign up and follow along.
Table of contents
Quick Note and Disclaimer
The queries we’re sharing today are intended to be hunting queries and not to be “perfect” detections, so you may encounter a very small number of false positives through these. In saying that, we have verified that a significant number of results for each query are matching on the relevant threat or malware group.
There are also variations of each query that we use internally for additional coverage, so you may need to modify these slightly if you’re aiming for complete coverage of the threats mentioned.
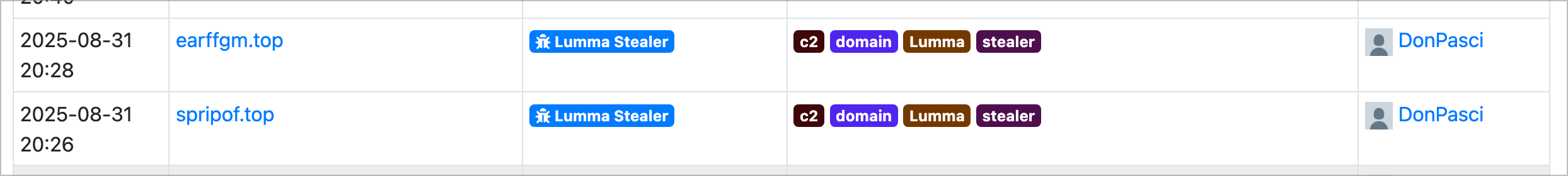
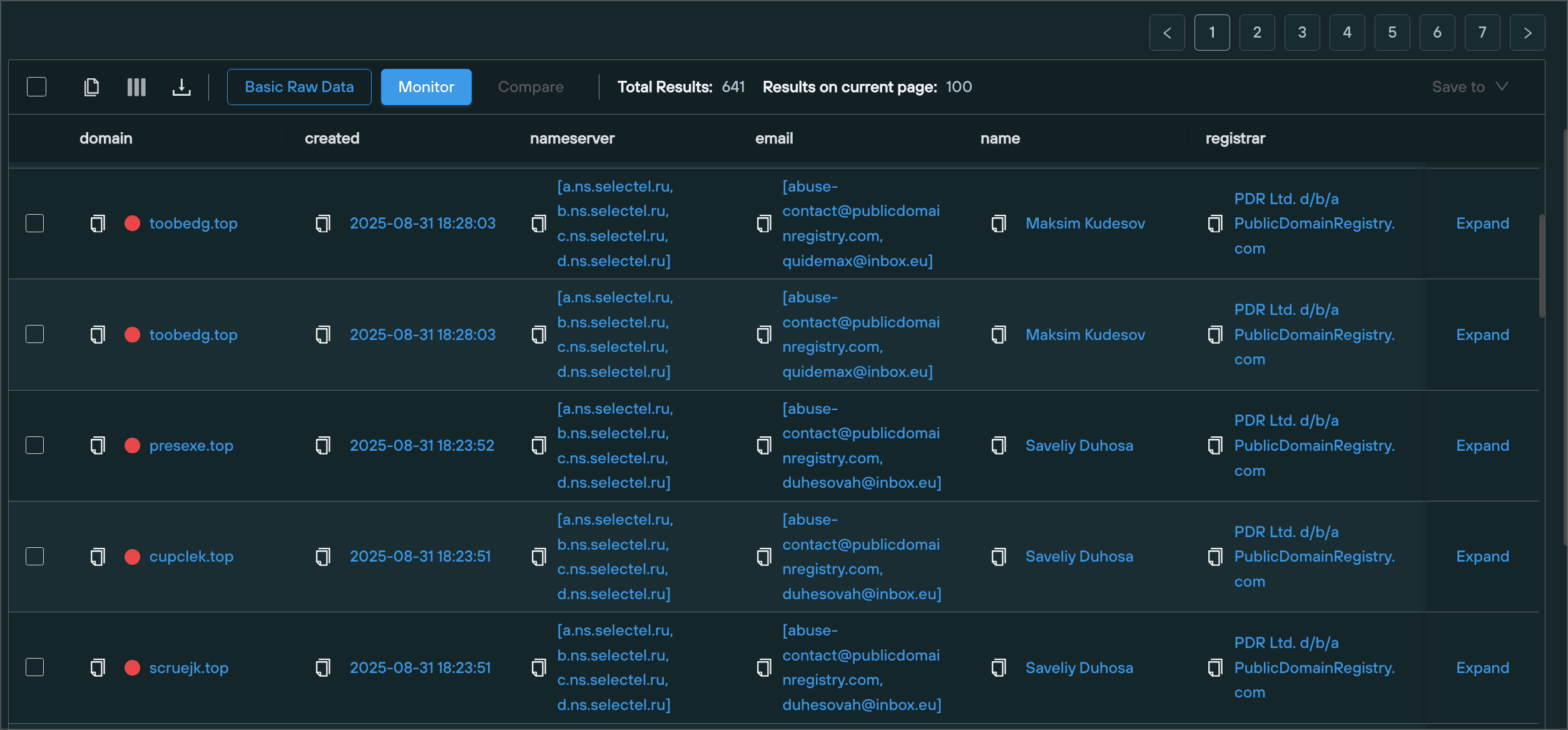
Lumma Stealer – C2 Domains
Lumma Stealer is popular and prolific infostealer that has been around for a while, with the associated domains featuring a repeated yet seemingly overlooked pattern that is present in their infrastructure prior to weaponization. The pattern was first observed around February 2025, and has since been used as the basis of various signatures since then.
There have been some minor variations over this period, especially around the “takedown” of Lumma in May, but the overall logic and concept have remained strong for a significant period of time this year.
The pattern is largely based on a registration pattern used by Lumma, which features aspects of randomization that itself produces a unique pattern we can signature on.
- Use of primarily alphabetical domain names with uncommon TLD’s
- Heavy usage of specific nameservers at a given time, typically cloudflare or selectel.
- Rotating and seemingly randomised email addresses, always on the
@inbox.euemail provider - A
Firstname Lastnamepattern in both the organization and name fields, where the same value is always present in both. - Primarily using the
PDRregistrar
datasource = "whois" AND name ~= "(\'|)[A-Z][a-z]{1,} [A-Z][a-z]{1,}(\'|)" AND organization ~= "(\'|)[A-Z][a-z]{1,} [A-Z][a-z]{1,}(\'|)" AND nameserver = ["*.ns.selectel.ru"] AND email = "*inbox.eu" AND created > "now-30d" AND registrar = "PDR Ltd. d/b/a PublicDomainRegistry.com"
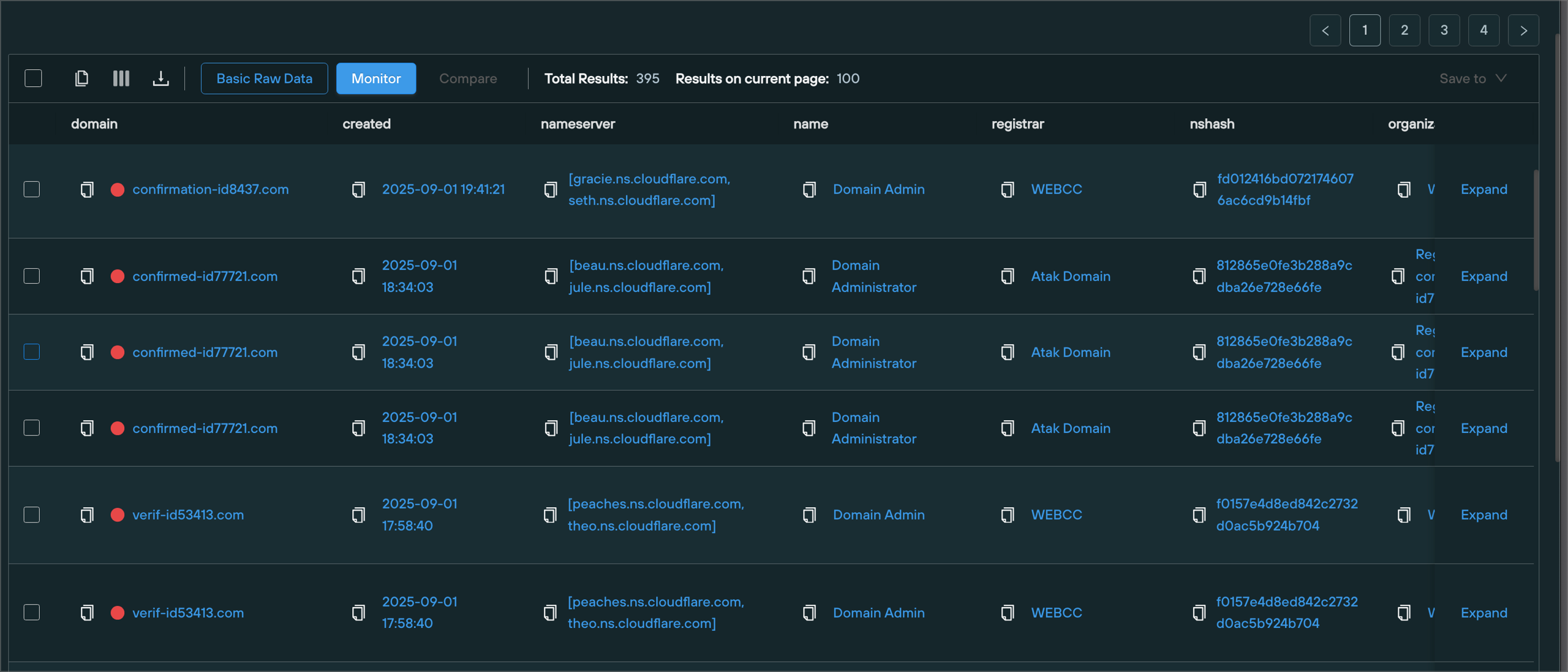
Clickfix Reservation Themed Domains
There are a seemingly infinite number of variations of Clickfix and fake captcha sites, but one pattern in particular has stood out as being easily signature-able at an early (domain registration) stage in the infrastructure lifecycle.
Below we’ve included one of the many signatures that we have deployed for these techniques, which is built around a cluster with a heavy usage of Cloudflare and a repeated naming theme captured via a regular expression.
This particular detection is based on
- Repeated usage of Cloudflare nameservers
- Domain name consistent of alphabetical characters followed by a dash, followed by
idor slight variants, followed by a long sequence of numbers and a.comTLD.
datasource = "whois" AND domain ~= "^[a-z]{3,}\-(id|di)[0-9]{4,}\.com$" AND created > "now-30d" AND nameserver = "*.ns.cloudflare.com"
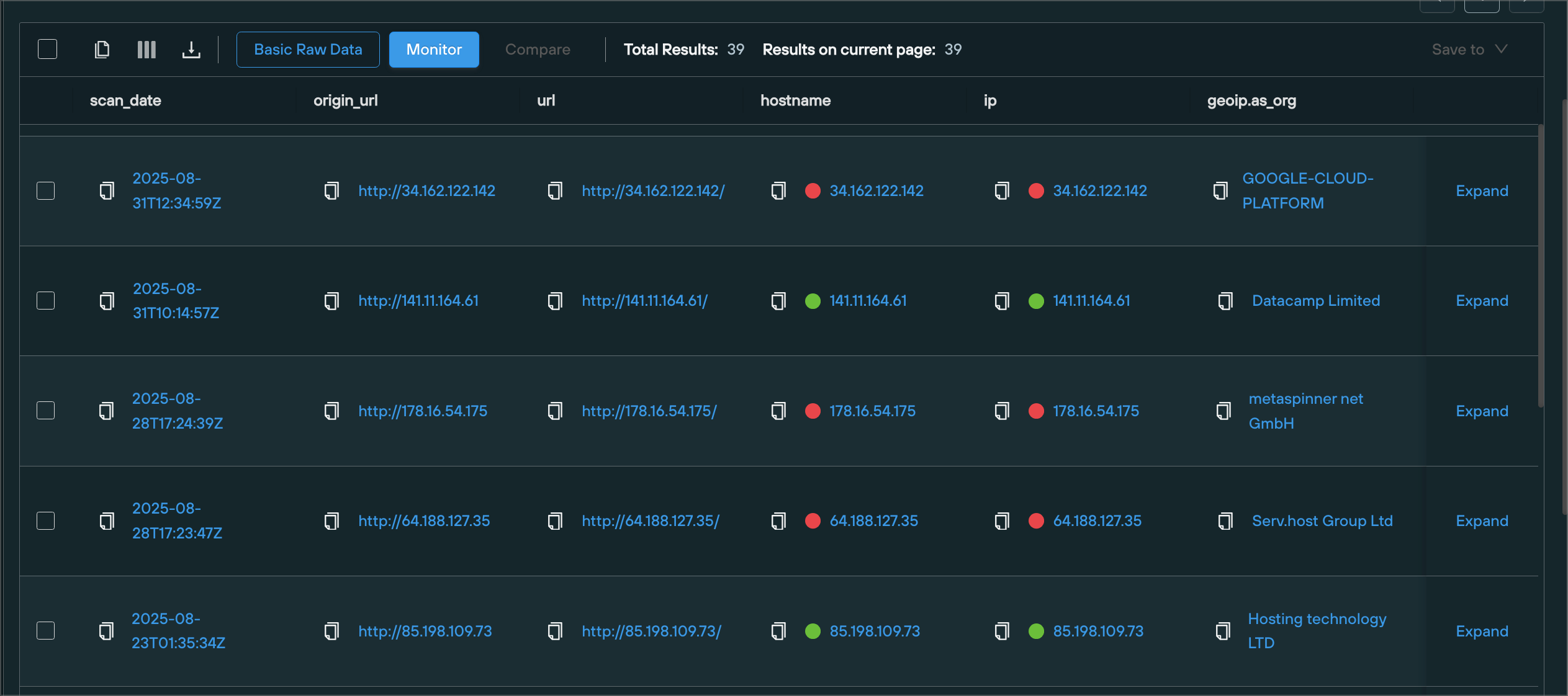
StealC – C2 Servers
StealC often configures their infrastructure in a way that leaves highly specific server headers that result in a specific header hash value (HHV) and 403 page if the C2 is scanned on the root directory. In addition to these, the servers often run with nginx on Ubuntu.
By querying for these exact characteristics, we can discover StealC command and control servers at an early stage and often long before other tooling has caught on.
datasource = ["webscan"] AND HHV = "72762a685d741189f3a91bd890" AND response = 403 AND path = "/" AND header.content-length = 0 AND header.server ~= "^nginx\/[0-9].[0-9]{1,2}.[0-9] \(Ubuntu\)$" AND tld ~= "^$"
We’ve regularly encountered results like the ones below, where search results show low detections on other tooling, often (but not always) with recent communicating files.
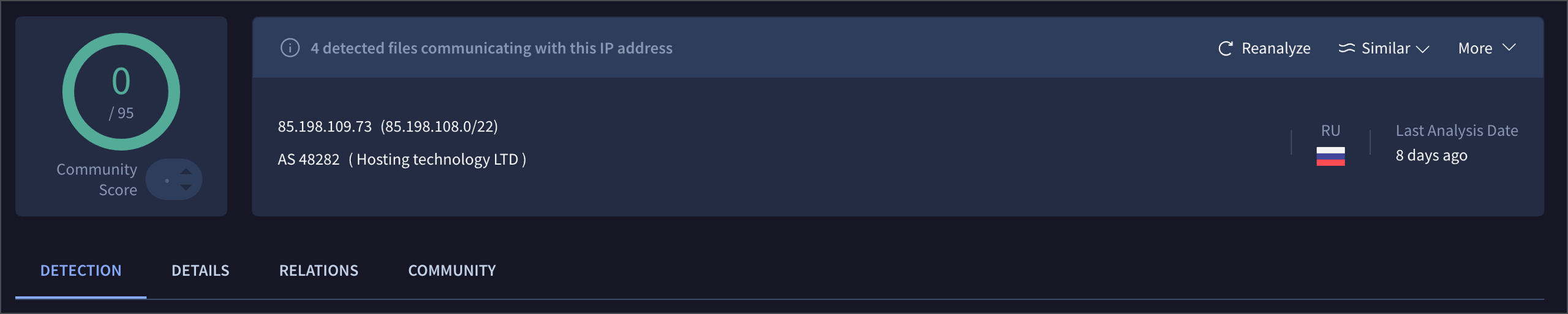
Latrodectus
Latrodectus is a popular loader and potential successor to the IcedID group of malware. For a period of time, Latrodectus command and control (C2) infrastructure featured a pattern that allowed it’s early discovery by our Threat Analyst team. Latrodectus has since made changes to this pattern, so we’re sharing this as insight into our approach and capabilities.
At the time of signature, we were able to find Latrodectus through their usage of Cloudflare, preference for .com domains, and a unique- 404 page on a root directory that we were able to signature using a partial ssdeep hash.
datasource = ["webscan"] AND geoip.asn = 13335 AND htmltitle = "404 Not Found" AND response = 404 AND html_body_ssdeep = "6:qzxqGObRBAEr6hzetKwzRx3eY+Cezou*" AND tld = "com" AND origin_scheme = "http" AND scheme = "http"
Clearfake – DGA Domain Discovery
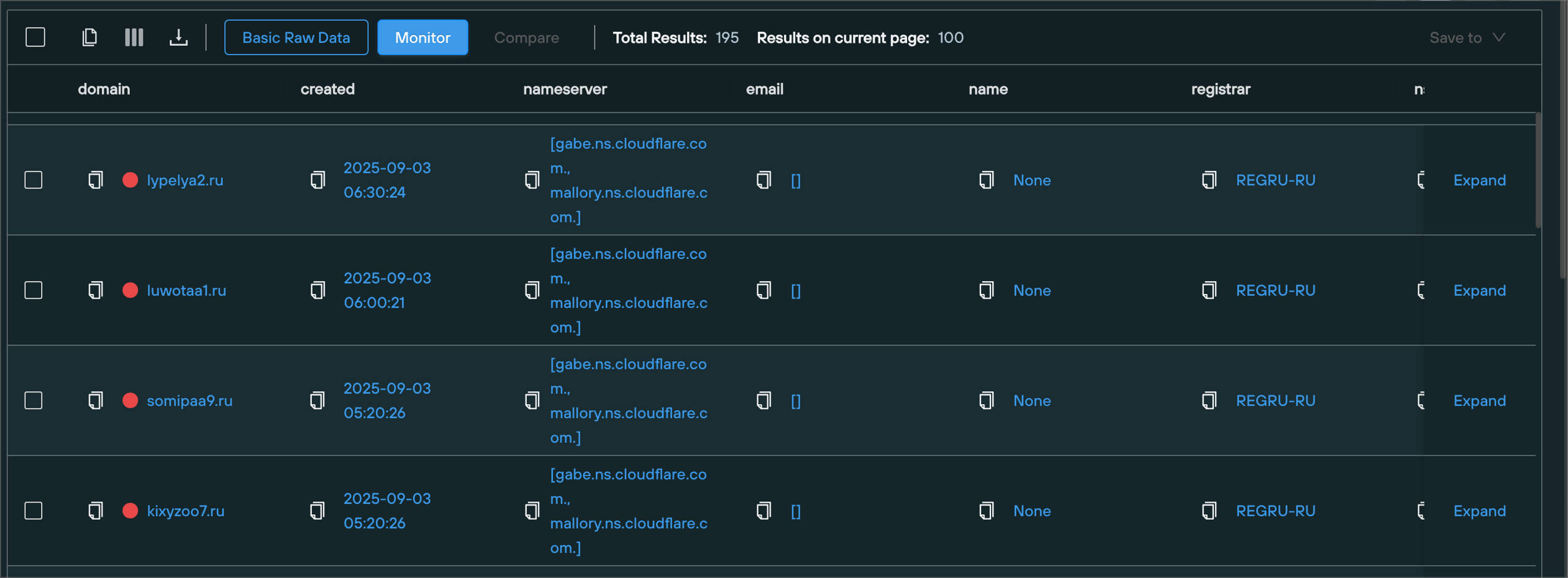
A less interesting but common occurence is the use of DGA style algorithms by Threat Actors to create and deploy domain infrastructure. A recent wave of infrastructure related to Clearfake falls into this category, with the cluster featuring a very consistent naming theme, registrar and nameserver pattern.
These characteristics can be combined for an early detection based on…
- Repeated usage of REGRU for the domain registrar
- Repeated usage of Cloudflare nameservers
- A domain naming pattern consistent of 7 alphabetical characters, followed by a single digit, followed by a
.ruTop Level Domain.
datasource = "whois" AND registrar = "REGRU-RU" AND created > "now-30d" AND nameserver = "*.ns.cloudflare.com." AND domain ~= "^[a-z]{7}[0-9]{1}\.ru$"
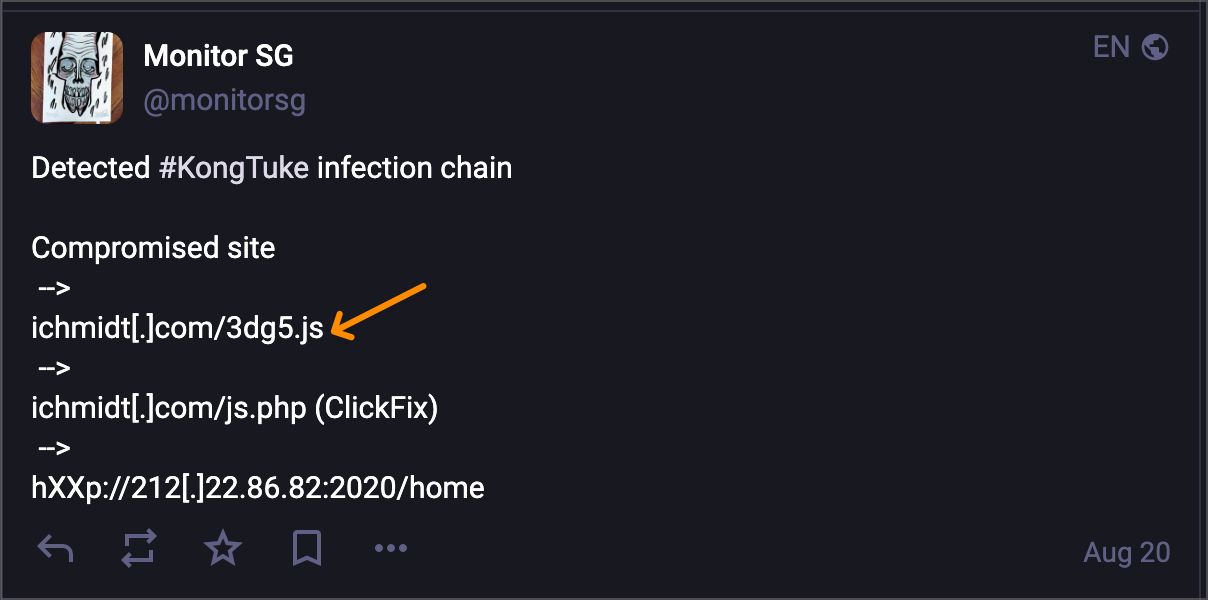
Kongtuke – Infected Sites
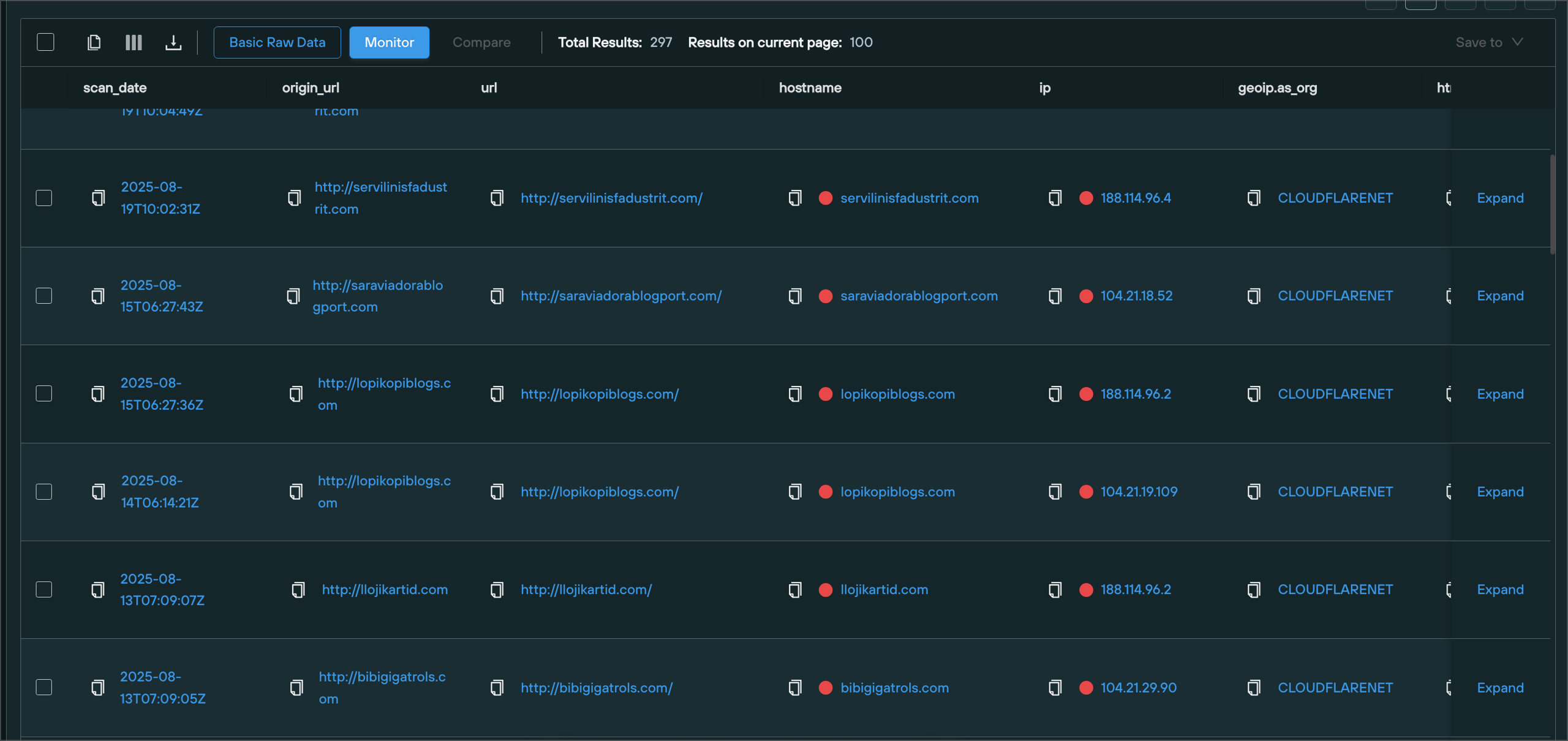
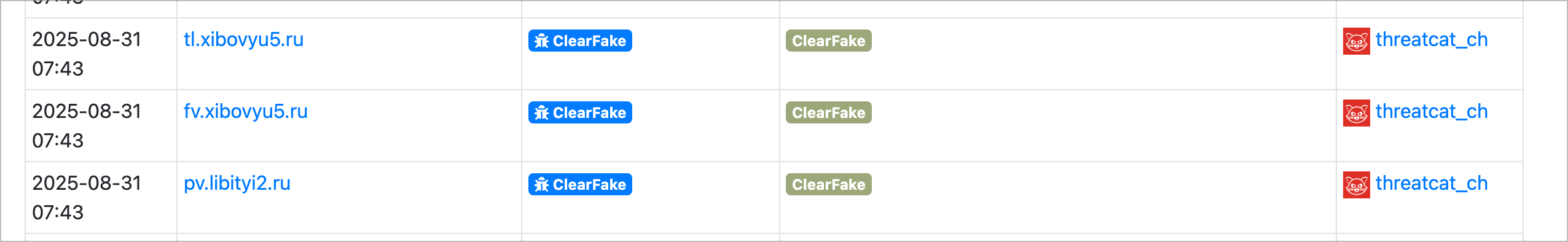
Kongtuke has been another ever present threat in the last months, with large numbers of sites compromised and injected with javascript files that ultimately display malicious prompts (via fakeupdates, clickfix or other tactics) that themselves deliver variants of malware.
When kongtuke or similar threats compromise a site, they often inject and load their own javascript file. During a given period of time, this javascript file follows a distinct naming pattern that can be signatured and used to track infected pages.
There are many variants of these patterns, but one of the most recent is a 4 character javascript file containing alternating alphabetical and numerical characters. The javascript file is generally hosted in the root directory of the attacker controlled site.
This all leads to the following primary pattern, with variants being derivations of this.
- Alphabetical domain name with varying TLD’s.
- 4 character javascript file hosted in root directory
- Javascript file is named with alternating alphabetic and numerical characters
- The domain is external to the infected page.
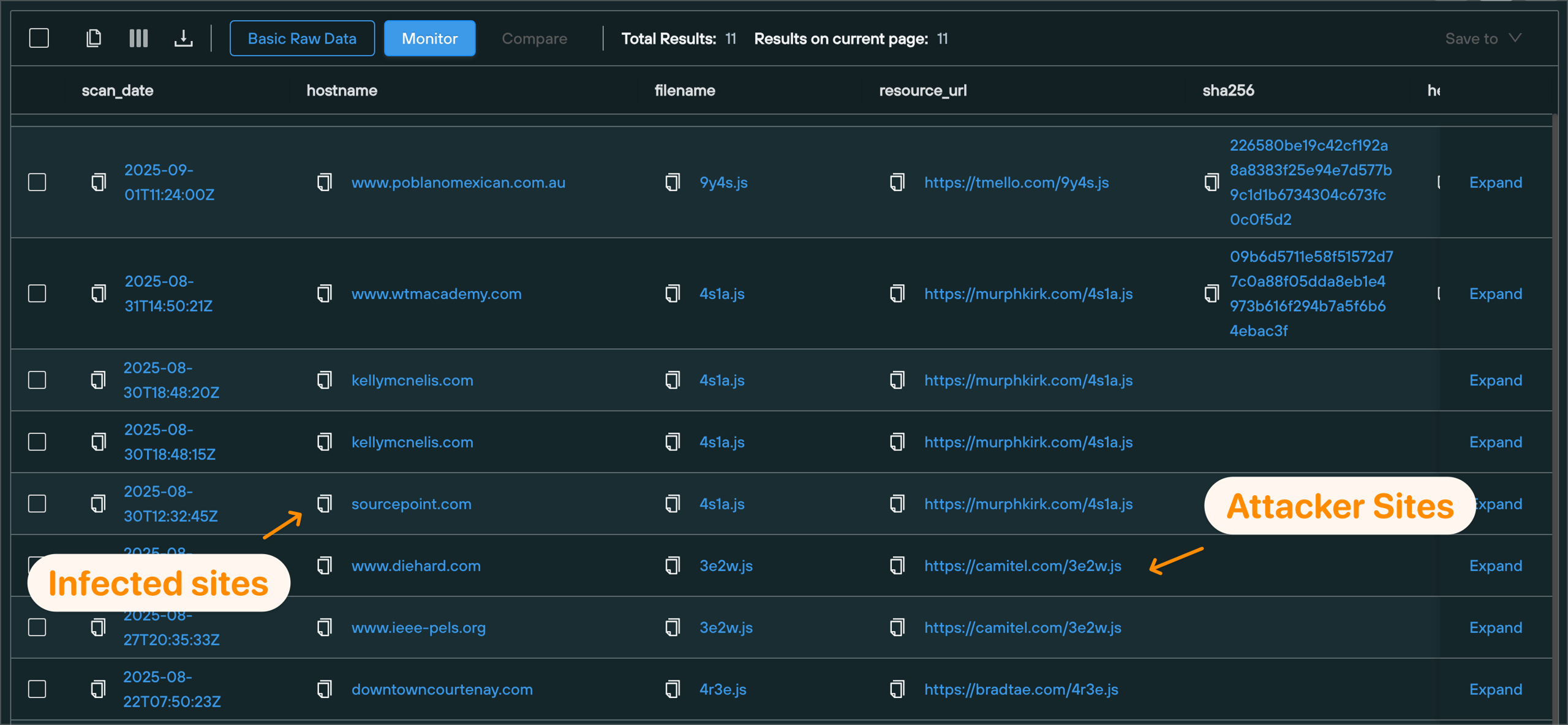
We can implement this as the following query
datasource = ["webresources"] AND external = "true" AND scan_date > "now-45d" AND resource_url ~= "^https{0,1}:\/\/[a-z]{3,20}\.[a-z]{1,}\/[0-9][a-z][0-9][a-z]\.js$"
Staying Ahead of Evolving Cyber Threats
Our Threat Analyst and product teams are hard at work creating fingerprints and capabilities to proactively detect the latest threats, helping our customers stay safe up to months in advance of many other tools.
If your team is interested in early detection and proactive cyber defense, book a demo with our team today.

