An autonomous system (AS) is a collection of IP subnets that is managed by a single administrative entity. Think of an ISP or a hosting provider, but also a large corporation or a university, many of which manage one or more autonomous systems. Each AS is assigned a unique number, called an ASN; in practice the terms AS and ASN are often used interchangeably.
ASNs play a crucial role in routing and thus in making the Internet work. However, because each of them is managed by a single entity, it also makes sense to assign a reputation to them, based on the amount of malicious activity hosted on the AS.
Silent Push assigns a reputation to each ASN, that takes into account both the number of active IP addresses within the AS and the number of these that are currently being used for malicious activities.
The reputation of an ASN reflects the current state rather than a historical reputation, so that ASNs that shut down malicious activity will see their reputation drop immediately. Historic reputation data is available through the API.
The Silent Push platform’s threat score reaches from 0 (best reputation) to 100 (worst reputation). The following are the ASNs with the worst reputation ranked by the number of IP addresses currently listed.
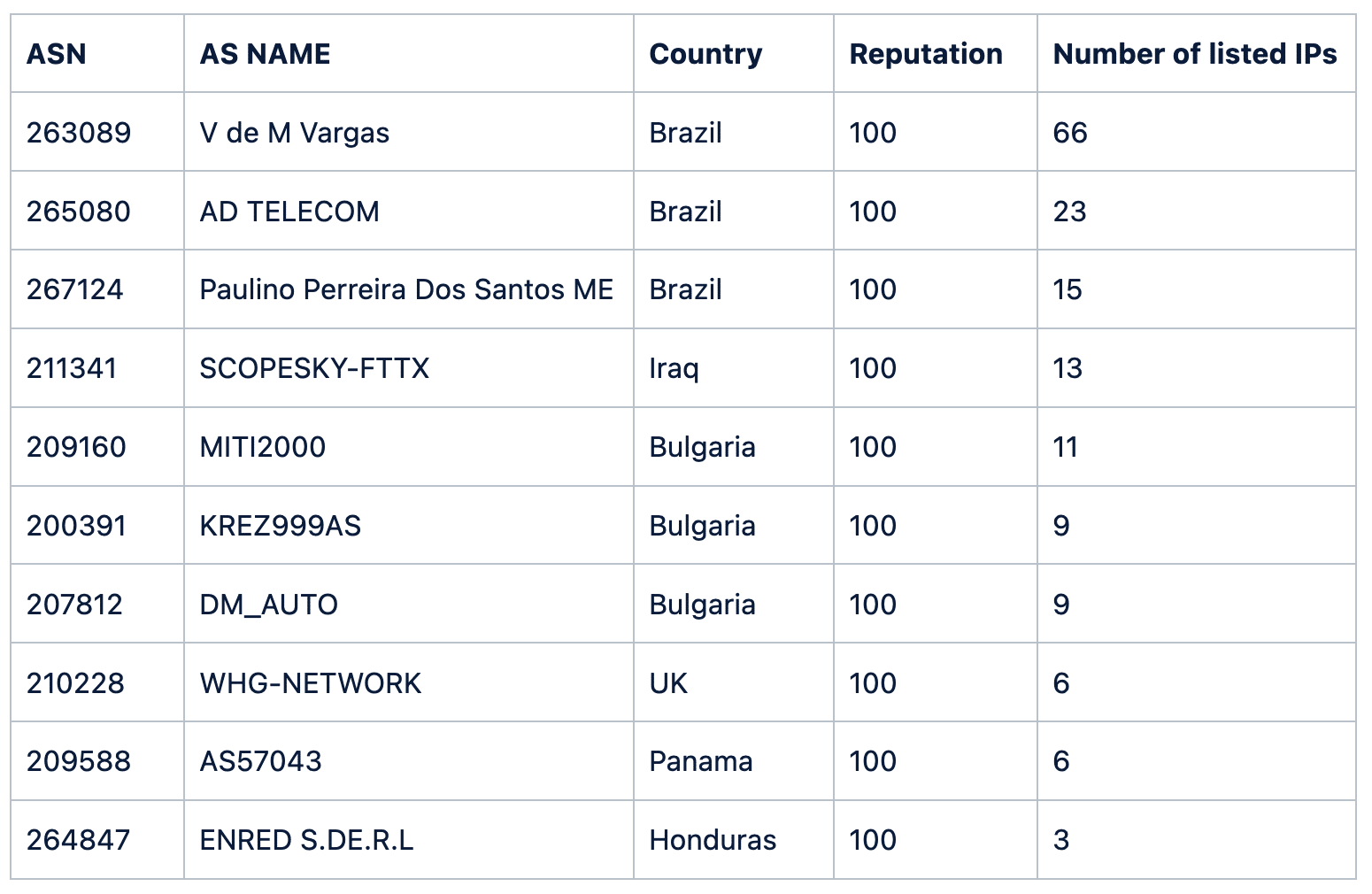
However, all of ASNs are all quite small, with each containing 2048 or fewer IP addresses. They host a relatively large amount of malicious activity, but in absolute terms, their contribution to ‘bad things on the Internet’ is pretty small.
Look at the ASNs below that contain at least 100,000 IP addresses (active or not):
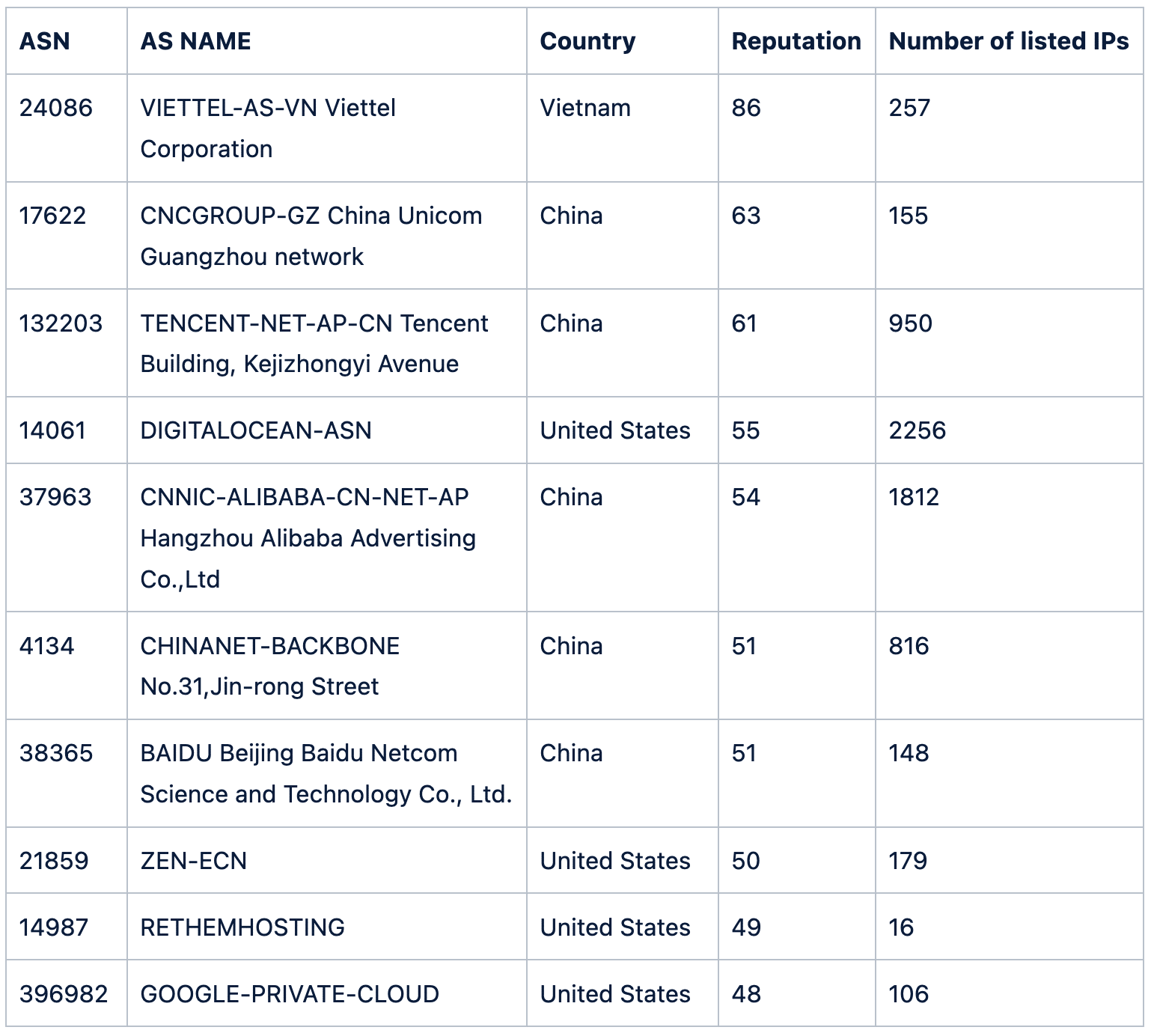
Now, a number of well-known companies appear in the list, including Tencent, Digital Ocean, Alibaba and Google.
Each of these cloud providers make it easy for someone to quickly and anonymously set up a virtual server. That has many advantages for researchers and developers but also attracts those hosting malicious infrastructure, such as malware authors or those providing services to them.
It is not recommended to block something just because it is hosted by any of these providers. But something unknown hosted there definitely deserves some extra scrutiny.
Takedown reputation
In fairness, it is unreasonable to expect a hosting provider or other network to be able to proactively block all malicious activity on its network. After all, it’s not like a malicious actor is open about their intentions when renting a server or purchasing a domain.
This is why at Silent Push, one can assign a ‘takedown reputation’ to each ASN, that assigns a score from 0 (best reputation) to 100 (worst reputation). This measures how well an ASN takes down malicious activity hosted on its network.
If we add the takedown reputations to the previous table, we note they are all low, but in some cases not 0. This leaves some room for improvement for these ASNs when it comes to their due diligence in keeping the Internet free of malware and scams.
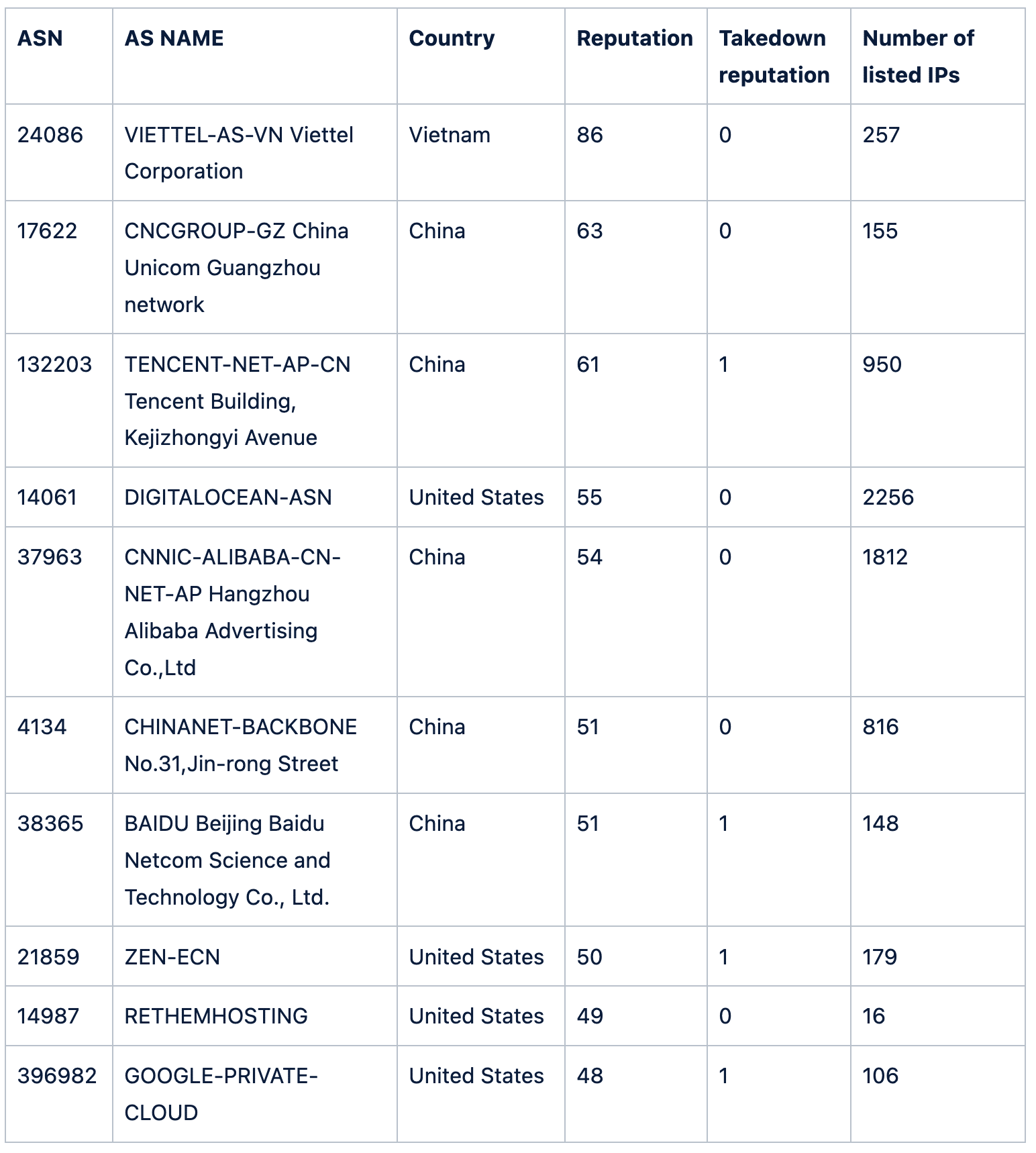
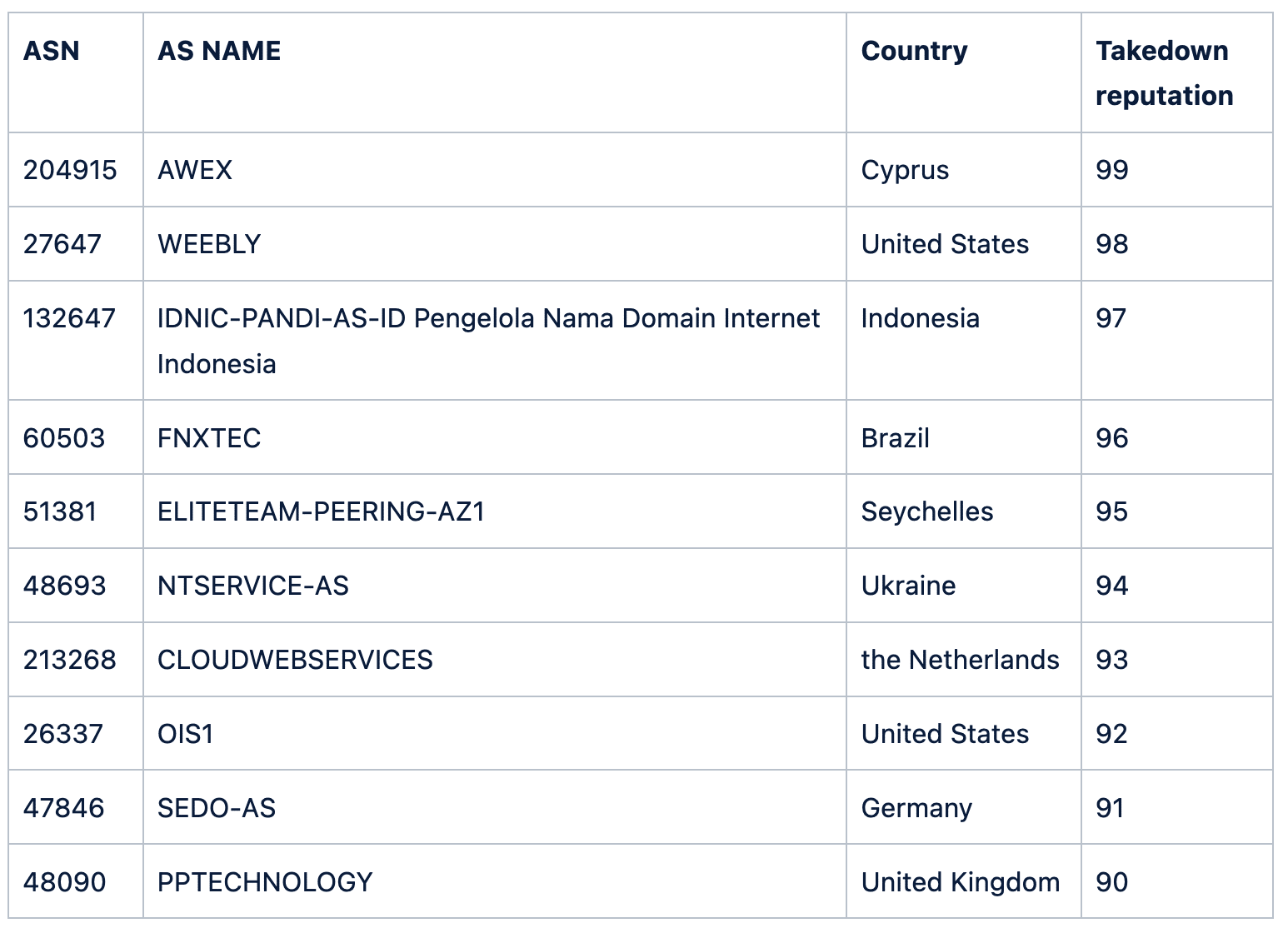
Finally, look at the ASNs with the worst takedown reputation. These are all pretty small, containing 4096 IP addresses or fewer, and have a takedown reputation higher than 90:
Conclusion
Simply ranking ASNs or hosting providers by the number of IP addresses that are hosting or have hosted malicious content ignores both their actual size and their responsiveness when it comes to takedown requests. By including both, Silent Push provides you with a clearer picture of what ASNs to consider somewhat suspicious, which combined with other context can help during an investigation.