Fake trading apps are on the rise, and spreading to a wider a wider global victim base than ever before.
In crypto scams alone, in 2021, the figure was over $7billion. Let’s take a look at some common tactics, and tell-tale signs that’ll help you spot the fraud.
Fake trading app scams involve both mainstream regulated platforms, and new, unregulated crypto exchange start-ups.
Let’s take a look at standard a real-world example: a malicious app download from attacker-controlled infrastructure.
Outline
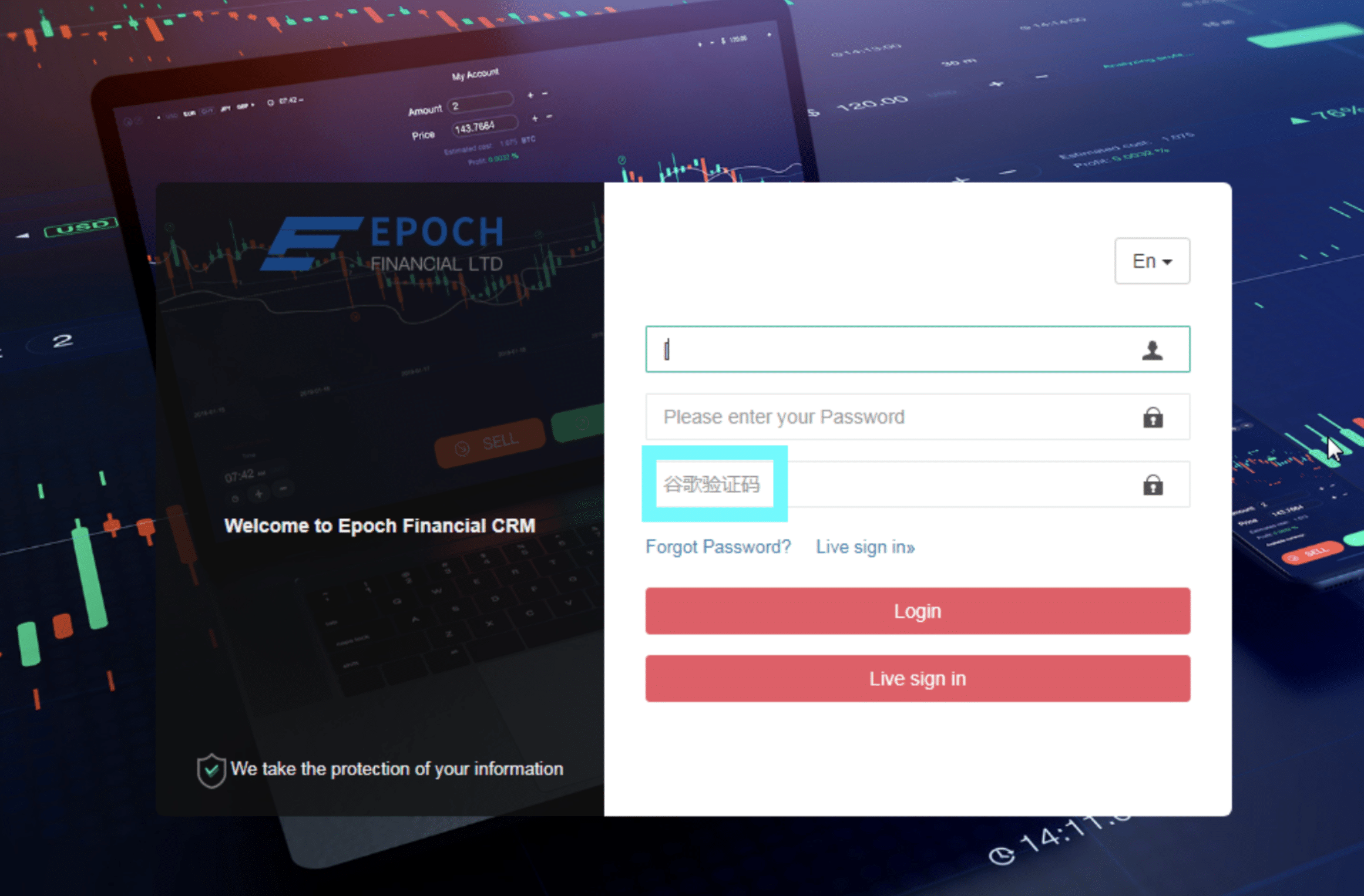
Silent Push has uncovered a threat actor operating via several websites, Android and iOS applications with counterfeit versions of trading platforms on the traditional stock market, and across a variety of crypto exchanges.
Bespoke fake trading platforms mimic well-known financial organizations – including such as the Australian Securities Exchange (ASX), Coinbase, CoinSmart, eToro and Nasdaq – lure unsuspecting victims into trusting their services, only to steal their investments.
This particular group has scammed and stolen money from countless individuals worldwide. We’ve conducted a large investigation, collecting hundreds of Indicators of Compromise (IoCs), as well as reports from victims which allowed us to map their infrastructure and put together a pattern of events that revealed a common set of attack vectors.

Threat actor profile and history
Although we’re unable to pinpoint a date when this threat group began its activity, we can confirm that several active items of malicious infrastructure were deployed in early 2021.
We also have access to reports which describe several occurrences with similar characteristics to this group, around that time period.
Given that these victims were located in Asian countries and that we found a small number of websites written in Asian dialects, we can only assume that this threat actor is located in Asia.
After analyzing their current infrastructure, American and European organizations appear to be at the highest risk.
Platform design
A visual pattern is evident across the majority of the websites we investigated.
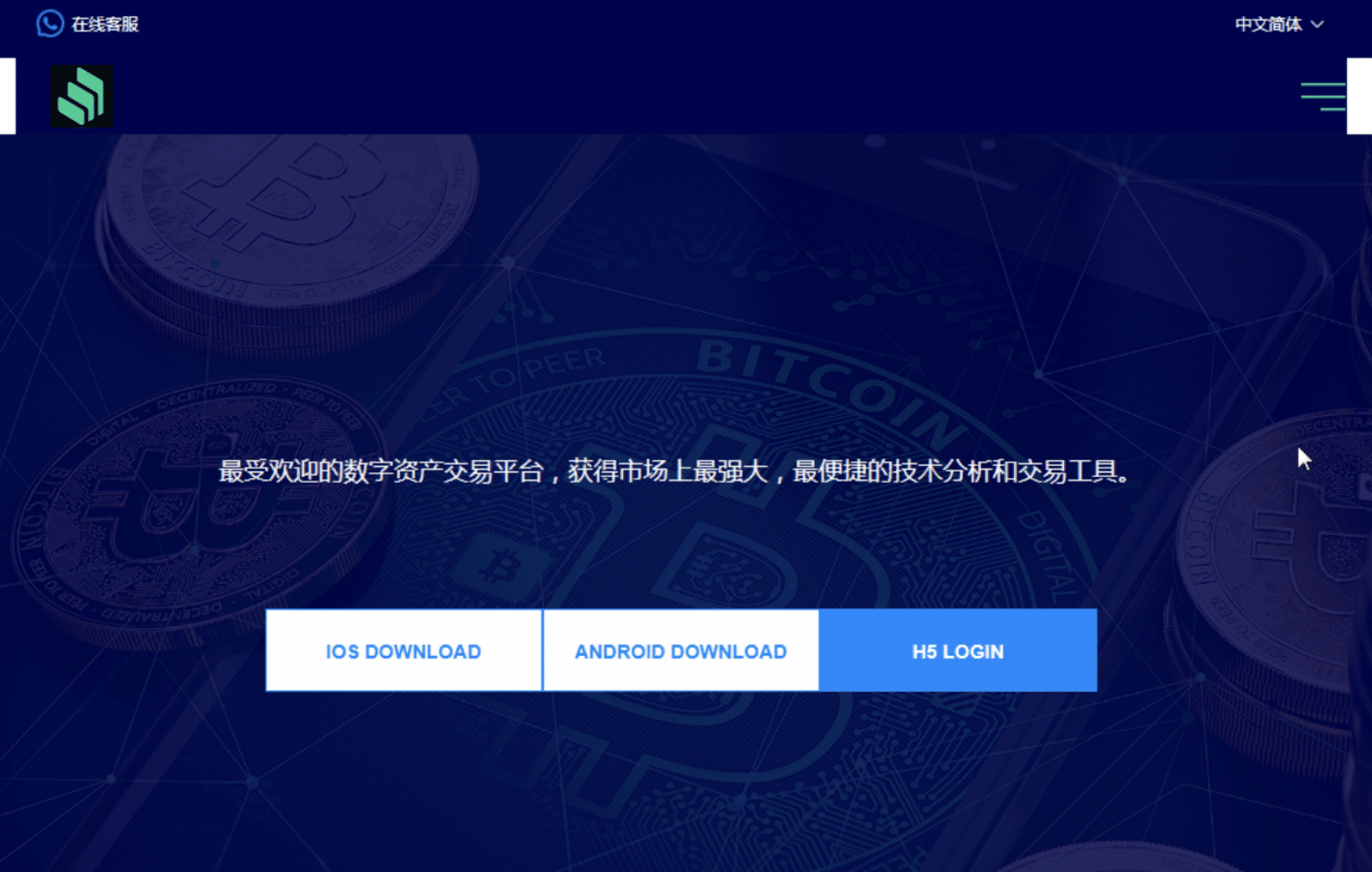
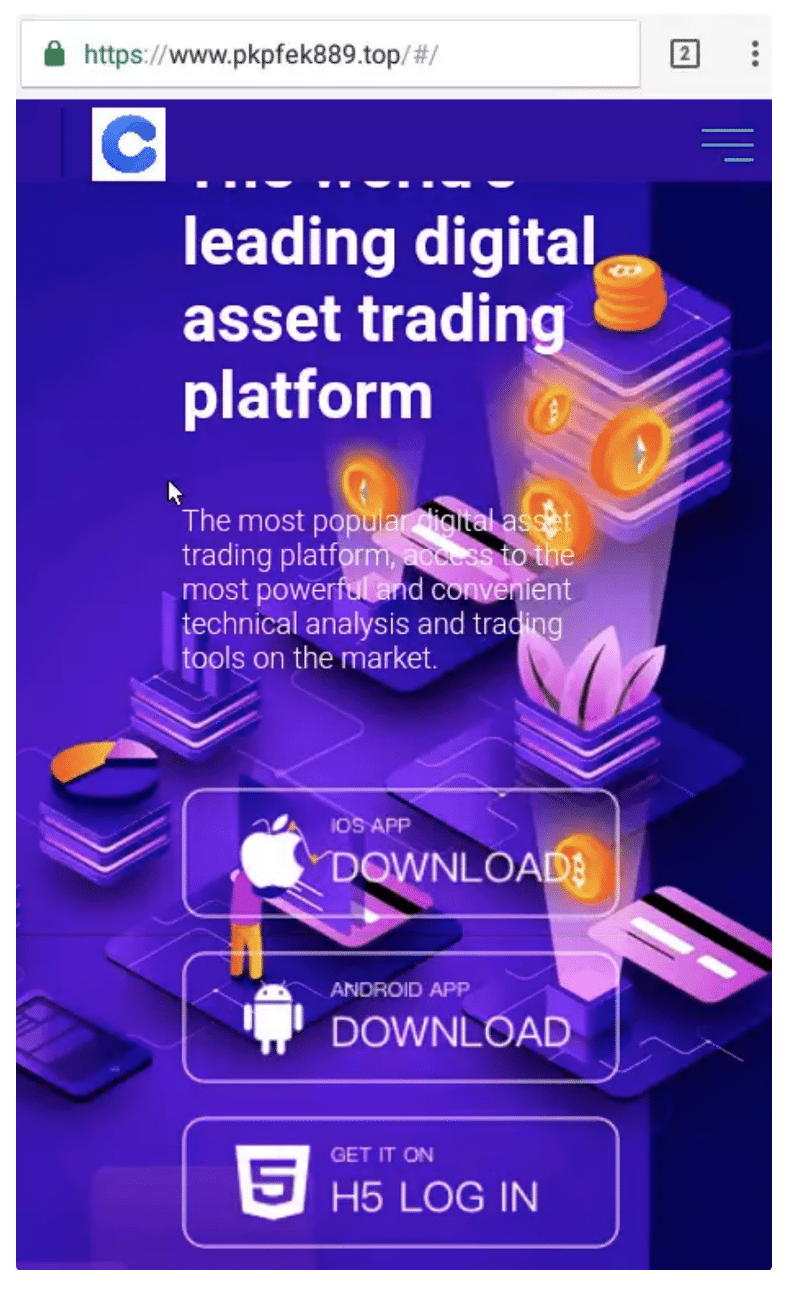
Despite having different branding, the pages are structured in the same way: there is an initial website similar to the one displayed below, which is used as a landing page to attract potential victims.
From this website, visitors are able to navigate to one of the following two pages:
– the app download page, similar to the one displayed in Image 1;
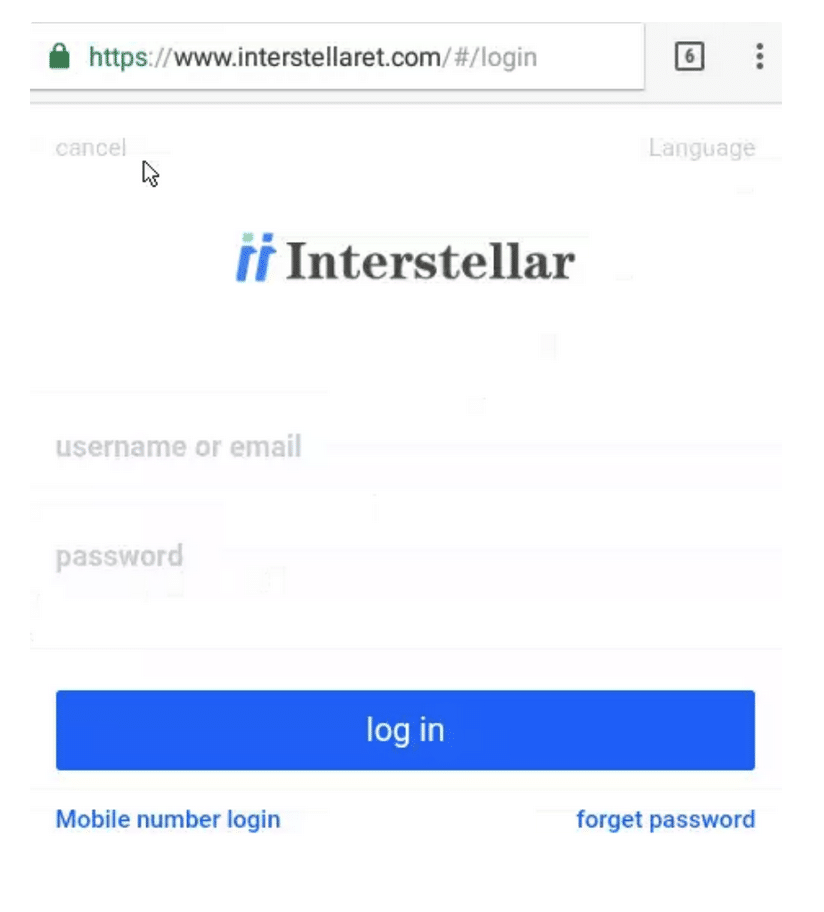
– the website login page, where users can register and login into an account.
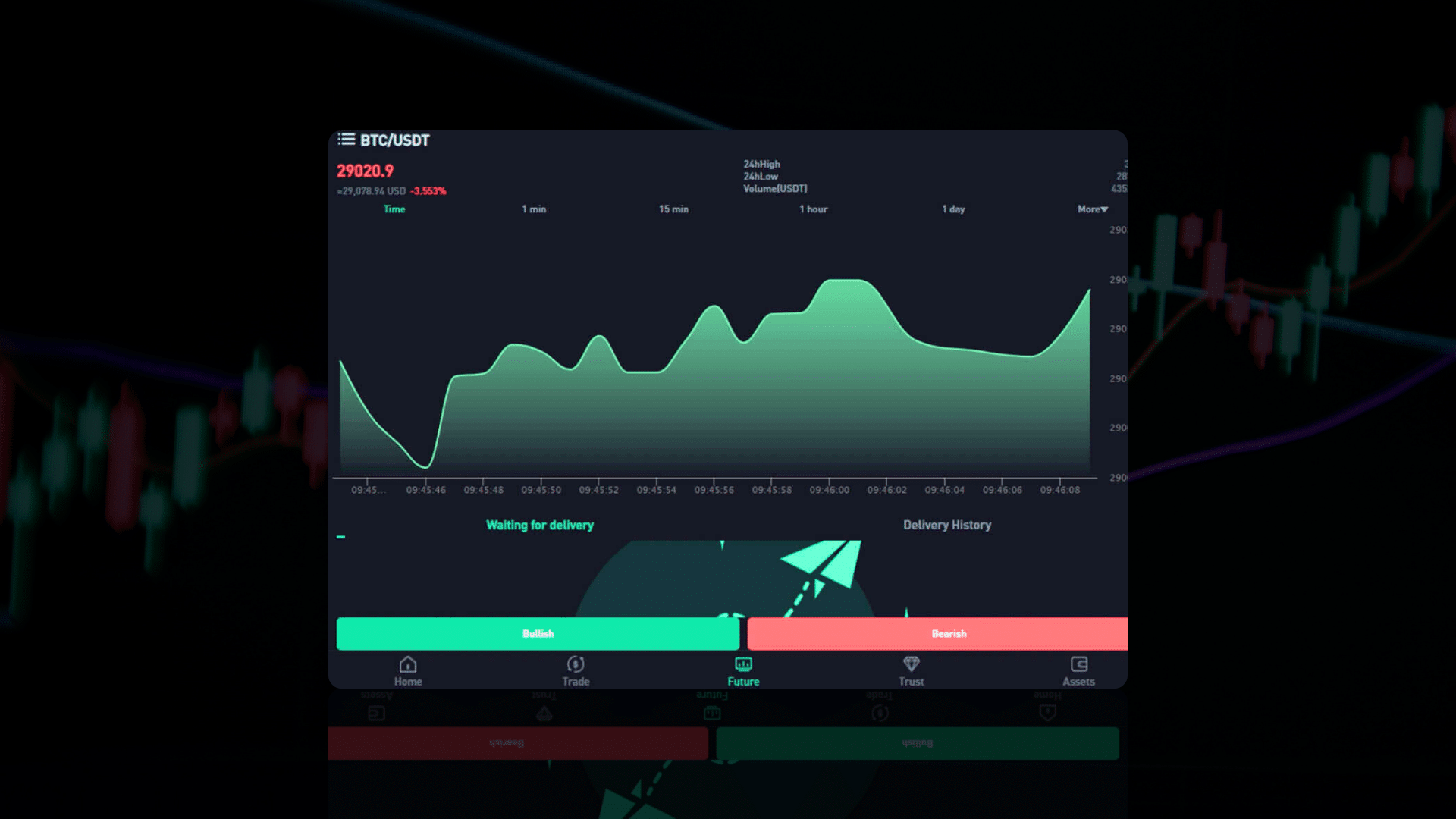
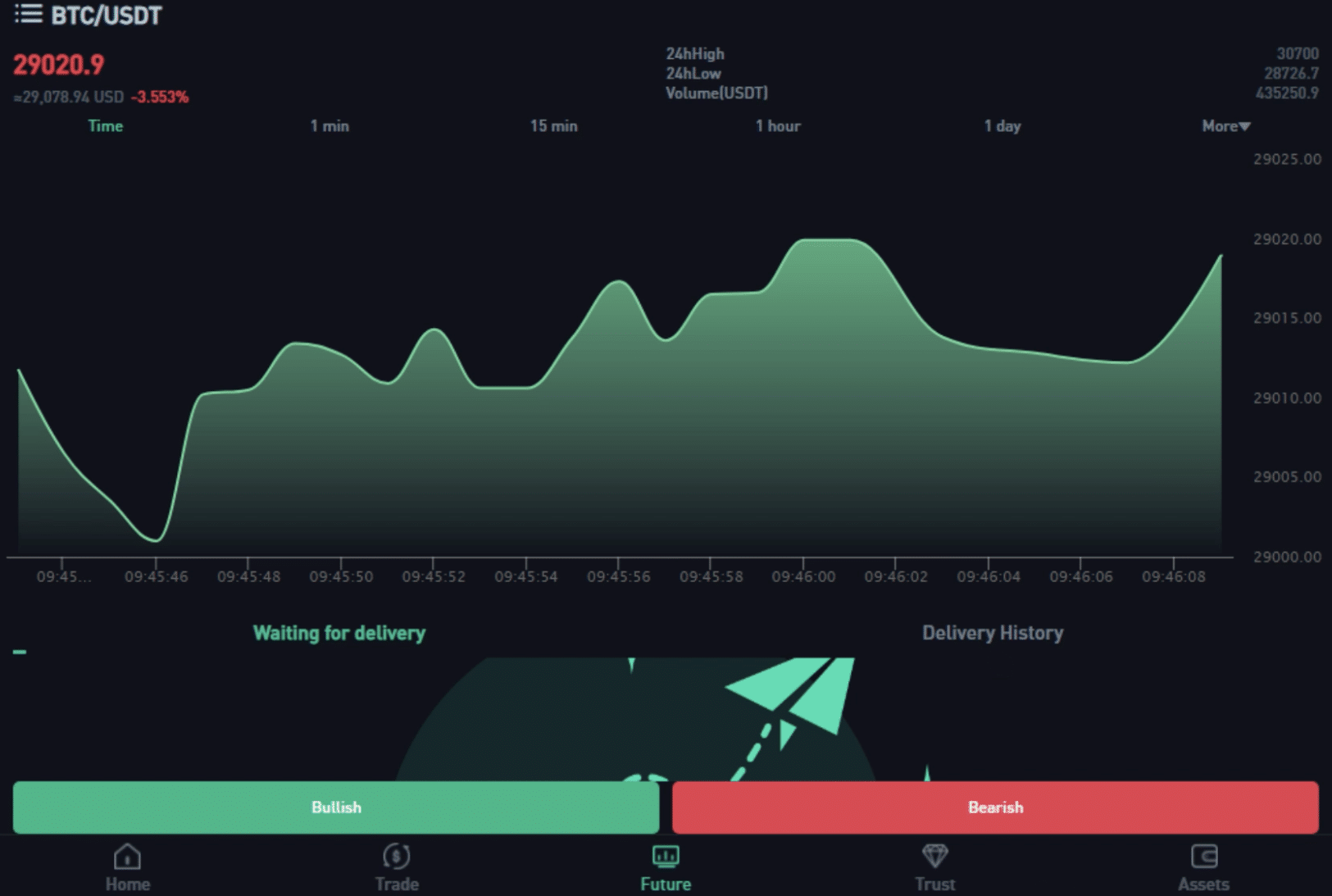
We believe that this is a web alternative to the app, which allows the users to transact funds and analyze fake stock indexes, as is visible in Image 3.
This fits into the Crime-as-a-service model with the fraudulent platform being distributed by different affiliate providers.
Victims’ reports
We found many complaints concerning this malicious agent surfacing on the internet. As suspected, the majority of them were written by scammed individuals but also by people who wish to take down this organization.
Initial interactions with the threat actors vary due to a possible affiliate scheme. We have seen varying reports from Romance Scams (hence Sophos referring to this as Cryptorom) to Forum recommendations.
Whatever the initial introduction and resulting conversation the victim eventually puts money into the fake account.
Unfortunately, once the victim tries to withdraw the money, they see themselves logged out of their account and unable to log in, while the threat actors keep their funds and plan the next target.
We found similar messages on various websites as well as announcements from some fintechs reporting this robbery scheme.
Installation process.
The primary target is mobile devices.
The threat actors encourage users to download a mobile app or a web app, with download links for both iOS, and Android.
It appears that the attackers exploit two main ways to get around the Apple approvals process:
- The first one is done by creating a configuration profile, which is a
.mobileconfigfile that can be easily shared. - The second one is through Testflight, a tool created by Apple, that allows developers to test their applications and provide Beta versions of new apps without facing the severe verification protocols found on the Apple Store. TestFlight apps allow public downloads to up to 10,000 accounts.
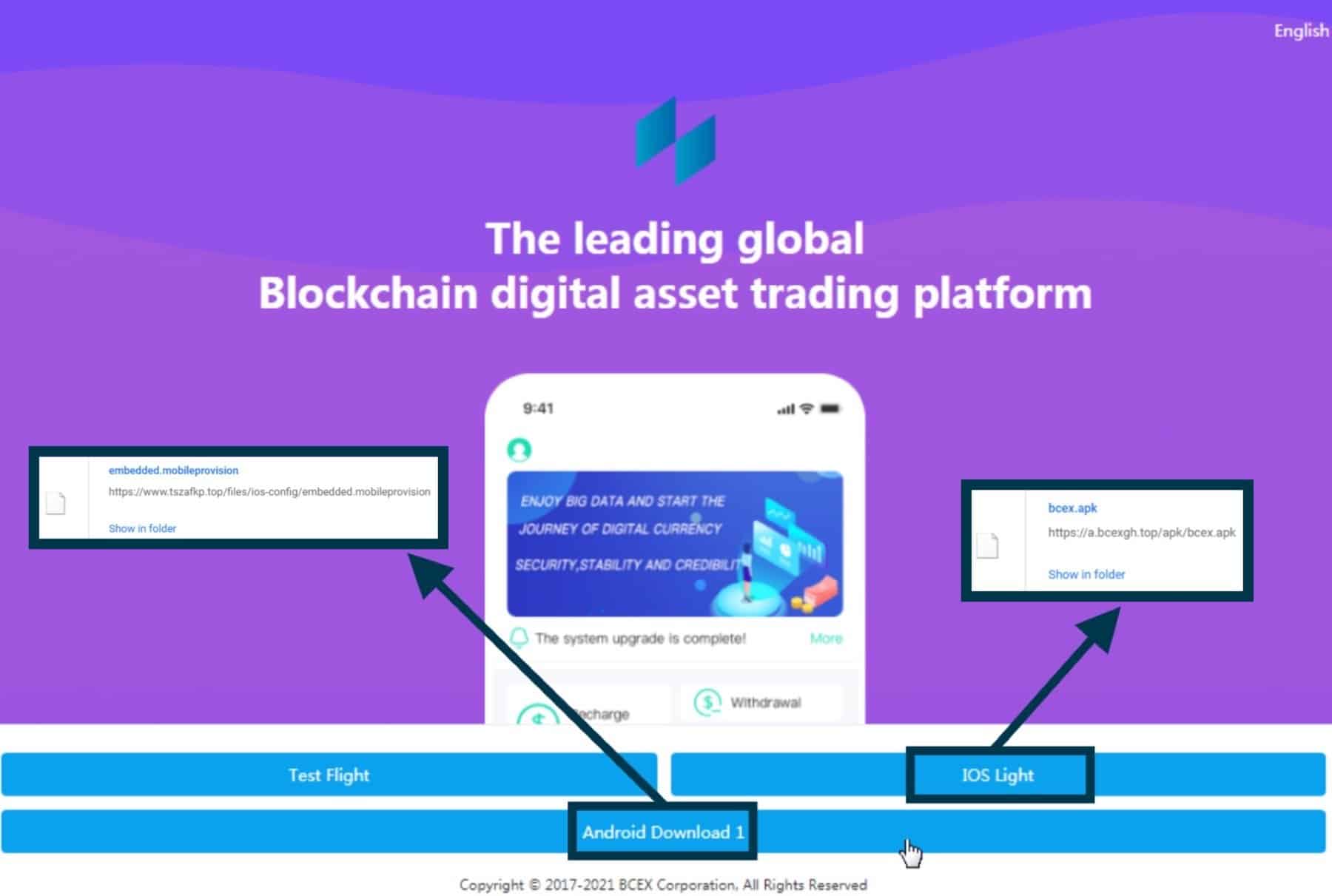
When it comes to Android users, an .apk file with a tailored name matching the specific website gets downloaded.
Careful analysis reveals obfuscated information using a combination of StringFog, base 64 and a XOR operation to encrypt suspicious data.
Using Silent Push to combat malicious infrastructure
Taking everything into account, we are confident that this threat actor will continue to develop and distribute trading platforms, in order to exploit and steal funds.
The methods of delivery will vary, as expected with an affiliate program. We recommend blocking access to the underlying app download infrastructure and utilizing proactive threat intelligence to pinpoint malicious domains and DNS infrastructure.
With that in mind, we’ve collated an extensive list of IoC, available for paid Silent Push customers.
Paid users have access to pre-built customizable queries that allow them to identify malicious infrastructure before it becomes a problem, as well as access to granular WHOIS, server and DNS information, and curated risk scores.

IOCs of Fake Trading Apps
Subdomains
d.appk12036[.]xyz
d.appk56295[.]xyz
d.appkoi65y[.]xyz
d.appl8965[.]xyz
d.appl9035[.]xyz
d.appr6552[.]xyz
d.atfxwqe[.]xyz
d.avatradewqd[.]xyz
d.bbexsbcv[.]xyz
d.bitcudbf[.]xyz
h5.amcoinbhd.buzz
h5.ascifgm[.]top
h5.asxnvds[.]cc
h5.biupsdfe[.]cc
h5.blyg367[.]top
h5.bqsbkomh[.]net
h5.bsxkiso[.]cc
h5.cnfalwk[.]top
h5.coinbasekp.buzz
h5.coindealmip[.]cc
h5.dbag-prot[.]com
h5.dbagde[.].cc
h5.dcgbyre[.]shop
h5.dcgtbh[.]com
h5.eurexvky[.]cc
h5.fegeh42415[.]top
www.hifly01569[.]top
www.hifly22787[.]top
www.hifly22878[.]top
www.hifly27702[.]top
www.hifly38283[.]top
www.hifly56982[.]top
www.hifly76862[.]top
www.hifly85086[.]top
www.hiflyk47344[.]top
www.hiflyk87327[.]top
Android apk file download URLs:
hxxps://a.digitalsurgeno[.]top/apk/digitalsurge[.]apk
hxxps://a.edgecryptoge[.]top/apk/edgecrypto[.]apk
hxxps://a.etorodes[.]buzz/apk/etoro[.]apk
hxxps://a.exnessge[.]top/apk/exness[.]apk
hxxps://a.ftxano[.]top/apk/ftx[.]apk
hxxps://a.jubinok[.]top/apk/jubi[.]apk
hxxps://a.masteryptge[.]top/apk/masterypto[.]apk
hxxps://a.okcoinge[.]top/apk/opkcoin[.]apk
hxxps://a.olymptradeno[.]top/apk/olymptrade[.]apk
hxxps://a.opkcoinno[.]top/apk/opkcoin[.]apk
hxxps://a.parvestano[.]top/apk/parvesta[.]apk
hxxps://a.timexdes[.]buzz/apk/timex[.]apk
hxxps://a.tycoonsege[.]top/apk/tycoonse[.]apk
Apple Configuration profile download URLs:
hxxps://www.bfefe96b[.]top/files/ios-config/olymptrade[.]mobileconfig
hxxps://www.gniyfe35f[.]xyz/files/ios-config/opkcoinabc[.]mobileconfig
hxxps://www.grgrnt55y[.]top/files/ios-config/parvesta[.]mobileconfig
hxxps://www.hifly69972[.]xyz/files/ios-config/timex[.]mobileconfig
hxxps://www.hiflyf14255[.]top/files/ios-config/tycoonse[.]mobileconfig
hxxps://www.hiflyg41344[.]top/files/ios-config/exness[.]mobileconfig
hxxps://www.hiflyg66779[.]xyz/files/ios-config/etoro123[.]mobileconfig
hxxps://www.hutyfr688[.]top/files/ios-config/okcoin1[.]mobileconfig
hxxps://www.kod89h5[.]top/files/ios-config/ftx[.]mobileconfig
hxxps://www.lkqv215[.]xyz/files/ios-config/masterypto[.]mobileconfig
hxxps://www.niyfe35f[.]xyz/files/ios-config/opkcoinabc[.]mobileconfig
hxxps://www.pade00bg[.]top/files/ios-config/digitalsurge[.]mobileconfig
hxxps://www.pkofe675[.]top/files/ios-config/jubi[.]mobileconfig
hxxps://www.tvao183[.]xyz/files/ios-config/edgecrypto123[.]mobileconfig
If you have been affected by the Counterfeit Trading scams please share the details with us so we can keep trying to get them taken down as we find them. Contact us via [email protected].