Key Findings
Silent Push Threat Analysts recently discovered two hostnames, api2.cloudns[.]net and web2.cloudns[.]net, belonging to ClouDNS, that pointed to an IP address managed by threat actor Prolific Puma.
ClouDNS is a hosting company based in Bulgaria that appears to work with numerous enterprise organizations like Hostway, KIA, Der Spiegel, Houston Community College, and more. When we contacted them, ClouDNS quickly updated the DNS records for the affected hostnames.
While we were not able to detect malicious activity around this discovery, we want to make our community aware of potential vulnerabilities:
- Legitimate hostnames pointing to maliciously owned infrastructure can be used to bypass security products.
- They can be misused to directly target a company, using familiar-looking links to trick employees and users into believing malicious links are legitimate.
- They can be used to conduct cookie-based attacks on authentication providers and to set up sophisticated phishing kits.
- They can also be used to show ownership, at least of the subdomain, and to generate SSL certificates.
Mitigation
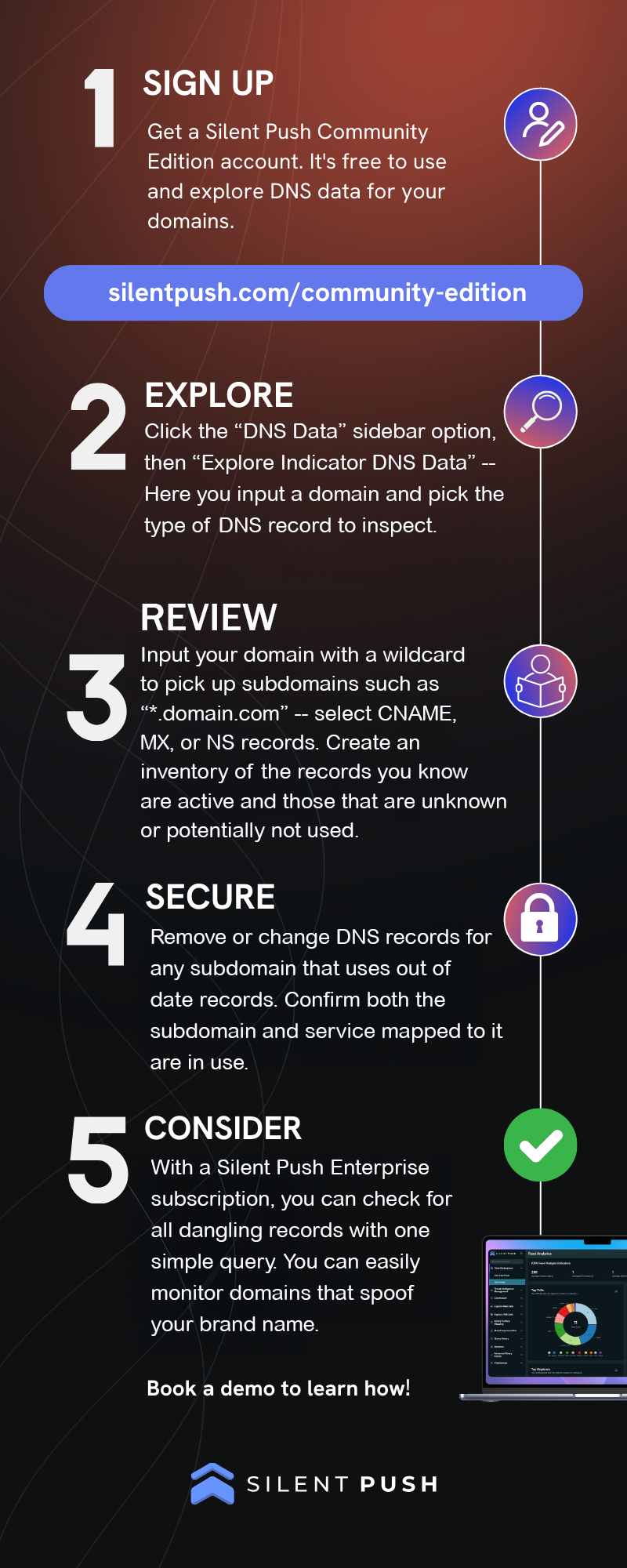
We encourage organizations to regularly check their DNS settings for hostnames pointing to IP addresses they don’t control or might not be using. Silent Push makes this process simple, enabling users to easily check DNS settings of interest by using our free Silent Push Community Edition account.
While the nature of this public-facing blog is to make our community aware of vulnerabilities associated with forgotten domains, Silent Push believes all domains associated with Prolific Puma offer some level of risk.
Our analysts have constructed a Silent Push IOFA™ Feed that provides a list of Prolific Puma Indicators of Future Attack™ (IOFA™). Silent Push threat researchers continuously track over a thousand active domains for Prolific Puma as we observe and monitor changes to this actor’s infrastructure. New discoveries, campaigns, and TTP changes will be immediately reflected in our feeds.
For operational security reasons, we are unable to publicly share the exact details of how we are tracking Prolific Puma infrastructure.
Silent Push IOFA™ Feeds are available as part of an Enterprise subscription. Enterprise users can ingest IOFA™ Feed data into their security stack to inform their detection protocols or use it to pivot across attacker infrastructure using the Silent Push Console and Feed Analytics screen.
Register for Silent Push Community Edition
Silent Push Community Edition offers free access to our threat-hunting and cyber defense platform, featuring a range of advanced offensive and defensive lookups, web content queries, and enriched data types, including both the Silent Push Web Scanner and Live Scan.
How Silent Push Tracks Threat Actors
Watch our presentation at mWISE 2024 to learn more about how we track threat actors like Prolific Puma.
Get a Demo of Silent Push Preemptive Threat Intelligence
Silent Push is the first and only provider to reveal unique threat patterns of all attacker infrastructure existing on the clear net and dark web.
We go beyond Indicators of Compromise (IOCs) and expose IOFA™ through our proprietary behavioral threat modeling. This allows security teams to reveal attacker campaigns before they even start – neutralizing threats and preventing damage.
Request a demo today to see how your team can block threats before they become problematic.


