A key component of any attack surface mapping operation lies in an organization’s ability to collect information related to its brand that isn’t exclusively limited to second and top-level domain data.
Subdomain data plays an increasingly important role in corporate ethical hacking endeavours, from red and blue team ops to bug bounties and standard threat management activities.
Let’s delve a little deeper into subdomain enumeration as a modern countermeasure, and explore how Silent Push’s new Subdomain Finder allows you to not only scan for subdomain vulnerabilities using a single query but also provides results with reputational risk scoring generated from automated queries, that are custom-made for a brand’s unique public DNS infrastructure.
What is subdomain enumeration?
Subdomain enumeration is the act of categorizing all subdomains for any given domain.
Enumeration isn’t limited to security functions. Brands often need to collect domain data for a range of organizational purposes, such as audits, inventory, product development cycles or restructuring activities.
From a security perspective, however, subdomain enumeration is explicitly concerned with providing security teams with an actionable list of assets that need to be protected from all manner of conventional and lesser-known exploits.
Why are subdomains so important to security-conscious organizations?
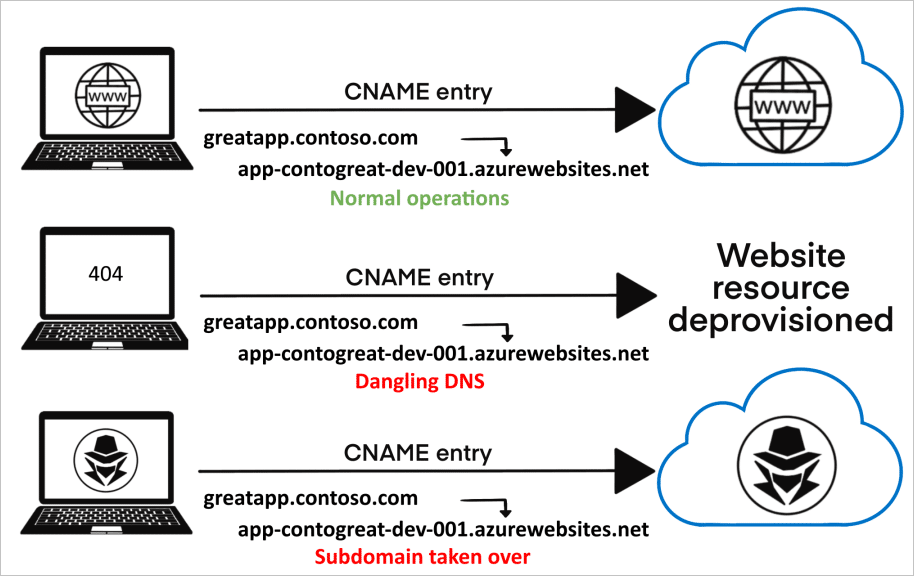
Subdomain takeovers are a growing malady within the world of corporate DNS security. If a subdomain has a CNAME associated with it, but no content is being provided by the host, threat actors can hijack the domain by deploying their own replacement host.
The consequences of such an attack are disproportionate to how easy it can be to perform the takeover in the first place, once a subdomain has been compromised
Threat actors are able to obtain hashed credentials, gain access to SSO-secured systems and applications via hijacked session cookies and perform cross-site scripting attacks that facilitate access to sensitive information and even have the ability to modify a site’s underlying HTML.
Obtaining a comprehensive top-down picture of an organization’s subdomain infrastructure allows security professionals to:
- discover and directly address a larger attack surface than was previously acknowledged;
- identify lesser-known entry points and vulnerable DNS records;
- deal with dormant applications or migrated/expired services.
Red and Blue Team ops
Subdomain data is one of several factors within Red and Blue Team ops that should be given an equal amount of consideration by both sides during a simulated attack, particularly throughout the reconnaissance phase, or indeed any activity that involves an adversarial assessment of a company’s public DNS infrastructure.
For both Red and Blue Team practitioners, subdomains offer a goldmine of information that facilitate the development of unique attack vectors and allow for robust defense mechanisms which are unique to the target organization, including:
- safeguarding host and identity information;
- securing organizational data;
- identifying open databases or file repositories;
- closing bridges to exploitable sites and services
Once a list of subdomains has been obtained, each one can be interrogated to ascertain whether the domain is live and its HTTP status code, further refining the attack surface map and providing specific subdomains that require attention.
How subdomain enumeration is carried out: passive vs. active domain identification
Subdomain enumeration techniques are categorized in two ways: passive enumeration and active enumeration.
Both techniques involve time-consuming and inexact ways of discovering a reliable list of subdomains that are prone to human error and don’t always return a categorical and up-to-date set of results.
Before reading on about passive and active enumeration, it’s important to note that the Silent Push Subdomain Finder achieves a complete list of associated subdomains through a simple search based on a single apex domain, without the need to engage with multiple distinct techniques spread across numerous DNS lookup tools, consoles and scripts.
Passive enumeration
Passive enumeration involves gathering domain data without any direct interaction with the primary domain infrastructure, with the help of third-party tools. Passive enumeration techniques include:
Scanning Certificate Transparency logs
Certificate Transparency logs all the entries of domain certificates in a centralised database, accessible to the public – including a list of domain names, subdomains, and email addresses.
ASN discovery
ISPs purchase unique IP address pools and ASN numbers from the Internet Assigned Numbers Authority (IANA), which distinguishes them from other providers. Security teams identify an ASN number by IP address (or domain name), which then leads them to an address pool. If a PTR record is visible on the DNS setup, subdomains can then be resolved to an IP address, using a variety of tools.
Operator searches on mainstream search engines
Certain subdomains can also be located using widely-used search engines (e.g. Google, Yahoo, Bing). Using the operator ‘site:’ prior to the brand name
Extracting subdomain data from multi-domain SSL certificates
Multi-domain SSL certificates allow a single certificate to secure multiple domains – including subdomains – underneath a single apex domain name (or even a completely different domain name) with the end goal of protecting the subdomains through SSL. Where present, subdomain data can be extracted from multi-domain SSL certificates using tools such as OpenSSL, or custom scripts.
Searching through large public DNS datasets
Various publicly available DNS datasets are available online that cover all manner of DNS data from a large number of visible domains online, from Forward and Reverse DNS lookups to SSL certificates and HTML responses. Each dataset is broken down into categories that contain responses for all records known by that particular repository, and security teams need to create their own filters and search scripts based on the subdomain information they’re looking for.
Utilizing reverse proxy servers and Content Delivery Networks (CDNs) (e.g. Cloudflare)
CDNs are groups of proxy servers linked together using a web application firewall (WAF) to cache content that’s closer geographically (also called a Point of Presence) to the end user who is requesting it, thereby increasing performance and reducing data bottlenecks.
Certain CDNs display DNS data for any target domain that a user is attempting to add, including a list of subdomains for the associated apex domain.
Active enumeration
Active enumeration involves direct interaction with the apex domain – rather than utilising publicly available information or third-party DNS services, in order to gather a list of associated domains:
‘Brute force’ discovery
‘Brute forcing’ (either utilising a unique wordlist or by using permutations of known domain names) involves using third-party tools in an attempt to guess subdomain hostnames through random or sequential strings of characters and/or numbers. This tactic is often used to discover hostnames that have either been overlooked by the controlling organization or to uncover subdomains that aren’t publicly discoverable using standard aggregation tactics.
DNS zone transfers
A zone file is a basic text file that includes data on the various mappings between domain names, IP addresses and other hostname information such as physical network assets.
If zone transfers aren’t properly configured and maintained, and a DNS server is allowed to transfer zone files to anywhere other than a controlled location such as a nameserver or specific IP address, zone files can be read by unauthorised personnel, along with a treasure trove of information relating to public and privately visible subdomains stemming from an apex domain.
Enumeration by CNAME and SPF record
Sender Policy Framework (SPF) is a method used to authenticate an email as originating from a trusted source – i.e. the domain that sent it.
The way that SPF discovery work means that if an accompanying record is not found on an email subdomain (e.g. sales.example[.]com) that validates that subdomain as being able to send email, then SPF will return a negative value without attempting to validate using the second level domain (example[.]com). Tools exist that parse domain and subdomain data from SPF records, allowing threat actors to extract information on how an organization’s public DNS presence is structured.
Canonical Names (CNAMES) are used to map a subdomain to a domain that’s used to host content. Querying CNAMES can be used to reveal information about associated subdomains, and any third-party services attached to them.
Harvesting Content Security Policy (CSP) data
CSPs are HTTP headers that allow domain owners to define what kind of content is able to be loaded on a specific website – e.g. JavaScript, CSS, frames, fonts, image files, and embeddable content such as Java applets, ActiveX, and audio/video files.
CSPs also contain domain and subdomain names that the CSP is applicable to. Various Python tools exist that parse domain names from CSP headers and provide further information, such as whether or not an A record is associated with a particular subdomain and any associated IP addresses.
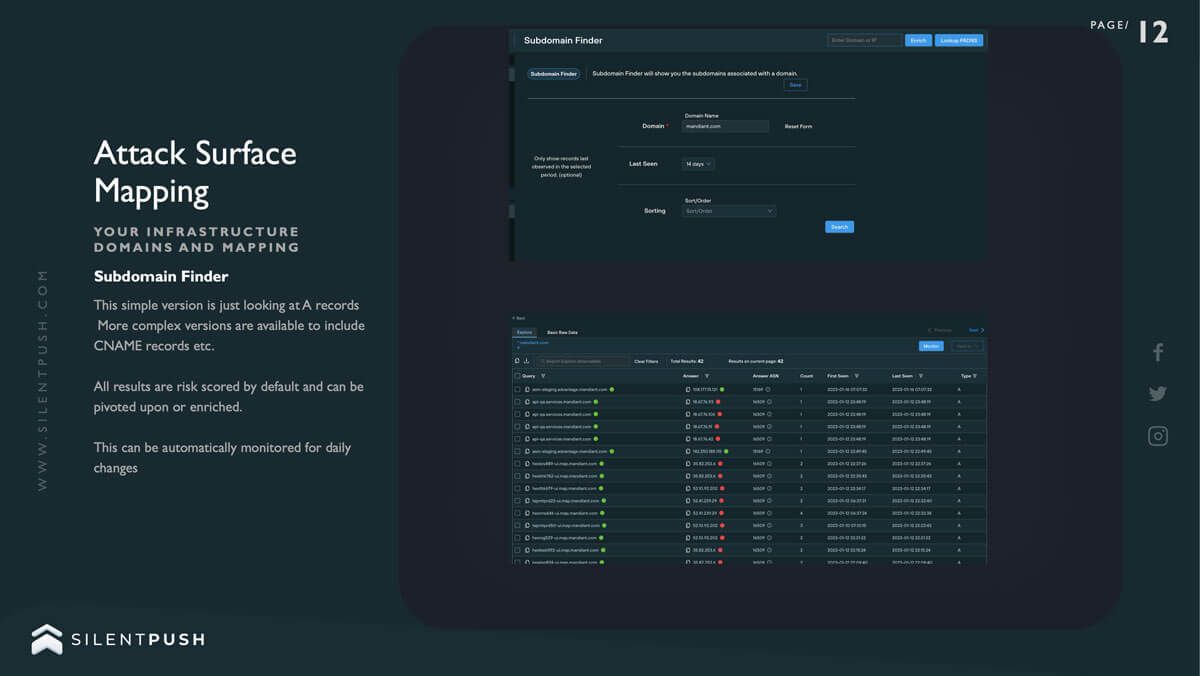
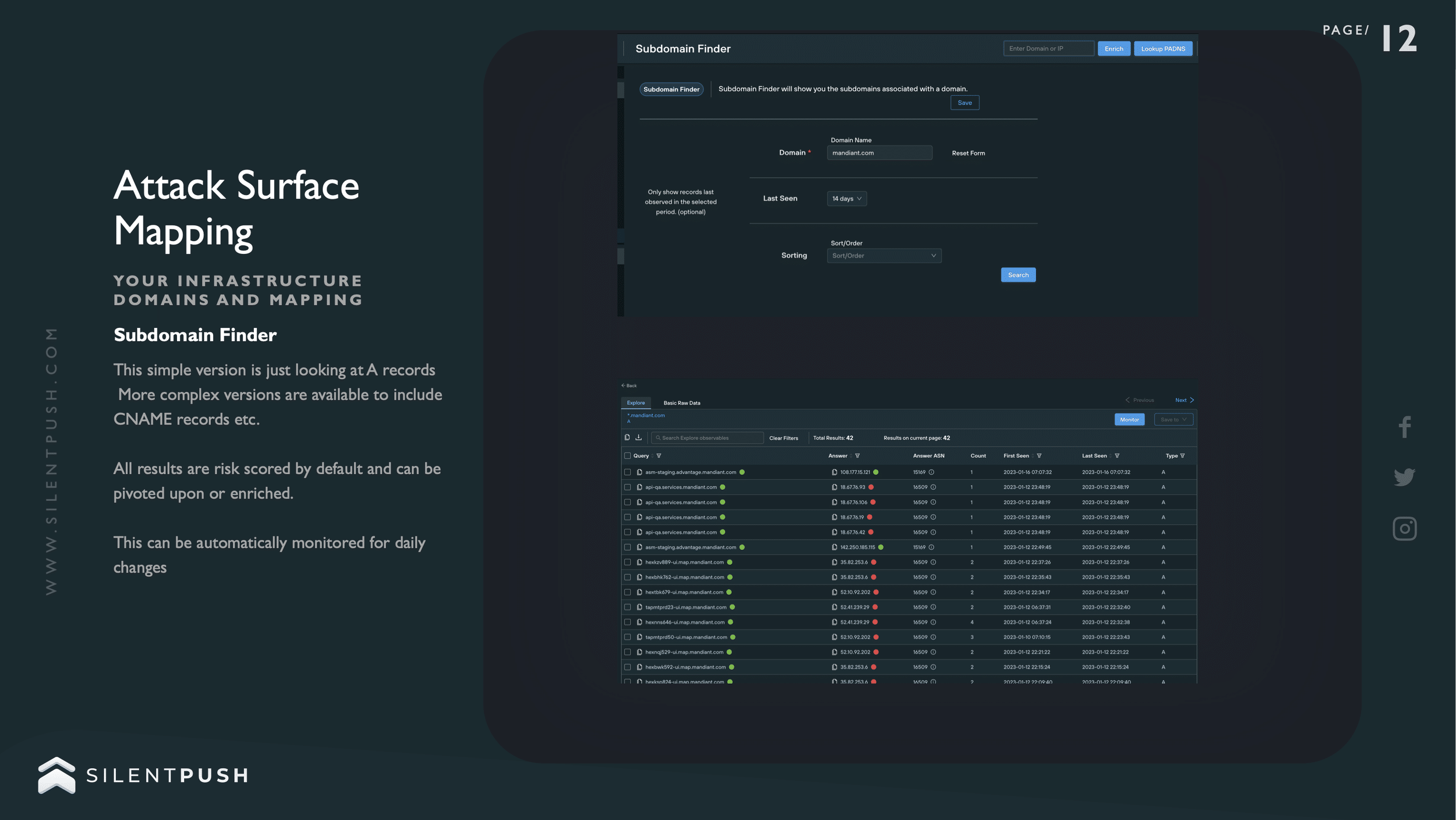
The Silent Push Subdomain Finder
Obtaining an accurate and complete set of subdomains attached to an associated domain can be a time-consuming, inexact and unreliable process. Online DNS aggregators don’t always return an accurate set of results for a variety of reasons, and even paid-for services are liable to return suspect datasets that are incomplete, out of date and overtly incorrect.
Take this example from a well-known subscription-based service:

Several subdomains are listed as being first seen, and last updated, on January 1970. The Internet’s DNS architecture wasn’t invented until 1983.
The Silent Push Subdomain Finder utilises a comprehensive set of back-end enumeration techniques to output a complete list of what subdomains actually exist underneath a second-level domain, their associated IP addresses, any attached record and whether or not they are able to be connected to.
The service also scans the endpoint and facilitates a pivot into any other asset, record or piece of data associated with the same IP address.
Crucially, Silent Push subdomain enumerations are able to be monitored, with an email alert sent every 24 hours listing any changes, such as additions and removals to your DNS infrastructure (paid subscribers only).
Red and Blue Teams, bug bounty chasers and security professionals require a subdomain enumeration service that doesn’t leave them guessing and eliminates the need to interact with numerous different consoles, scripts, third-party tools, Linux platforms, online aggregators and vast unfiltered data dumps – most of which may be returning conflicting information based off inexact searches, guesswork and the incidental availability of public DNS information.

The Silent Push Subdomain Finder is available for free using the Silent Push Community App – The largest free library of SaaS-based threat defense tools available anywhere in the world.
Click here to register.
Follow us on LinkedIn and Twitter for weekly threat intelligence updates and research.