A penetration tester was asked to try the Silent Push service to see how it could help him and his team to get their work done quicker. This is written in the tester’s own words and only uses the Silent Push ‘DNS Explore’ feature.
Reconnaissance
Reconnaissance is performed to gain as much information on the target before beginning the penetration testing. ‘Recon’ is an essential element of any penetration testing. Recon on a target can be done in two ways: passive and active reconnaissance.
During the recon process researchers try to collect information about the subdomains associated with the target and their respective IP address. Most applications today are protected using WAFs and CDNs and it is often challenging to identify the real IP address associated with an application. That is where the subdomains associated with the application help researchers get more information about the main application and expand the attack surface.
The Silent Push application can be used for passive reconnaissance quickly.
Case Study:
Domain : magicbricks[.]com
For the past few years, the tester has been testing web applications and spent around 2 to 5 days on collecting the information about each target. The information that he collected included all the domains that are associated with the company, their respective subdomains and IP addresses, as well as the information about the OS.
There are different search engines available for collections of the above information but there is no single place where more information can be found at any one time.
The tester worked on the application mentioned above a couple of months back and was not able to collect more information. Then, he gave it a try with Silent Push and the information was gathered in just a few minutes. Normally, it would take the tester several days to get that information from different sources.
1. The tester started by using their Explore DNS feature which accepts wildcards:
2. The tester then searched for any records associated with the test domain:
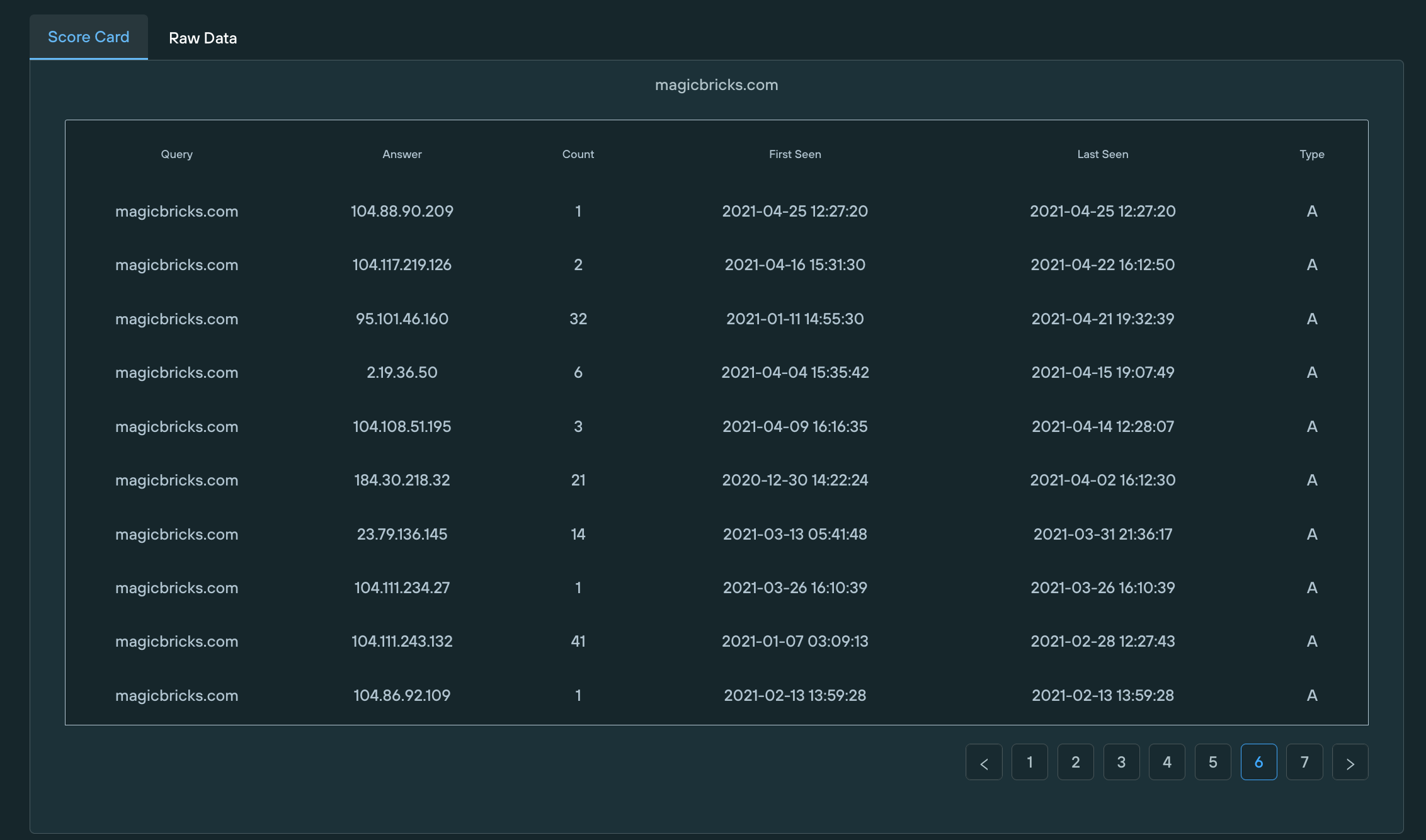
3. The tester then realized he could use a wildcard and gather subdomains and see what CNAME records were gathered and what IPs subdomains were using.

4. This allowed the tester to pivot off this information and see what else was pointed to the same infrastructure:
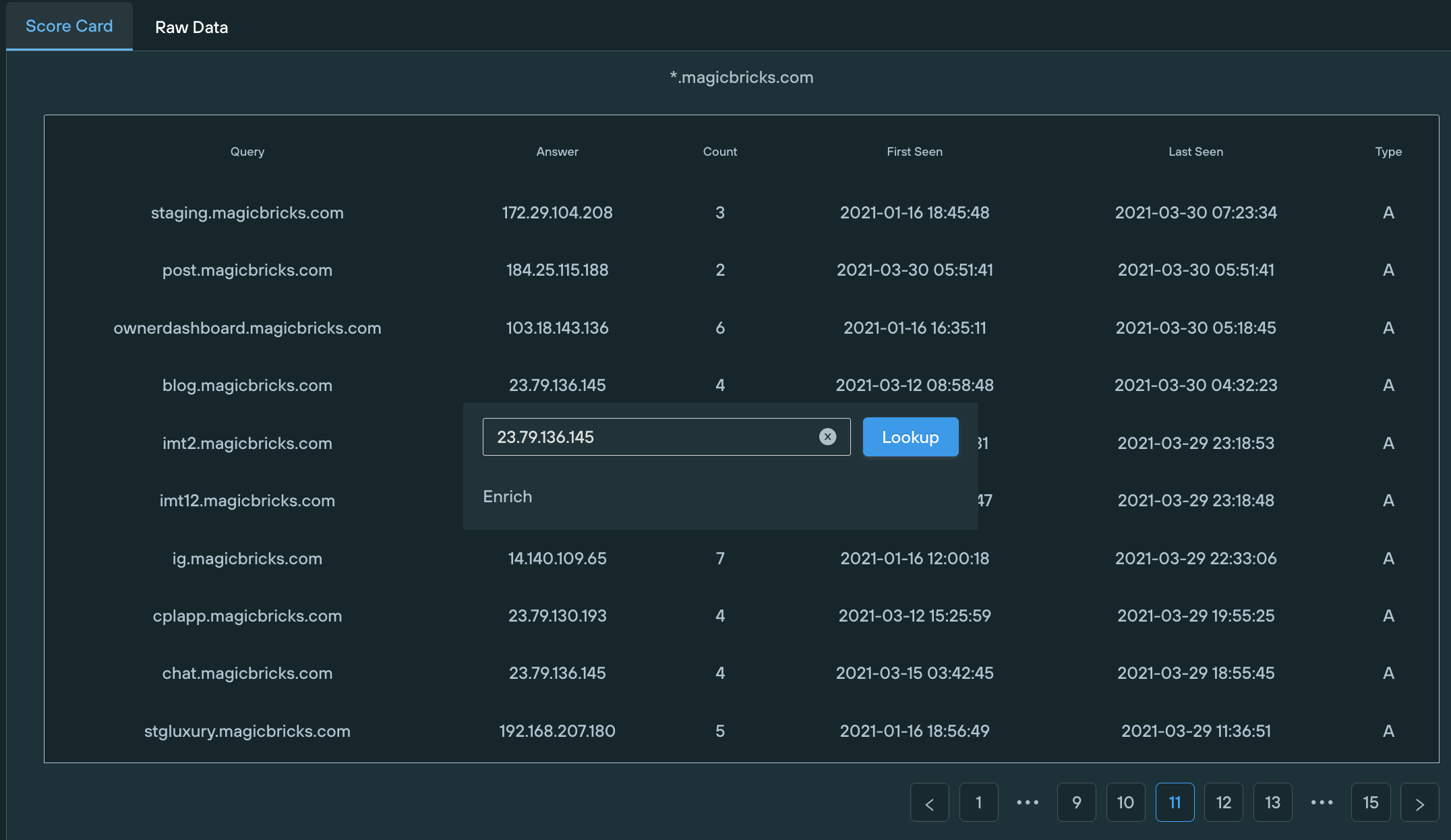
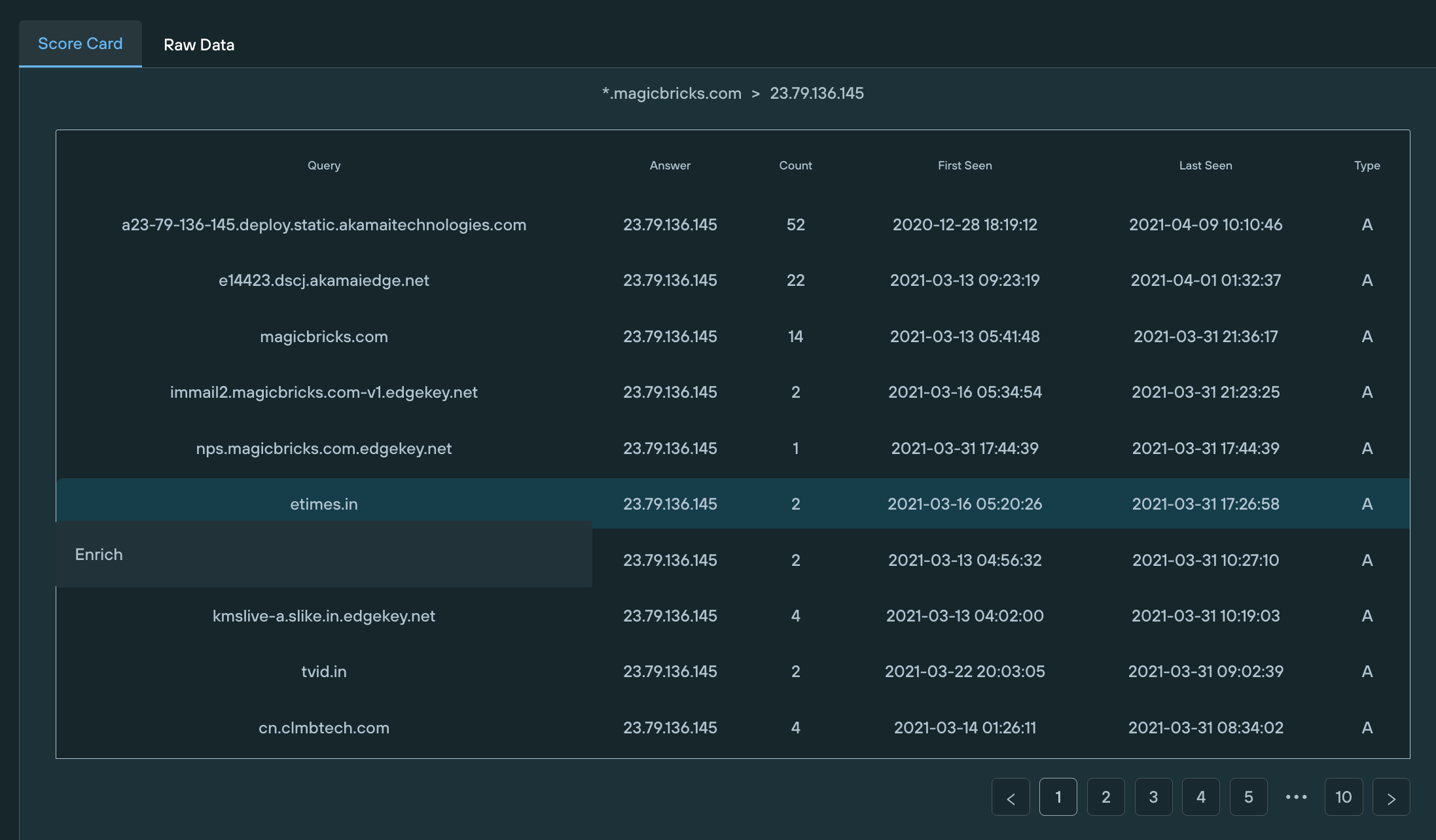
5. The tester could enrich that information to find out more about ‘the neighbours’ and see what sort of reputation was associated with them.
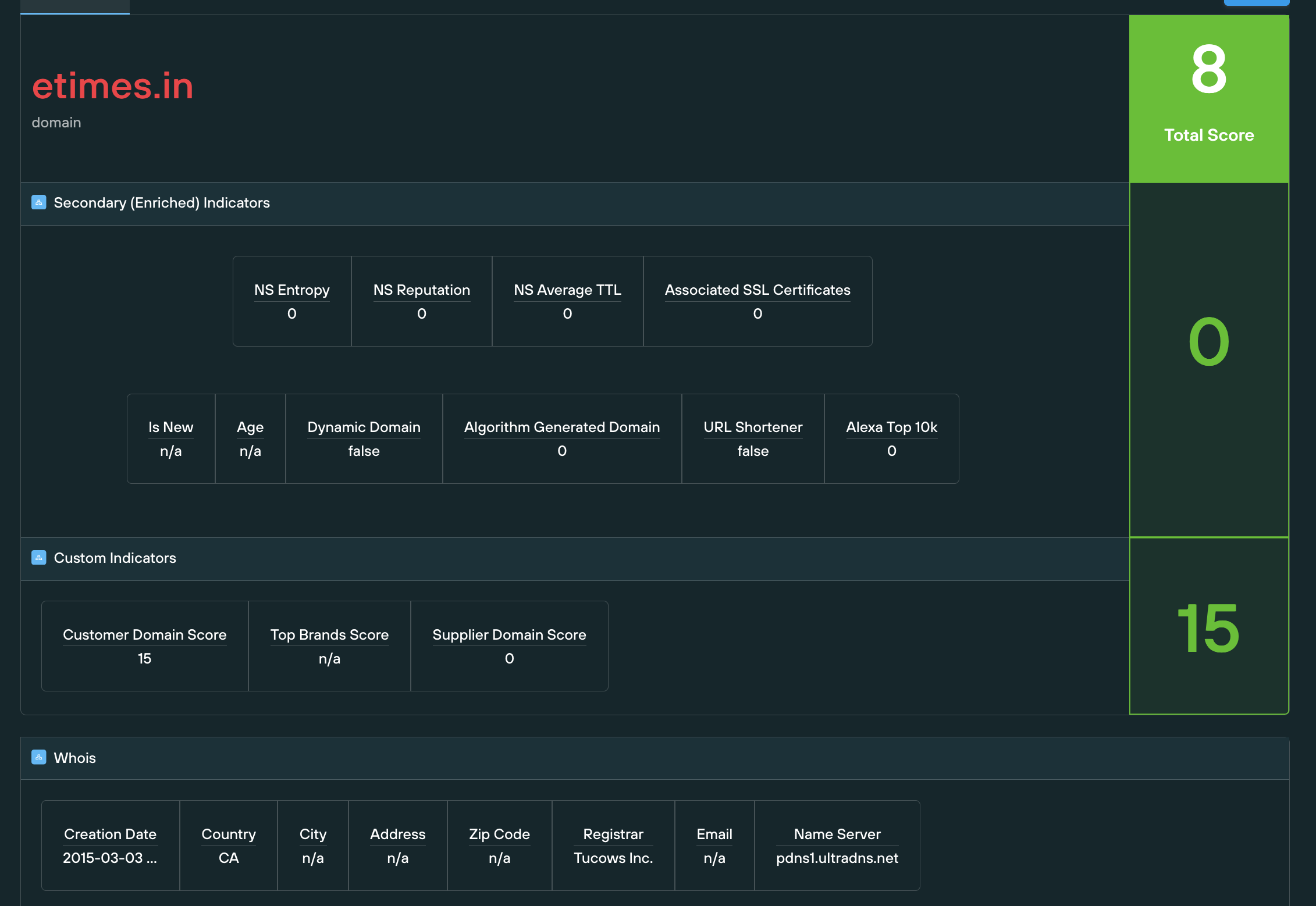
Conclusion
Even though the tester was not on a threat intelligence team, the simple data gathering capabilities of this part of the Silent Push application saved him enormous amounts of time. Quite literally, this saves the tester days per job. The use cases across entire security teams is tremendous.


