In October 2022, we published research that detailed how threat actors were using a ScreenConnect exploit to inject malware onto users’ machines.
ScreenConnect is back in the news again, with a widely-publicized authentication vulnerability first confirmed by ConnectWise on February 19th. Prominent security vendors (led by Huntress) subsequently published numerous reports on how simple it was to replicate and weaponize the exploit.
Since then, Mandiant has released a post-incident remediation and hardening guide for on-premise mitigation.
Summary
In this blog, we’ll explore how Silent Push analysts captured 60+ IP addresses linked to ScreenConnect threat activity, how we constructed a map of global servers, and a timeline of events starting with the initial discovery.
For a free snapshot of 50+ IPs to plumb into your security stack, scroll to the end of this blog.
ScreenConnect exploit honeypot
To help minimize the global impact of what could well turn into the largest security vulnerability event of the year, Silent Push threat analysts have successfully implemented a honeypot server that’s actively collecting the IP addresses of would-be attackers every hour, and gathering them together into a feed for our Enterprise users.
Note: An IP address is only placed in our ScreenConnect feed if an attacker attempts to trigger the vulnerability.
As of writing, we’ve collected 60+ IPv4 Indicators of Future Attack (IOFA). With threat groups leveraging the exploit to deploy ransomware, cryptocoin miners and infostealers on infected systems (most notably LockBit), we expect this number to increase dramatically over the coming weeks.
Mapping vulnerable ScreenConnect exploit servers
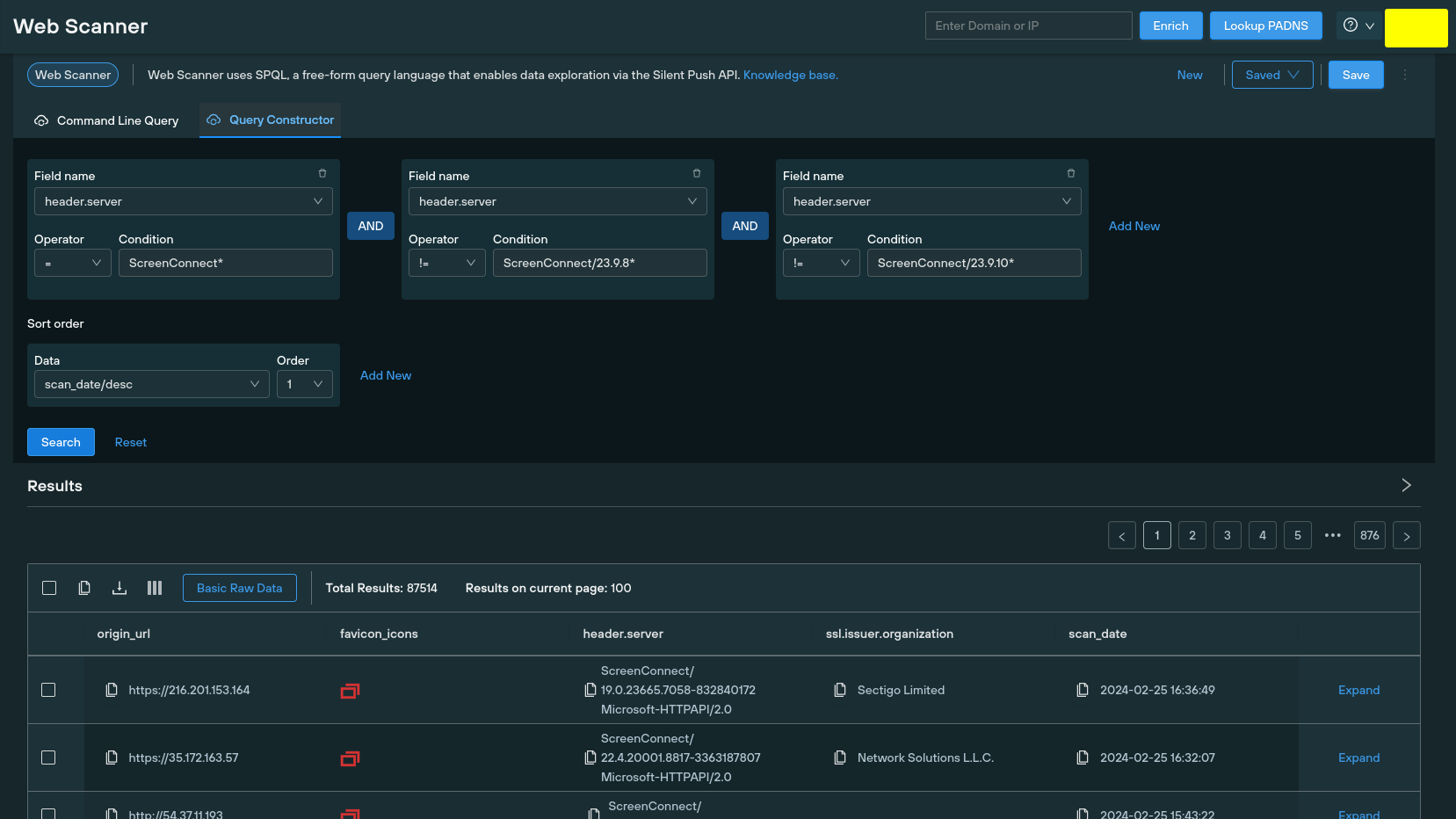
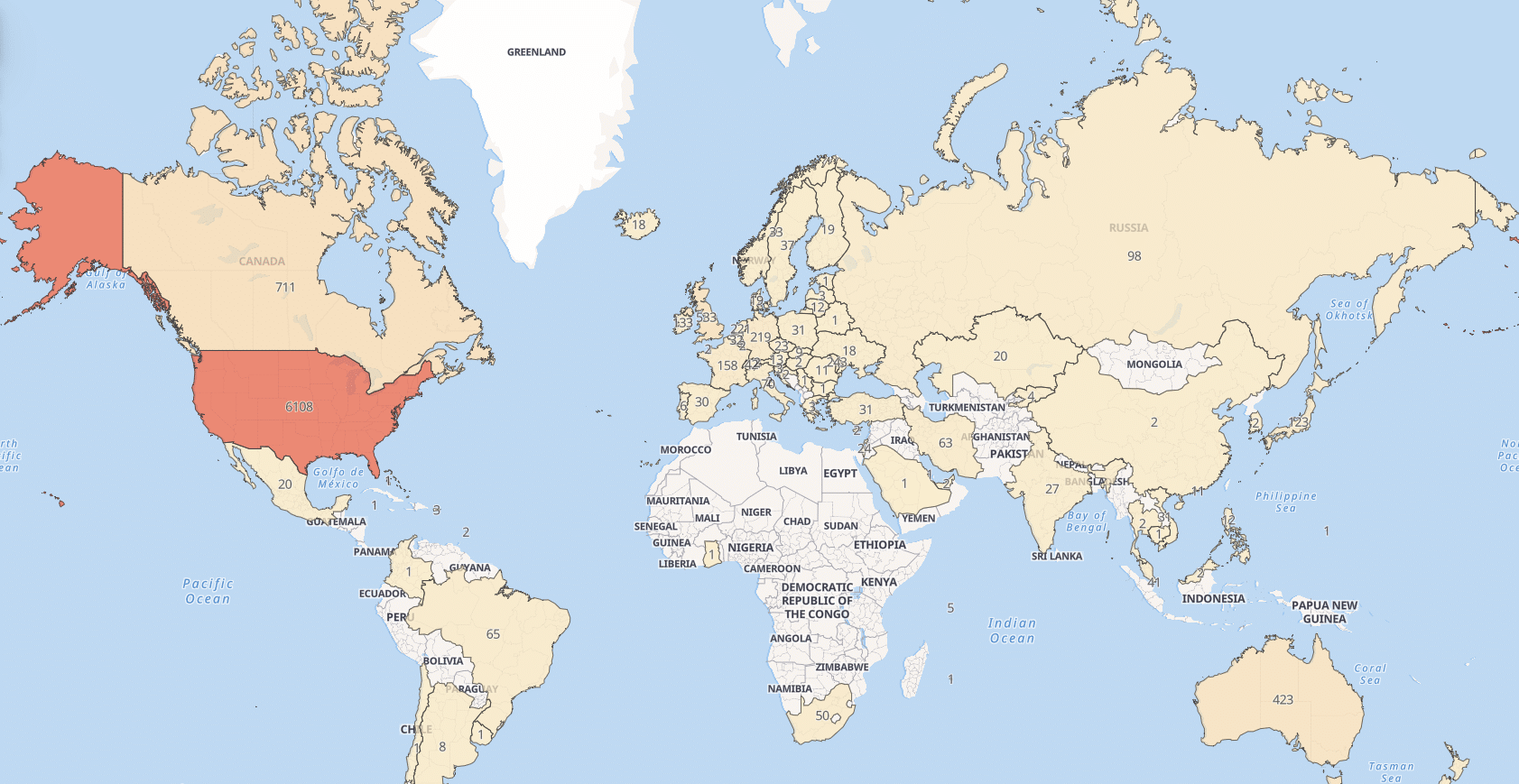
Silent Push Web Scanner allows you to search through a passive database of web content, including on-page data, HTML titles and server headers. ScreenConnect servers return the version number in their header data. Our analysts used a Web Scanner query to conduct a global search of servers running version 23.9.7* or previous, to obtain a global dataset that we mapped to each region:
Query syntax: header.server = "ScreenConnect*" AND header.server != "ScreenConnect/23.9.8*" AND header.server != "ScreenConnect/23.9.10*"
All Web Scanner queries can be executed using a ‘Constructor’ feature, along with the standard command line syntax. Here’s the ScreenConnect query in action:
ScreenConnect exploit timeline
February 13
- ConnectWise starts to receive reports (via the ConnectWise Trust Center) of an authentication vulnerability related to ScreenConnect, within on-premise servers running version 23.9.7 and prior.
- ConnectWise declares that they found no evidence of the vulnerabilities being actively exploited in the wild.
February 13/14
- ConnectWise validates the vulnerability, which was reported to them by an independent security researcher.
February 15
- ConnectWise applies manual mitigation to cloud-hosted ScreenConnect instances, and urges all on-premise partners to immediately update their servers to version 23.9.8 to apply a patch.
- ConnectWise suspends outdated ScreenConnect instances, while organizations apply the patch.
February 19
- ConnectWise officially announce the vulnerability in a security bulletin, with a severity of “Critical” and a priority of “1 – High”:, including remedial actions required and two corresponding NIST Common Vulnerabilities and Exposures (CVE) entries:
| CWE ID | CVE ID | Description | Base score |
| CWE-288 | CVE-2024-1708 | Authentication bypass using an alternate path or channel | 10 |
| CWE-22 | CVE-2024-1709 | Improper limitation of a pathname to a restricted directory (“path traversal”) | 8.4 |
- ConnectWise provides updated versions of releases 22.4 through 23.9.7 for remediation.
- ConnectWise are yet to acknowledge instances of exploitation in the wild.
- Huntress publish a blog stating that their researchers have “successfully created and validated a proof-of-concept exploit” for both CWEs, and claim that over 8,800 servers are running vulnerable ScreenConnect instances.
February 20
- ConnectWise receive notification of active threat campaigns targeting unpatches instances, and release three IP addresses known to be engaging in malicious activity:
- 155.133.5[.]15
- 155.133.5[.]14
- 118.69.65[.]60
- Huntress publish a blog confirming that they have reproduced and weaponized the attack chain for CWE-288 (“Authentication bypass using an alternate path of channel”) with “ease and minimal technical knowledge and resources”. In the blog, Huntress provide a detailed explanation of how to detect the exploit, including XML file contents, event data and disk activity.
February 21
- Multiple security vendors begin sharing a proof-of-concept exploit.
- Huntress publish a blog that includes forensic examination of the attack chain. The authentication bypass and remote code execution element are demonstrated via a series of Linux shell commands that take all of the 30 seconds to complete.
- ScreenConnect 23.9.10.8817 is released.
- ConnectWise removes license restrictions, enabling customers no longer covered by a maintenance agreement to upgrade to ScreenConnect 23.9.10.8817 as an “interim step”.
February 22
- ConnectWise suspends ScreenConnect instances that are not running version 23.9.8 or later. Affected users are sent alerts on login with instructions on how to upgrade, with the following upgrade path:
- 2.1 → 2.5 → 3.1 → 4.4 → 5.4 → 19.2 → 22.8 → 23.3 → 23.9.
- Silent Push begins scanning the IPv4 range for server headers that identify affected servers below version 23.9.8*.
- Silent Push creates a “honeypot” IP, mimicking a ScreenConnect server header with a fake front page as bait, and begins populating an Early Detection Feed with attacker IPs.
February 23
- Multiple sources report on threat actors leveraging the exploit to deploy ransomware, infostealer and cryptocoin miners on infected systems, most notably LockBit.
- Mandiant publish a remediation and hardening guide for all ConnectWise.
ScreenConnect exploit IOFAs
Here’s a list of IP addresses that have initiated attacks on our honeypot server, as of 26 Feb.
Enterprise customers have access to a realtime list of adversary IPs.
- 155.133.5[.]14
- 116.0.56[.]101
- 64.31.63[.]240
- 118.69.65[.]60
- 185.220.101[.]109
- 206.189.150[.]171
- 36.19.230[.]138
- 47.243.72[.]174
- 79.137.204[.]241
- 185.196.8[.]220
- 185.174.137[.]26
- 85.192.41[.]211
- 38.180.54[.]210
- 45.9.249[.]238
- 149.28.197[.]45
- 207.180.217[.]230
- 139.227.34[.]124
- 20.210.105[.]88
- 191.96.36[.]99
- 191.101.217[.]122
- 154.57.3[.]32
- 135.181.175[.]26
- 126.108.60[.]57
- 123.252.45[.]246
- 185.231.205[.]31
- 94.131.101[.]37
- 213.230.93[.]76
- 24.251.120[.]147
- 46.249.38[.]211
- 194.156.98[.]18
- 193.252.215[.]164
- 89.39.107[.]191
- 169.150.202[.]67
- 194.116.217[.]176
- 91.92.248[.]164
- 91.92.247[.]58
- 173.239.232[.]10
- 173.239.232[.]3
- 173.239.232[.]33
- 91.92.254[.]160
- 173.239.232[.]30
- 104.28.222[.]75
- 176.160.145[.]191
- 176.130.45[.]168
- 172.58.109[.]243
- 46.232.121[.]61
- 88.209.197[.]8
- 38.181.70[.]150
- 103.170.154[.]83
- 209.127.228[.]186
- 38.207.173[.]102
- 223.26.103[.]16
- 195.26.87[.]209
- 185.56.83[.]82
- 103.166.86[.]29
- 172.56.201[.]183
- 155.133.5[.]15
ScreenConnect exploit assistance
If you’ve been affected by the recent ScreenConnect exploit, or you’d like to learn more about how Silent Push can help your organization stop attacks before they become a problem, get in touch today.


