How threat actors are exploiting the collapse of Silicon Valley Bank: A case study in financial spoofing

On Friday, March 10th, 2023, Silicon Valley Bank collapsed. The financial institution’s unexpected failure spread chaos amongst thousands of businesses, including tech companies, VCs, and other banks.
With the failure comes a massive opportunity for crime groups to take advantage of vulnerable companies seeking out information and trying get access to their funds, creating an additional existential threat for all those affected.
Background
The collateral damage caused by SVB’s collapse is most noticeable in the form of countless clients trying to desperately relocate their funds. However, third-party companies with outstanding payments from SVB customers or stakeholders are equally affected, and need to overcome liquidity bottlenecks to pay their bills and stay afloat.
In short, the financial reality of thousands of companies is currently dominated by uncertainty and desperate urgency.
The door for fraud is wide open. Our Threat Analysts are already tracking malicious infrastructure that’s been set up to take advantage of the situation. The risk applies to anyone affiliated with SVB and its clients.
Attack Vectors
Bank and invoice frauds are some of the easiest ways for crime groups to gain quick wins.
Threat actors constantly monitor for major events such as the SVB crash, and exploit the fact that thousands of organizations and individuals need to communicate their banking credentials this week to secure their funds and process payments.
SVB Spoofing
The most obvious targets are those directly affected by SVB’s collapse, i.e. those holding deposits with the bank.
SVB customers need to check in on their funds and most likely transfer them to different accounts outside of SVB.
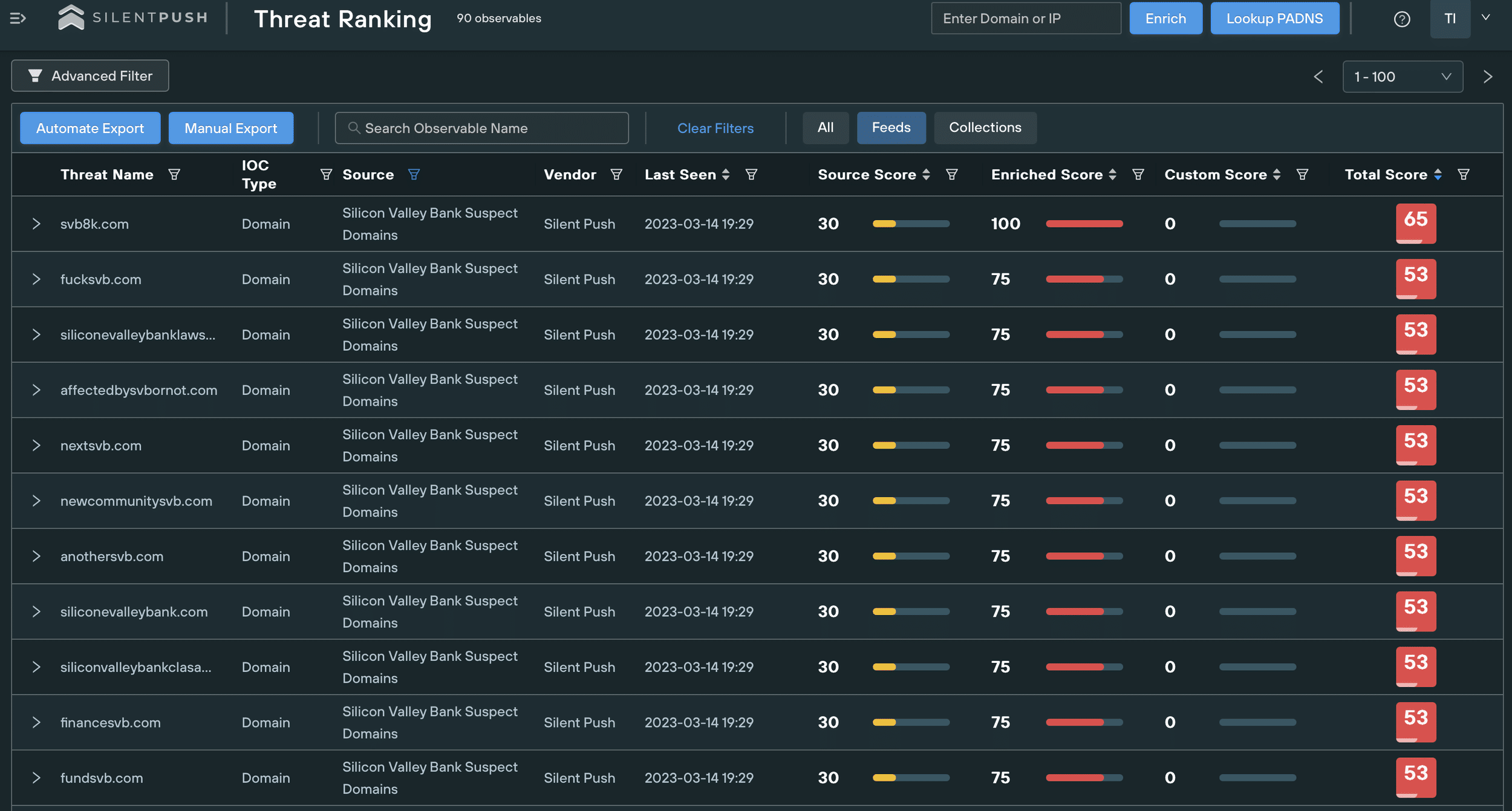
We’re already tracking a huge spike in domains potentially imitating SVB, many of which we expect to be launching malicious content soon:
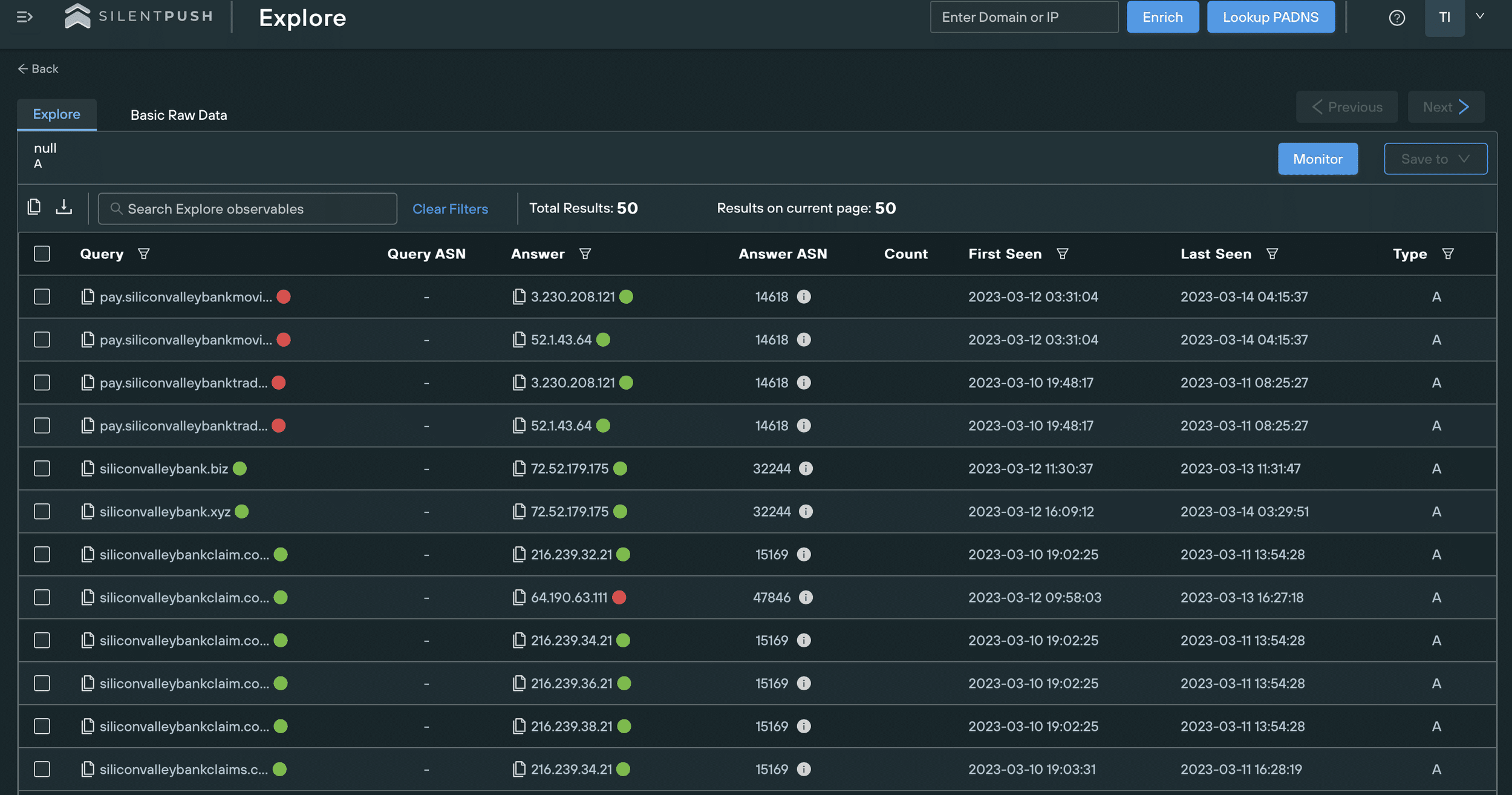
Threat actors can use the typosquatted SVB domains to redirect traffic to their infrastructure and add legitimacy to it. We’re also expecting to see spoofing pages imitating SVB’s branding and digital presence to entice users to interact with fake login portals designed to harvest credentials.
We extensively cover the TTPs of brand impersonation here.
We’re expecting phishing emails and messages imitating SVB that target the bank’s clients. These attacks will use urgent messaging and aggressive CTAs to pressure recipients to share private information, or visit fraudulent domains.
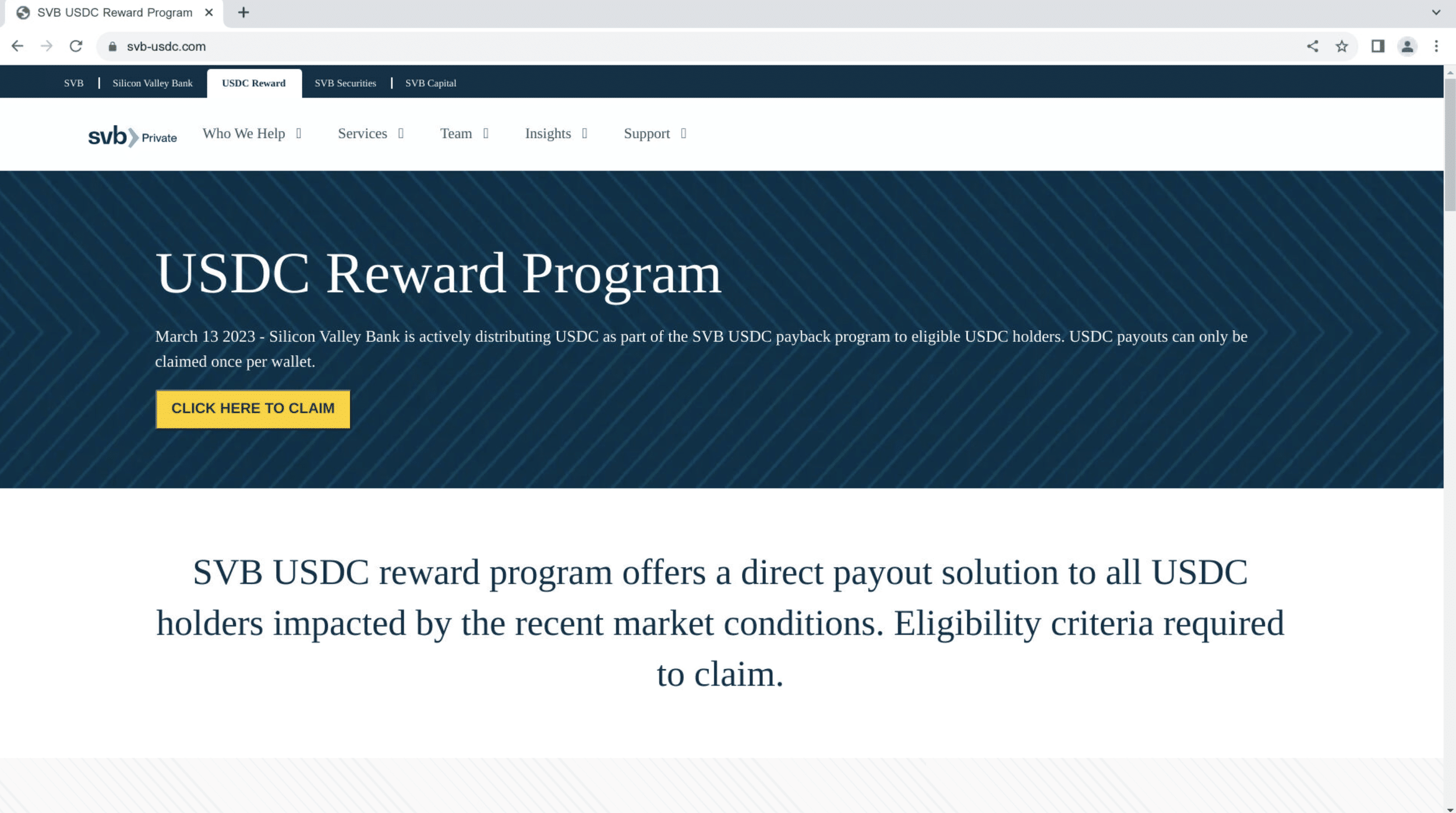
Case Study – svb-usdc[.]com
We’ve marked the typosquatted domain svb-usdc[.]com as an active threat.
The domain is part of a cryptocurrency scam that poses as a USDC reward/compensation program for SVB clients.
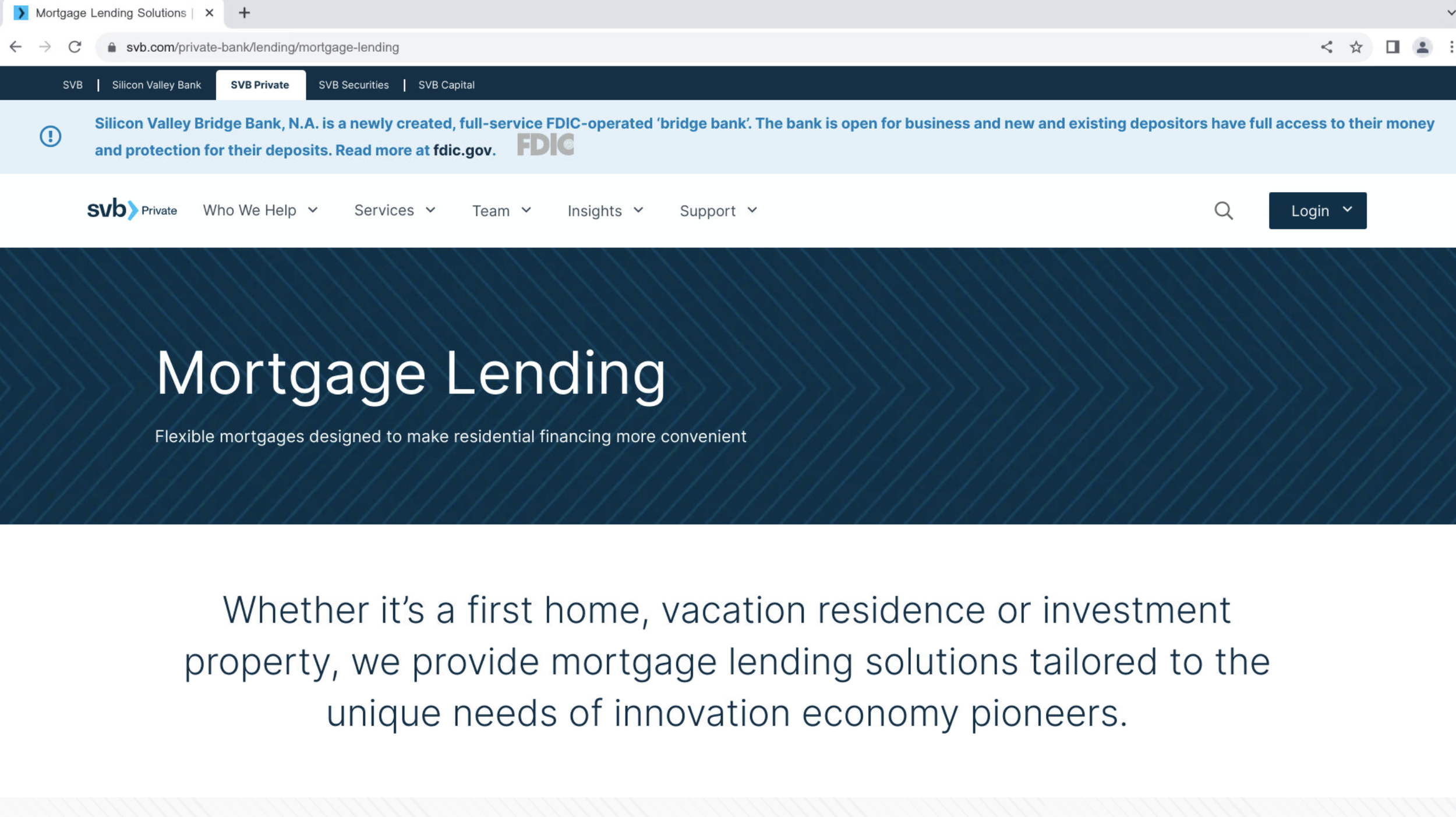
Most of the phishing page’s content is copied from svb[.]com/private-bank/lending/mortgage-lending:
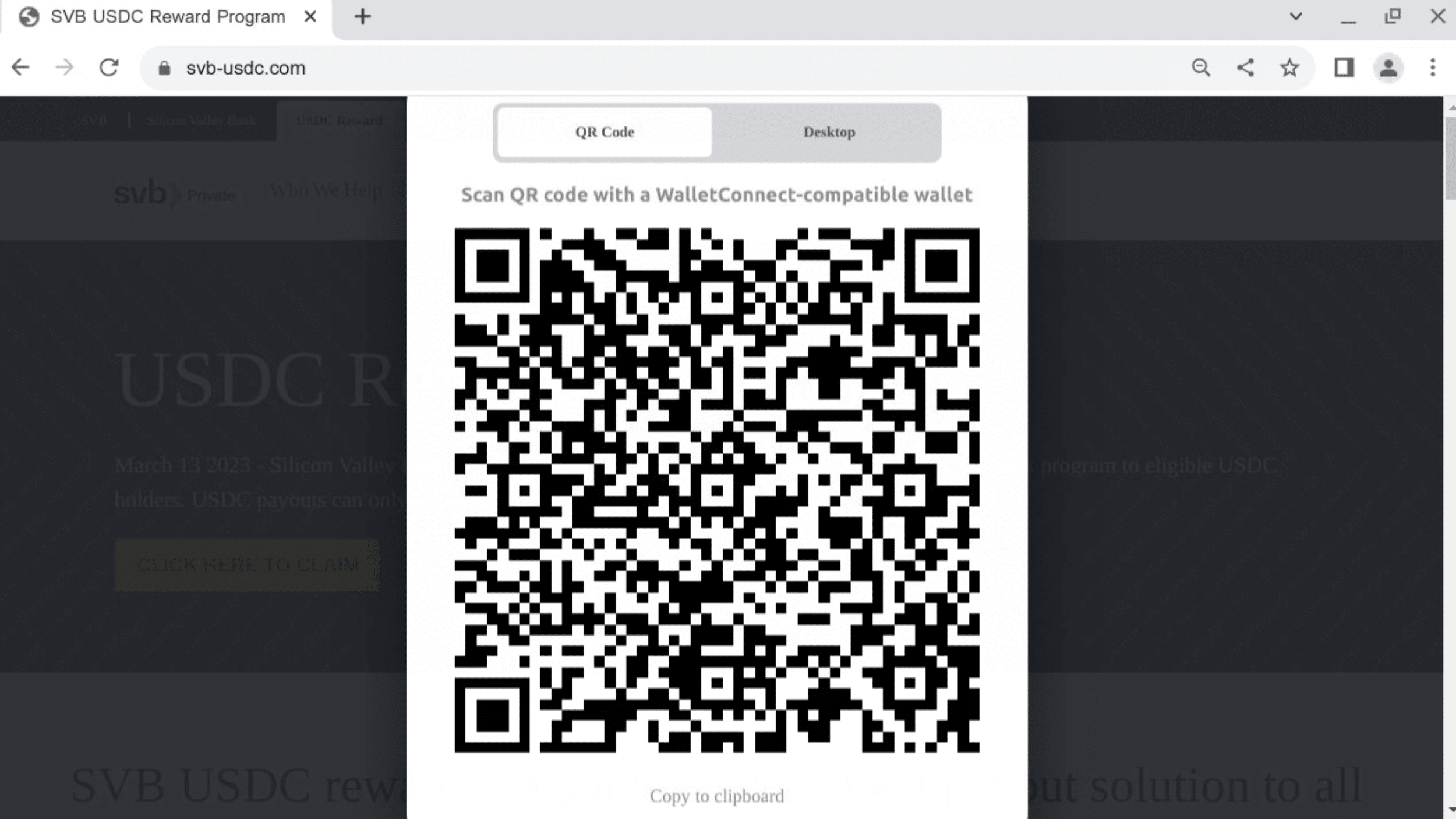
The button added to the fraudulent page redirects users to a cryptocurrency wallet via WalletConnect:
Case Study – pay.fsvb[.]net
We’ve also discovered malicious SVB-typosquatted domains related to pay.fsvb[.]net. They are likely part of a phishing campaign aimed at misappropriating users’ payment details.
The domains are registered on GoDaddy and make use of the platform’s online payment option:
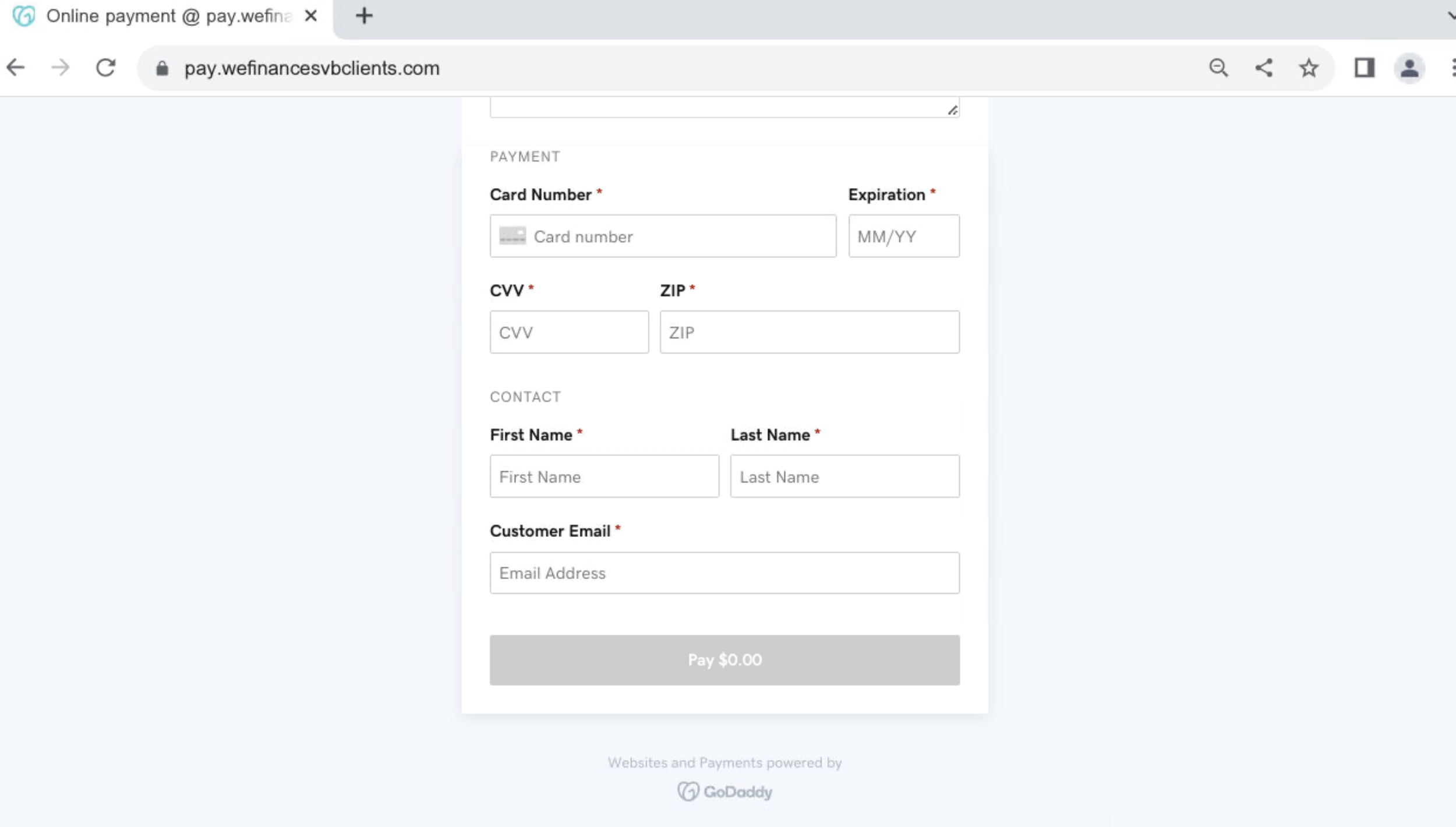
Fake refunds
Many individuals and organizations not directly affiliated with SVB are still affected by the crash, and are now waiting for potential pay-backs, refunds, and insurance claims.
We’re also seeing companies struggling with liquidity bottlenecks, meaning entire staff, as well as third-party clients, are dealing with with frozen salary and services payments.
Threat actors have the opportunity to imitate a variety of organizations and institutions offering supposed financial support, aid, and compensation. As above, this can be either achieved through simple typosquatting or combined with brand spoofing and phishing campaigns.
It is also likely for unaffected individuals to be targeted under the pretext that they are, in fact, eligible for monetary compensation.
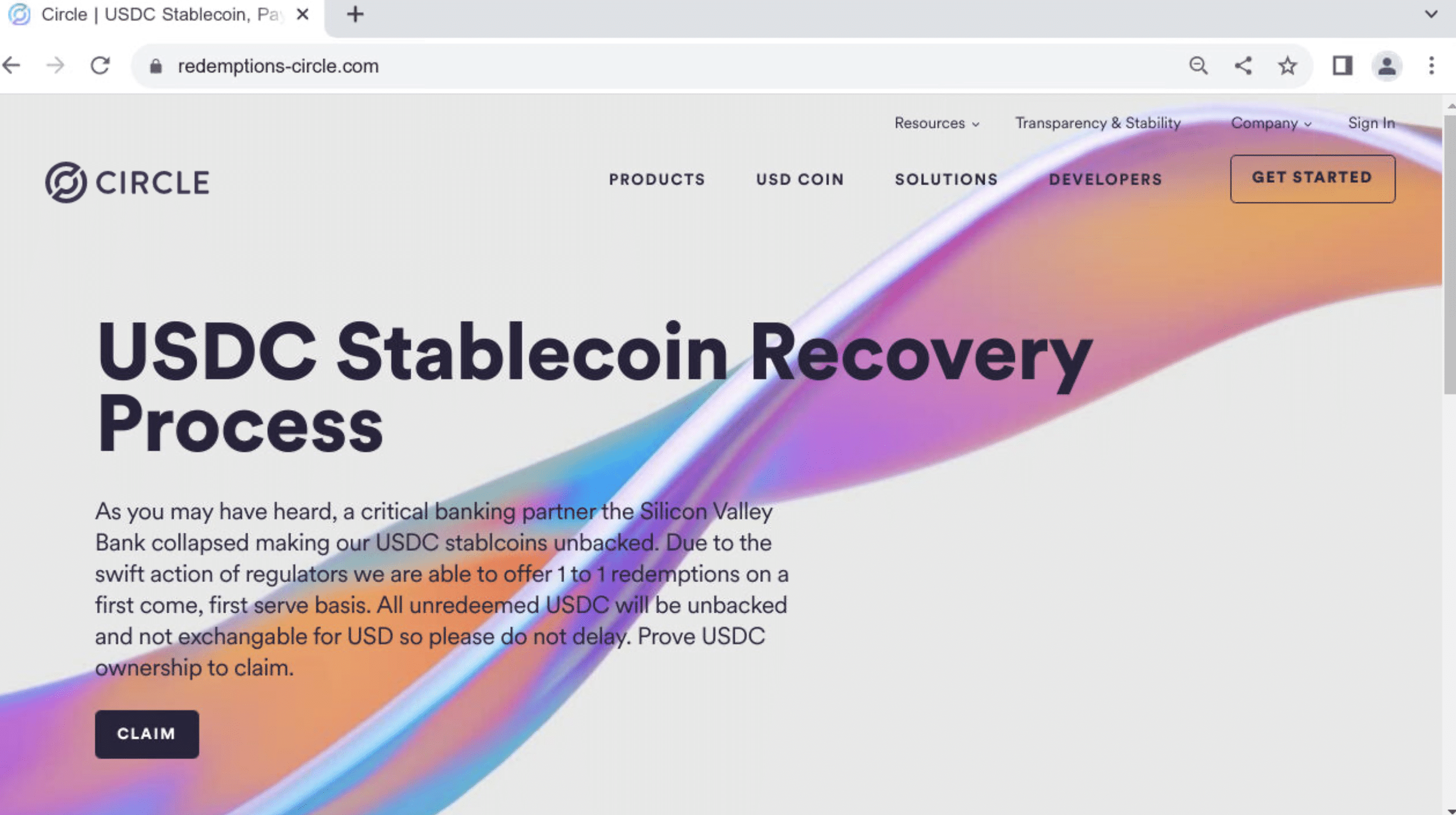
Case Study – redemptions-circle[.]com
We uncovered additional infrastructure associated with the cryptocurrency fraud mentioned above. The related domains impersonate Circle, and were registered after the company announced they had $3.3bn of their USDC cash reserves with SVB.
The phishing pages urge users to connect their crypto wallets to reclaim USDC:
We’ve also discovered pages displaying SVB’s logo in combination with Circle’s branding.
Invoice fraud & requests to change payment information
Invoice fraud consists of threat actors posing as a company’s supplier and requesting payment on their behalf.
This is often combined with an explanation as to why the funds need to be transferred to a different bank account than was previously used.
Following SVB’s failure, thousands of companies will have to forcefully change banks, and thus thousands of their clients can expect updated invoices and payment requests.
Some may still be unsure as to whether or not their suppliers are affected by the SVB collapse, and will be awaiting updates.
Threat actors will use this opportunity to contact companies and request payments to new recipient accounts, using the excuse that payments via SVB are now impossible.
Additional factors
Lack of two-factor authentication
SVB does not enforce 2FA, making both itself and its deposit holders far more vulnerable to fraud and security breaches.
Once threat actors are in receipt of SVB’s customers’ details, a lack of 2FA means that they do not have to overcome additional security hurdles to gain access to the accounts in question.
Not enforcing 2FA also makes it easier for threat actors to pass off fake login pages as legitimate.
Unusual legitimate behavior mixed with genuine threats
While it is possible for banks (and their clients) to notice suspicious transfers and malicious activity, the environment surrounding SVB almost exclusively encourages irregular account activity.
The current panic will make it easy for threat actors to go unnoticed long before the dust has settled.
Managing the risk
The threat landscape caused by SVBs collapse is extremely aggressive and has the potential to adversley affect countless institutions and organizations.
We’re dedicating our resources to offer real-time insights into the threats and to help companies stay ahead of potential attacks.
Stay informed about SVB imitators
We’ve created an SVB spoofing feed that scans global DNS infrastructure for signs of threat actors imitating the bank.
The feed is automatically updated, and contains all recently registered domains relating to SVB.
Not all domains listed here are malicious or have not yet had malicious activity hosted on them.
Since we expect a spike in fraudulent campaigns in the coming weeks, we’re closely monitoring all associated assets and we’ll flag serious threats as and when they appear.
Protect yourself from impersonation
We’re offering our free typosquatting tool for companies to detect domains and email communication falsely created on their behalf.
SVB’s crash creates an opportunity for impersonation campaigns and attacks targeting a vast number of brands and organizations. We’re encouraging particular awareness of invoice fraud committed in your name.
Impersonation attempts are a liability to you and your assets and can cause lasting reputation damage. Detecting malicious infrastructure before it can facilitate an attack is the best way to keep your organization safe.
Get access to our free community app and typosquatting tool here.
Indicators of Compromise
Below is a categorized list of the IoCs discussed in this article. Please note that the actual number of IoCs is far greater.
We track several malicious groups and threats. Comprehensive lists of real-time IoCs relating to SVB bank and others are available with a Silent Push Enterprise subscription.
Enterprise users can search for IoCs related to this campaign using the tag sp-blog-2023-03-15.
Domains impersonating SVB
svb-usdc[.]com
svb-usdc[.]net
pay.fsvb[.]net
pay.nextsvb[.]com
pay.siliconvalleybankmovie[.]com
pay.siliconvalleybanktradeclaim[.]com
pay.svbbankruptcy[.]com
pay.svbdeposits[.]com
pay.svbrecovery[.]com
pay.wefinancesvbclients[.]com
Domains impersonating SVB and Circle
circle-reserve[.]com
circle-usdc[.]net
claimcircle[.]net
reserve-circle[.]com
usdc-circle[.]net
Domains impersonating Circle
airdrops-circle[.]com
allocation-circle[.]com
circle-bonus[.]com
circle-gifts[.]co
circle-reserves[.]com
circle-reward[.]com
circle-usdcoin[.]co
circle-usdcoin[.]com
circle[.]tips
circlecustody[.]org
circleusdcoin[.]com
circleusdcswap[.]com
claim-circle[.]org
claimingcircle[.]com
claims-circle[.]xyz
joinus-circle[.]com
redeemable-circle[.]com
redeemed-circle[.]com
redemptions-circle[.]com

