Cloud-based solutions and third-party SaaS are a go-to for startups and large enterprises alike. With their popularity on the rise, we want to talk about the role they play in helping threat actors bypass companies’ security efforts and threat monitoring.
This article outlines the inherent risk of adding third-party services to your tech stack, and the measures you can take to appropriately safeguard your infrastructure and assets.
How threat actors use your third-party apps against you
Signing up for a SaaS product immediately increases your company’s attack surface. Platforms lacking basic security measures such as 2FA pose a particular risk to their clients, but any third-party addition to your tech stack creates new angles of attack for threat actors to take advantage of.
By targeting your enterprise through your third-party platforms, threat actors exploit vulnerabilities that are often neglected by internal security efforts, but which are nevertheless linked to your infrastructure and assets.
Supply-chain attacks, email takeovers, subdomain takeovers, and brand impersonation are the most common attack vectors used for harming your enterprise via a connected third party:
Supply chain attacks
Supply chain attacks spread viruses and other malicious code via a company’s third-party software, often hidden behind system updates. Attackers commonly place malware within source code that then spreads the malicious content to trusted apps and systems.
This type of attack is difficult to track, and a single piece of compromised software is enough to propagate malware across an entire supply chain. Threat actors can additionally use stolen certificates to make it easier for the code to pass as legitimate.
Malware attacks are used to damage your infrastructure, steal or withhold your information, enable broader security breaches, and more.
Email & subdomain takeovers
Threat actors gaining control over a third party’s subdomain (or subdomains) can use these to host malicious content, gain control of sensitive information, steal cookies, hijack SSO sessions, and more.
Compromised subdomains are hard to spot. The related apex domains are known and trusted, and threat actors often obtain SSL certificates to add to the perceived legitimacy.
Threat actors hijack emails and email servers to spread fraudulent content in the name of known and trusted senders. Since these emails stem from otherwise legitimate contacts, they can easily bypass security filters. They are especially difficult to identify when the threat actors imitate the content and tone of previous email traffic.
Compromised emails are commonly used to request employees’ personal information, spread malicious links, send fraudulent invoices, and more.
Third-party impersonation
Threat actors often impersonate legitimate brands and companies to obscure malicious intent and activity. Third-party platforms along an enterprise’s supply chain are a popular target for these impersonations.
Impersonation attacks follow a similar pattern to email and subdomain takeovers, only that the third party’s infrastructure is imitated, rather than directly breached. Spoofed and typosquatted domains are used for both fraudulent pages and malicious emails. Content, copy, and visuals can be made to further imitate the targeted third party, and make the fakes more convincing.
As above, these fraudulent emails and pages are used to harvest credentials, commit invoice fraud, open the door for further attacks, and more.
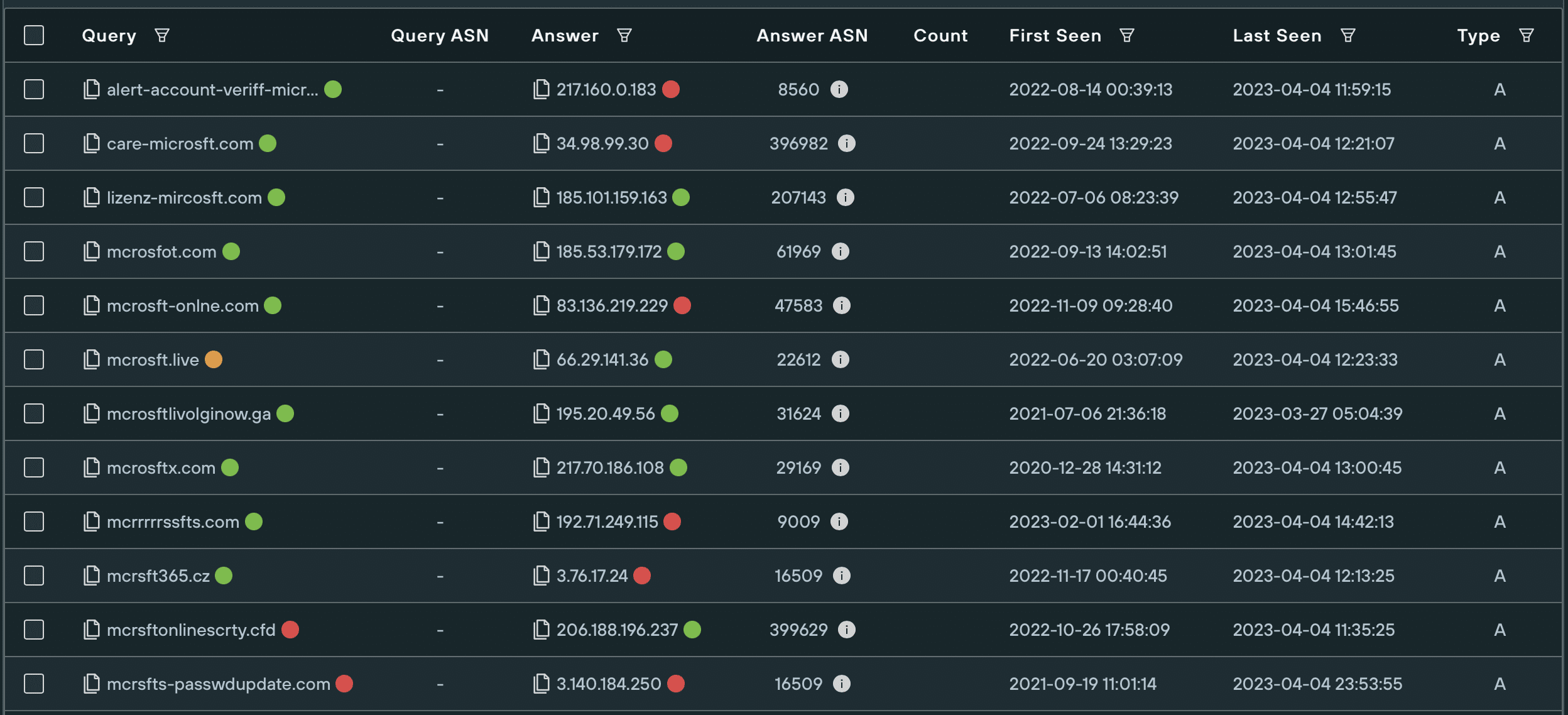
Domain impersonations of microsoft[.]com
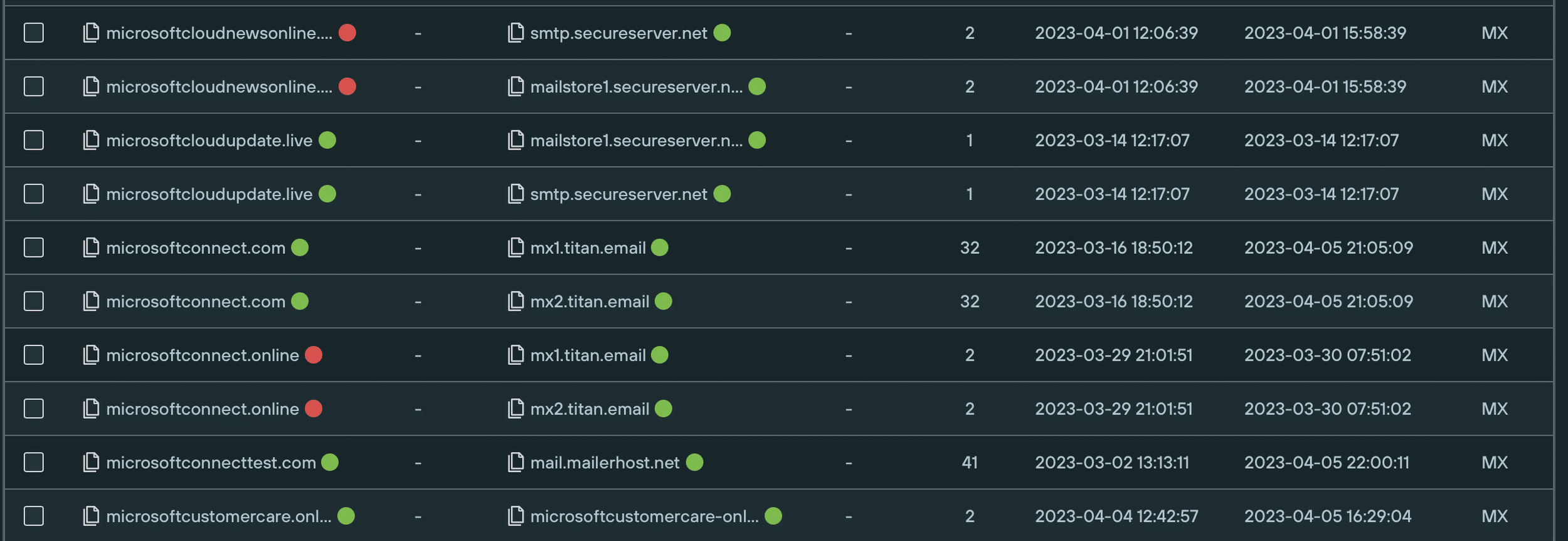
Email impersonations of microsoft[.]com
Security best practices
Adding your third-party infrastructure to your threat framework allows you to keep the ball in your court. Rudimentary security hygiene and best practices significantly reduce the risk stemming from platforms and SaaS you’ve made part of your tech stack, or want to.
Assess vulnerabilities beforehand
Some SaaS platforms are quickly identifiable as liabilities to their potential clients. Vulnerabilities that are easy to spot for you are also evident to threat actors and should be taken into consideration when assessing a platform or service.
- Check for two-factor authentication
Before signing up for a platform, check if they offer 2FA.
Two-factor authentication is a minimum safety standard for any platform or service. Threat actors have a nearly endless toolset for stealing login credentials — without 2FA, a stolen password and email address are all that is needed to infiltrate your third-party’s infrastructure and spread attacks amongst the entire length of your supply chain. - Scan for dangling DNS
Companies allowing subdomains to expire without removing the DNS records pointing at them, make themselves vulnerable to subdomain takeovers and vast infrastructure/data compromises from there on out.
These so-called dangling DNS can be easily spotted by outsiders, and you should scan for them before signing up for a new platform.
On the Silent Push App, the Xperimental-PADNS Report on Dangling Records Audits a given domain name for dangling records. The query returns all dangling DNS records — type A, NS, MX, or all — that were created, removed, or left unchanged in the past 7 days for the given domain name and its subdomains. This allows your security team to quickly identify infrastructure susceptible to takeover by malicious actors. - Investigate open directories
Open directories are publicly accessible web directories that do not require authentication or access control to view the files within them. Lax security measures and information mismanagement go hand in hand, and it is not uncommon for companies to store critical data in freely accessible files.
Much like threat actors, you can scan for a third party’s open directories and investigate the information they contain.
On the Silent Push App, the Open Directories query allows you to locate all open directories within a given network/IP address, or to search for specific files across all IPs, either by name or regex. Before signing up for a platform, your security team should perform an open directory search to assess whether critical information that is freely available for threat actors to steal and abuse.
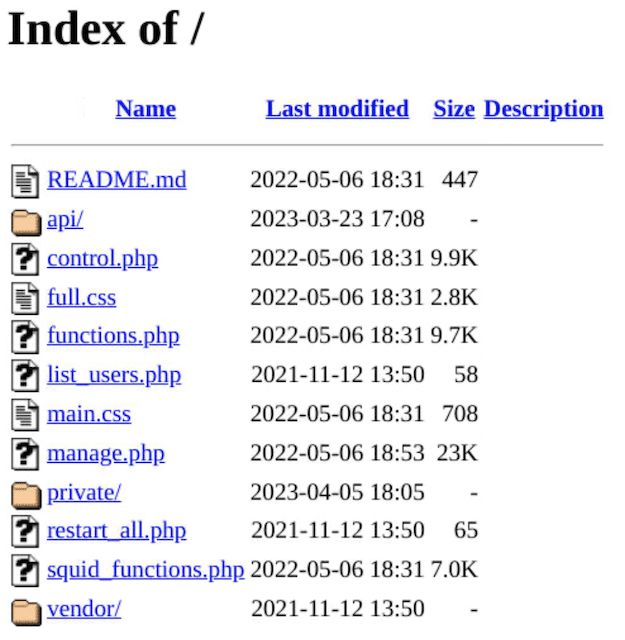
Open directory example with exposed sensitive information
Manage your infrastructure
Keep an eye on your existing third-party services to track the true borders of your infrastructure. Unused applications should be removed from your tech stack, and platforms with obvious safety concerns replaced with more appropriate alternatives.
- Track infrastructure associated with you
Manually kept logs of your third-party services are prone to inaccuracy, more so as your company grows in size and headcount, and your departments start autonomously signing up for platforms to support their operations. Over time, your associated infrastructure becomes hidden and vulnerable to attacks.
Creating an automated, centralized dashboard of your related third-party infrastructure removes dangerous unknowns.
On the Silent Push App, the Discover Shadow IT uncovers related infrastructure by returning subdomains set up in your name by your third-party services. This allows you to see which parts of your supply chain are easily visible to threat actors, and likely entry points for attack. - Educate and train your teams
Human error is the most common cause of security breaches. Employee education makes a noticeable impact on the safety of your infrastructure.
Train your departments on the risks associated with third-party infrastructure, and have potential sign-ups to new platforms assessed and sanctioned by your security team. Ensure that all employees adhered to basic security standards such as using 2FA for all services, maintaining and updating strong passwords, not sharing sensitive emails on suspicious channels, etc. - Create fail-safe scenarios:
Outlining how a third-party breach would impact internal systems is part of a cohesive strategy for protecting organization data and assets.
Start by identifying which parts of your infrastructure would be immediately affected by a breach and whether they are cohesively nested within other systems. Implement fail-safe mechanisms and consider how you could minimize an attack’s collateral damage, for instance by isolating core system resources or encrypting sensitive data.
Periodically re-evaluate the security controls in place to avoid having your data extracted or erased as a consequence of a third-party compromise.
Monitor your full attack surface
Monitor your third-party apps as part of your expanded attack surface to quickly spot suspicious activity on the periphery of your infrastructure.
- Scan for impersonation
Typosquatted domain and subdomain names of your third-party platforms are common indicators of impersonation and spoofing. You can use them as entry points for more extensive investigation and prompt countermeasures.
On the Silent Push App, the Domain Impersonation recipe identifies typosquatted domains of your trusted third-party services and enables you to proactively block any traffic stemming from them. Similarly, the Autospoofing query tracks and lists likely impersonations of your third party’s emails, allowing you to block these as well.
Set up daily monitors for both lookups to be automatically notified of any new domain and email impersonations. Exclude benign infrastructure from your searches and filter your results to remove false positives and attain more accurate tracking. - Tailor your threat predictions
Since it is impossible to closely monitor all of the internet’s activity, threat prediction tools give additional weight to suspicious movement in close proximity to a given organization. Marking your third-party solutions as part of your infrastructure enables your security teams and tools to better predict and monitor the likely entry points for attacks on your enterprise.
On the Silent Push App (Enterprise Subscription), adding your Supply Chain Domains to your trusted Organization Assets improves the tailored threat prediction given for known IOCs. This increases their given threat scores visible on the Threat Ranking Page and allows you to counteract suspicious infrastructure before it is activated for malicious campaigns.
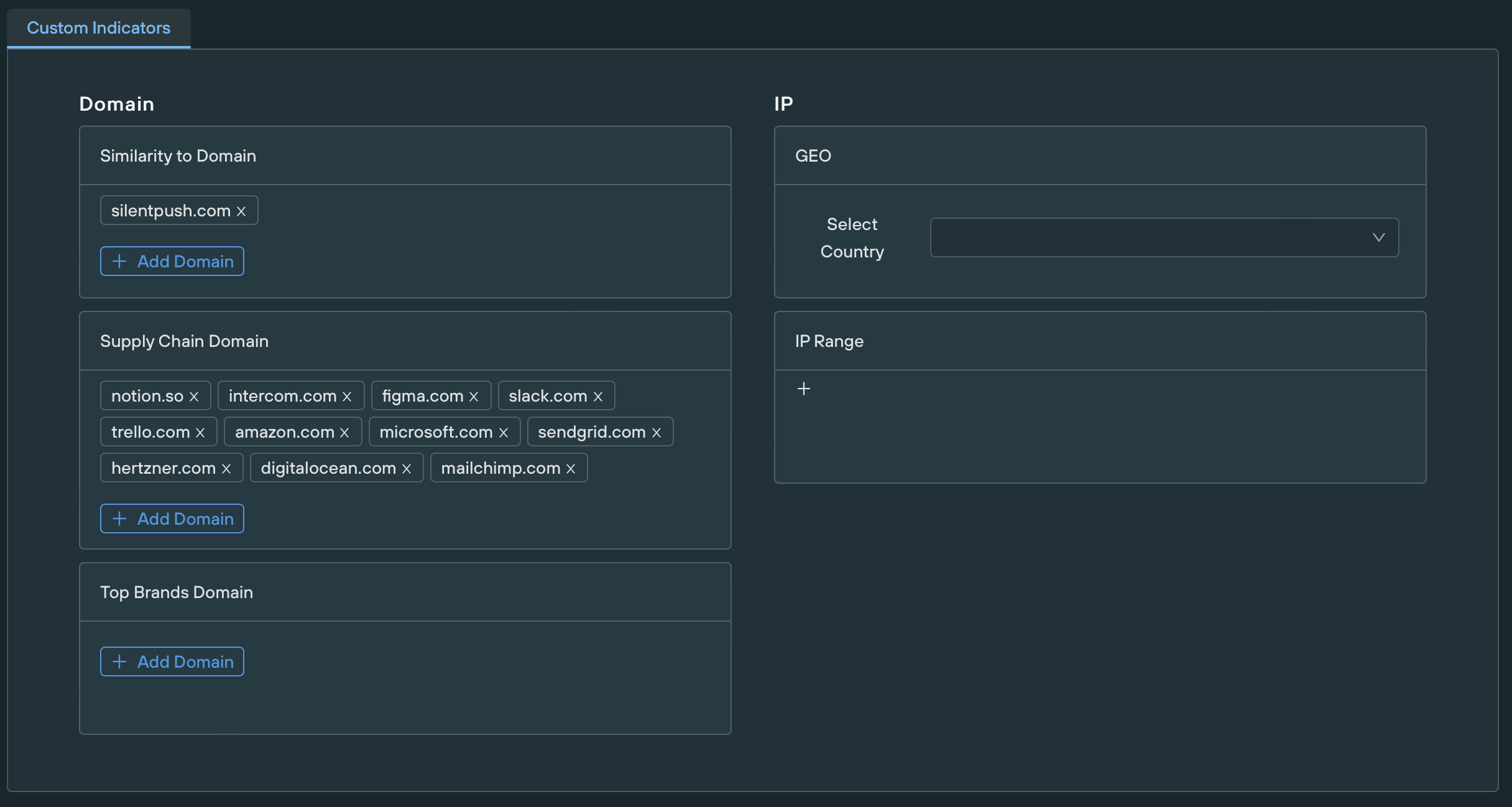
Organization Assets
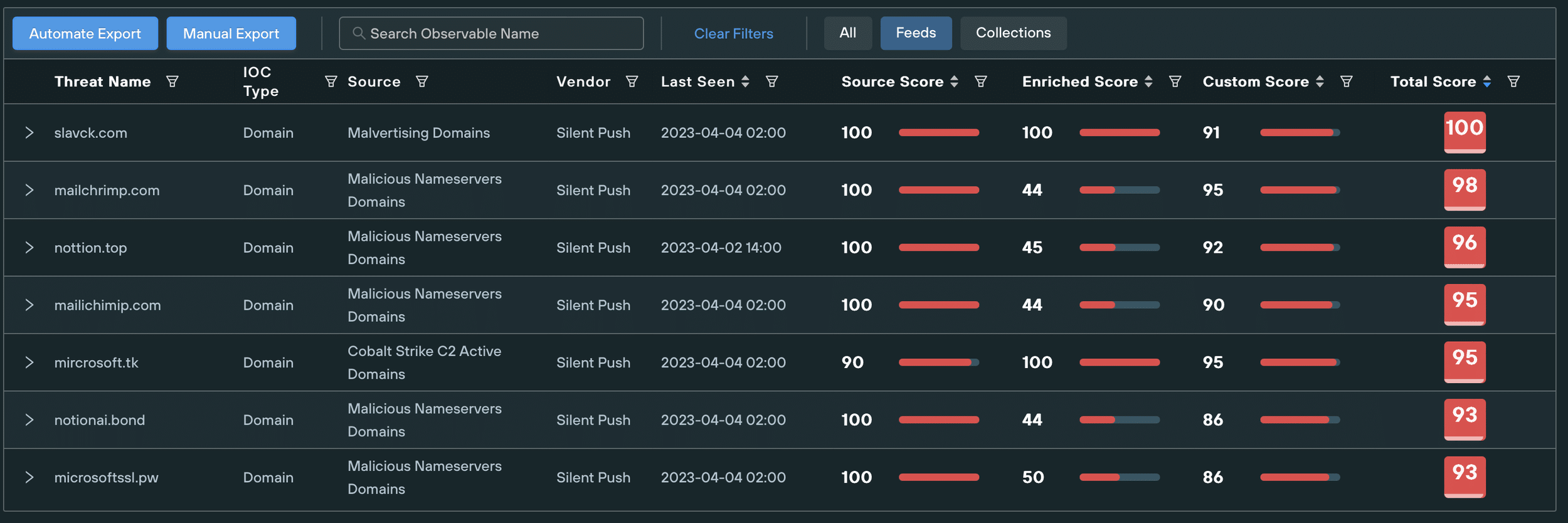
Filtered Threat Ranking page showing IoCs similar to Organization Assets
Takeaways
SaaS and third-party solutions are an integral part of the digital landscape and are often crucial to companies’ operationality and growth. Be it to provide cost-efficient scalability, or to allow more agile management, there are many good reasons to keep SaaS platforms as a part of your tech stack.
Third-party solutions are not inherently dangerous. The risk associated with them stems from lacking security tools and frameworks that don’t integrate associated infrastructure into threat management efforts. Correctly using tools like the Silent Push App allows you to make the most out of SaaS and third-party solutions without creating unnecessary risks to your enterprise’s security.
Take advantage of Silent Push’s vast array of threat defense tools by signing up for our free Community App.


