Eight-legged Phreaks: Silent Push DNS and content scans discover new Scattered Spider phishing infrastructure.

Key Points
- New Scattered Spider infrastructure discovered on Hostinger
- Silent Push content scans confirm the re-use of 2022 infrastructure to propagate new attacks
- Malicious domains parked prior to weaponization, possibly to avoid reputation degradation
- Silent Push HTML header and favicon scans used to pinpoint phishing kits across hundreds of new domains
Background
Scattered Spider are a financially motivated threat group who has been active since the second quarter of 2022.
The group is known for launching sophisticated social engineering attacks designed to obtain login credentials and MFA tokens from employees.
Scattered Spider have been responsible for hundreds of incidents in the past year, two of which generated a large amount of media interested and caused significant financial and reputational harm for the organizations involved: the Twilio/Okta breach of August 2022 and the MGM breach of September 2023.
Attacks commonly commence with sustained SMS phishing messages sent to the mobile phones of both current and former employees of the targeted organization.
Infrastructure and attack vectors
Scattered Spider phishing pages are hosted on short-lived domains that are created and hosted using bitcoin-friendly services, featuring typosquats of the targeted brand or the exact brand name followed or preceded by keywords such as ‘okta’, ‘help’, ‘sso’, and ‘servicedesk’.
The use of US registrars and providers, US carrier networks for voice and SMS phishing campaigns, the clear North American accent reported by the victims and the modus operandi of targeting US enterprises, indicates that Scattered Spider is focused on targets within the USA.
Throughout last year’s attacks, Scattered Spider used a small number of services to create and host malicious infrastructure:
2022 registrars:
- Porkbun
- NAMECHEAP
2022 ASNs
- DIGITALOCEAN (AS14061)
- AS-CHOOPA (AS20473)
- AKAMAI-LINODE-AP (AS63949)
- NAMECHEAP-NET (AS22612)
Data is exfiltrated once the threat actor obtains login credentials that provide an opportunity for lateral or elevated network movement, via a combination of techniques including a signed driver that terminates security processes, and VM admin console access via Azure Serial Console.
Front-end infrastructure shares the same code, e.g. the same favicon, ssdeep data and HTML title (‘Sign In’). The threat actor performs a call to the C2 server to obtain the target company’s name and logo, and the kit calls two legitimate Okta scripts.
Motivation
Scattered Spider uses stolen data to propagate secondary attacks across the user base of the affected company, and its supply chain operation.
This, in part, explains why the group focuses their efforts on organizations with a large amount of downstream users that aren’t directly attributed with the target organization: telecommunications providers, software and technology companies, Business Process Outsourcing (BPO) providers, and cryptocurrency platforms.
Using Silent Push data to uncover new infrastructure deployed via Hostinger
Over the past 90 days, Threat Analysts working with Silent Push first-party data have observed an increase in the number of domains created by Scattered Spider targeting organizations in the financial, insurance, investment, food ordering and delivery, retail and entertainment sectors.
Silent Push offers a monitoring feature that allows analysts to setup rules for domains or IPs that triggers an alert when a specific DNS change is detected. Silent Push analysts were researching Scattered Spider’s 2022 Twilio attack, and noticed new domains appearing in the results set.
Silent Push logs and tracks registrar and ASN information, including hosting changes, for every domain on the IPv4 scope. A large number of the new domains were registered through, and hosted on, providers not previously used by the group, indicating a notable expansion of infrastructure.
Identifying and tracking a new phishing kit
Whilst scanning for new domains, we discovered that two legacy domains which were created and used by the threat actor during 2022, t-mobile-okta[.]com and rogers-rci[.]com, had recently been re-registered via Hostinger on October 1 2023 and October 16 2023 respectively – a new registrar that Scattered Spider are not known for using (usually the group registers their infrastructure via Porkbun and NAMECHEAP).
It’s not uncommon for malicious domains to be re-registered – organizations acquire previously weaponized domains to analyze traffic or prevent them being re-used by threat actors – but we discovered that t-mobile-okta[.]com featured an active Okta-themed phishing page, one week after creation.
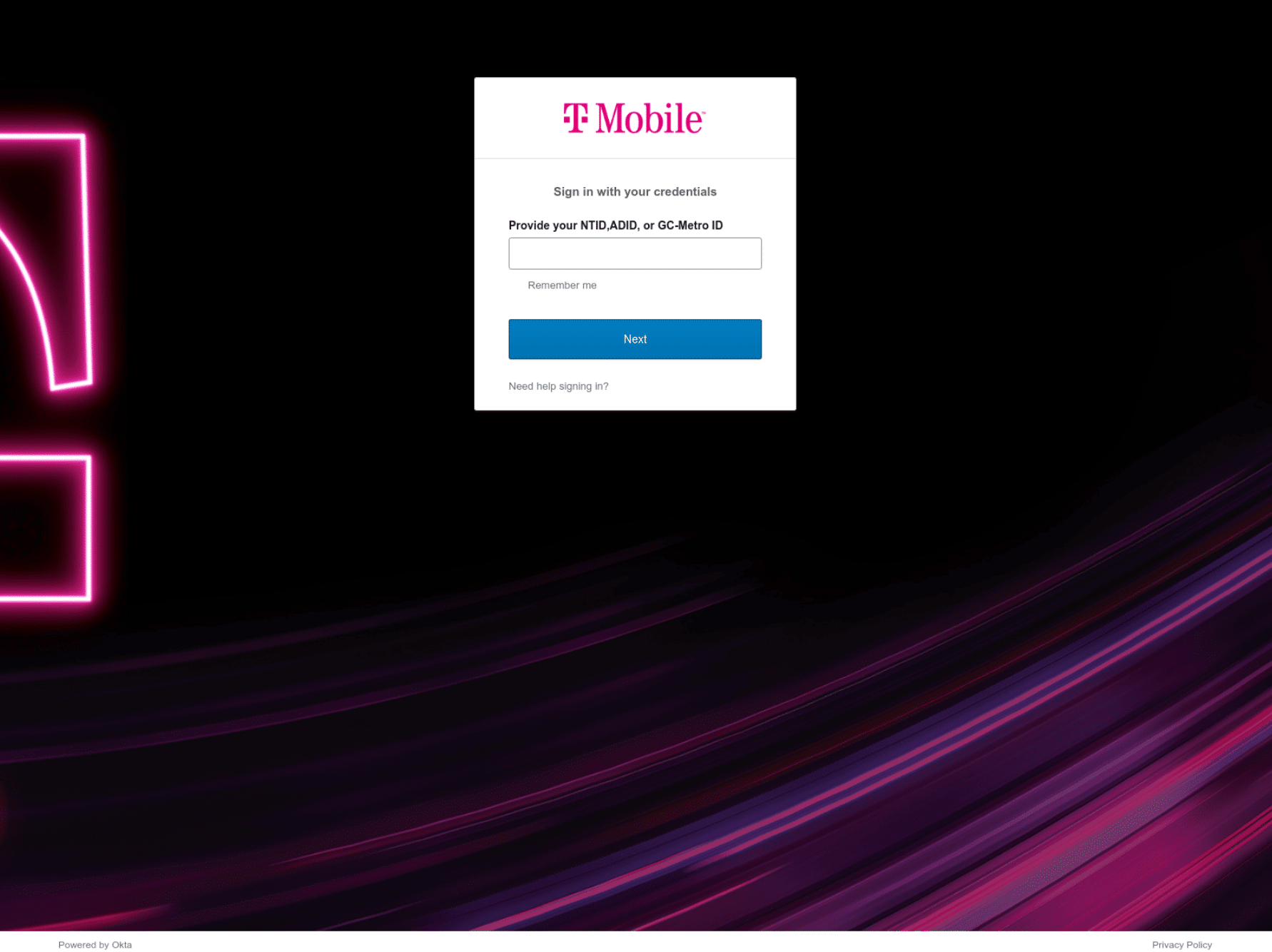
t-mobile-okta[.]comScattered Spider are known to use a variety of phishing kits, including ones available on underground forums. A quick search through the Silent Push hash content database established that the above domain contains a new phishing kit that’s deployed on all Scattered Spider domains registered since September 20223 (neither the Silent Push database nor third-party URL scanners such as urlscan.io show any matches pre-September).
Domain scans revealed that the phishing page was up for a little over a day – a common characteristic of most Scattered Spider domains.
Historical scan results also revealed that the domain was aged, given that it displayed the Hostinger parked paged in the days prior to the attack. The threat actor likely uses this technique to avoid reputation degradation across global scoring systems.
To recap:
- We discovered re-registered Scattered Spider phishing domains
- One of them hosted a phishing kit with content resembling the type found in previous attacks
- The TTL of the phishing page was in line with historical activity
- The Registrar was DIFFERENT than previously seen from Scattered Spider (Hostinger in 2023 vs Namecheap or Porkbun in 2022)
- The domains were aged, possibly after re-registration
Validating malicious domains using the Silent Push Domain Search
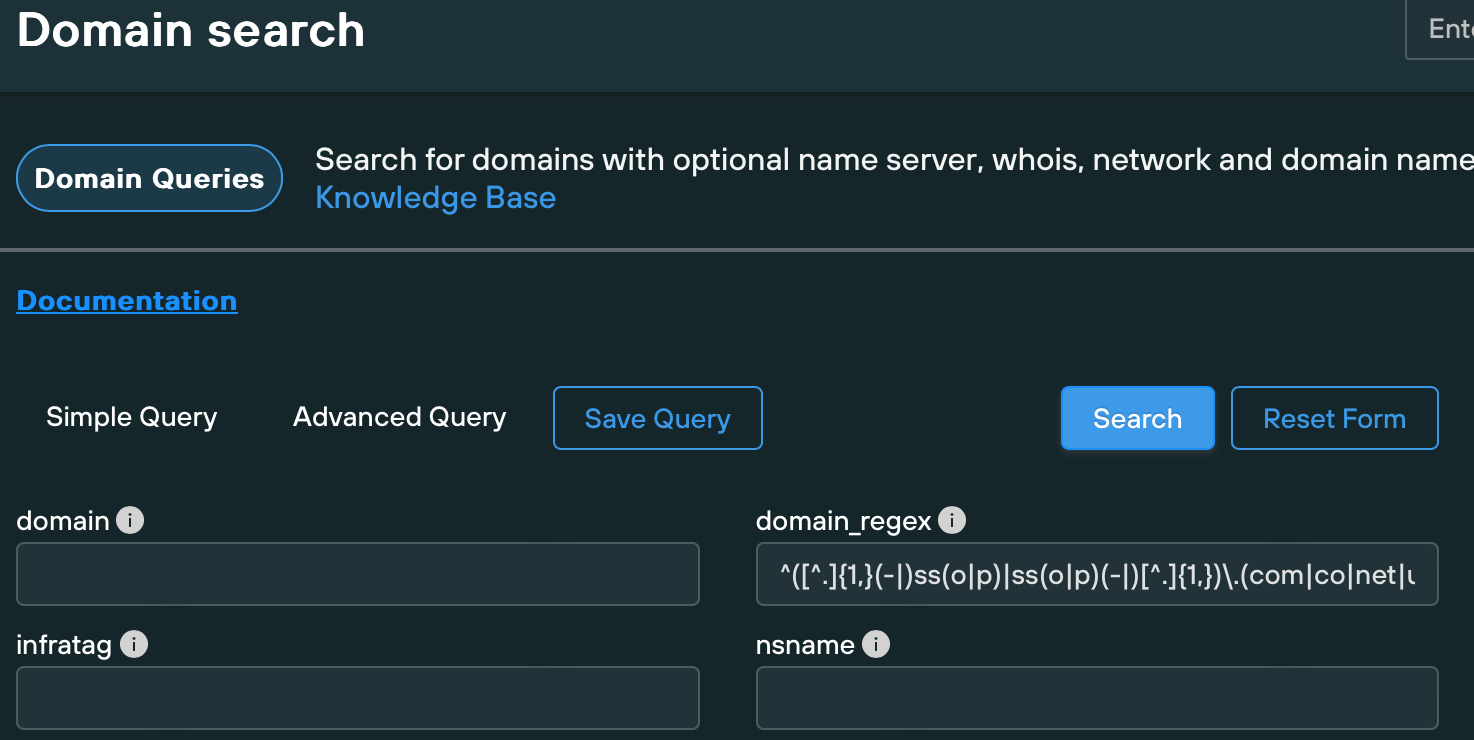
To confirm our hypothesis, we searched the Silent Push database for any domains created and hosted on Hostinger since September 2023, that matched Scattered Spider naming conventions, using custom regex parameters on the Silent Push Domain Search Query.
Regex examples:
^([^.]{1,}(-|)ss(o|p)|ss(o|p)(-|)[^.]{1,})\.(com|co|net|us|help)$^([^.]{1,}(-|)okta|okta(-|)[^.]{1,})\.(com|co|net|us|help)$^([^.]{1,}(-|)h(e|1)lp(|desk|now)|h(e|1)lp(|desk|now)(-|)[^.]{1,})\.(com|co|net|us|help)$^([^.]{1,}(-|)my|my(-|)[^.]{1,})\.(com|co|net|us|help)$
Working with false positives
In the above syntax, we included the hyphen character as optional, given that Scattered Spider doesn’t always enforce a hyphen between the brand name and the keyword. This results in a broader results set that may return a higher number of false positives.
Enforcing the hyphen as mandatory between the keyword and the brand name returns a smaller amount of domain that whilst not covering the maximum amount of infrastructure, returns a fewer false positives.
Confirming the presence of malicious infrastructure
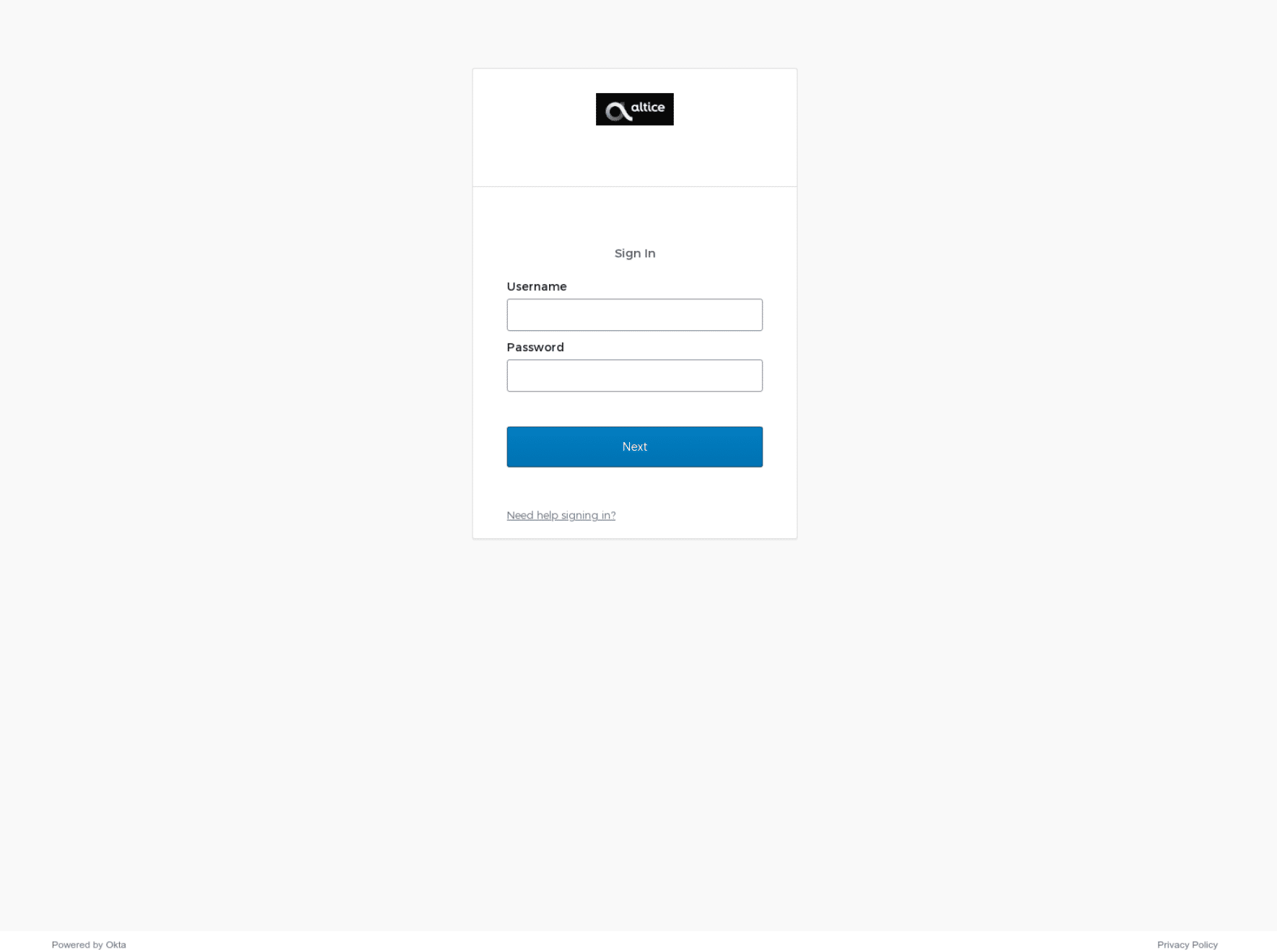
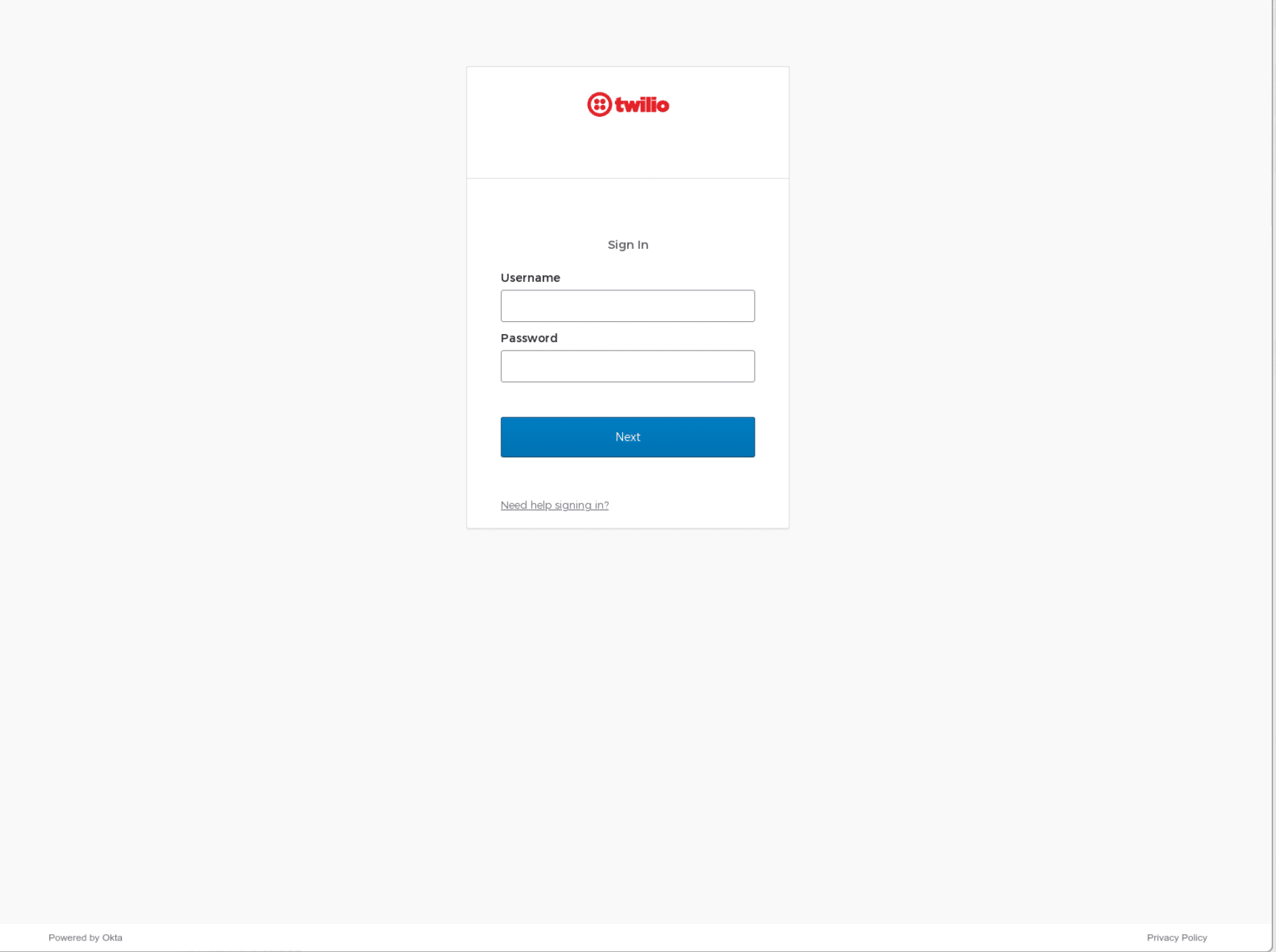
The above search returned hundreds of suspicious domains. We used some query parameters available through the Silent Push API and our custom query language, SPQL, to interrogate the dataset and discovered that a large number of the returned domains featured matching content and scripts, indicating the presence of a common phishing kit.
We accessed these domains using a browser and confirmed it is highly likely that they were created and launched by Scattered Spider – they all contained an Okta phishing page targeting commercial sectors that Scattered Spider have historically gone after, including Financial, Telecommunications, Software/Cloud Communications Platforms and CMR.
Here’s a sample of what we discovered:
53help[.]orgaitice-usa[.]comatt-my[.]comatt-networks[.]netbbt-work[.]comcashsso[.]comfedsso[.]netfreshworks-sso[.]comfreshworks-sso[.]netfreshworksso[.]comgrayscale-sso[.]comgrayscalesso[.]comgraysso[.]commy-twilio[.]compodiumsso[.]comssopodium[.]comssotelnyx[.]comtelnyx-sso[.]comtelnyxsso[.]comvictrasso[.]comvictrasso[.]networkbbt[.]com
Investigating the re-use of old infrastructure
Some of the above domains were weaponized the moment they were created, whilst others were aged for days or weeks, suggesting that Scattered Spider were either in a hurry to deploy elements of their infrastructure or are possibly weaponizing domains to deliberately erratic schedules in order to avoid detection. rogers-rci[.]com was re-registered more than two months ago, yet still presents the Hostinger parked page.
After confirming that Scattered Spider are now using a different method of registering and hosting their infrastructure, we scanned for newly registered domains that used the old infrastructure, on the following parameters:
- Registered on Porkbun and NAMECHEAP (i.e. the 2022 Registrars)
- Registered from September 2023
- Featured HTML content that indicated a Scattered Spider phishing page
- Used the following ASNs from 2022:
- DIGITALOCEAN (AS14061)
- AS-CHOOPA(AS20473)
- AKAMAI-LINODE-AP(AS63949)
- NAMECHEAP-NET(AS22612)
Here’s a sample of the hundreds of domains we discovered:
activesso[.]comactlvecampaign[.]netassurionsso[.]netasurionsso[.]combbt-hr[.]combbtemps[.]combbthour[.]combbtplus[.]combbtvpn[.]comconnect-cox[.]comdashsso[.]comhubsso[.]netintercomsso[.]netklaviyocorp[.]netpostmarksso[.]comtelesignsso[.]comtrustsso[.]comworkatbbt[.]comxn--gryscale-ox0d[.]com
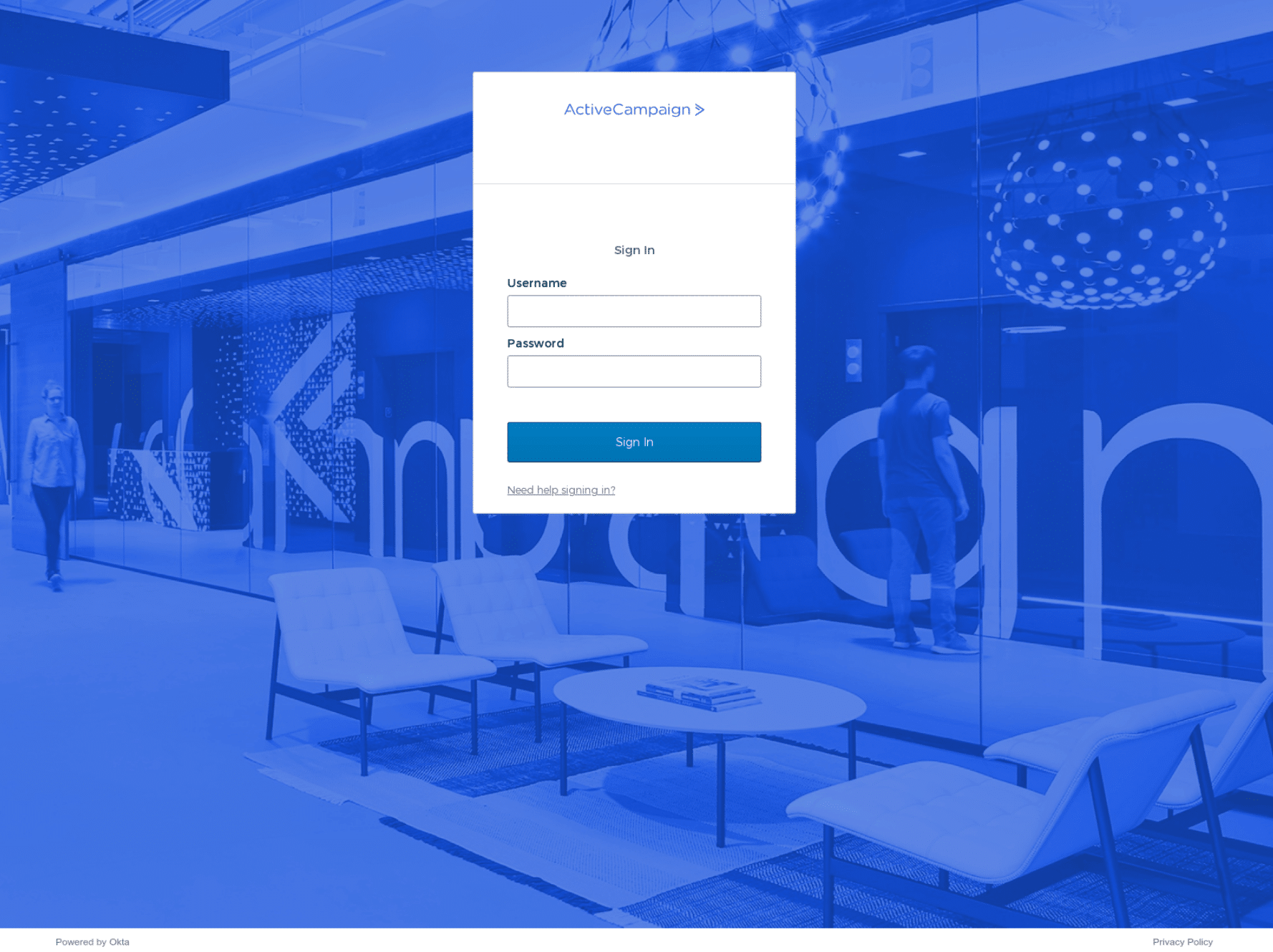
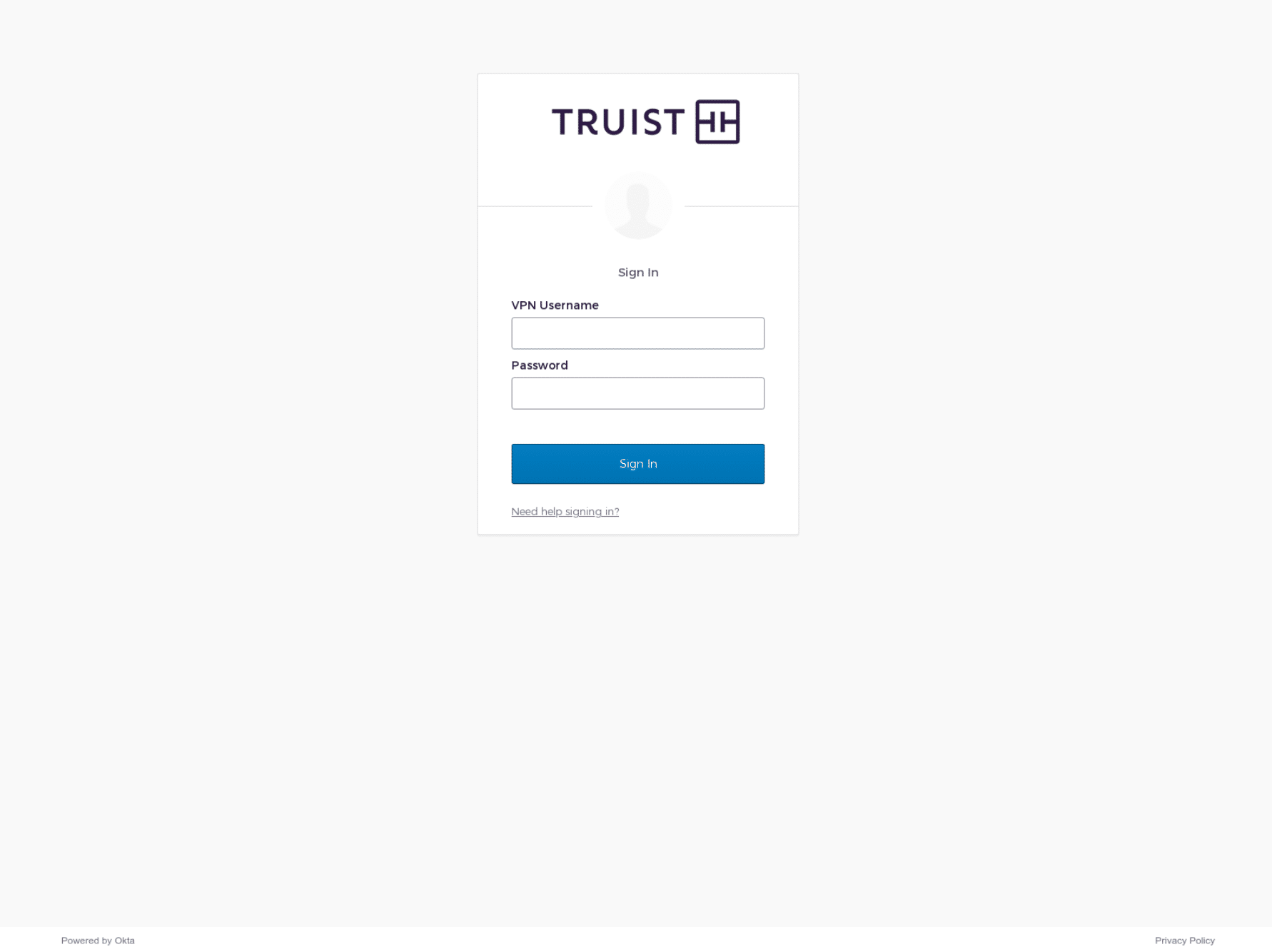
Prevention
All of the domains that we have listed in this blog contained active phishing pages at the point of discovery, but there are potentially hundreds of others that are being aged in preparation for an attack.
Scattered Spider’s deployment methods feature identifiable patterns and commonalities that allow Silent Push users to discover associated infrastructure and enumerate the threat actor’s online presence, using an array of lookups that can be tailored to a unique set of requirements.
Applicable queries
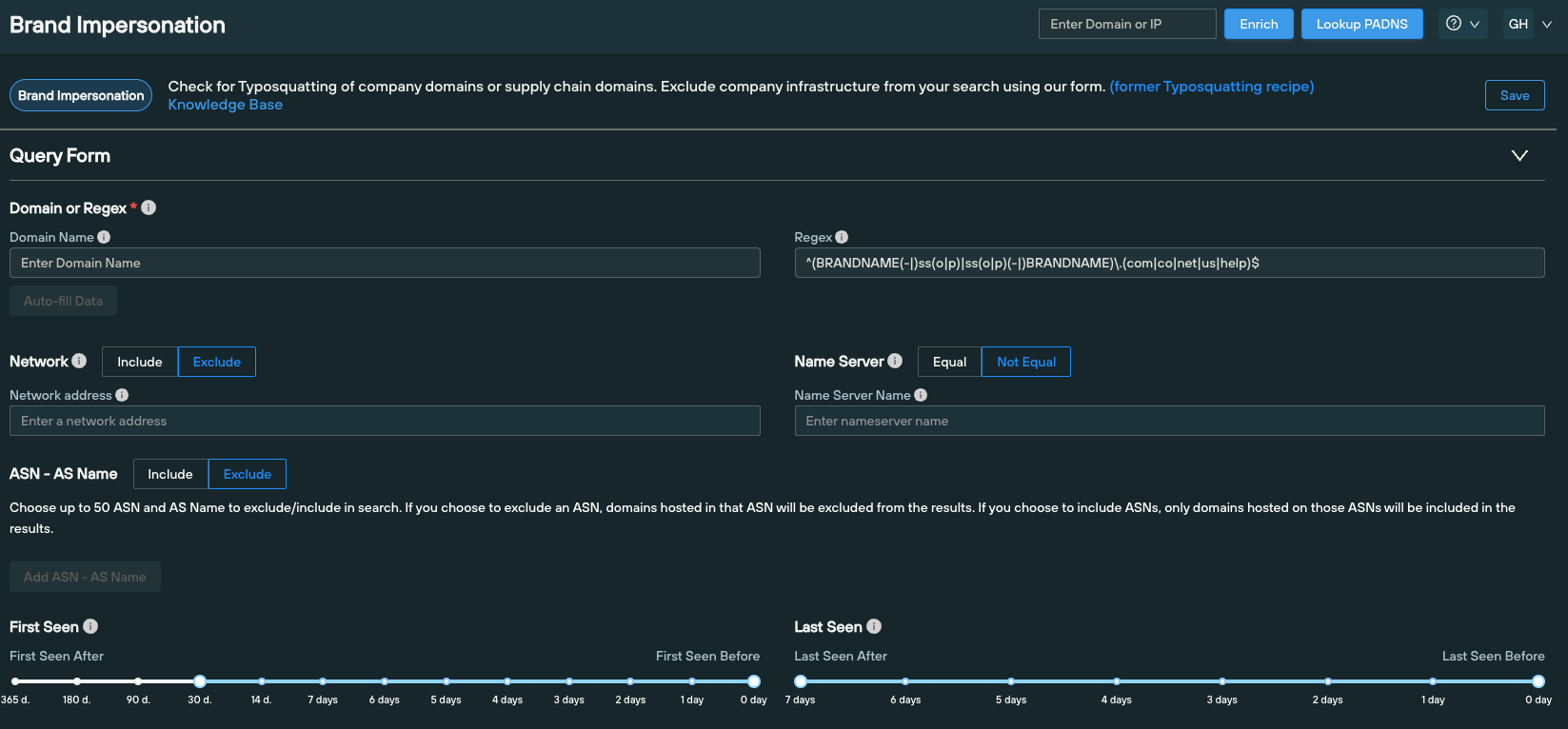
Silent Push Community and Enterprise users should execute the following Brand Impersonation queries to detect and monitor Scattered Spider brand spoofing campaigns that feature common naming conventions, targeting their own infrastructure:
- ^(BRANDNAME(-|)ss(o|p)|(o|p)(-|)BRANDNAME)\.(com|co|net|us|help)$Looks for a domain as a brand name, followed or preceded by SSO or SSP (typosquatted version of SSO), with an optional hyphen between company name and keyword, on those 5 TLDs.
- ^(BRANDNAME(-|)okta|okta(-|)BRANDNAME)\.(com|co|net|us|help)$Looks for a domain as a brand name followed or preceded by Okta, with an optional hyphen between company name and keyword, on those 5 TLDs.
- ^(BRANDNAME(-|)h(e|1)lp(|desk|now)|h(e|1)lp(|desk|now)(-|)BRANDNAME)\.(com|co|net|us|help)$Looks for a domain as a brand name followed or preceded by a typosquatted version of ‘helpdesknow’, with an optional hyphen between company name and keyword, on those 5 TLDs.
- ^(BRANDNAME(-|)my|my(-|)BRANDNAME)\.(com|co|net|us|help)$Looks for a domain as a brand name followed or preceded by “my”, with an optional hyphen between company name and keyword, on those 5 TLDs.
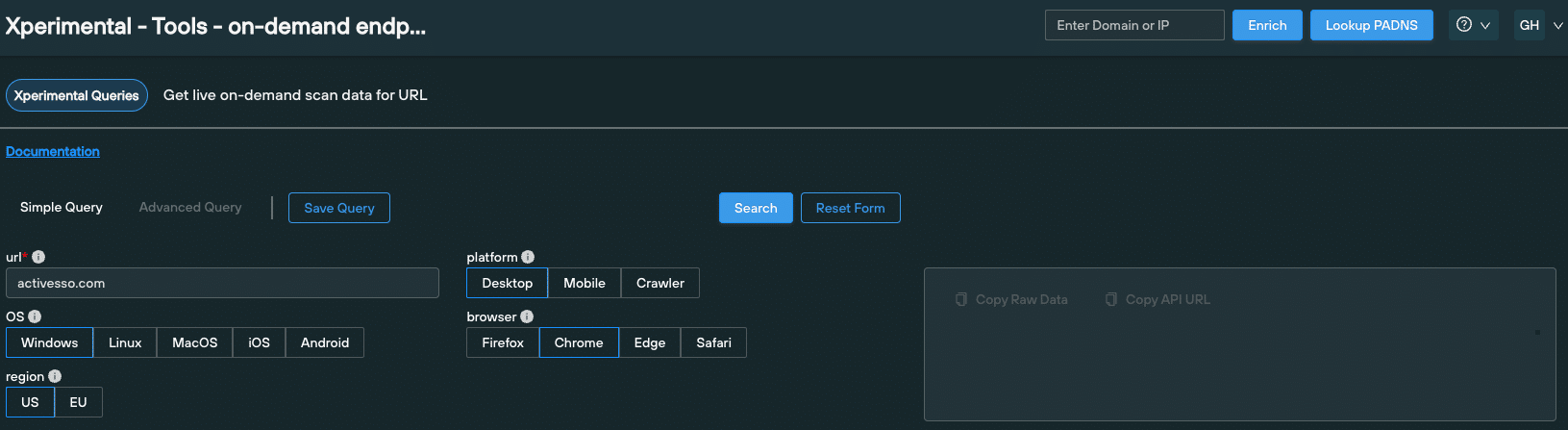
Silent Push users should also make use of the platform’s On-Demand Endpoint Scan to locate infrastructure featuring the same phishing kit content, by harvesting HTML title, page content, SSL information and favicon hash data from a single URL.
Early Detection Feeds
Silent Push Enterprise users benefit from two Early Detection Feeds – ‘Scattered Spider Domains and IPs’ and ‘Scattered Spider Suspected Domains and IPs’ – that allow security teams to track and monitor Scattered Spider infrastructure either using the Silent Push console, or via an API that enriches an existing security stack with realtime threat data.
Register for Silent Push Community Edition
All of the lookups and datasets we used to detect and traverse Scattered Spider’s phishing infrastructure are available via Silent Push Community Edition – a free threat hunting platform available to security pros, researchers and analysts, including:
- Brand Impersonation queries
- Advanced domain searches
- URL-based HTML content scans
IOFAs
actlvecampaign[.]netactivesso[.]comassurionsso[.]netasurionsso[.]combbt-hr[.]combbtemps[.]combbthour[.]combbtplus[.]combbtvpn[.]comconnect-cox[.]comdashsso[.]comhubsso[.]netintercomsso[.]netklaviyocorp[.]netpostmarksso[.]comtelesignsso[.]comtrustsso[.]comworkatbbt[.]comxn--gryscale-ox0d[.]com53help[.]orgaitice-usa[.]comatt-my[.]comatt-networks[.]netbbt-work[.]comcashsso[.]comfedsso[.]netfreshworks-sso[.]comfreshworks-sso[.]netfreshworksso[.]comgrayscale-sso[.]comgrayscalesso[.]comgraysso[.]commy-twilio[.]compodiumsso[.]comssopodium[.]comssotelnyx[.]comtelnyx-sso[.]comtelnyxsso[.]comvictrasso[.]comvictrasso[.]networkbbt[.]com

