How Preemptive Cyber Defence Supports the UK's ACD Strategy
UK organisations are expanding their digital footprint, but reliance on reactive security is leaving them exposed. To align with the NCSC’s Active Cyber Defence (ACD) strategy, teams must shift to preemptive defence.
In response to growing cyber threats, the UK’s National Cyber Security Centre (NCSC) has implemented the Active Cyber Defence (ACD) programme. The ACD’s mandate is clear: to “Protect the majority of people in the UK from the majority of the harm caused by the majority of the cyber-attacks the majority of the time.”
This strategy specifically targets the high-volume commodity attacks, like mass phishing and spoofing, that affect our everyday lives, rather than focusing only on highly sophisticated, targeted attacks. Achieving this level of protection at scale requires a fundamental shift in our defensive strategy.
The Limitations of a Reactive Cyber Defence

Historically, cyber defence has relied heavily on reactive security models that use Indicators of Compromise (IOCs). These traditional indicators typically provide generic, post-breach data about where an attack has been. This data often consists of stale lists that quickly become obsolete as attackers rapidly recycle infrastructure.
Relying solely on IOCs forces security teams into a reactive posture, where they are left struggling to manage complex incidents after the damage has already been done. To meet the NCSC’s aim of scalable protection, the industry must move beyond reaction and adopt a preemptive stance.
A New Approach: Preemptive Cyber Defence

Preemptive cyber defence is an approach focused on a single goal: identifying and preventing attacks before they cause harm.
This is possible because threat actors leave behind more than just IOCs; they leave behavioural fingerprints. The Tactics, Techniques, and Procedures (TTPs) they use to build and manage their infrastructure create a unique, digital DNA.
Our platform is built to analyse this DNA, correlating seemingly isolated indicators to map out the entire attack picture. This moves beyond simple pattern-matching, allowing us to connect all the pieces of a campaign and identify malicious infrastructure the moment it appears online, long before it’s fully weaponised.
Achieving preemptive defence requires two things:
- Massive-Scale Data Collection: Continuously mapping and actively resolving DNS across the entire global IPv4 and IPv6 space to reveal new infrastructure the moment it comes online.
- TTP-Led Behavioural Tracking: Analysing that data to spot the “fingerprints” of malicious activity, such as combining recurring patterns in domains, infrastructure, and operational behavior to track Scattered Spider.
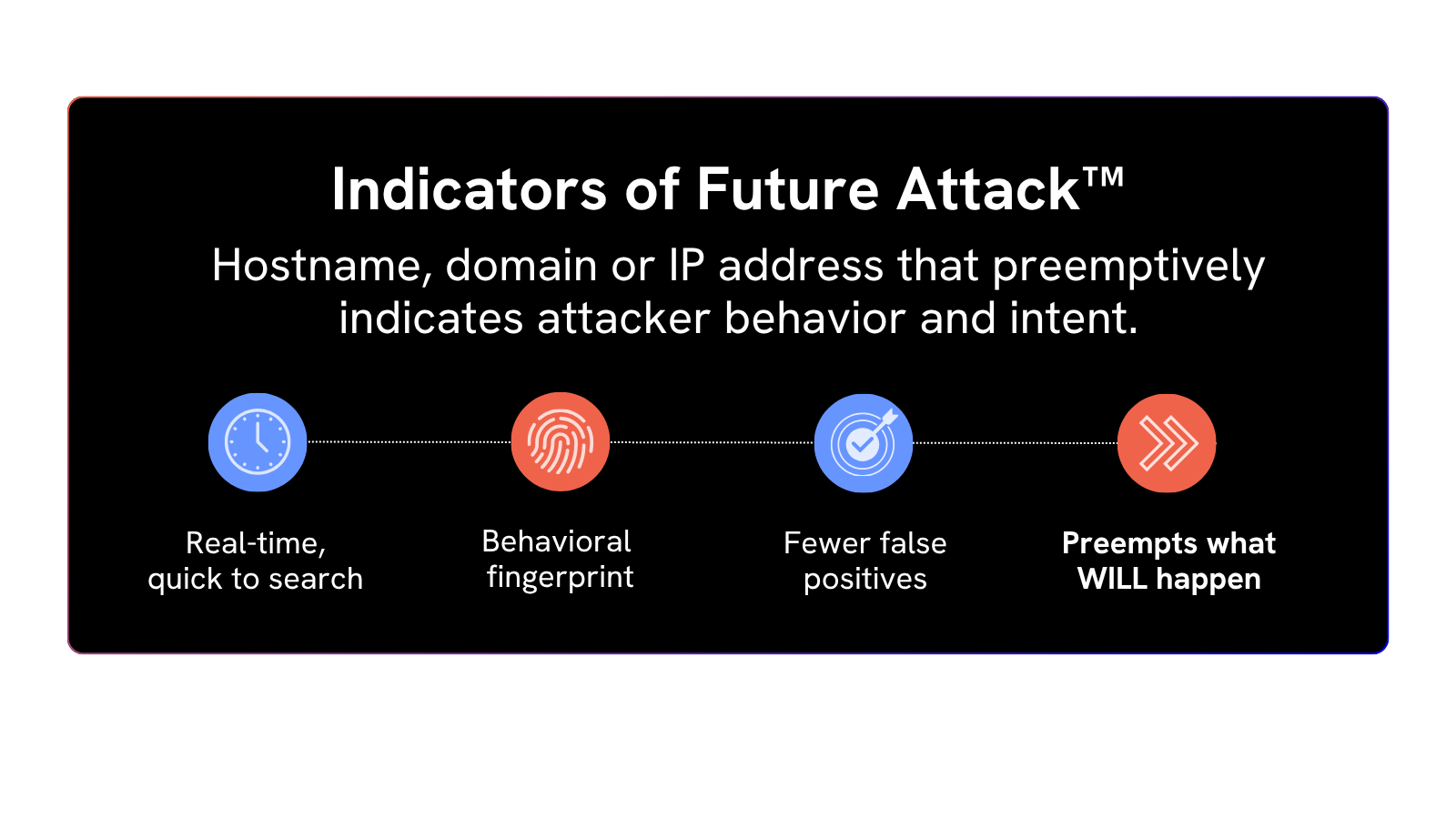
This proactive process tracks and blocks adversary infrastructure during its staging phase. It generates high-fidelity Indicators of Future Attack (IOFA)™: proactive IP, domain, and URL data that allow security teams to identify, track, and ultimately block adversary infrastructure before it is even weaponised. This approach uncovers novel infrastructure yet to be reported.
Turning ACD Strategy into Tactical Reality
ACD and preemptive cyber defence are two sides of the same coin: ACD establishes the strategic mandate for scalable protection, while a preemptive approach to defence provides the technical capability to achieve it by neutralising threats at their source.
Achieving preemptive detection at scale isn’t about having more data; it’s about better data. This capability requires a foundation of Data Independence. By collecting 100% of our own data, we eliminate the noise and latency of third-party feeds and ensure a uniquely accurate and reliable view of global infrastructure.
By leveraging this pre-attack behavioural fingerprinting and the resulting infrastructure data, security teams can automate the detection and blocking of the very mass-volume threats the ACD programme is designed to stop.
This approach directly targets the high-volume attacks central to the ACD’s mission:
- Phishing and spoofing: This method identifies brand impersonation attacks, including typo-squatted domains, before they are deployed. For example, analysts can track phishing campaigns targeting UK banks while they are still being set up.
- Malvertising: It exposes malicious infrastructure hidden within online ads, a key vector for commodity attacks, allowing it to be blocked before ads are served.
- Mass scams: Silent Push data is essential for uncovering large-scale criminal operations. A key example is the FUNNULL CDN, the hub of the Triad Nexus financial fraud network, which hid malicious activity within legitimate cloud services.
- Infrastructure Scale: Over 200,000 hostnames were proxied through FUNNULL in just a few weeks.
- Cloud IP Usage: FUNNULL rented more than 1,200 Amazon IPs and nearly 200 Microsoft IPs.
- Malicious Activities: Supported retail phishing, money laundering, and fraudulent investment platforms targeting global victims.
- This case demonstrates Silent Push’s ability to track hidden infrastructure, reveal novel TTPs, and deliver actionable intelligence to disrupt large-scale scams.
- This case demonstrates Silent Push’s ability to track hidden infrastructure, reveal novel TTPs, and deliver actionable intelligence to disrupt large-scale scams.
Tracking and blocking this infrastructure before the malicious texts are sent is a perfect example of preemptive defence at scale. The focus on disrupting an attack at its origin (the infrastructure), turns the ACD’s strategic mandate into measurable protection against high-volume threats.
Empowering UK Cyber Resilience
The Silent Push Enterprise Edition operationalises preemptive defence at scale, feeding high-fidelity infrastructure data directly into existing security stacks (SIEM, SOAR, firewalls) for automated blocking.
By leveraging data that enables preemptive cyber defense, from community research to enterprise-grade automation, the UK can build a truly proactive digital defence. This stance aligns perfectly with the ACD’s goal, building national resilience by stopping threats before they strike.
See how automated, preemptive cyber defence can protect your organisation. Get a demo of the Silent Push Enterprise Edition today.

