- Scammers harvesting personal information and payment card details from fake websites.
- Big name clothing and footwear brands affected in multiple countries.
- Dangers for global consumers in the run-up to Cyber Monday and Black Friday.
- Hoax websites appearing on the first page of search results.
The holiday season is nearly upon us. With Black Friday and Cyber Monday fast approaching on the 25th and 28th November, and with 60% of adults planning to start their Christmas shopping before December, the accelerated digitization of shopping habits throughout the COVID-19 pandemic has retailers crossing their fingers for an early rush to online checkouts.
Last year, US consumers alone spent $204.5 billion online during the holiday season, and the global ecommerce market is set to top $5.5 trillion by the end of the year.
Unfortunately, it’s not only big name brands that are vying for consumers’ attention.
Silent Push Threat Analysts have uncovered an enormous fake ecommerce network – featuring high-end brands and thousands of hoax websites – that’s fooling unsuspecting shoppers into handing over personal data and payment card information in a global online shopping scam, affecting household names from around the world of retail, including:
- Versace
- Prada
- Puma
- Nike
- Ted Baker
- Converse
- Nautica
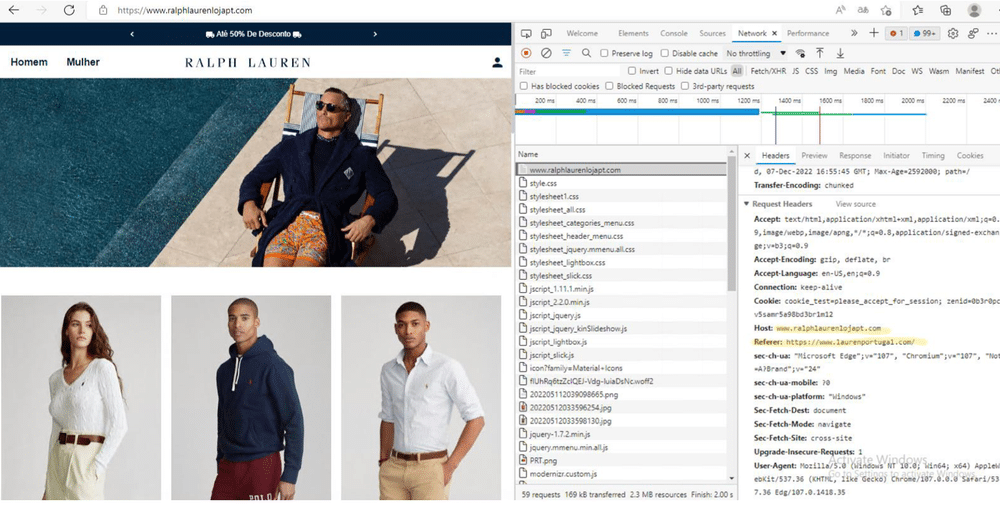
- Ralph Lauren
- Lacoste
- Quicksilver
- Timberland
- Vans
- The North Face
- La Perla
- Ugg
The method
Capturing traffic
To redirect consumer traffic away from genuine companies, the scammers register domain names that mimic a brand’s legitimate online presence – usually by adding words to the company name, spelling words differently, or targeting a brand’s presence in a particular country.
Once the site is live, the scammers install an SSL certificate, allowing them to hide behind what appears to be a valid identity, using HTTPS and a padlock icon to build legitimacy with unsuspecting visitors:
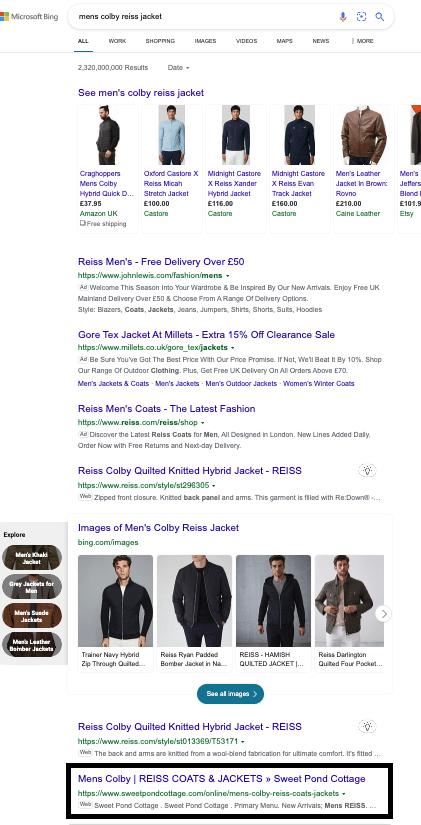
To make matters worse, the scammers have managed to get their websites listed on the front page of prominent search engines such as Bing, Yahoo and DuckDuckGo.
A search on Bing for a popular product from global fashion retailer Reiss displays a scam website (sweetpondcottage[.]com) on the front page, underneath the company’s legitimate website, and well-known outlets such as John Lewis and Millets:
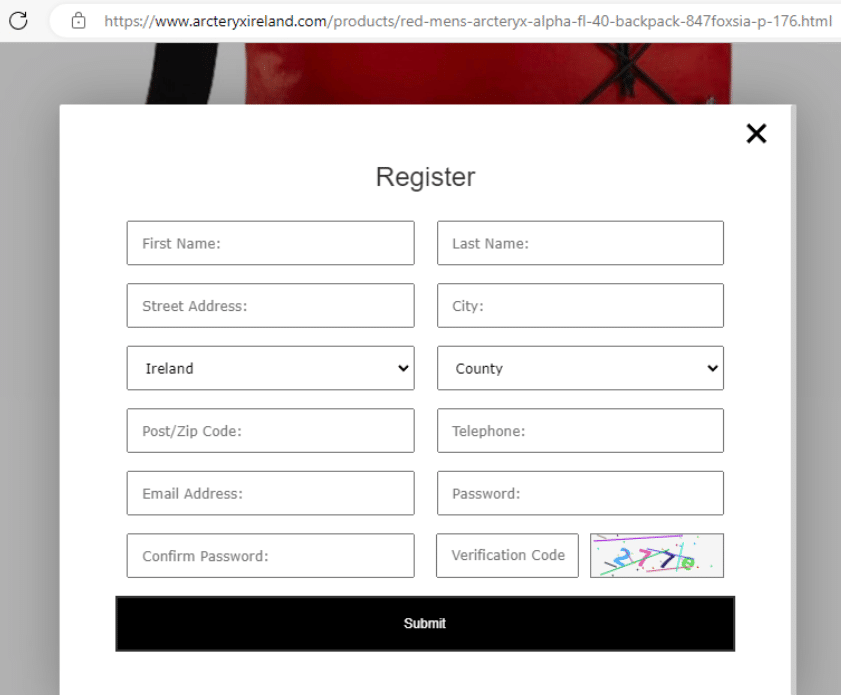
Fake sign-up forms
All of the websites we uncovered feature a registration page that’s designed to steal Personally Identifiable Information (PII) and password data, and with over half of online consumers regularly using the same password combinations for work and personal accounts, there’s almost no end of damage that can be done when that data falls into the wrong hands.
Phony product pages
To get at consumer’s payment card details, the websites present visitors with what appear to be legitimate high-end products, offered at a significant discount (usually within the $50-$200 price range) compared to their standard RRP.
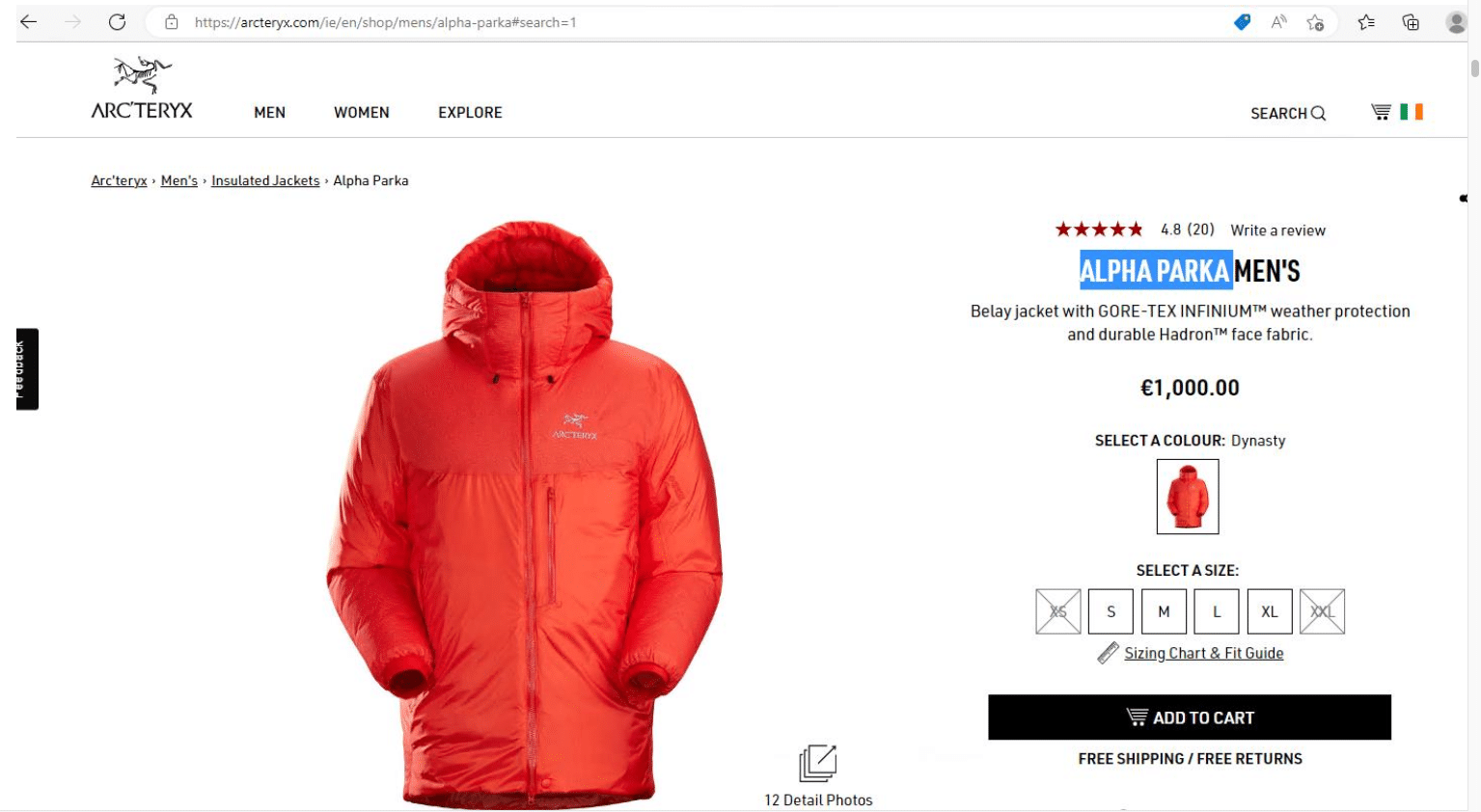
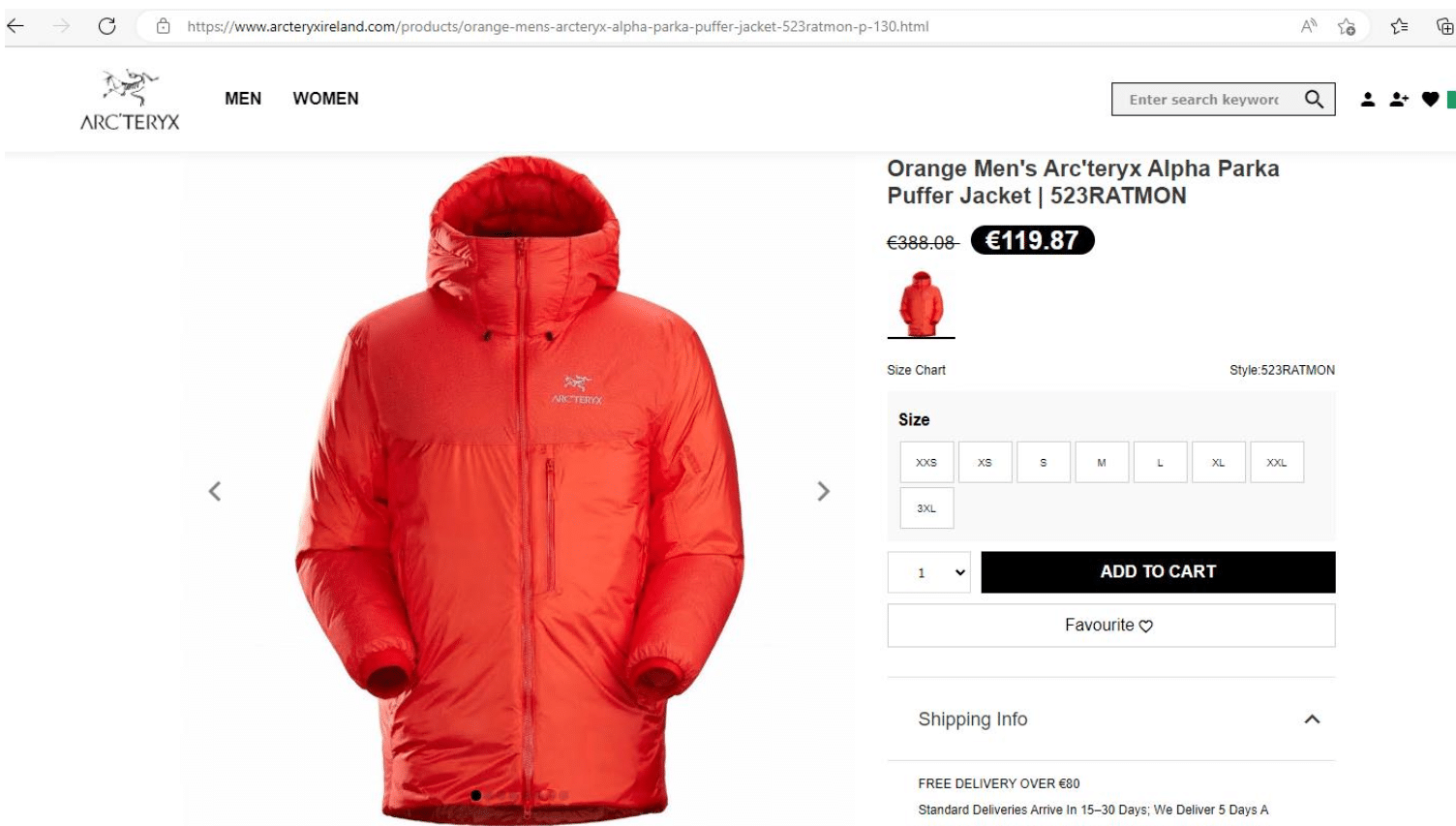
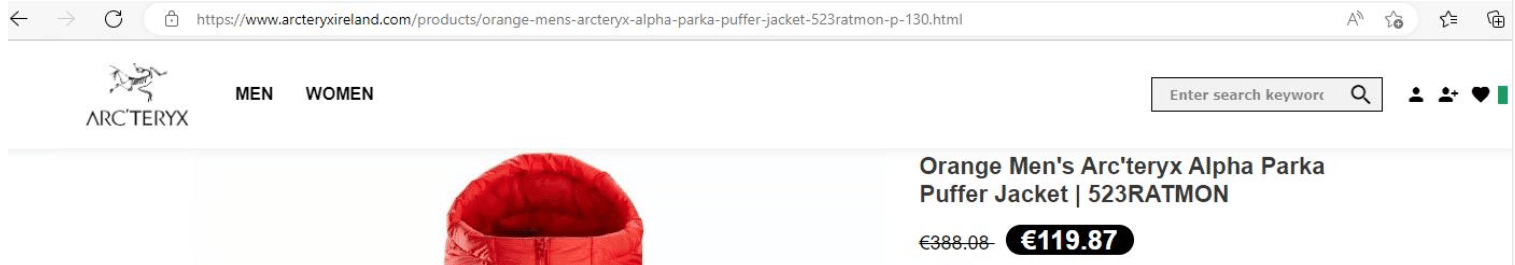
An Arc’teryx Alpha Parka winter coat sells for €1,000 on the company’s official website (arcteryx[.]com). Scammers have set up a similar domain targeting Irish consumers at arcteryxireland[.]com, featuring a product page that’s relatively similar to the original:
Harvesting payment details
As well as fake sign-up forms, the scam also features phony payment pages – used to harvest payment card details – that re-direct consumers to suspect third-party payment services, which in turn have the potential to obtain money directly from a user’s bank account.
Investigating the payments operation
Let’s delve a little deeper into the mechanics behind the payment fraud, and investigate how the scammers were utilising customers’ payment card details and PII.
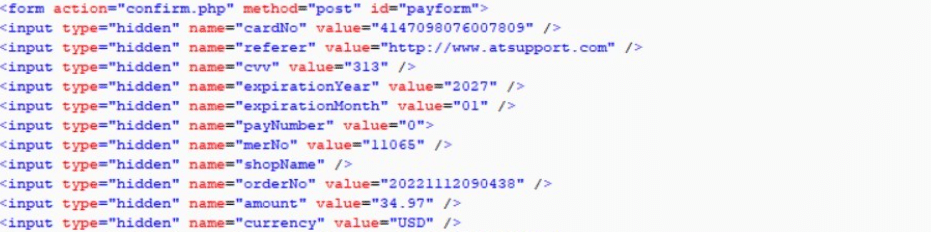
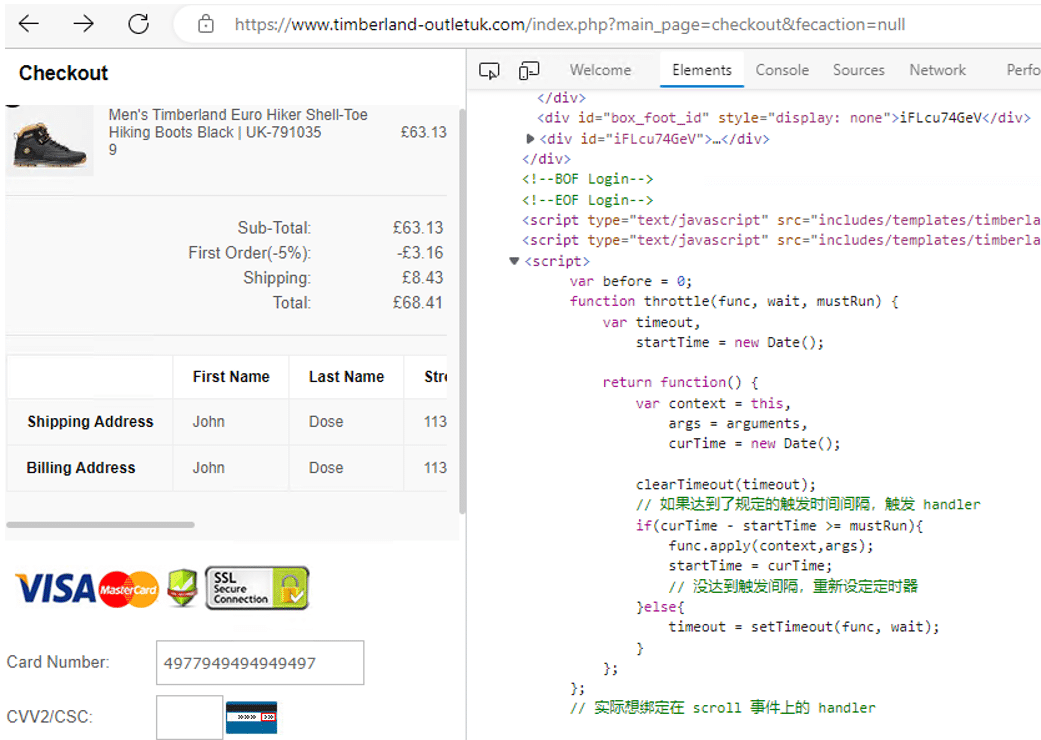
We used a dummy card to attempt to make a purchase on several domains. When the scam sites processed our fake payment, our scans showed that data was harvested the moment it was submitted.
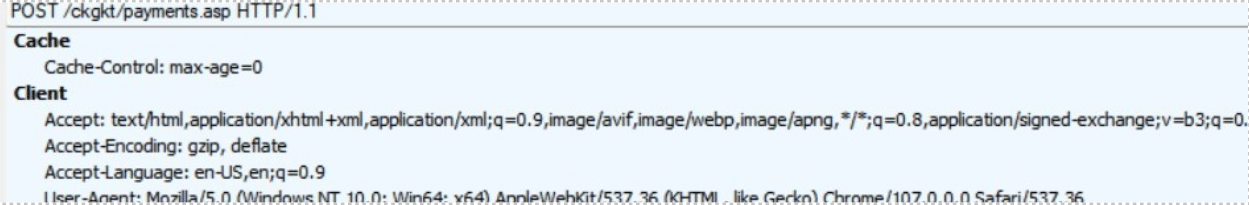
On one fake domain featuring the popular outdoor apparel brand Jack Wolfskin (jackwolfskinoutlet[.]com), visitors are redirected to a seperate payment URL at the checkout – atsupport[.]com/ckgkt/ckout.asp.

The portal is designed to look like a genuine online checkout that’s verified by a legitimate third-party service, but once payment details are entered, the site uploads the card number, the CVV code and all other personal details to its own server, and other malicious servers.
Once the scammers have captured the data, they’re able to use it for all manner of purposes, including resale on the dark web, or to make purchases with directly.
Common denominators
Thankfully, all is not lost. As with most scam operations, there are tell-tale signs that should set the alarm bells ringing and alert users to the fact that they’re being taken for a ride.
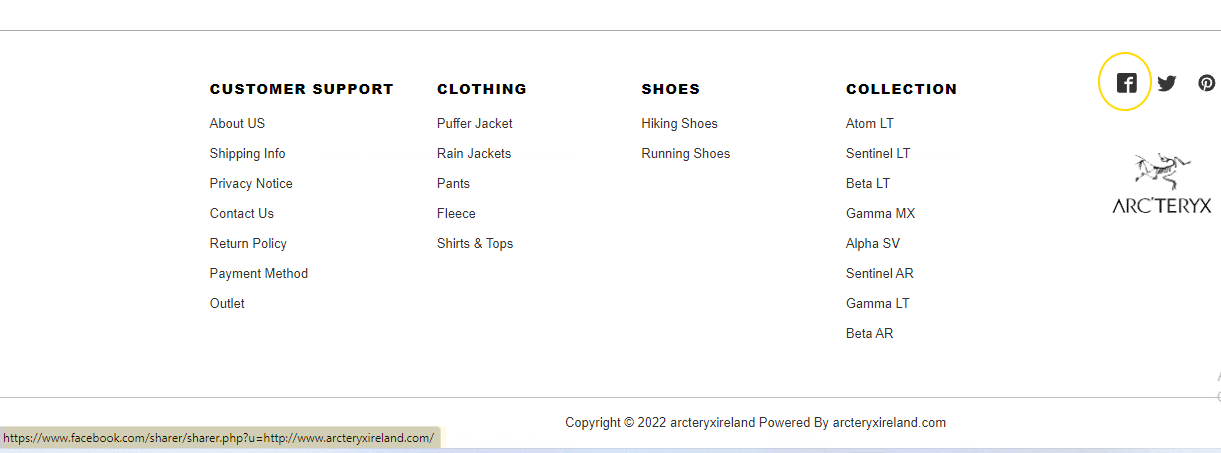
1. Social media buttons not linking to official sources
Fake websites always avoid linking directly to a brand’s main social feeds.
To understand how potential customers are engaging with their brand, it’s standard practice for marketing departments to analyse traffic to their social media accounts.
Scammers know this, and return links to social media login pages or lists of Tweets by a company, rather than run the risk of being detected by a traffic algorithm.
Here’s an example. Note how the fake Facebook button is coded to provide a link to the user’s Facebook login page, rather than the official Arc’teryx page:

2. ‘Contact Us’ form missing or incorrect
Threat actors aren’t in the business of encouraging communication from their marks, but that doesn’t stop them adding in a link to a ‘Contact Us’ form, in order to attempt to appear legitimate to anyone casually browsing the site.
All of the websites we encountered throughout the campaign had customer contact forms that either didn’t work, or triggered no response once completed (i.e. no auto-acknowledgment emails received after a message was sent).
3. Textual anomalies
Be on the lookout for spelling mistakes, grammatical errors, and strange text formats (fonts and spacing) that, for one reason or another, just seem out of place.
This kind of scam relies on teams of threat actors creating websites from a pre-configured template that allows them to pump out the maximum amount of fake content, in the least amount of time.
This leads to similarities within the same campaign, from site-to-site, that become relatively easy to spot once you know what you’re looking for.
Several of the fake sites we investigated placed a small amount of text under the brand name, and included a small marketing message in the top banner, directly under the address bar, that looks completely out of place on the website of a big name clothing brand.
Here’s a fake Nike Ireland page advertising (in italics on their ‘homepage’) the fact that they offer a ‘30-day money back guarantee’, between two dollar sign characters.
You’ll notice that the menu font for ‘Men’ and ‘Women’ is also not branded, and looks equally out of place:
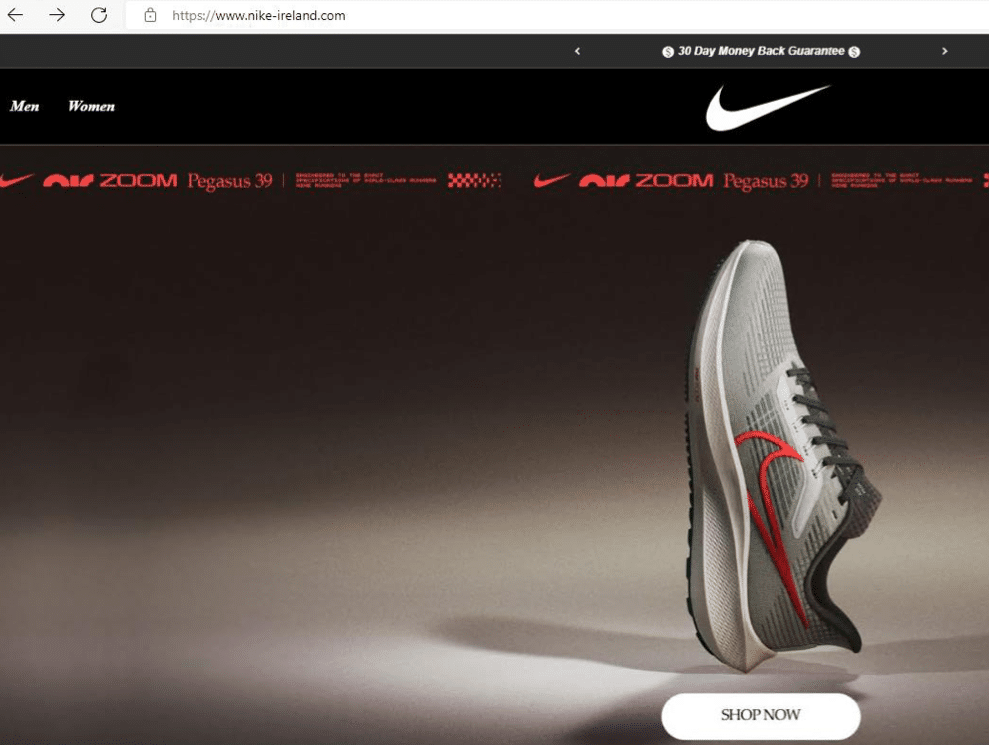
The message box stays in the same place throughout all the fake website – sticking to the template – but usually displays different text, depending on what page the user is on.
Here’s the same domain displaying a different message, on a different page, this time adapting the text to the main body content – promoting ‘Fast Delivery’ between two aeroplane icons (replacing the dollar signs from the homepage) on a pair of suspiciously cheap Nike trainers:
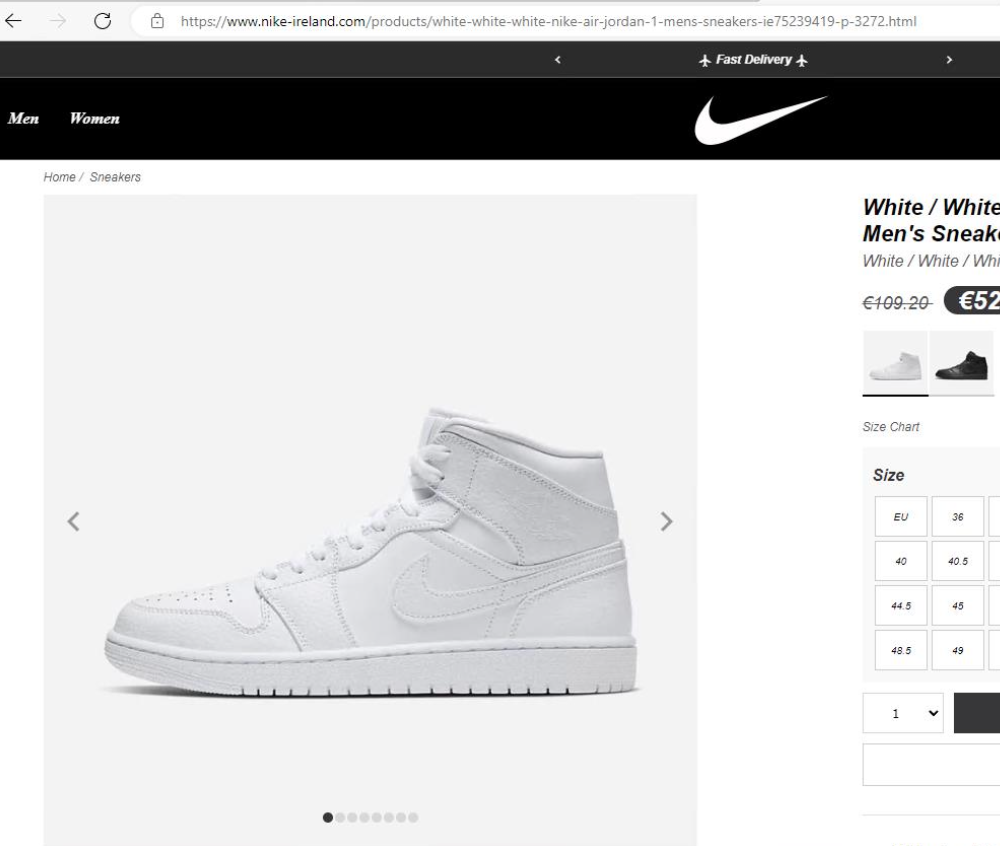
4. Suspect product pricing
It would appear that the architects of the scam have decided that offering goods for the same price range across all the fake websites – whatever brand they’re from, and whatever type of product they are – is the best way to grab a user’s attention.
Most of the fake online stores that we encountered advertised goods for ‘sale’ usually between $70 and $300, with items marked down at a huge discount, and an RRP displayed prominently alongside the ‘actual’ price.
Here’s a set of Ugg boots (that retails for £145 on the official website) being sold for £65 on a scam site, and an entire range of Timberland clothing advertised at around £40 a piece.
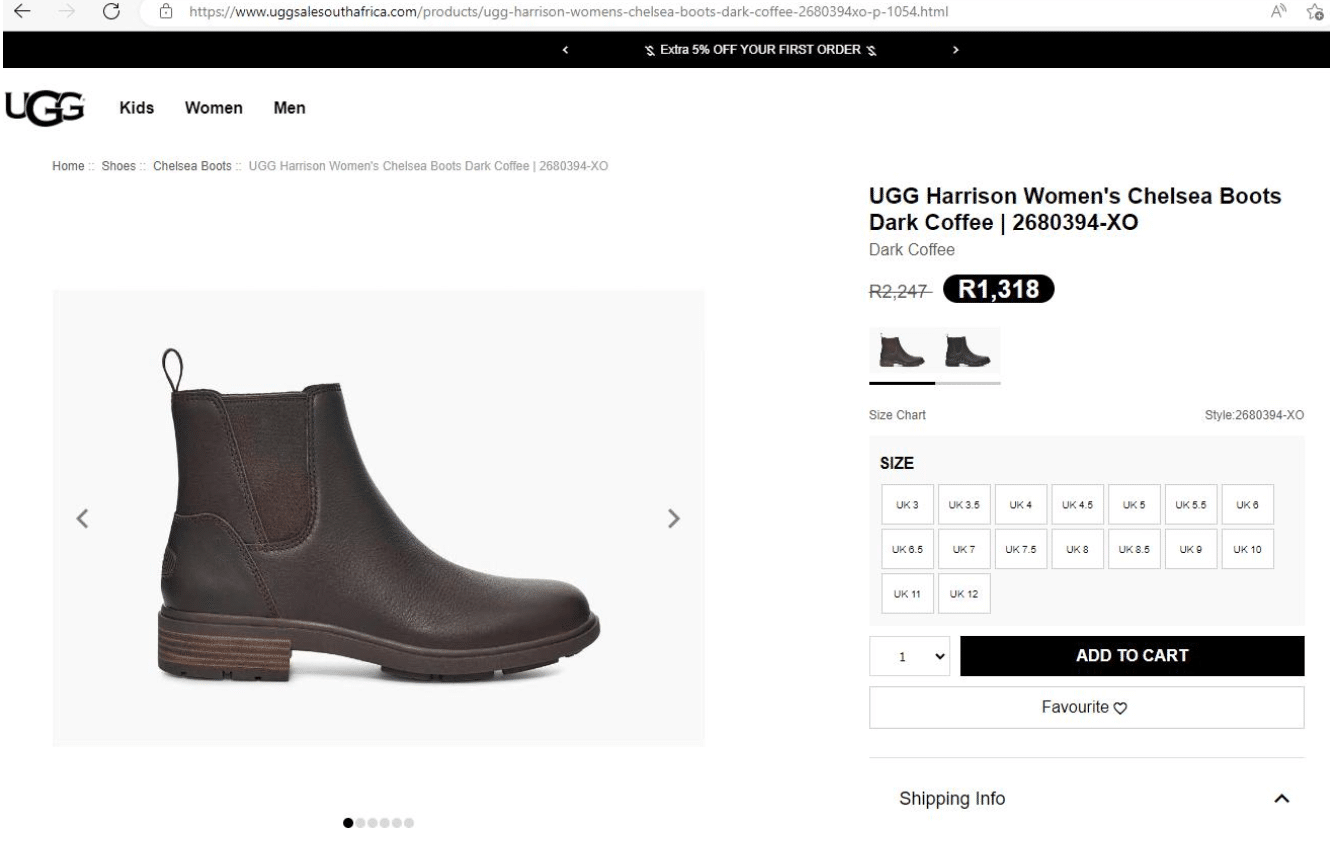

5. A focus on high-end goods
The scammers are swinging for the fences and focusing their efforts on big-name brands that sell high quality goods, allowing them to leverage their strategy of applying huge discounts on well-known product lines that are advertised twice, three times or quadruple the price anywhere else they’re available.
If it looks to good to be true, it almost always is.
Fake ecommerce operations rarely waste their time on low-end products that generate tiny amounts of revenue.
This particular campaign is intent on capturing the attention of consumers with a level of disposable income that allows them to shop at expensive outlets such as Versace, Prada and Ralph Lauren.
6. No product reviews
Product reviews – or a lack thereof – are always a dead giveaway.
We’ve already discovered thousands of websites spread across potentially hundreds of brand names, and that’s just the tip of the iceberg. Setting up this kind of campaign is a numbers game, and threat actors simply don’t have the time to create fake product reviews for every item they feature on their websites.
Unlike legitimate shopping portals, barely any of the products we encountered had an accompanying review section, and if they did, the link was broken.
Here’s the product page for the Arc’teryx jacket we analysed earlier on. The real website encourages you to read user reviews. The fake website doesn’t:
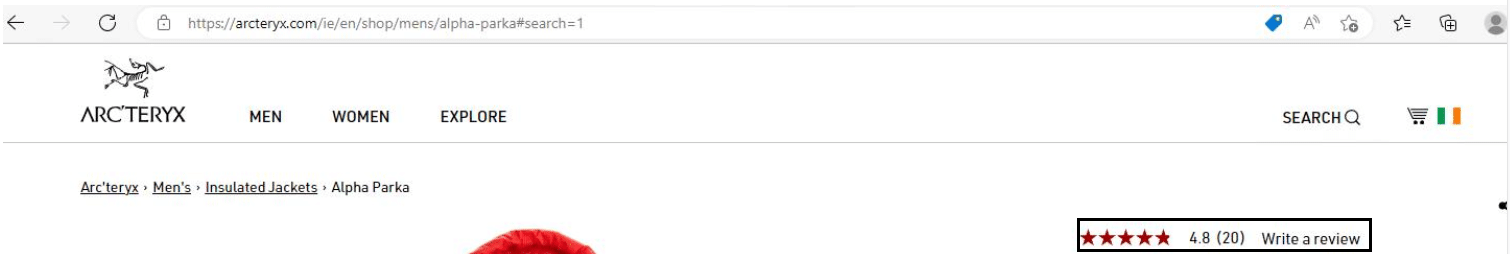
Extent of the campaign
Given that the operation relies on templated websites that can be quickly populated with images, text and links without a great deal of effort, there are currently thousands of IP addresses and domain names active within the campaign, affecting prominent brands across the world.
Our Threat Analysts are working on producing a custom feed that’ll proactively track activity on the Silent Push platform across all the various iterations of domain names and IP addresses.
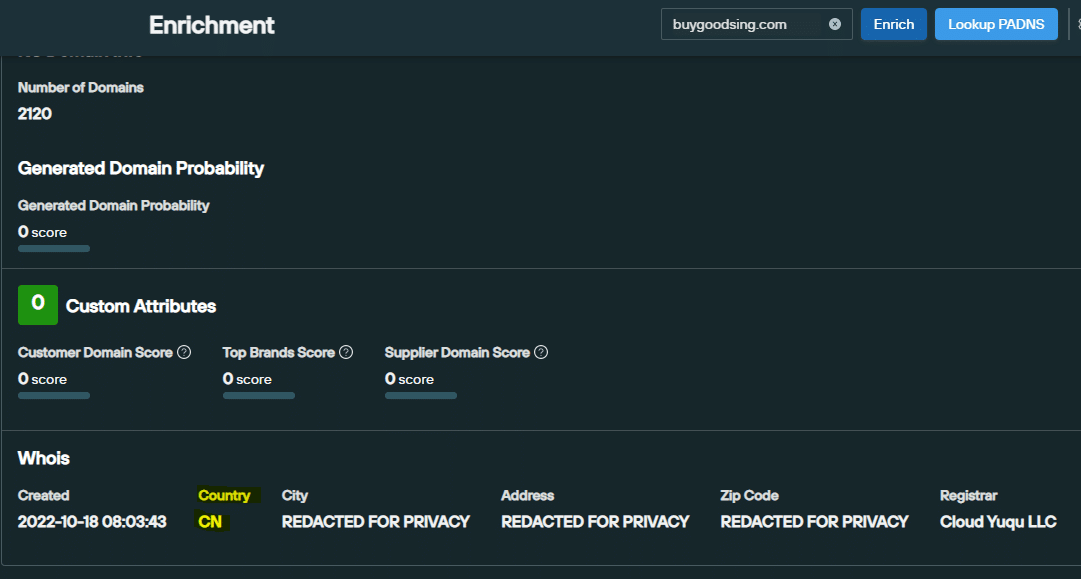
We discovered Chinese characters in some malicious code on several prominent scam sites, and numerous domains we encountered were registered in China, but without definitive evidence across the majority of IoCs in the campaign, we need to keep an open mind as to where the scam originated:
We’re currently conducting further research into the operation that delves into the technical specifics, and sheds even more light on how threat actors are deploying domains and websites, what to look out for and, potentially, who’s behind it.
We’ll be publishing a deep dive over the next week or so. Follow us on LinkedIn and Twitter, and keep an eye out for more blogs.
Indicators of Compromise
5.157.8[.]195 – 5.157.8[.]254
104.160.23[.]130 – 104.160.23[.]188
173.44.202[.]2 – 173.44.202[.]30
196.196.52[.]69 – 196.196.52[.]162
196.196.154[.]195 – 196.196.154[.]243
196.196.194[.]130 – 196.196.194[.]177
196.196.197[.]67 – 196.196.197[.]254
196.196.205[.]2 – 196.196.205[.]126
196.196.205[.]195 – 196.196.205[.]254
196.196.206[.]67 – 196.196.206[.]242
196.196.231[.]66 – 196.196.231[.]254
196.240.45[.]2 – 196.240.45[.]56
196.240.121[.]66 – 196.240.121[.]254
196.245.52[.]67 – 196.245.52[.]126
196.245.155[.]4 – 196.245.155[.]62
196.245.157[.]68 – 196.245.157[.]126
196.245.249[.]66 – 196.245.249[.]126

Start using Silent Push today
Silent Push is an industry-leading extended threat intelligence solution that generates game-changing insights, and identifies new threats to your organization before they launch.
We scan the Internet’s entire IPv4 range every day, and alert you to new threats and rogue assets before they emerge, providing you with the most comprehensive view of Internet activity available anywhere in the world.
Silent Push Community App
The Silent Push Community App allows you to deploy a vast array of powerful domain/IP queries, record lookups and anti-exploit tools free of charge.
Give your teams full access to the Explore and Query Builder sections of the Silent Push App – including access to the Silent Push API – with zero subscription costs.
Silent Push for Enterprise
Silent Push for Enterprise enriches your security stack, providing industry-leading intelligence that you can use to proactively hunt and identify threats to your organization way in advance of your competitors.
Take our product tour and discover how Silent Push will transform the way your organization protects its corporate assets, and analyzes risk.
Follow us on LinkedIn and Twitter for weekly threat intelligence updates and research.