Silent Push now offers bi-directional support for STIX (Structured Threat Information Expression) and TAXII (Trusted Automated Exchange of Indicator Information) – two of the most widely adopted standards for Cyber Threat Intelligence (CTI) sharing and automation.
This capability injects our industry-leading preemptive threat intelligence directly into your existing security workflows, allowing for faster, smarter decision-making without added complexity, and giving teams the ability to collaborate cross-platform to detect emerging threats at the earliest opportunity.
What are STIX and TAXII?
The speed and clarity of intelligence delivery determines how well teams respond to emerging adversary activity. CTI is often fragmented, stuck in proprietary formats, or siloed across different systems, making it hard to get at actionable intelligence, or collaborate effectively to detect hidden threats.
Enter stage right: STIX and TAXII.
STIX is a standardized format for structuring threat intelligence – from domain and IP indicators, to TTPs, APT relationships, and threat actor profiles. It provides a machine-readable way to express contextual intelligence in a format that analysts and tools can easily understand.
TAXII is the protocol for sharing that same intelligence securely and efficiently. It lets platforms push and pull data between trusted sources and subscribers, enabling real-time intelligence exchange across organizations, teams, and tools.
Together, STIX and TAXII simplify integration, reduce manual effort, and help security teams operate with greater precision and speed.
Not Just Another Feed: Actionable STIX Data Built from IOFA™
Silent Push Enterprise users can now easily ingest threat data derived from infrastructure-level intelligence that focuses on the ways threat actors setup and manage their infrastructure, structured in STIX format and delivered via TAXII feeds.
This allows Silent Push data to plug directly into TIP, SIEM and SOAR platforms, or any other cybersecurity system that supports these standards.
It’s not just about the format. What sets Silent Push apart is the quality and depth of the intelligence being shared.
Unlike CTI vendors that aggregate third-party feeds, or focus solely on IOCs, Silent Push captures and analyzes the unseen layers of attacker infrastructure – from passive DNS and web content changes to behavioral patterns, automation signatures, and hosting relationships – and delivers them as Indicators of Future Attack (IOFA)™.
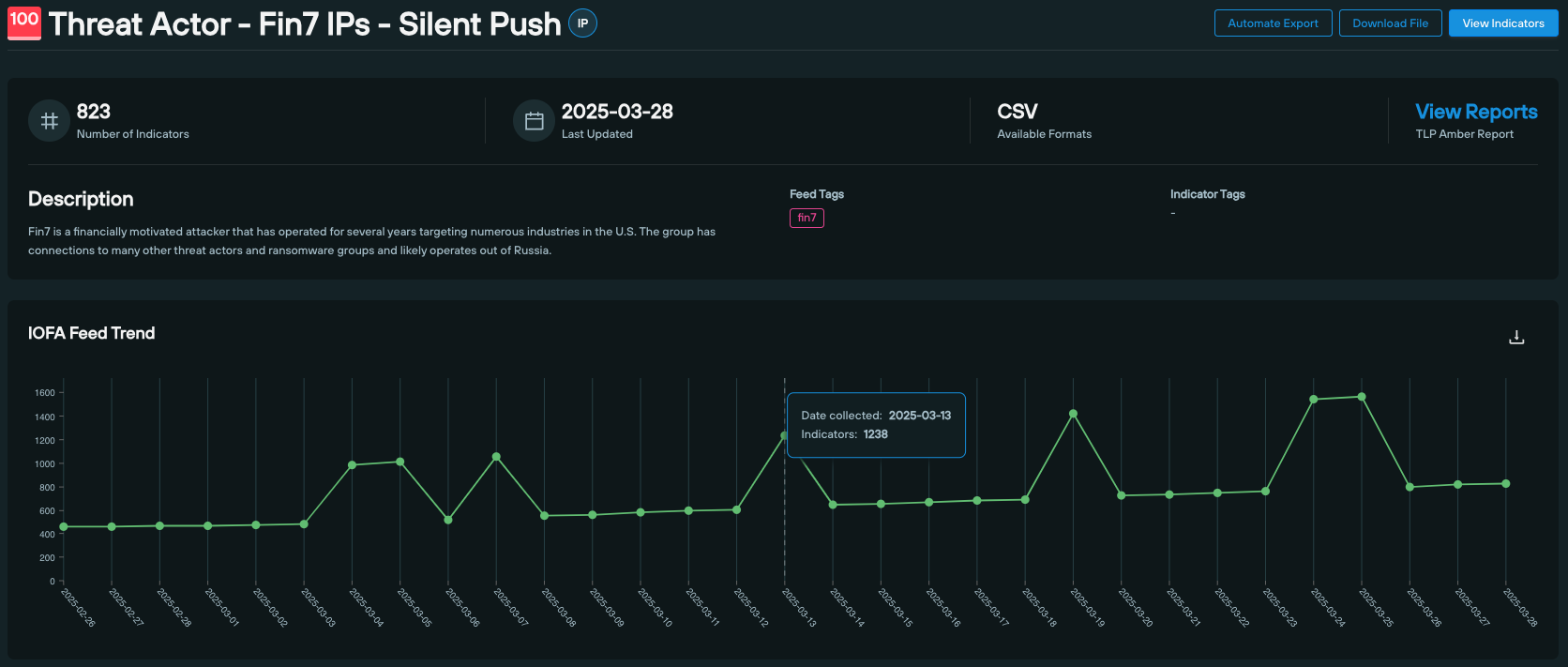
All our data is collected and aggregated by us, globally and independently, with no reliance on external resolvers or limited partnerships.
This means the STIX data you’re receiving isn’t just another feed of stale domains or hashes. It’s real infrastructure context, including domains and IPs tagged with relevant information, such as threat actor name, linked campaigns, nameserver reputation, malware type, and IOFA™ feed presence.
Plug and Protect: Use Cases for STIX/TAXII in Silent Push
With Silent Push’s STIX/TAXII support, organizations can:
- Automate IOFA™ ingestion: Feed Silent Push indicators directly into your SIEM or firewall policy engine without manual formatting or translation.
- Enrich existing alerts: Correlate events in your environment with deeper infrastructure context pulled from Silent Push intelligence.
- Build custom detections: Use Silent Push data in threat-hunting playbooks or SOAR workflows to uncover related infrastructure and prevent lateral movement.
- Bi-directional intelligence sharing: Ingest external CTI data into your Silent Push subscription and contribute IOFA™to CTI sharing communities using a common, interoperable language.
Whether you’re part of a Security Operations Center (SOC), threat hunting team, or CTI unit, this integration allows you to move faster, reduce noise, and act with greater confidence.
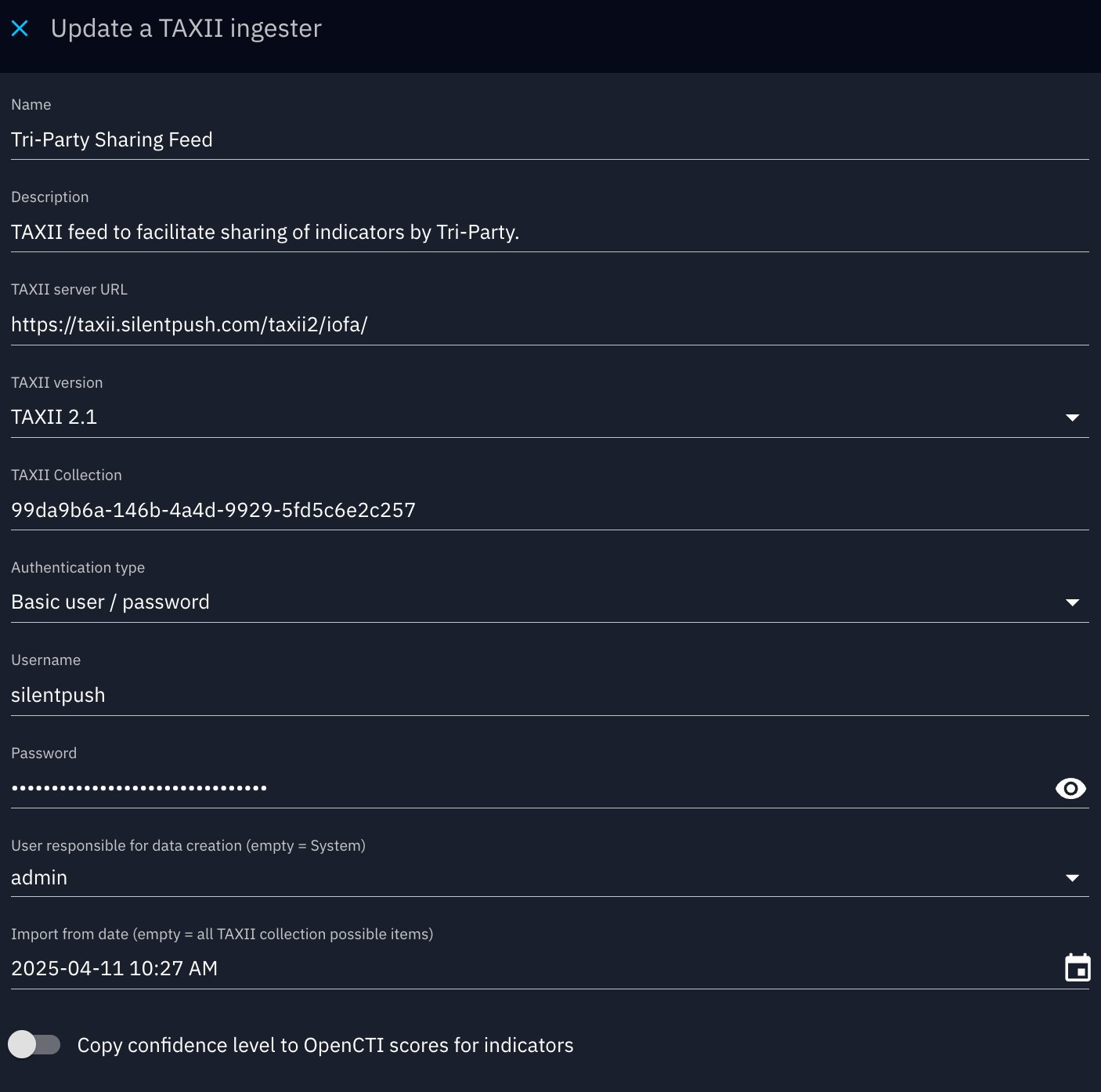
Designed for Flexibility
Silent Push’s STIX/TAXII implementation is engineered to support flexible consumption of CTI data.
- Pull or push feeds to your preferred tools and platforms
- Choose from curated data sets – including malicious hosting clusters, high-risk domains, or specific TTPs
- Apply filters based on region, time, or infrastructure type in Feed Scanner
- Access feeds programmatically for full automation, or manually for ad hoc investigations
We’ve also made sure our TAXII server meets the latest interoperability standards, ensuring compatibility with the tools your team already uses.
Book a Demo
In a security environment that demands faster decisions and tighter integration, Silent Push’s support for STIX and TAXII helps organizations minimize siloed information sharing, and operationalize threat intelligence with minimal friction.
By combining the depth of Silent Push data with the power of open standards, we’re making it easier than ever for teams to stay ahead of adversary infrastructure, and act before the next attack chain begins.
Get in touch today for a personalized demonstration.


