Search through indexed directories and files from open directories to help protect your organization.
Most people have listened to an elderly relative extolling the virtues of the ‘good old days’, including a semi-smug description of their front door being left open in the summer – usually justified by the fact that they didn’t have anything worth stealing.
Open directories are just that – an open door onto your fileserver which, unlike an average 1950s living room, contains information that is extremely valuable, for a variety of reasons.
In the world of global commerce, data is a highly lucrative and sought-after commodity. By using open directories, threat actors are able to seize vast amounts of commercially sensitive information in a matter of seconds, and they’re gone before you even know they were there.
Let’s take a look at the global problem of open directories, what the consequences are, and how you can find them using the Silent Push Open Directory Finder.
What are open directories?
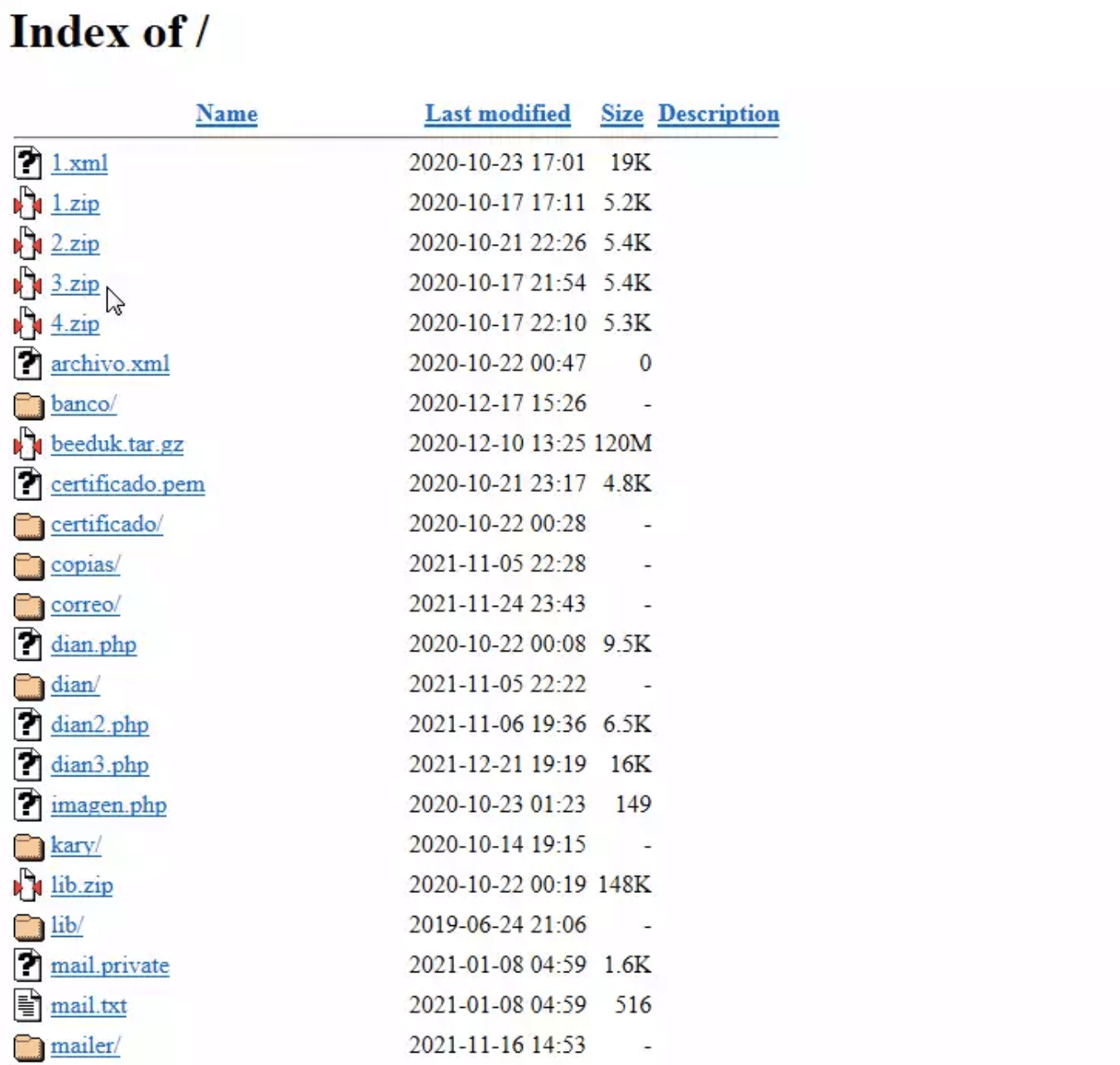
Open directories are freely accessible links to files hosted on a webserver that’s connected to the Internet, and not subject to any authentication methods or external access rules.
There’s no software-based trickery involved. Open directories can be found using a simple Google search, tailored towards different categories of data. Once a threat actor has identified an open directory, they’re free to browse through an organization’s file structure without circumnavigating RBAC or permissions-based security measures.
Whilst it is undoubtedly immoral to access and/or download sensitive information that isn’t meant for prying eyes, the act of browsing through an open directory is a legal gray area. There’s no global consensus on how such scenarios should be legislated against, and sentiments vary from jurisdiction to jurisdiction.
How damaging can they be to your organization?
Very. Extremely. Catastrophically, in fact.
Malicious activity on open directories is nigh on impossible to detect. The first you’ll hear of it is either a phone call from a law enforcement/regulatory agency, an email from a hacker demanding money to keep quiet, or a very annoyed customer wondering why their data has been passed around the Internet for the last few years.
Then there’s the compliance and liability aspect. Cyber insurance policies don’t cover the commercial or operational consequences of an open directory exploit, so unless you have the working capital to deal with the fall-out, it could lead to untold reputational and financial damage and land you in pretty hot regulatory water.
Last, and by no means least, is the data itself. Take a moment to think about the data held on your organization’s webservers and fileservers, and what would happen if you exposed it to the world through an open directory.
By working with firms to improve their threat resilience, we’ve seen sensitive data held in open directories that would make a privacy protection lawyer spontaneously combust:
- Full environment files.
- Commercial application configs.
- Cryptowallet logins.
- VPN installers.
- .xls and .docx files containing PII and GDPR/HIPAA-regulated data.
Once you start investigating open directories on the behalf of large organizations, the horror stories come thick and fast. We recently came across a fairly sizable prison in the USA that left the door open to tens of thousands of electronic prisoner and staff records, including legal information, social security numbers and conviction details.
How do you prevent them?
Like other forms of threat protection (such as stopping subdomain takeovers), securing your organization’s data by preventing open directories is done through a combination of vigilance and good housekeeping.
Anyone who’s ever browsed the Internet has, somewhere along the line, received the dreaded error 403 Forbidden or 404 File Not Found, instead of a web page. As an organization looking to protect its data, these errors are your friends, not your enemies – this is what users are faced with when a server has been configured to block access to directory content.
Methods vary from platform to platform (from simple login controls to modifying your .htaccess files and ensuring that IIS is configured correctly), but if you host ANY kind of sensitive data on a webserver, you need to make sure that it’s configured so that external and unauthenticated users aren’t able to view directory data.
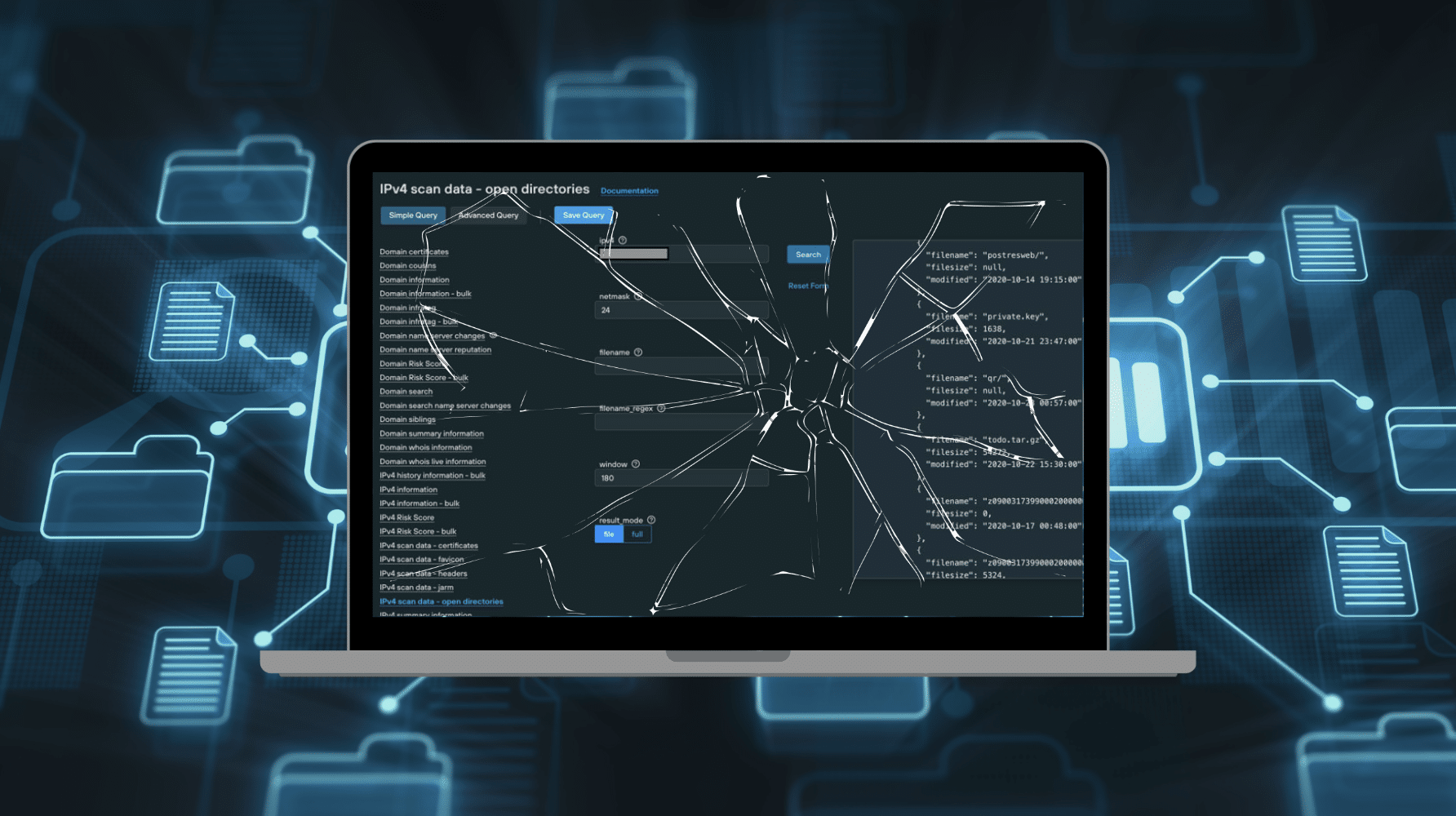
Silent Push Open Directory Finder
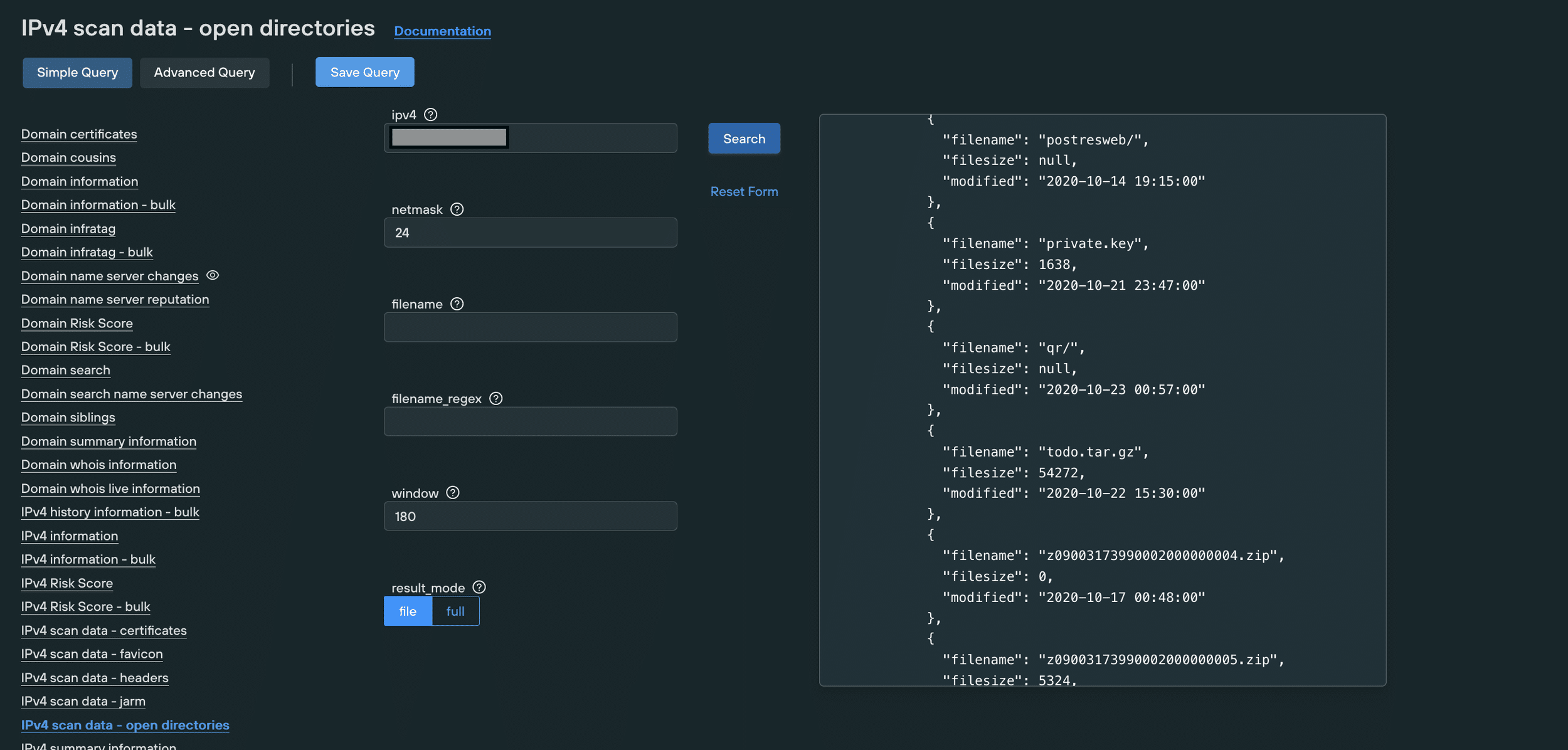
The Silent Push Open Directory Finder searches the global IPv4 range (all 4,294,967,296 addresses) for open directories, to a granular set of parameters that can be configured to your organization’s unique requirements.
Our cloud-based platform provides search and filter options (with RE2 regex support) on all known open directories, including variables such as range, partial match and time window. Results can either be outputted in full, or to a file for further interrogation.
If you’re a large, multi-site, multi-jurisdictional organization with an extensive online presence, you’ll be presented with a realtime list of open directories within the specified range.
Enterprise-level threat monitoring (including open directory detection) doesn’t need to be resource hungry. With the right tools, it is quite literally as easy as clicking a few buttons, in order to shore up your commercial data and close the aforementioned door onto your network that leads to something considerably more valuable than your grandmother’s collection of faux-porcelain dogs.