Log4shell or CVE-2021-44228, a vulnerability in the Java-based Log4j-logging framework is bad. Like, seriously bad. If measured by the number of hours spent globally remediating the issue, it is likely among the worst vulnerabilities that has ever been found.
The vulnerability allows an adversary to execute code on an affected system by having a specific string written to a log file, which may involve little more than setting the HTTP user agent to contain that string. To make matters worse, logs are often written to servers not directly exposed to the Internet, which makes these servers vulnerable too.
And to make matters even worse, Log4j is ubiquitous: even if you are not using the software directly, it may still have been included in third-party software you’re running on your network.
The vulnerability was first reported a week ago and scanning for it started at the beginning of the month. Yet in the short time since it was discovered, it has been used to install cryptominers, launch ransomware, as well as in state-sponsored attacks.
This means that Log4shell, though initially and still primarily a security operations issue, is now also a threat intelligence issue.
I have seen lists being shared of IP addresses from which Log4shell has seen being exploited. Given how easy it is to scan for it, such lists don’t seem particularly useful. Indeed, I saw many Tor exit nodes contained in such lists.
Lists of servers hosting Log4shell payloads may be more useful, but only slightly so: it’s simply too easy to set up a server and host a payload, so it would lead to a frustrating game of whack-a-mole. Moreover, there will be a lot of noise from security companies probing for the vulnerability without actually exploiting it.
The most effective thing a threat intelligence team can do is closely monitor for indicators linked to malware exploiting Log4shell.
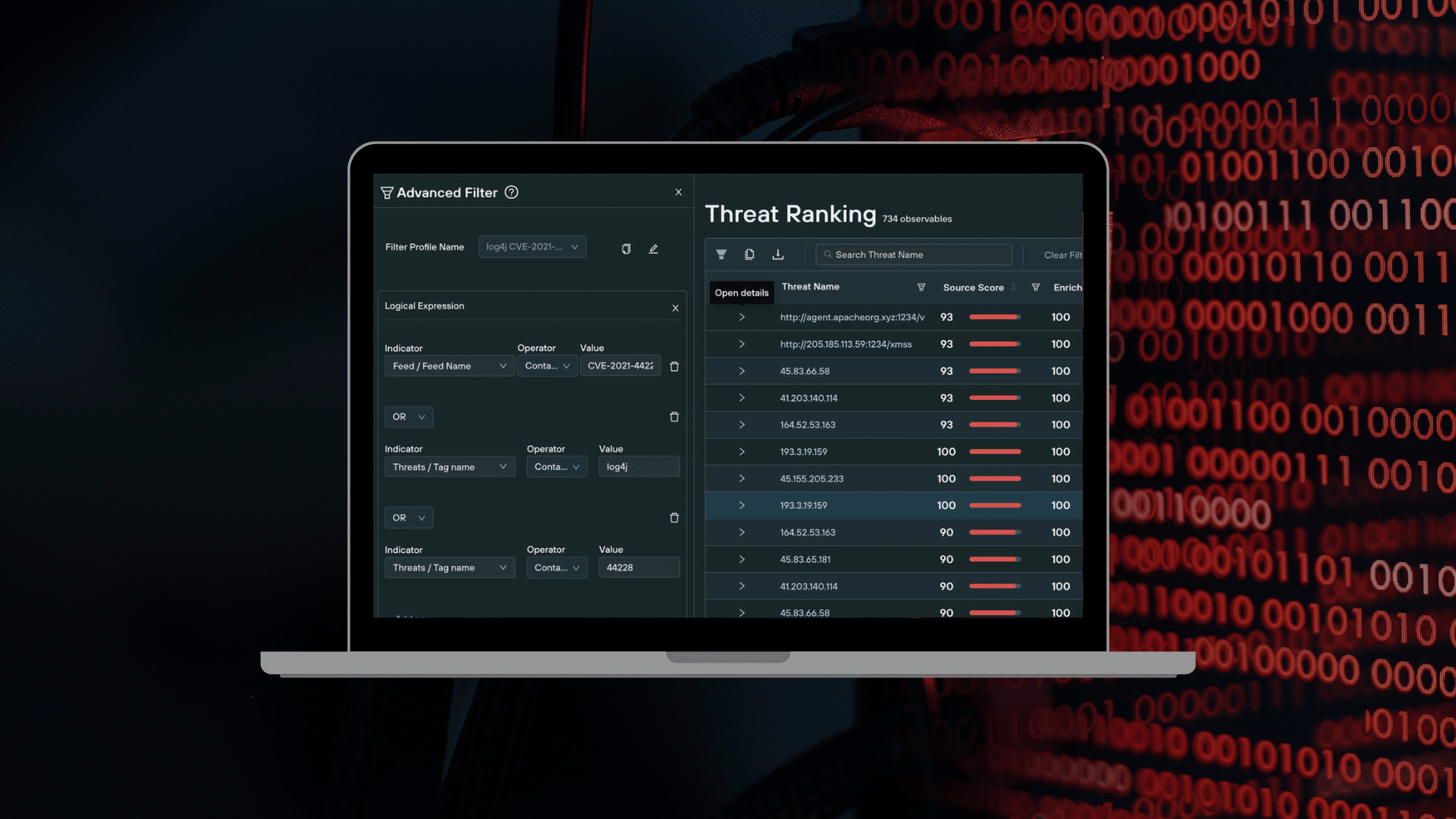
The Silent Push platform makes it easy for you to do so: you can filter your public and private feeds to only include those indicators with tags containing the strings log4j, log4shell or 44228, as well as those on specific feeds linked to Log4shell.
Silent Push platform showing the use of advanced filters:
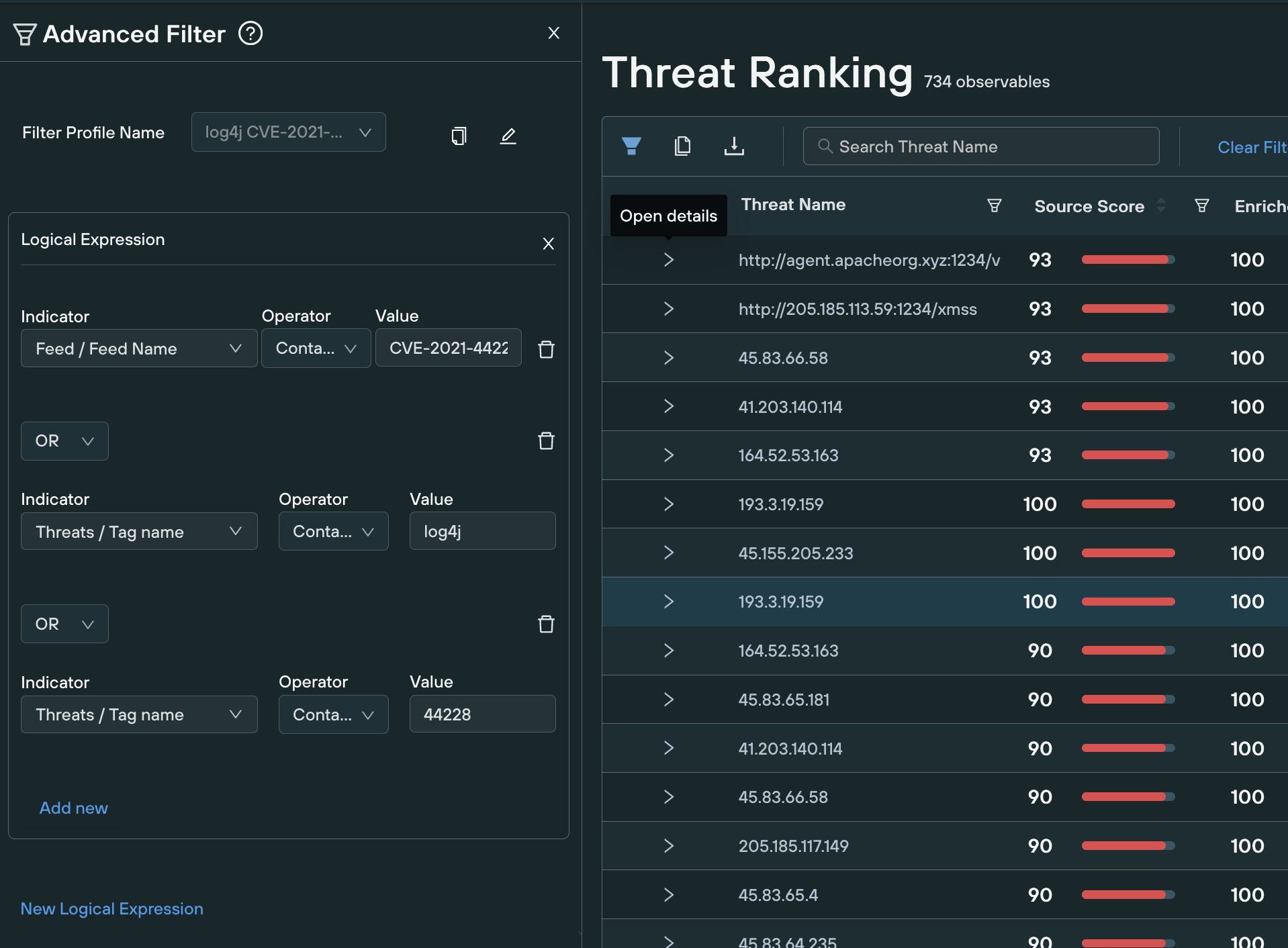
Of course, as a threat intelligence team you will want to monitor for all threats, regardless of how they got into your network. But searching for Log4shell-related threats not only helps you focus on some of the hottest threats out there, it will also help you discover hidden instances of Log4j in your network, while at the same time helping you answer questions about Log4j exploitation you are no doubt getting from the board.