Security teams face several challenges when attempting to turn large amounts of indicator data into actionable intelligence, at scale, across an expansive security automation operation that encompasses numerous vendor platforms.
Teams often find themselves battling with ever-increasing alert queues, containing domains and IPs which require multiple manual pivots to validate an authentic threat.
Silent Push Enterprise Edition changes the game by giving teams the ability to automatically feed a world of additional context into each indicator they come across in the wild, at scale, using proprietary categorization that isn’t available through any other vendor.
Categorization and Correlation
Each hostname, website and IP Silent Push scans is enriched with 200+ datapoints that allow teams to enact faster, better informed, automated decisions on how to deal with indicators they encounter in their alert queues – known or unknown – including:
- Attacker DNS automation
- Malicious hosting clusters
- Infrastructure changes over time
- Inbound scanning signatures
- Website content
- WHOIS and certificate data
IOFA™ Feed Integration
As well as historic DNS and web content data analysis, a key capability of the Silent Push API is the ability to query all of our Indicators of Future Attack (IOFA)™ Feed data, and use the information to gain better insight on where the next attack may be coming.
Let’s look at some of the industry-leading SOAR platforms that we connect with via the Silent Push API, along with some quick workflow examples.
Cortex XSOAR (Palo Alto Networks)
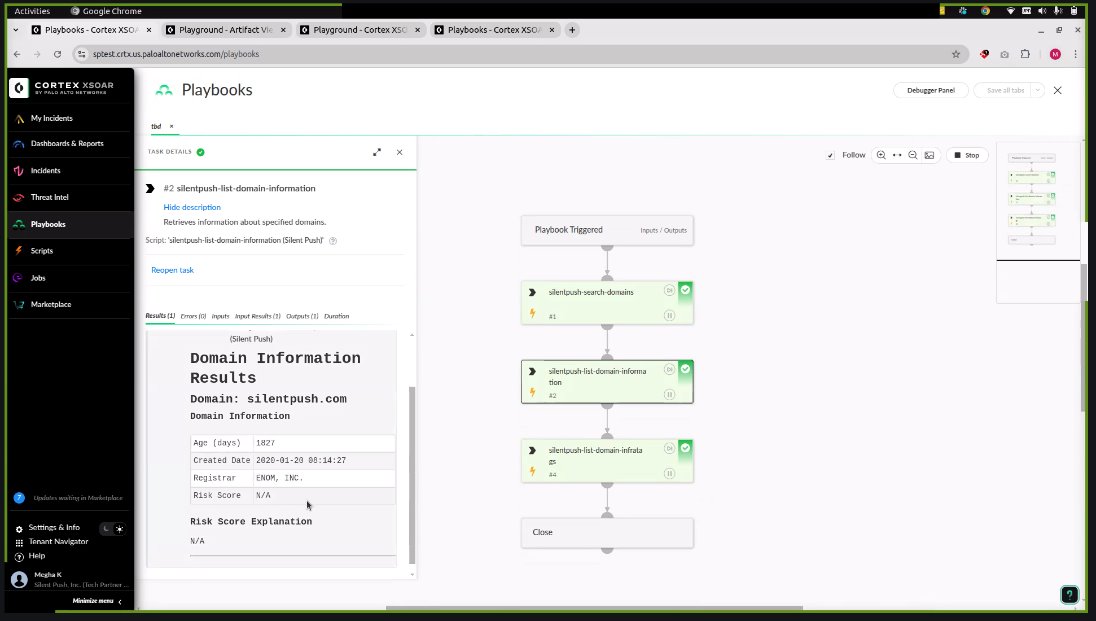
Our Cortex XSOAR integration brings together two powerful cybersecurity functions: preemptive threat detection and enterprise-grade security orchestration.
By combining Silent Push data with XSOAR’s playbook automation capabilities, security teams can transition from reactive IOC-based triage to proactive threat discovery, at scale.
Capabilities
- Enrich domains, IPs, and ASNs in real-time
- Automatically triage alerts by correlating indicators with IOFA™ feed data, including Silent Push risk scoring
- Trigger live URL scans (including screenshots of suspicious domains) directly from an XSOAR playbook
- Feed enriched indicators into downstream systems, like firewalls or SIEMs, enabling faster mitigation and reduced analyst load
Example
When an alert hits your SOC, it can be passed through XSOAR to Silent Push, where the domain is enriched with DNS history, certificate associations, infrastructure movement, and similarity to known threat actor TTPs.
After generating an enhanced risk profile based on the above information, the system can escalate, suppress, or initiate blocking – all without manual intervention.
Key Outcomes Delivered
- Reduced response times
- Eliminates a need for isolated lookups
- Continuous infrastructure monitoring within existing playbooks
Splunk SOAR
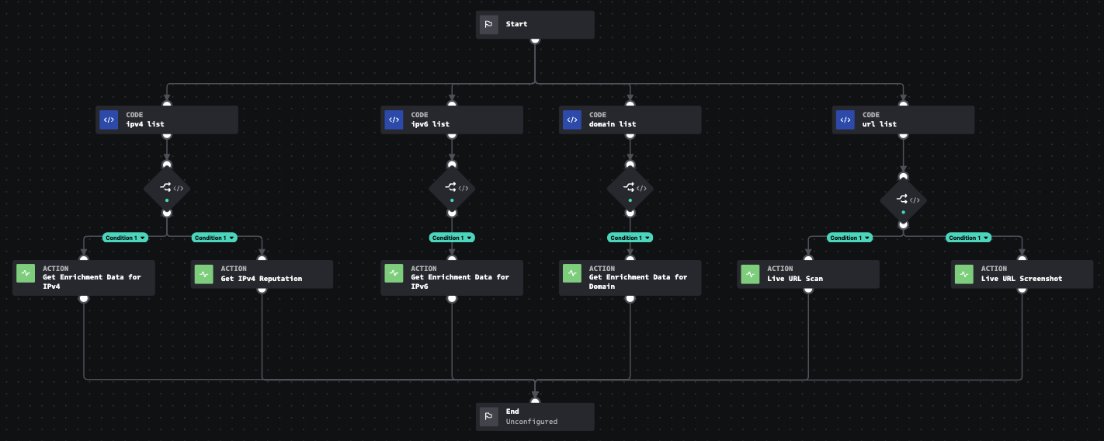
Our Splunkbase app for Splunk SOAR (formerly Phantom) delivers threat intelligence and playbook automation within Splunk SecOps workflows.
By embedding infrastructure-focused data alongside Splunk datastreams, teams can move from manual investigation to proactive, TTP-driven responses.
Capabilities
- Perform domain and IP enrichment within a Splunk instance
- Lookup historic and live WHOIS data, certificate information, and ASN/subnet reputations
- Explore DNS history
- Automatically generate risk scores
- Fetch live URLs with scans and screenshots into Splunk
Example
Your SOC receives a phishing or brand impersonation alert into your Splunk instance. A playbook takes the suspicious domain, enriches it via Silent Push (including IOFA™ feed correlation and DNS history), and calculates a risk score. If the domain is flagged as high risk, an automated response is triggered – such as initiating an action in a ticketing system, or isolating the asset via firewall integration.
Key Outcomes Delivered
- Reduce manual triage steps
- Cut mean times to detect (MTTD) and respond (MTTR) to threats
- Provide your Splunk instance with the ability to proactively detect emerging infrastructure
Torq
The Silent Push Torq integration feeds Silent Push enrichment data directly into your no-code security workflows, allowing teams to operationalize threat data without writing a single line of code.
Our Torq integration automates early-stage threat detection and response with context from Silent Push’s DNS, certificate, WHOIS and content scanning datasets.
Capabilities
Silent Push exposes multiple API endpoints through a native integration with Torq, including:
- Domain and IP enrichment
- Forward and reverse DNS lookups
- Live endpoint scans and screenshots
- Access to IOFA™ feeds
Examples
Torq accepts a domain or IP input (e.g., from SIEM or ticketing alert), queries Silent Push, and uses caching to avoid redundant lookups (ideal for high volume investigations). Results can then be routed to downstream actions like ticketing (e.g., ServiceNow), chat (e.g., Slack), or blocking controls.
Key Outcomes Delivered
- Real-time infrastructure intelligence at scale, without scripting or manual triage
- Feed enhanced risk scores into EDR response logic
- Faster, smarter, and more proactive security decisions across your stack
Swimlane
Our Swimlane integration brings advanced infrastructure intelligence into Swimlane’s low-code, hyperautomation environment, enhancing Swimlane “cases” – a container or record within Swimlane SOAR that represents a security incident, alert, or event – with Silent Push data.
Capabilities
The Swimlane plugin supports data enrichment for:
- Domains, IPv4, and IPv6
- Nameserver details and change history
Example
Silent Push enrichment tasks automatically run when a SIEM or EDR alert is activated in Swimlane. Your SOAR parses observables, queries the Silent Push database, and enriches case records with infrastructure intelligence in real time. High-risk domains or IPs are highlighted through IOFA™ feed correlation, and trigger immediate escalation, task creation, or containment workflow actions.
Key Outcomes Delivered
- Inject preemptive infrastructure intelligence into Swimlane cases
- Detect and disrupt threat actor infrastructure at scale, before an attack is launched
- Trigger automatic escalation for high priority alerts
Tines
The Silent Push Tines integration allows security teams to embed Silent Push IOFA™ data directly into Tines stories, facilitating early detection, smarter triage, and automated response without the need for manual coding.
Capabilities
- Retrieve domain and IP risk scores, WHOIS data, nameserver reputations and historical change information
- Fetch subnet reputations and scanned data including open directories, JARM fingerprints, HTTP headers, favicons, and SSL attributes
- Analyze a domain’s digital footprint and output it to Tines as a downloadable CSV
Example
Your system flags a phishing trigger (via email, Slack, or SIEM) in a Tines Story. The domain is passed into Silent Push enrichment actions, which return risk scores, WHOIS details, associated domain clusters, and certificate data.
The dataset is then used to:
- Make a triage decision via conditional logic
- Present findings through a Tines page for analyst review (if manual approval is desired)
- Automatically generate a ticket in ServiceNow, or an alert in Slack, if critical thresholds are met
Key Outcomes Delivered
- Operationalize enrichment data at scale
- Elevate static lookups to dynamic stories, infused with context
- Speed-up detection by sharpening analyst workflows
ServiceNow
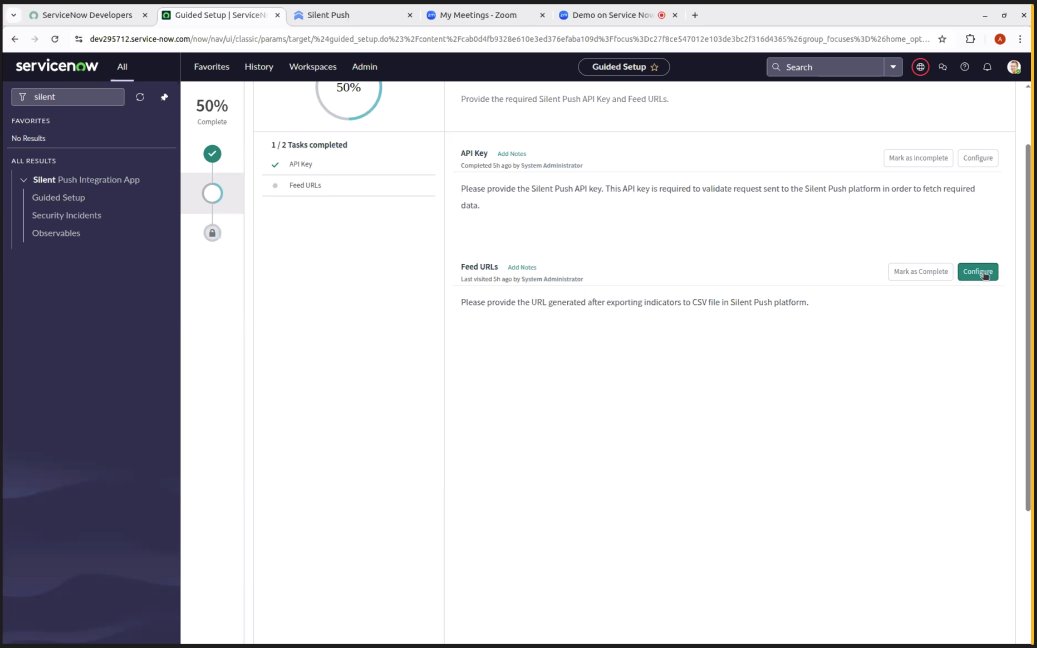
The upcoming Silent Push ServiceNow integration connects incidents and observables inside ServiceNow’s Security Operations suit, with Silent Push datapoints, enabling teams to take fast, informed action on emerging threats before they turn into a breach.
Capabilities
- Generate Tickets from an IOFA™ Feed
When Silent Push detects a newly registered domain mimicking your brand or infrastructure, a ServiceNow ticket is created that allows legal, brand protection, or threat intel teams to automatically initiate a takedown or investigation.
- Enrich Existing Tickets with IOFA™ Context
If an indicator appears in Splunk that triggers a ServiceNow ticket, Silent Push can be queried to retrieve DNS history, certificate data, hosting changes, and risk scoring to help assess its threat level.
- Build Custom Enrichment Workflows
Leverage over 20 Silent Push APIs within your ServiceNow playbooks. For example, automatically capture a live screenshot of any domain included in a phishing report or correlate IPs with infrastructure clusters seen in IOFA™ datasets.
Book a demo
Our team is on hand to show you how easy it is to link your SOAR platform with the Silent Push API, and build faster, more efficient security workflows that remove manual intervention and give teams access to better insight on emerging threat infrastructure.
Contact us today for a platform demonstration.


