Key Findings
- Silent Push has uncovered a massive Internet Protocol Television (IPTV)-based piracy network that has been active for several years and is currently hosted across more than 1,000 domains and over 10,000 IP addresses.
- Our threat research team has identified a company, XuiOne, involved in profiting from hosting this pirated content. This practice is alarmingly lucrative: studies reveal that pirated content, including illegal IPTV streams, generates billions of dollars annually for its operators.
- More than 20 major brands have been affected by this ongoing hosting of pirated content, including: Prime Video, Bein Sports, Disney Plus, NPO Plus, Formula 1, HBO, Viaplay, Videoland, Discovery Channel, Ziggo Sports, Netflix, Apple TV, Hulu, NBA, RMC Sport, Premier League, Champions League, Sky Sports, NHL, WWE, and UFC.
Update: The individual previously mentioned as connected to the network infrastructure referenced in this report reached out to us to confirm that neither they nor their company had any involvement in IPTV activities. At the individual’s request, and as they have denied knowledge of, or direct participation in, the copyright infringement outlined below, we have removed all references to them in this report.
Executive Summary
Silent Push Threat Analysts discovered a massive network of IPTV-based piracy, currently hosted across more than 10,000 IP addresses and 1,100 domains, that has been operating for several years and affecting more than 20 major brands. Our finding of more IP addresses than websites across this network is unique for most cyber threats we track, but it appears to be a fairly standard practice for IPTV networks.
We have identified the company, XuiOne, as being involved in profiting from hosting pirated content.
It’s important to note that, while our team has confirmed a significant portion (if not all) of this network’s content is unlicensed (re: pirated) with no hallmarks of legitimacy, conclusive verification ultimately requires responses from each of the affected brands. Without such confirmation, it is technically possible that some media companies may have a licensing agreement with these hyper-aggressive IPTV networks. However, our team has observed no evidence to support that conclusion.
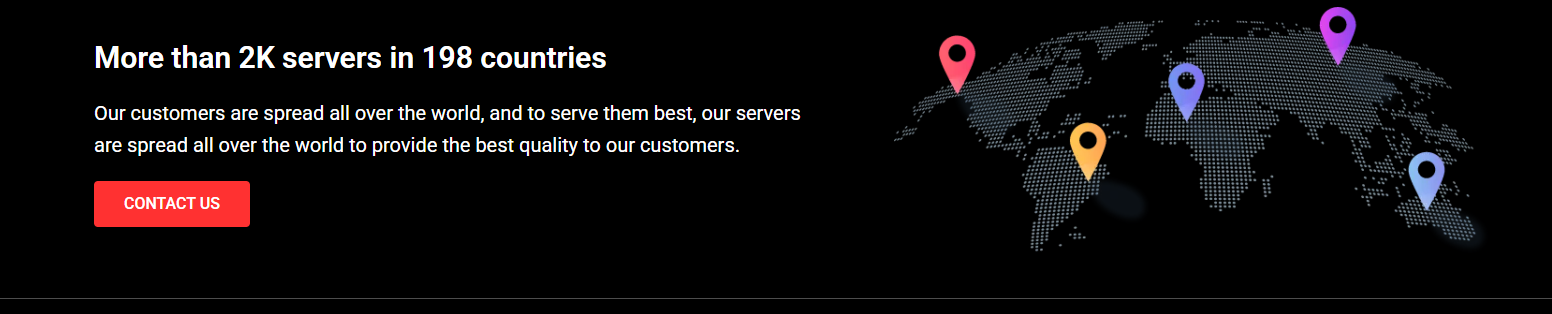
As a final note: One of the websites in the network, known as “JVTVlive,” openly claims to have “2,000 servers in 198 countries” (jvtvlive[.]com/faq/). Based on the data we’re tracking, these bold claims appear to be accurate.
Table of contents
- Key Findings
- Executive Summary
- Webinar 23 Sept. 2025: “Stopping Piracy Distribution Networks at Scale”
- IPTV Piracy Network Background
- Beginning Our Investigation
- Connections to Stalker Portal
- Advertisement of IPTV
- Dedicated IP Reveals New Domains
- Sign Up for a Free Silent Push Community Edition Account
- Mitigation
- Sample IPTV Piracy Network IOFA List
- Continuing to Track IPTV-based Piracy Networks
IPTV and streaming are not the same. While IPTV and streaming are both methods of delivering content over the internet, they differ in how the content is delivered and accessed. There are also differences in reliability, accessibility, and the types of devices used for content delivery and viewing.
IPTV uses a private, dedicated network managed by the service provider to deliver content, typically via a set-top box or the internet. Streaming, often referred to as “OTT” or Over-the-Top, bypasses traditional service providers and utilizes the open internet for viewers to access content on a wide range of devices, including smart TVs, computers, tablets, and smartphones.
Webinar 23 Sept. 2025: “Stopping Piracy Distribution Networks at Scale”
Join Silent Push Threat Analysts for a special webinar discussing how we exposed a massive IPTV-based piracy network targeting major media brands. In this threat intelligence session, our team will share how you can dissect adversary TTPs to map infrastructure, master proactive detection, and protect your brand.
Don’t wait for takedown notices. Register now to learn how to dismantle piracy networks before they grow.
IPTV Piracy Network Background
Common examples of legitimate providers of IPTV content include Hulu and YouTube TV. Access to this type of content typically relies only on an internet connection, so it is often abused for the delivery of pirated content, such as content provided without a license from the content rights holder.
Common characteristics of illicit/pirated content IPTV operations include:
- Illegal restreaming of licensed channels: Capturing legitimate TV feeds and redistributing them without permission.
- Subscription fraud: Selling access to premium content at a fraction of the cost (for example, offering deals of “$15/month for 22,500 channels and 100,000 Movies & TV Shows” found from “jvtvlive[.]xyz”).
- Use of the term “IPTV”: Most enterprise streaming services don’t use the term “IPTV,” but illicit streaming providers often do.
While digital piracy is illegal, it remains a booming underground market for several reasons. According to a 2024 Piracy Trends and Insights report from monitoring and content protection firm MUSO, TV piracy tends to rise in popularity due to “platform fragmentation” and “legitimate options failing to meet expectations in price, access, or timing.”
The Guardian notes that content titles are scattered, and escalating prices lead to an “artificial scarcity in a digital world that promised abundance.” It attributes the increasing interest in piracy to a “service issue,” where consumers face rising rental/subscription costs alongside fewer options for shorter periods.
IPTV piracy also poses significant risks to users, including financial fraud, malware infections, and legal consequences. Many consumers involved in IPTV piracy experience fraudulent charges to their credit cards after paying for pirated content through streaming services. Piracy app and website users are more likely to be victims of identity theft compared to non-pirating users. Piracy sites are also known for distributing malware that can steal personal data or infect devices.
When it comes to tracking these networks, the Silent Push platform makes it easy to map out the entire infrastructure supporting IPTV networks that advertise illicit/pirated content. Combining just a few technical fingerprints can be all that is needed to arm rights holders with the details they need to combat these pirates’ operations successfully.
Operational Security (OPSEC) Note: The analytical and infrastructure fingerprinting methods used by our team to enumerate this piracy network cannot be shared publicly; however, they are available in a more detailed report for our Enterprise clients.
Beginning Our Investigation
A research partner shared an initial indicator with us, premiumplustv[.]xyz, that had been hosting pirated content. From this single starting point, and utilizing the Silent Push Web Scanner, our team was then able to create a technical fingerprint connecting this service to more than 10,000 IP addresses and 1,100 domains.
The xuione[.]com website, seen below, is a massive IPTV provider that appears to support numerous pirated content schemes – confirming the initial suspicions of our research partner.
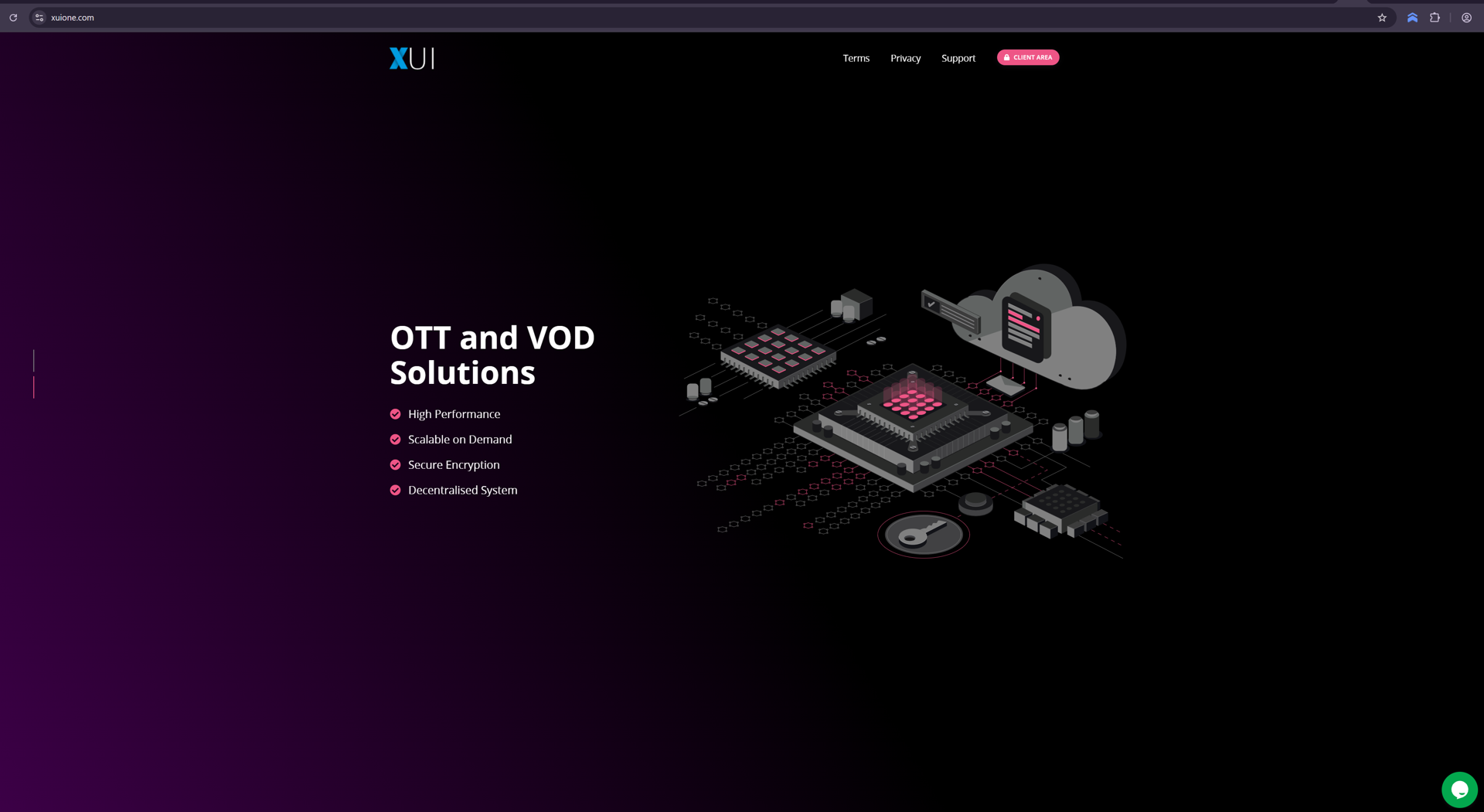
For several years, the xuione[.]com website listed details indicating the registrant was based in Herat, Afghanistan.
![Screenshot from the Silent Push platform of 2022 WHOIS records for xuione[.]com](https://www.silentpush.com/wp-content/uploads/iptv-image-2-whois-records-xuione-1.png)
Then, in March 2025, the registration details were updated to redact the Herat, Afghanistan, location data and replace it with a generic U.S. location.
![Screenshot from the Silent Push platform of 2025 WHOIS records for xuione[.]com](https://www.silentpush.com/wp-content/uploads/iptv-image-3-whois-2025-records-xuione.png)
Interestingly, while researching the XuiOne brand further, we conducted a quick Google search for the initial lead domain. There, we noticed a result for a “Debug Mode” from the domain that had a rather interesting URL path format: “premiumplustv[.]xyz:8080/get.php?username=TvWorld7382P&password=sYymzstukq&type=m3u“
![Google search screenshot of “premiumplustv[.]xyz”](https://www.silentpush.com/wp-content/uploads/iptv-image-4-google-premiumplus-xyz.png)
Checking the same full URL in our own Silent Push Live Scan capability, we confirmed the “XUI.one – Debug Mode” HTML Title response seen on Google.
![Screenshot from the Silent Push platform of the “premiumplustv[.]xyz” website](https://www.silentpush.com/wp-content/uploads/iptv-image-5-sp-platform-premiumplus-xyz-site.png)
In the next step, we will examine these pages and additional publicly shareable details.
Connections to Stalker Portal
Reviewing our previous XuiOne fingerprints also revealed connections to “Stalker_Portal,” another well-known open-source IPTV project that has been available for over a decade.
Stalker_Portal is the name of an open-source IPTV project that has been in existence for over 12 years. The code appears to be owned by Infomir[.]eu, which provides IPTV services. The phrase “Stalker Portal” is used by various projects that utilize the Infomir code, and it appears that the phrase is casually used to describe the backend management system of some IPTV providers.
Examples of Stalker_Portal being advertised can be seen below:

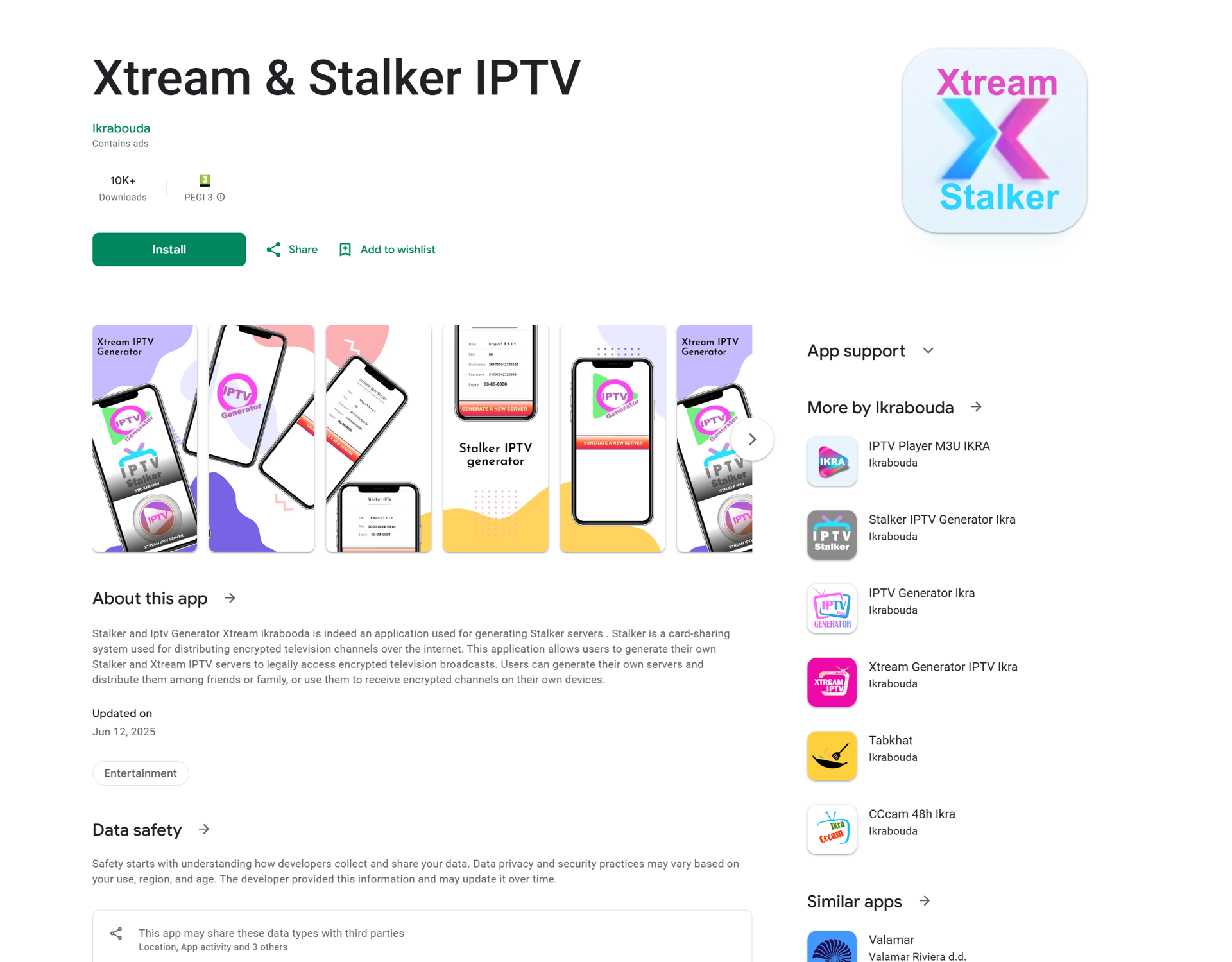
Advertisement of IPTV
Returning to Open-Source Intelligence (OSINT) for a moment, it’s possible to discover places where these domains have been spam-promoted, along with potentially related domains that Google picked up. In seeking to share this publicly, our team was able to create this effective “Google Dork”* based on the progress made so far.
*Note: A Google Dork is a specially crafted search query that uses “advanced” operators (such as site:, intitle:, filetype:) to find specific information on the web that’s not easily visible through normal searches.
Google Dork link: https://www.google.com/search?q=inurl%3A%22type%3Dm3u%22+inurl%3A%22get.php%22&filter=0
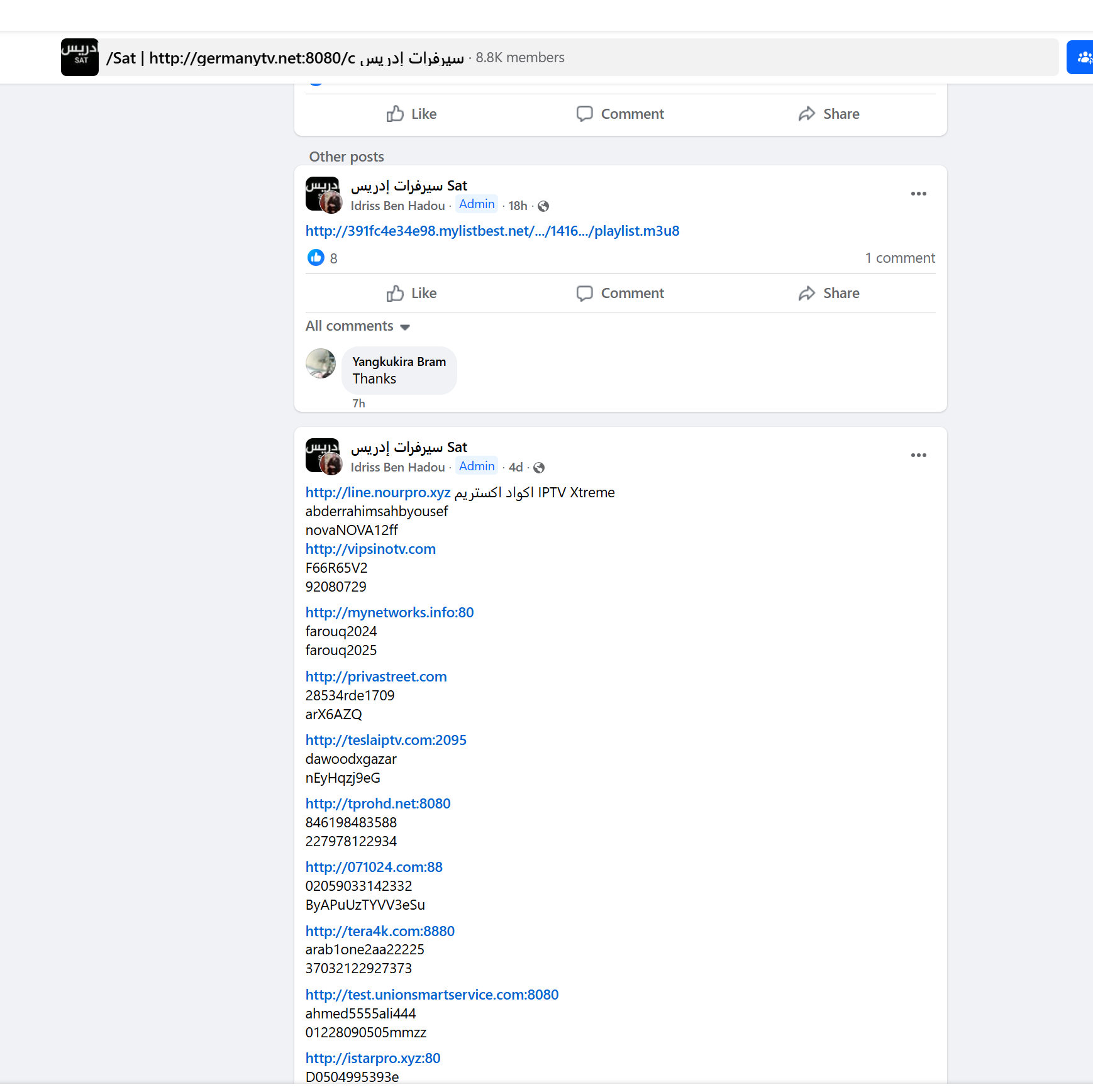
The Facebook group where this was posted is also notably sharing other, similar URLs. Still, many appear to have the username/password parameters, a practice often seen on Telegram by similar types of accounts.
On the Facebook group, commenters indicate whether a site is online by posting comments like “Off,” suggesting that these sites are often only accessible for brief periods or to specific users or IP addresses and locations. That group can be found here: https[:]//www[.]facebook[.]com/groups/862409924169988/.
Notably, they include an Arabic phrase for “servers’ address”: “سيرفرات إدريس ”.
It’s common to see people post “Does not work” or similar comments:
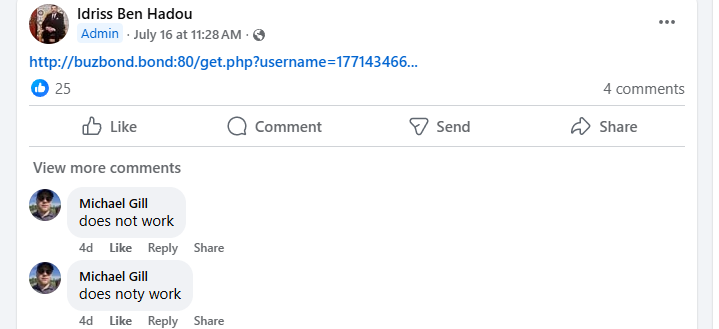
The format for many of the URLs being shared is relatively consistent, although the domain and the username/passwords being shared are chaotic, and the ports appear to change intermittently as well:
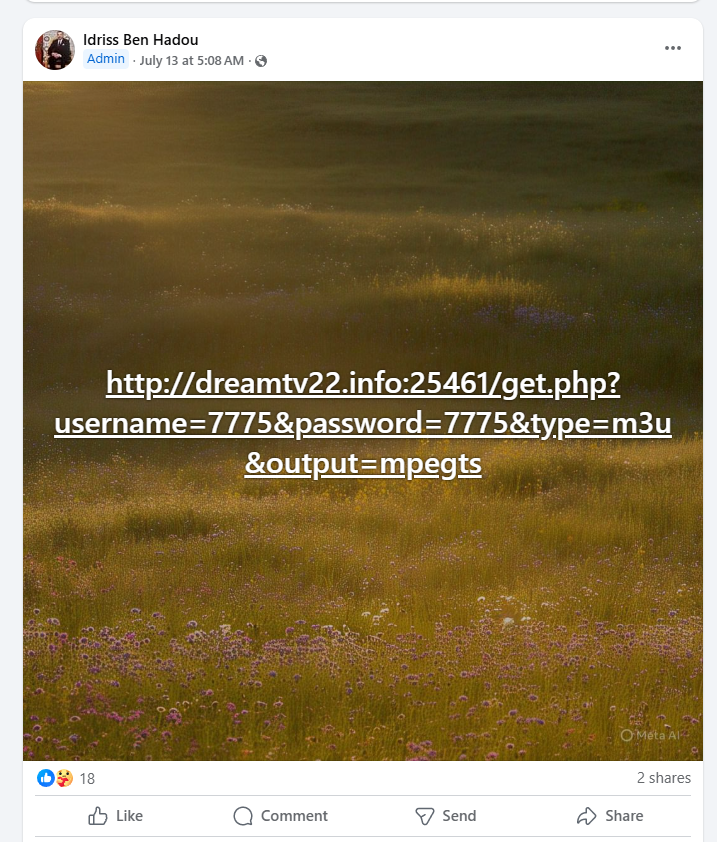
Examining the repetition, the most common format appears to be:
“http://domain[.]suffix:{Random_Port}/get.php?username={value}&password={value}&type=m3u&output={value}”.
Knowing the structure of the URLs used, our team was able to find evidence that this streaming network has been promoted across the web for years. Here’s an example from Imgur in 2018:
Dedicated IP Reveals New Domains
As we continued the investigation, our team noted that the xuione[.]com domain has been mapped to multiple A records, each of which appears to be a low-density, shared IP address. Since these small ranges also contain other IPTV websites, it’s likely that those sites are also part of this network.
An example of one such cluster can be seen by enriching the IP in question, 158.220.114[.]199, in our Total View:
![Screenshot of Silent Push Total View enriching IP address 158.220.114[.]199](https://www.silentpush.com/wp-content/uploads/iptv-image-13-sp-total-view-ip-158220114199.png)
Our team identified two IPTV-focused domains utilizing the dedicated IP address 158.220.114[.]199, which is also used by xuione[.]com. The first is self-evident, but the second is more interesting:
- streamxpert[.]net
- jvtvlive[.]xyz
![Screenshot of “streamxpert[.]net” website](https://www.silentpush.com/wp-content/uploads/iptv-image-14-streamxpert-net-site.png)
The second result, the JVTV website, jvtvlive[.]xyz, touts its services as:
“Top-notch JVTV live Subscription Provider: Unlock a World of Entertainment with Our Service: Access Thousands of Global Channels, Countless Movies, and an Extensive Collection of Series!”
![Screenshot of “jvtvlive[.]xyz” website](https://www.silentpush.com/wp-content/uploads/iptv-image-15-jvtvlive-xyz-site.png)
JVTV’s service includes promotions listed for the following “channels”: Prime Video, Bein Sports, Disney Plus, NPO Plus, Formula 1, HBO, Viaplay, Videoland, Discovery Channel, Ziggo Sports, Netflix, Apple TV, Hulu, NBA, RMC Sport, Premier League, Champions League, Sky Sports, NHL, WWE, and UFC.
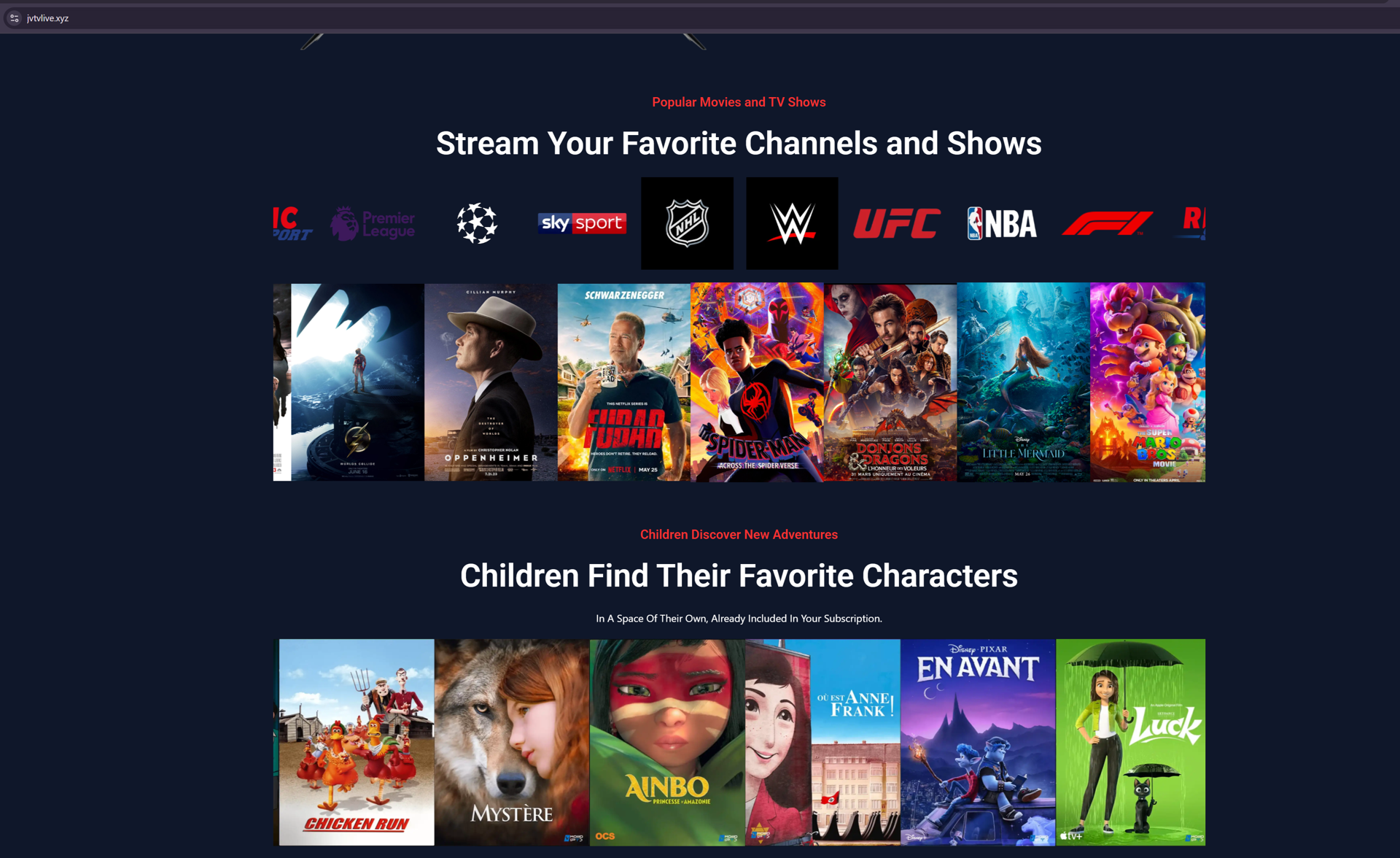
JVTV claims to have “2,000 servers across 198 countries” on its website:
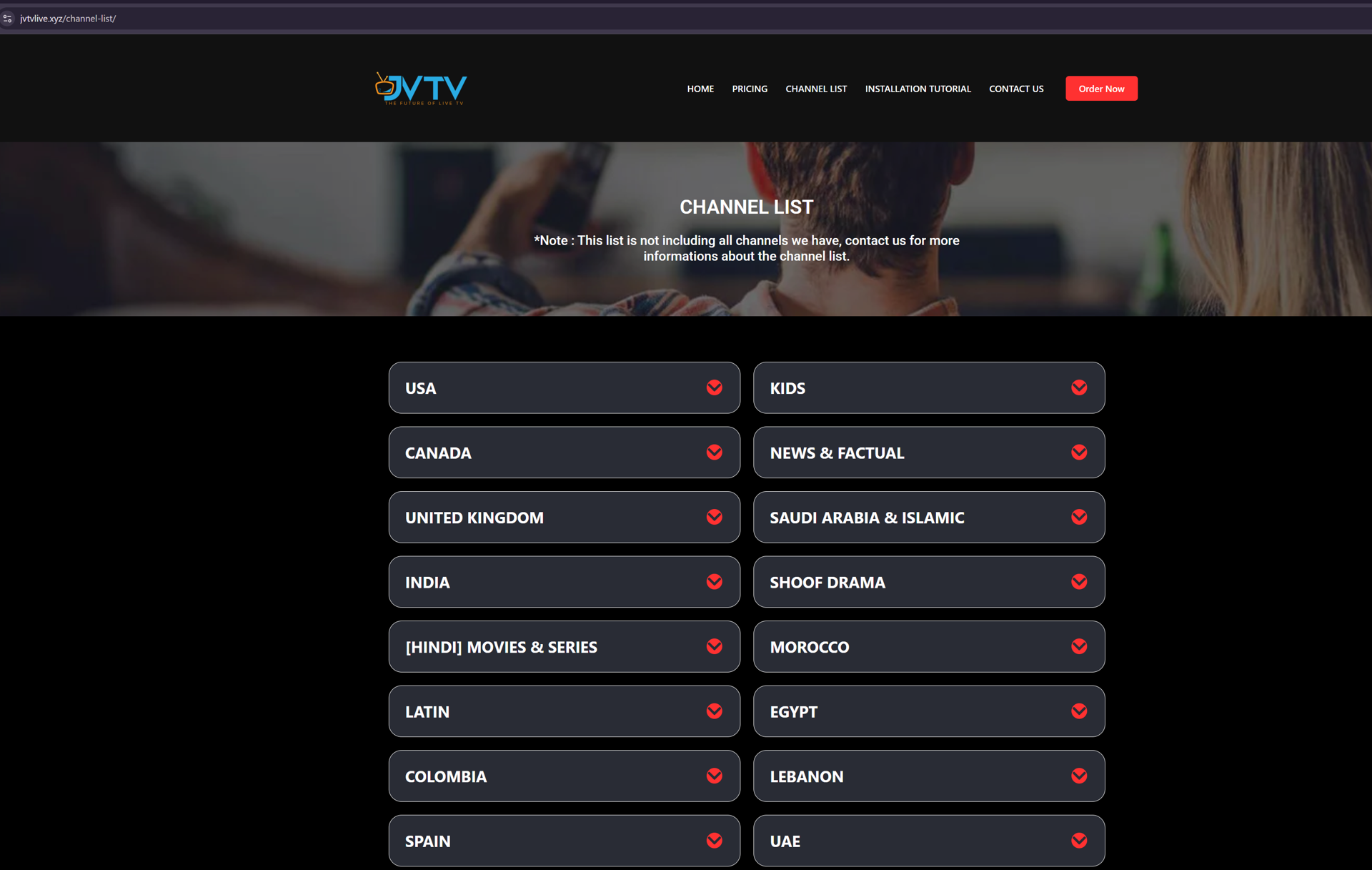
JVTV also provides a channel list for each country:
Sign Up for a Free Silent Push Community Edition Account
Register now for our free Community Edition to use all the tools and queries highlighted in this blog.
Mitigation
Silent Push’s unique visibility into the ever-shifting sands of the internet’s global architecture, and the peerless first-party data sources that support it, regularly provide our customers with pre-breach intelligence in the form of our Indicators Of Future Attack™ (IOFA™) Feeds.
Our platform’s ability to map attacker infrastructure before it can be weaponized also enables the rapid and comprehensive detection of content piracy networks, such as those described above.
In service to that, our analysts have constructed a pair of Bulk Data Exports containing the growing list of indicators focused on these types of IPTV-based pirates that our customers can use to support their brand protection investigations. These exports include:
- IPTV Piracy Domains
- IPTV Piracy IP addresses
Silent Push’s Bulk Data Exports are available as part of an Enterprise subscription. Enterprise users can use this data to support their investigations or pivot across piracy-related infrastructure in our platform.
Sample IPTV Piracy Network IOFA List
Below is a sample list of Silent Push IOFA™ associated with the IPTV Piracy Network. Our complete list is available for enterprise users.
- iptvadvice[.]com
- jvtvlive[.]xyz
- streamxpert[.]net
- xtreamui[.]org
- xuione[.]one
Continuing to Track IPTV-based Piracy Networks
Our team continues to actively monitor IPTV-based piracy networks, which host and stream illicit/pirated content, as well as their associated infrastructure.
Silent Push Enterprise customers enjoy customer-only reporting streams on this threat and many others. Where possible, we will share the details that can be made public with our readers.
If you or your organization has any information on this topic or would like to reach out for a demo on how we can help your brand map out a network that is pirating your content, we look forward to hearing from you.