Silent Push maps 5000+ domains and IPs affected by CrushFTP zero day exploit (CVE-2024-4040).

Executive Summary
On April 19th, CrushFTP released a public security advisory (since categorized as CVE-2024-4040, with a severity score of 9.8) that warned users about a zero-day bug in all versions prior to 10.7.1 and 11.1.0.
The exploit allows unauthenticated attackers to escape a user’s Virtual File System (VFS) via the WebInterface port, obtain administrative access, and execute remote code on the server.
CrushFTP has advised users to immediately upgrade to a secure version, even if they are operating a Demilitarized Zone (DMZ) in front of their CrushFTP instance.
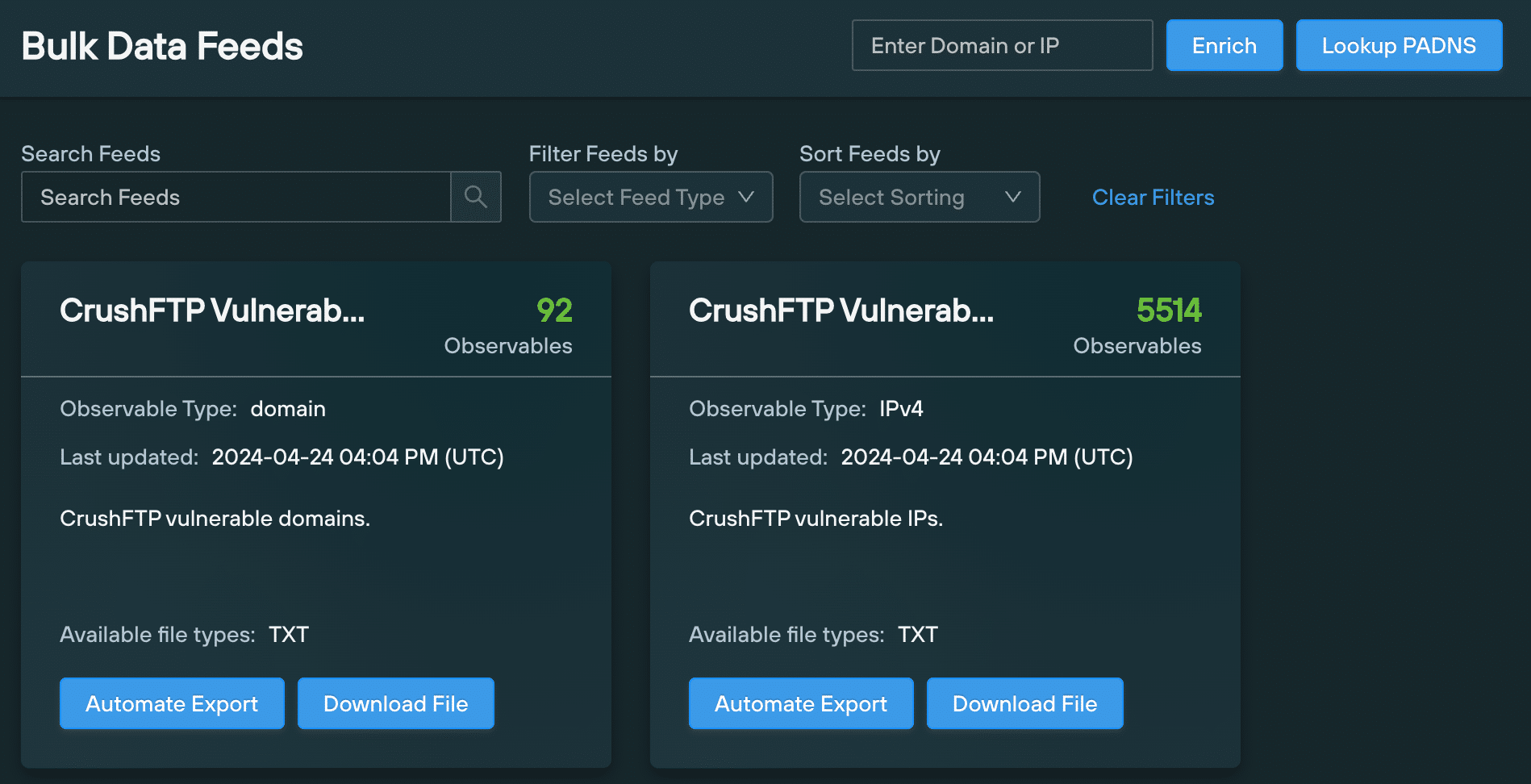
Silent Push Threat Analysts used our first-party dataset to track all vulnerable Crush FTP instances, and populate two Bulk Data Feeds with domains and IPs that are hosting vulnerable instances of the popular file transfer service.
We’re also in the process of creating an Early Detection Feed, filled with infrastructure that is actively attempting to exploit CVE-2024-4040.
Tracking vulnerable CVE-2024-4040 web portals
Silent Push scans the clearnet and dark web every day and categorizes the data using SPQL – our custom free-form query language – and makes it available for our customers to locate associated infrastructure and web content.
Using the information we have on CVE-2024-4040, we executed a query that locates exploitable CrushFTP web interfaces exposed to the Internet, and clustered the returned domains and IPs together in two Bulk Data Feeds that our Enterprise customers can use to locate and analyze vulnerable infrastructure:
- CrushFTP Vulnerable Domains
- CrushFTP Vulnerable IPs
Geographic spread of vulnerable servers
SPQL allows users to analyze DNS datasets across 90+ individual categories.
To help potential victims and the wider security community visualize the extent of the problem, we’ve created this map that displays the global distribution of vulnerable CrushFTP interfaces:
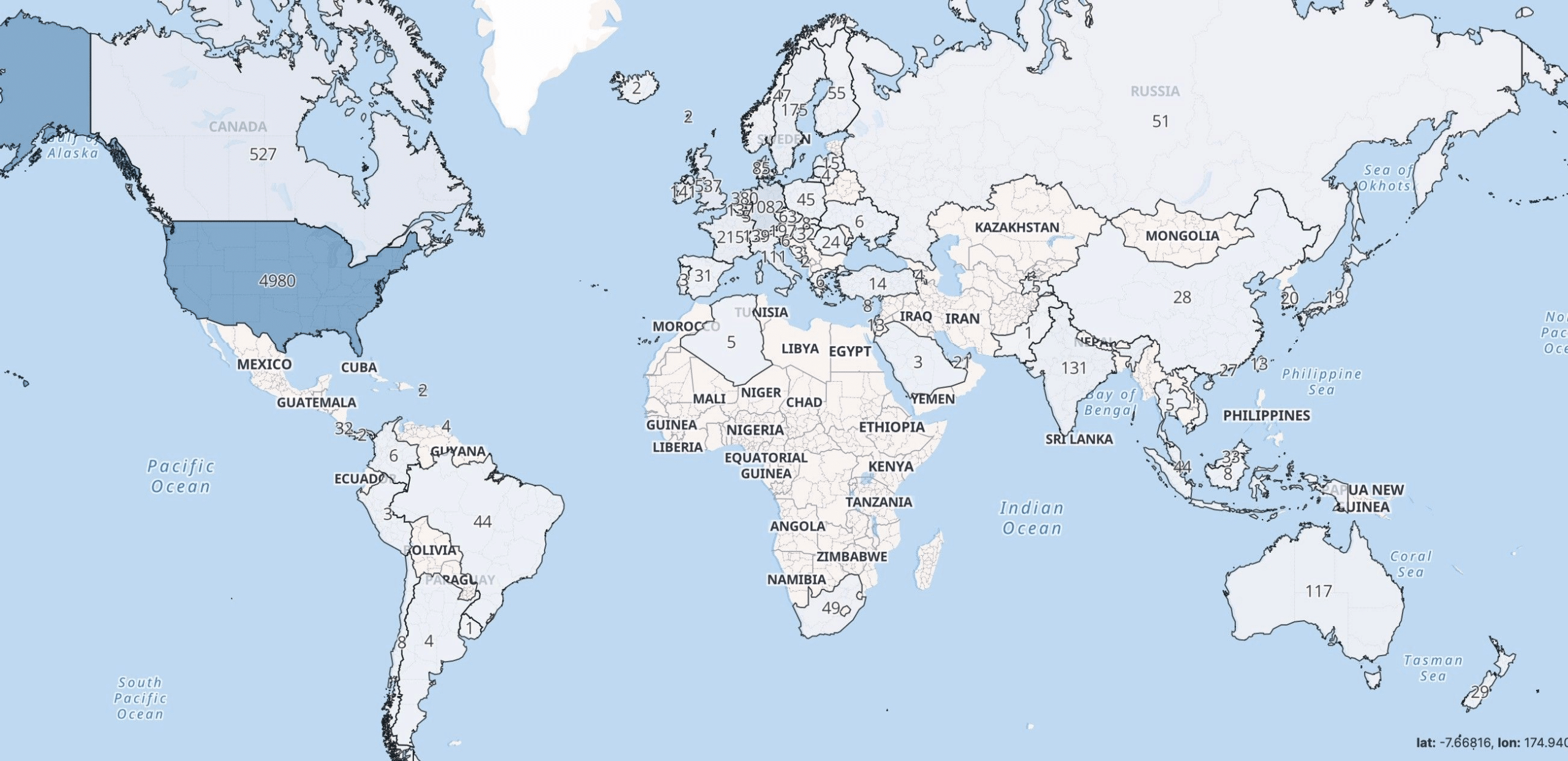
The majority of affected servers are located in the United States, Canada, and continental Europe, with the rest spread out fairly evenly across South America, Russia, Asia and Australia.
Mitigating the effects of CVE-2024-4040
As well as a raw data download, Enterprise users are able to export the Bulk Data Feeds as an API endpoint, containing all the domains and IP addresses of vulnerable CrushFTP instances.
Security teams can use this information to identify internal infrastructure that may be vulnerable, and inform any scoring systems they have in place that evaluate the risk level of external domains and IPs.
We’re also constructing an Early Detection Feed that’s tracking intrusion attempts in realtime, and logging the infrastructure involved for automatic blocking. We’ll be publishing further details on this in the coming days.
Register for Community Edition
Silent Push Community Edition is a free threat hunting and cyber defense platform featuring a range of advanced offensive and defensive lookups, web content queries, and enriched data types, including Silent Push ‘Web Scanner’ and ‘Live Scan’.
Click here to sign-up for a free Community Edition account.

