"Not what the doctor ordered": Silent Push maps out illegal pharmacy infrastructure. 2,500+ active IOFA domains and dedicated IPs discovered, primarily served via US-based hosts.

Executive summary
Building on the work of the DEA, Silent Push Threat Analysts have used content similarity and page metadata scans to reveal approximately 2,500 unique Indicator Of Future Attack (IOFA) domains and dedicated IPs actively hosting illegal pharmacy content.
The websites are actively engaged in numerous criminal acts, including the sale of illegal drugs and Counterfeit or Falsified Medication (CFM).
Domains are largely hosted via US-based ASNs and dedicated IPs, using Dynadot and Russian nameservers.
Silent Push Enterprise users have access to two dedicated IOFA Feeds containing all the true positive domains and IPs we gathered during our research.
For operational security reasons, we are unable to share the exact specifics of each query and pivot utilized. Silent Push Enterprise customers have access to a dedicated Illegal Pharmacies TLP Amber report, which contains all the relevant data types and pivot points we used to track the CFM infrastructure referenced in this blog.
Sign-up to Community Edition
Silent Push Community Edition is a free threat hunting, DNS and scanning toolkit that contains all the queries and lookups we used to locate and traverse the infrastructure included in this blog.
Sign-up here.
Background
According to a 2017 Frontiers in Pharmacology report, Counterfeit and Falsified Medicine can broadly be described as medicines that “contain substandard active ingredients, which are low quality and/or an incorrect amount, either too high or too low, and have not been properly evaluated by authorities in terms of quality, safety, and efficacy.”
Illegal online pharmacies that sell CFMs have existed for well over a decade. As far back as 2012, the WHO estimated that illegal prescription drug sales reached $431 billion.
During the Coronavirus pandemic, the number of illegal pharmacies dramatically increased. As concerned citizens searched for medicine online while they were in their homes during lockdown, bot spammers began polluting SEO results to redirect unsuspecting users to shady pharmacy sites.
More recently, on October 4, 2024, the DEA issued a Public Safety Alert that warned about the dangers of illegal online pharmacies, following the death of a US-based woman who ingested what she believed to be a oxycodone pill, but was in fact fentanyl.
Initial intelligence gathering
As part of the above investigation, the DEA published details of 9 fake online pharmacies:
- www.curecog[.]com
- www.pharmacystoresonline[.]com
- www.careonlinestore[.]com
- www.yourphamacy[.]online
- www.md724[.]com
- www.greenleafdispensarystore[.]com
- www.whatishydrocodone.weebly[.]com
- www.orderpainkillersonline[.]com
- www.usamedstores[.]com
Performing a Google search for “shop + cheap viagra” returns a list of templated domains that rank due to blackhat SEO tactics, with content templates that, whilst similar, contain subtle differences.
Here’s a few examples:
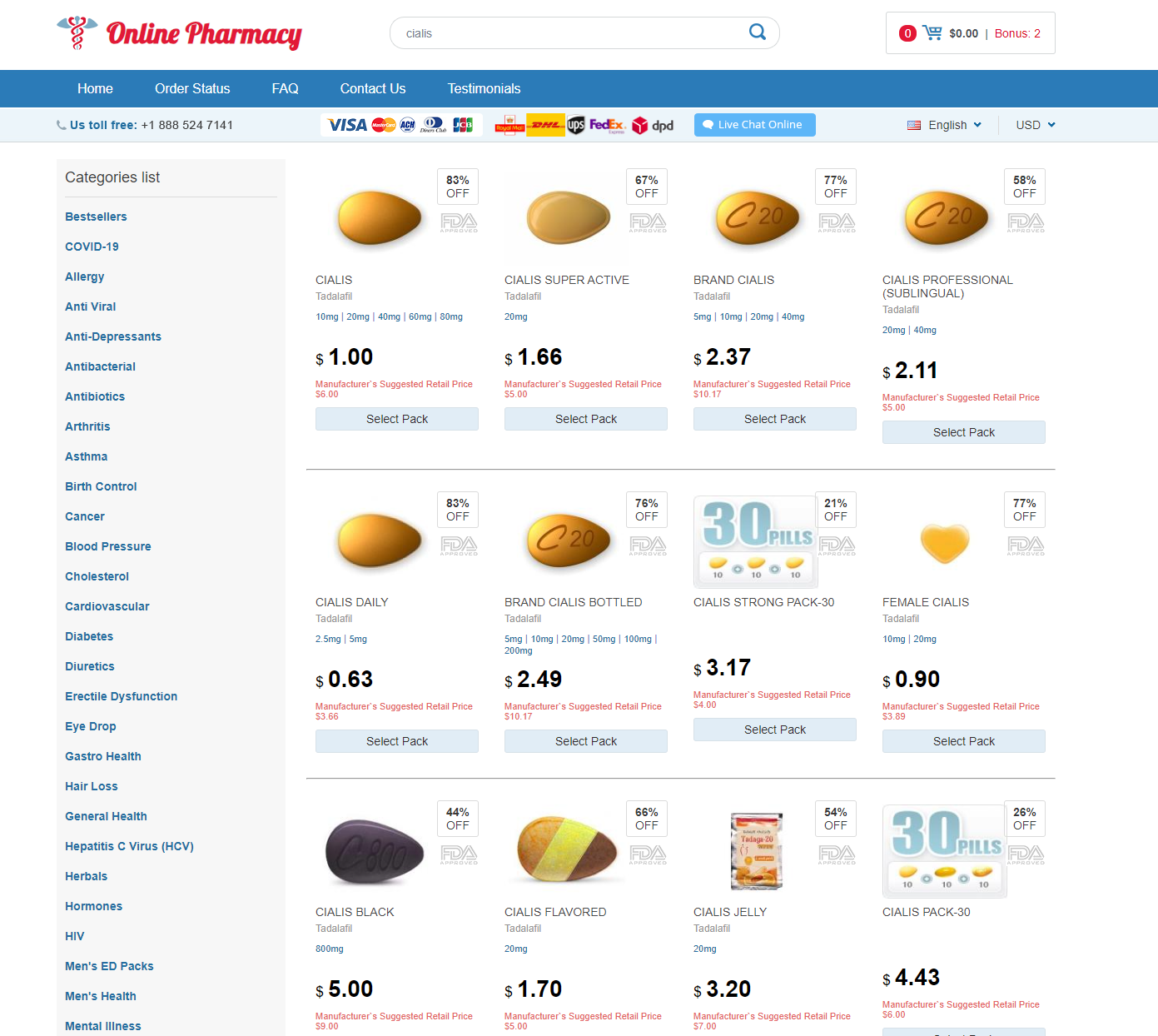
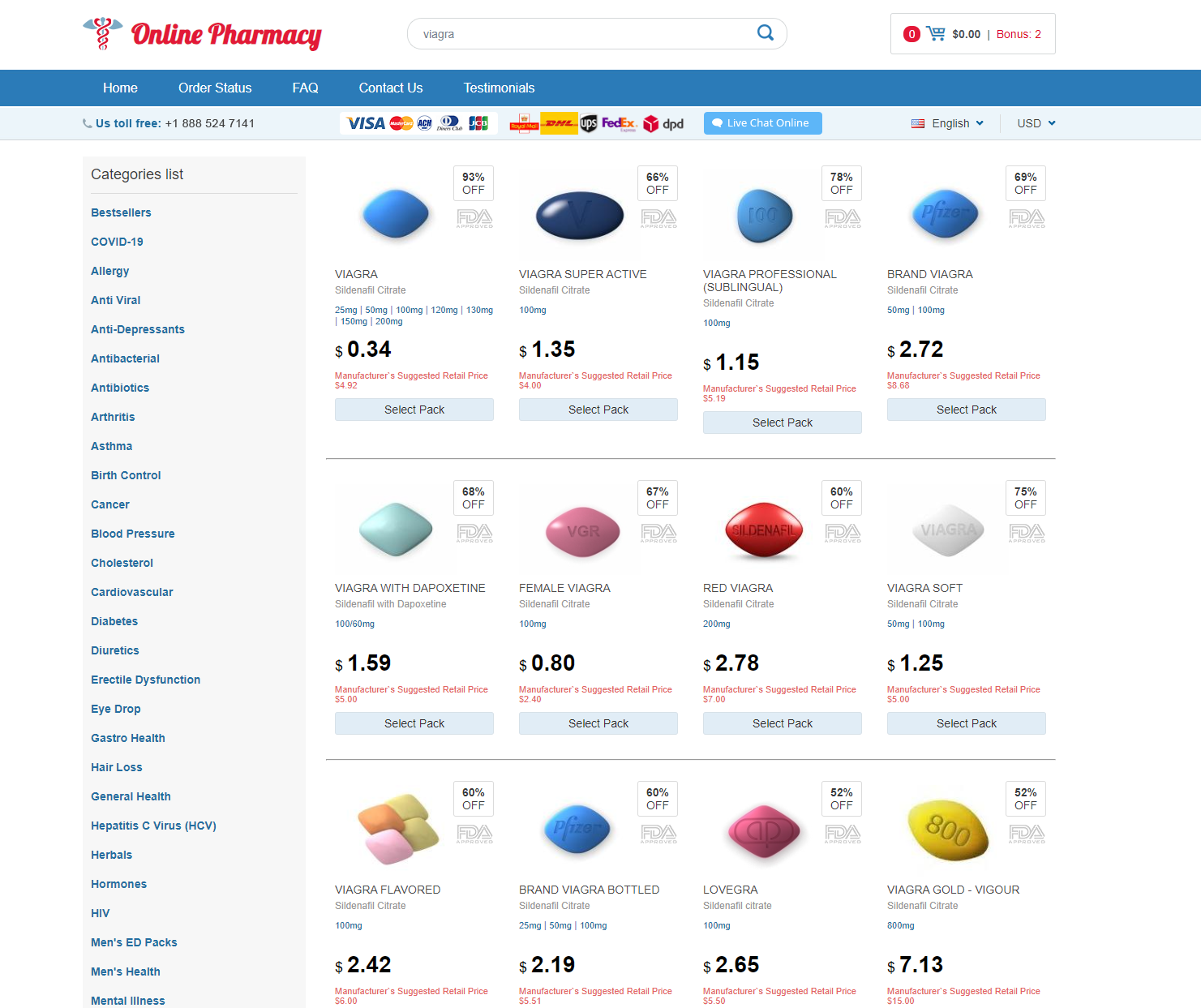
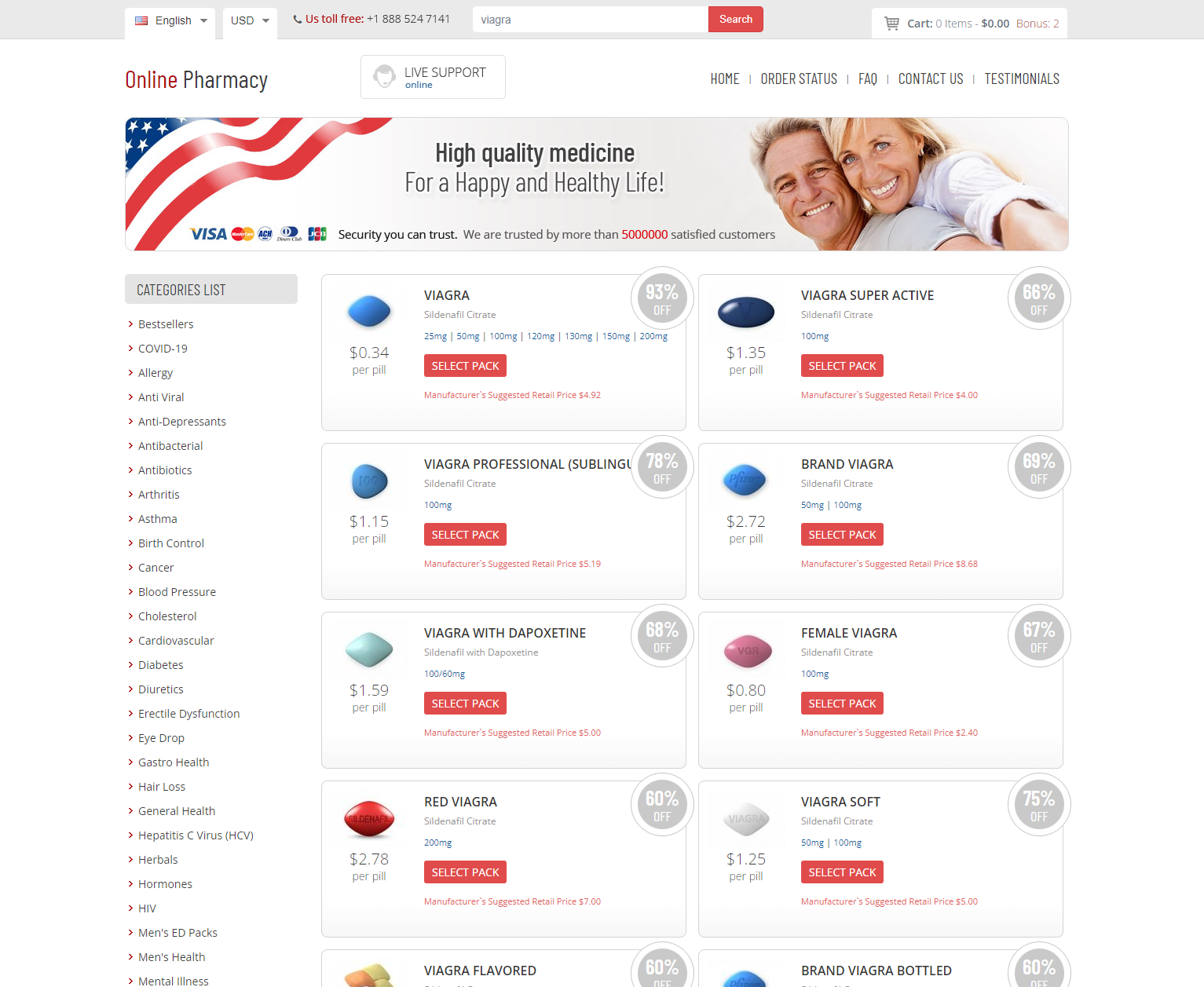
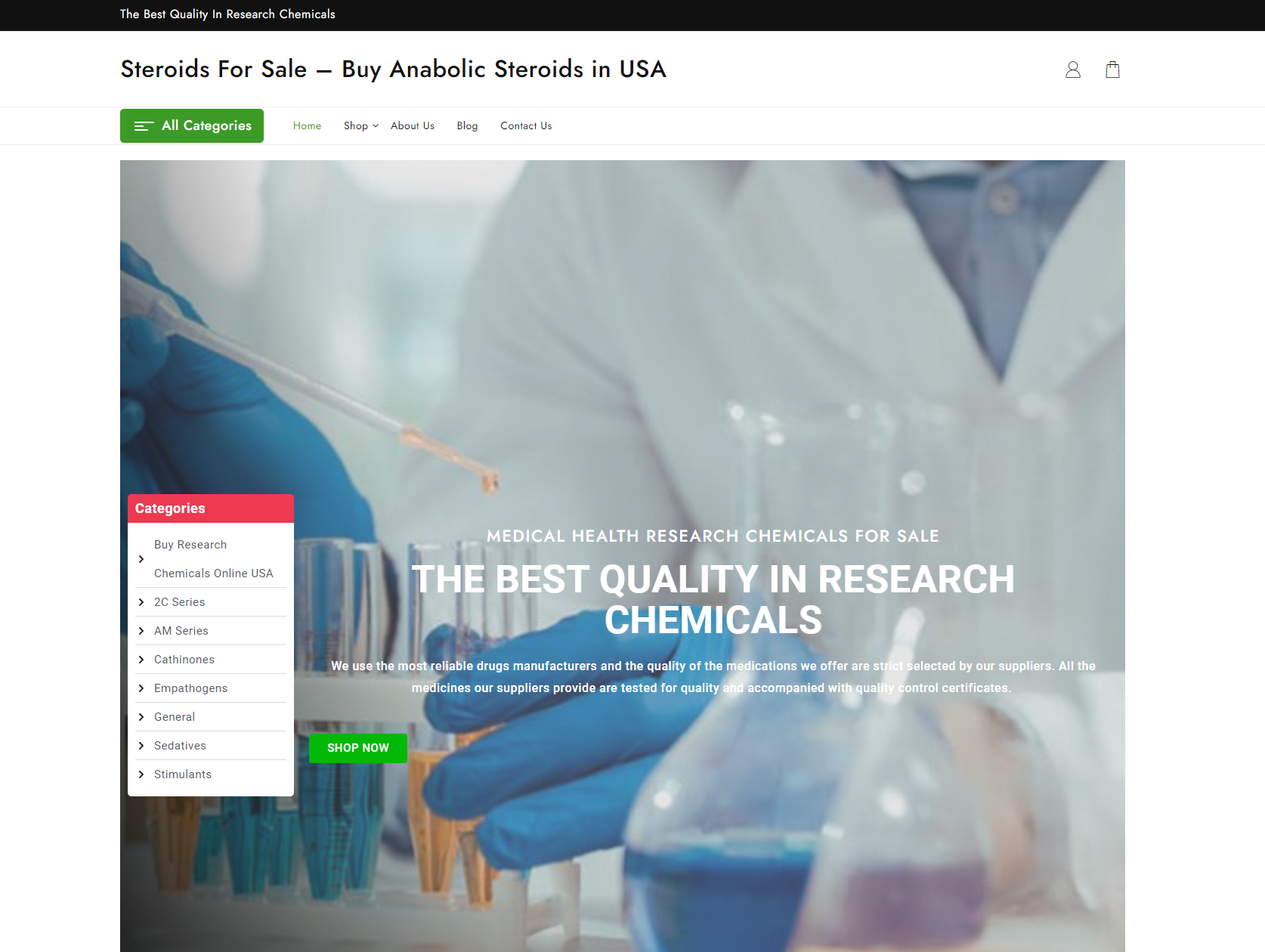
Pivot 1 – Web content similarity search
After analyzing the domains returned, our team identified several key on-page elements that we were able to use as parameters in a Silent Push Web Scanner query, in order to reveal linked infrastructure.
Silent Push Web Scanner outputs data on all public-facing and darkweb sites across 100+ categories, including body content hashes, header values, embedded code configurations, and certificate data.
Our scans returned an initial dataset of 1,000+ domains and IPs, containing 100% true positive results of websites engaged in the sale of CFMs and illegal drugs.
Here’s a sample of what we discovered. As you can see, the websites are re-using content templates in line with previously observed TTPs, indicating an infrastructural link between a majority of the domains.

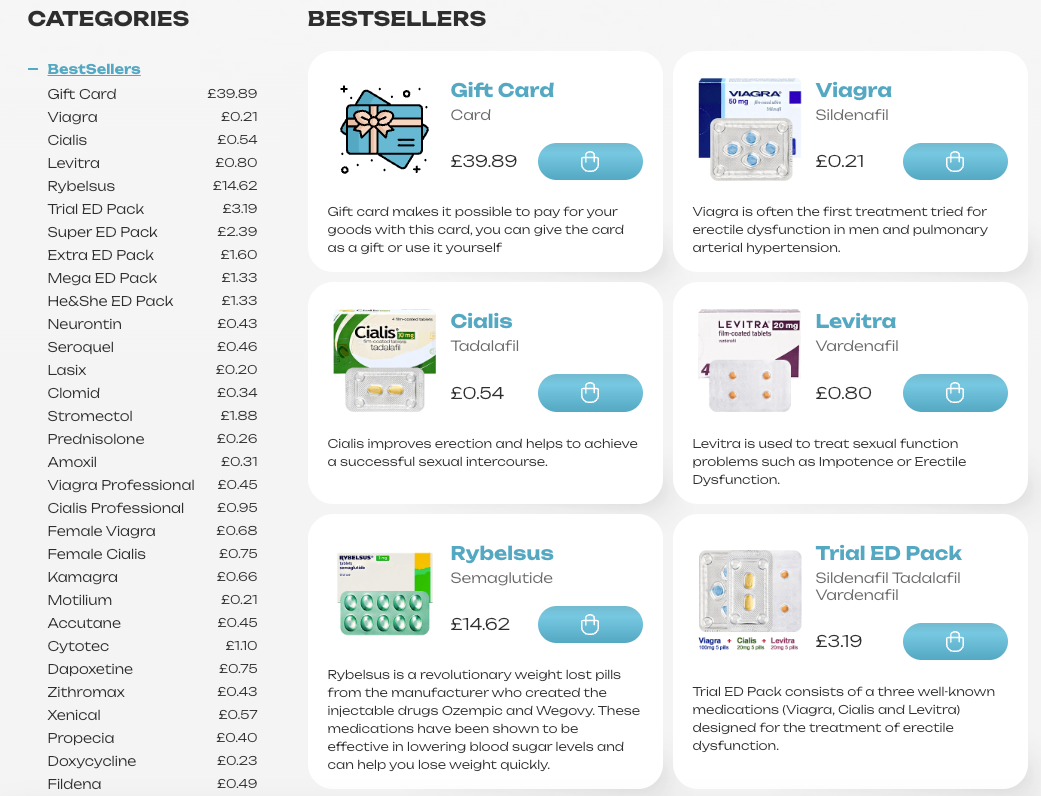
Pivot 2 – Proprietary scans
Once we knew that our datasets contained true positive linked domains, we used further Silent Push Web Scanner queries to create a proprietary behavioral fingerprint made up of back-end web infrastructure elements, that revealed yet more associated CFM websites.
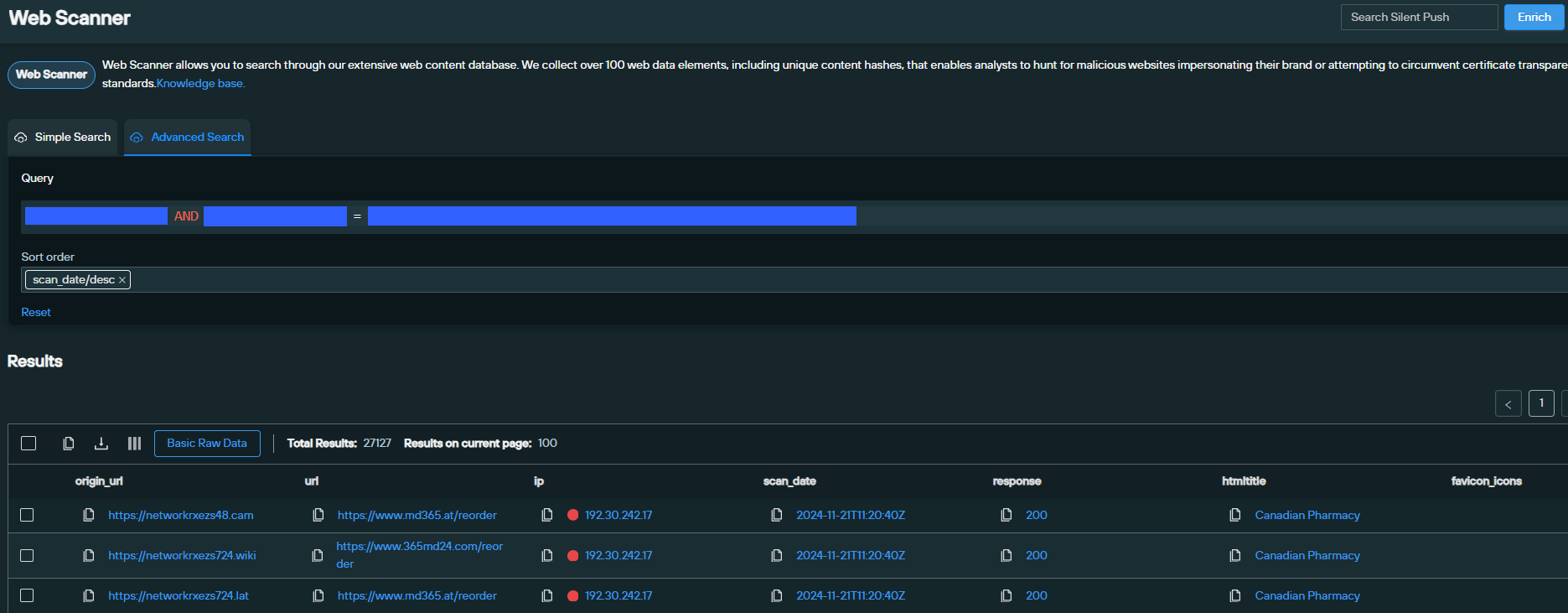
This secondary pivot led to the discovery of almost 4,000 unique domains and dedicated IPs that are all part of the same active CFM campaign. Not all were active.
A large number of the dedicated IPs we discovered map to additional domains, as well as rendering a website.
Here’s a sample:
- 146.70.87[.]241
- 192.30.242[.]17
- 23.236.66[.]178
- 154.12.59[.]150
- 89.117.226[.]128
- 162.253.153[.]78
- 206.168.240[.]120
- 146.70.87[.]241
- 23.236.66.213
- 216.73.156.103
“Illegal Online Pharmacies” IOFA Feed analysis
We’ve collected all the true positive CFM domains into two dedicated Indicator Of Future Attack (IOFA) feeds, available to Enterprise users.
As of writing, the feeds contain approximately 2,500 domain and IP IOFAs.
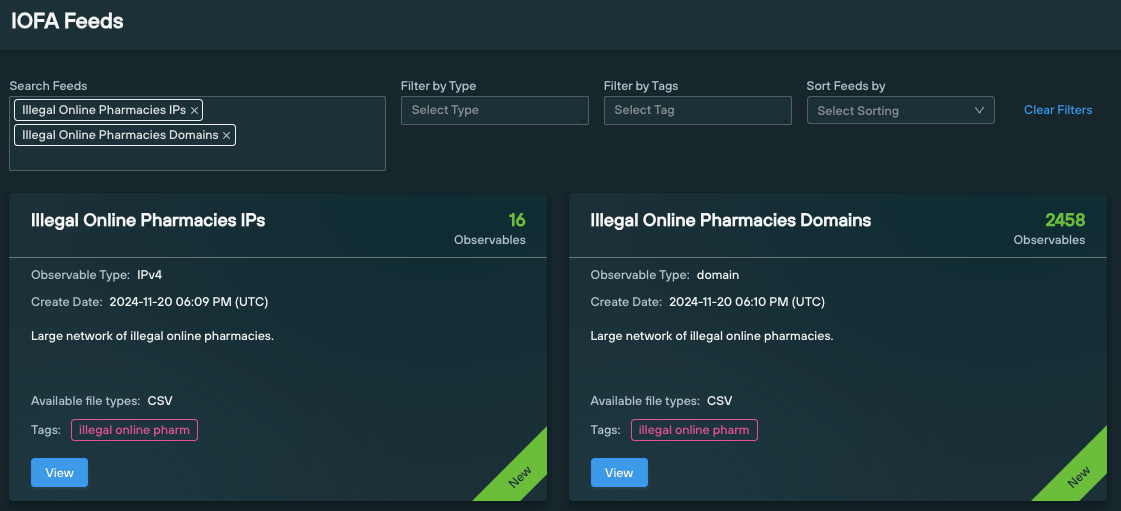
Enterprise users can ingest IOFA Feed data into their security stack to inform their detection protocols, or use enriched feed data to traverse known and unknown infrastructure, using the Silent Push API and Console.
Infrastructure deep dive
Clicking the “Feed Analysis” button displays numerous additional metrics associated with the data type contained within the feed.
In the “Illegal Online Pharmacies – Domain” feed, we can see that the majority of nameservers are hosted via Dynadot on ns1.dyna-ns[.]net and ns2.dyna-ns[.]net, with the remainder served by a mixture of primarily Russian nameservers.
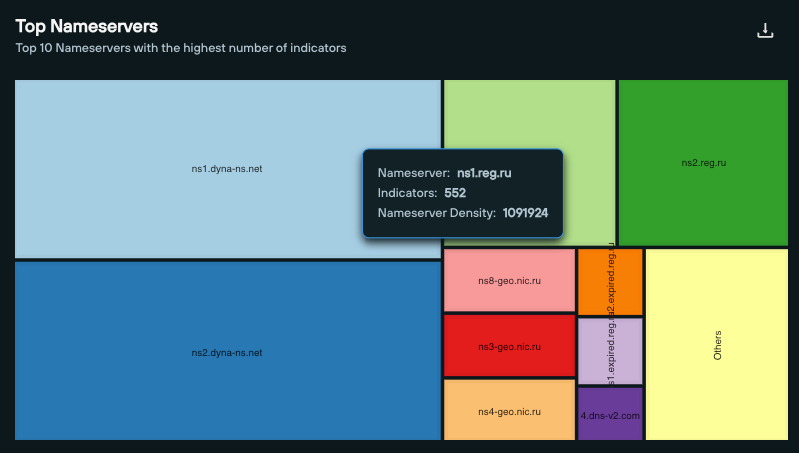
From the Feed Analytics screen, we can also see that that the majority of CFM domains are hosted on AS6134 (XNET LLC) and AS29802 (HIVELOCITY) – both of which are US-based.
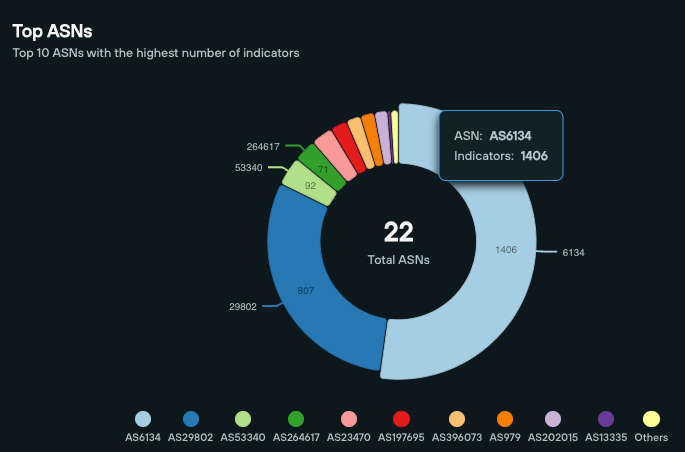
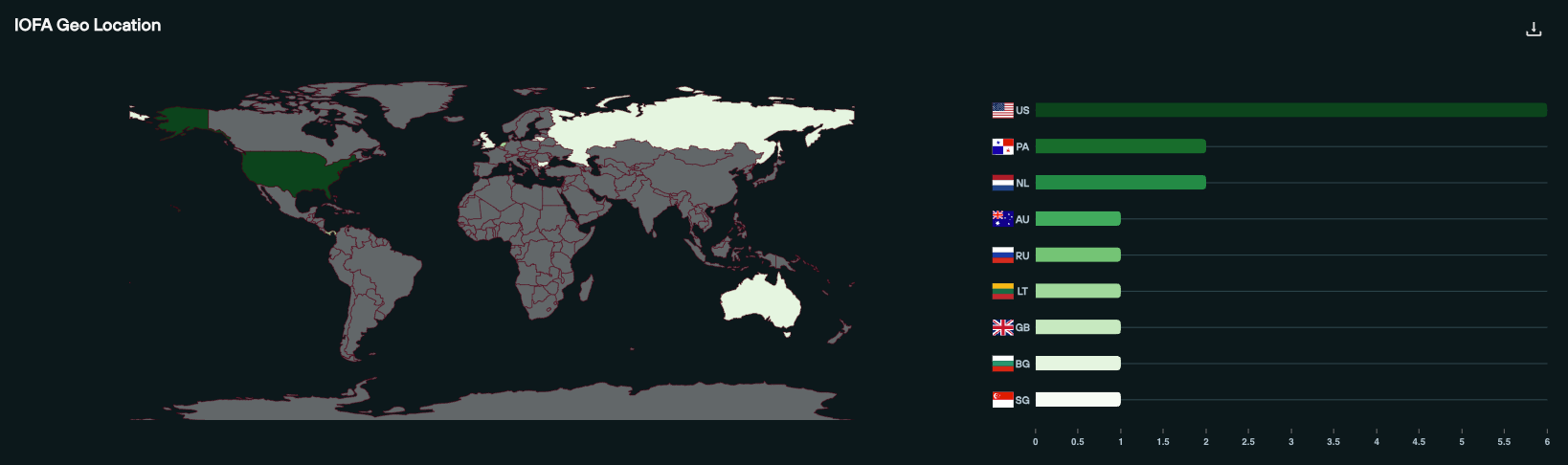
Pivoting through the IP feed, we can see that the geographic spread places the majority of dedicated IPs in the US:
Law enforcement seizure
It’s apparent that law enforcement authorities are aware of a certain number of domains located on the above cluster, but not all.
Several domains – such as allcentercenter365[.]ru (which redirects to www.724pharmonline[.]at) on 192.30.242[.]17 – have been seized through joint action between U.S. and European enforcement agencies:

Given that our scans revealed active domains sharing the same infrastructure, content elements and TTPs as seized domains, it’s clear that law enforcement are yet to map out the full extent of the campaign.
We’ll be passing our research on to all the relevant authorities. Law enforcement agencies can reach out to us at [email protected] for collaboration.
IOFA sample
- 146.70.87[.]241
- 192.30.242[.]17
- 23.236.66[.]178
- 154.12.59[.]150
- 89.117.226[.]128
- 162.253.153[.]78
- 206.168.240[.]120
- 146.70.87[.]241
- 23.236.66.213
- 216.73.156.103
- 724pharmonline[.]at
- 5-pharmacy[.]com
- 10-drugs[.]com
- biosteroitschem[.]com
- best-shop-it[.]com
- safe-shop-it[.]com
- rx-qualityshop[.]com

