Threat actors continue to exploit malvertising and brand spoofing to deploy infostealers and propagate crypto fraud
Background
Last month we blogged about malvertisement activity involving Russian banking trojans, originating from malicious Google ads.
Attack vectors included search phrases and fake advertisments targeting remote desktop apps and online meeting platforms.
A couple of days after releasing our research the FBI issued a PSA, warning users about brand impersonation activity that uses popular search engines as a tool to distribute malware.
Since then, we’ve been on the lookout for similar activity targeting the type of brands targeted in the initial campaign. We’ve uncovered new attack vectors featuring other spoofing activities not limited to the original campaign.
AnyDesk spoofing
One of the brands targeted in the initial campaign was AnyDesk – the remote desktop platform.
With the help of scanned data from Silent Push’s enrichment query, we’ve kept an eye on the AnyDesk attack vector, among other remote desktop tools.
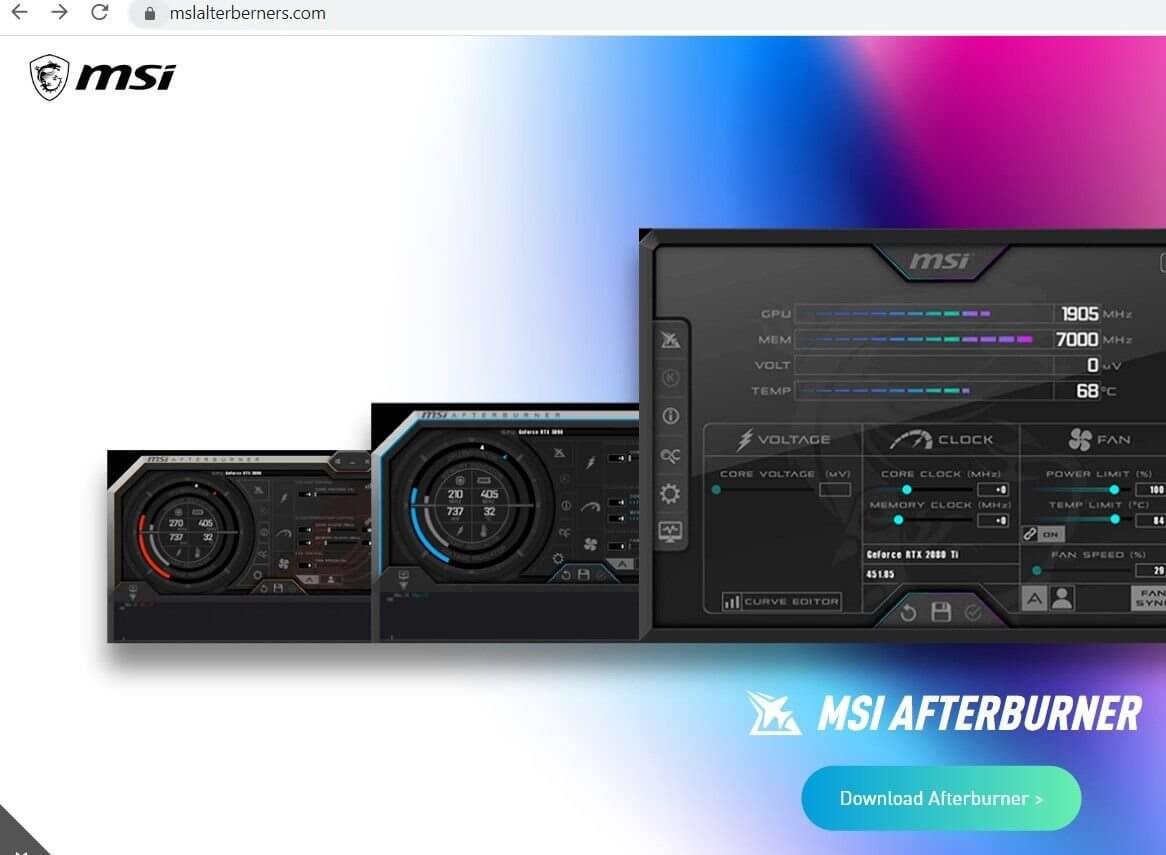
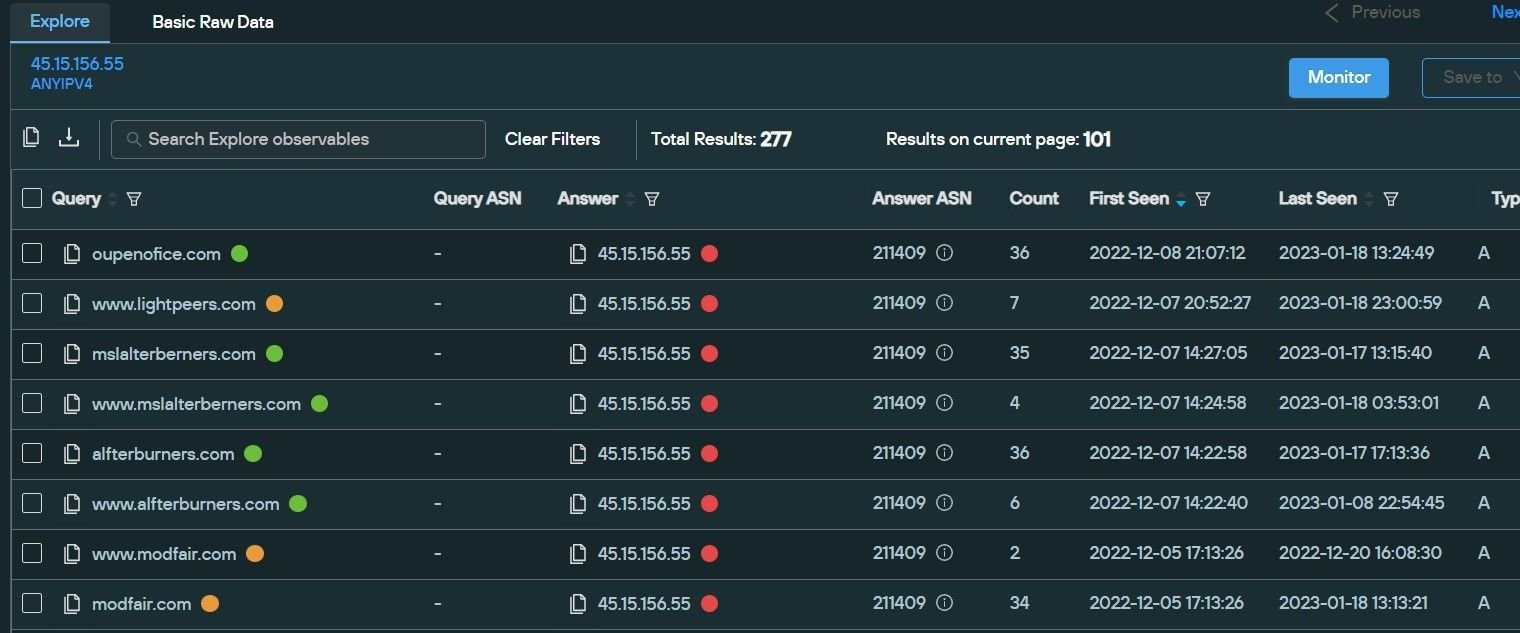
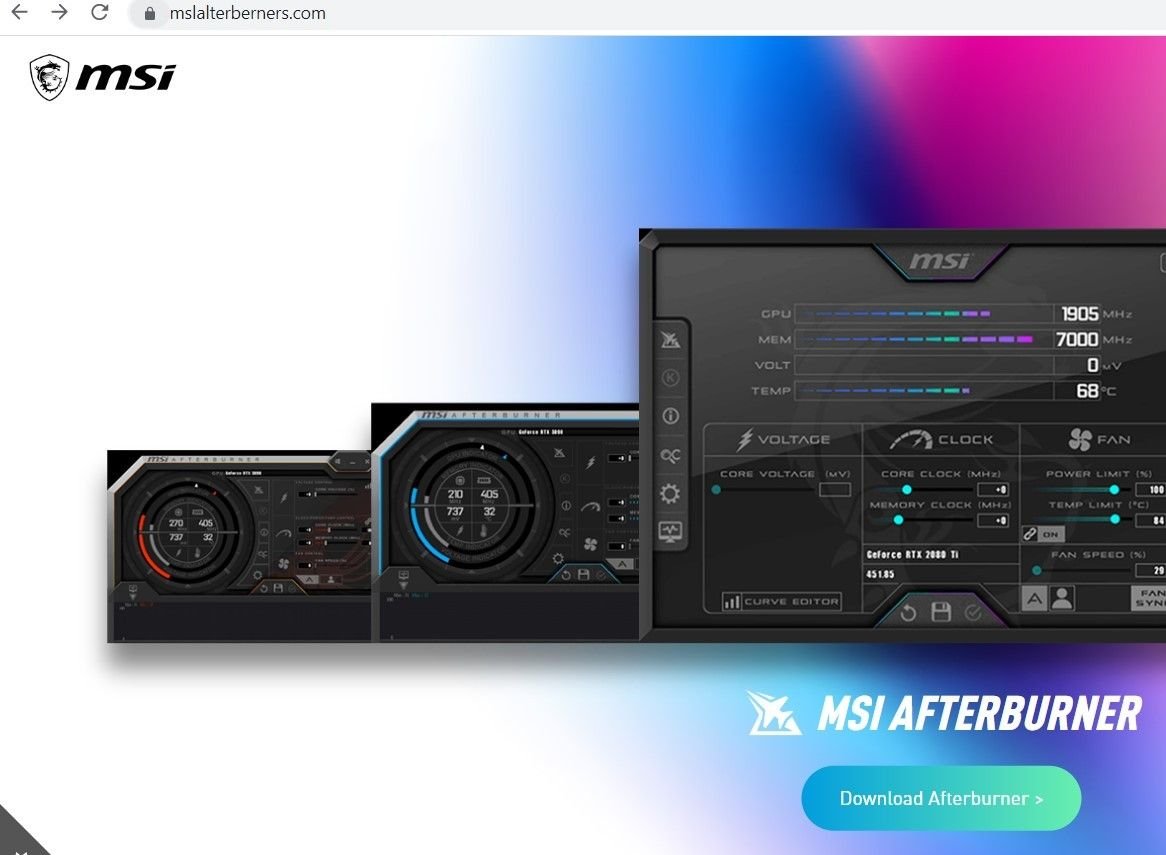
Throughout our collaboration with MalwareBytes whilst investigating DDOS-Guard, we uncovered a host of phishing domains impersonating AnyDesk software on the same IP infrastructure that hosted multiple spoofing pages targeting MSI After Burner, Trading View, Team Viewer, open source software such as OBS Studio and infostealers including Vidar and Aurora.
Through a combination of enriched data monitoring and granular research into DDOS-Guard’s infrastructure, we’ve kept track of similar infostealer-based threat activity, which has stuck around for the last two months.
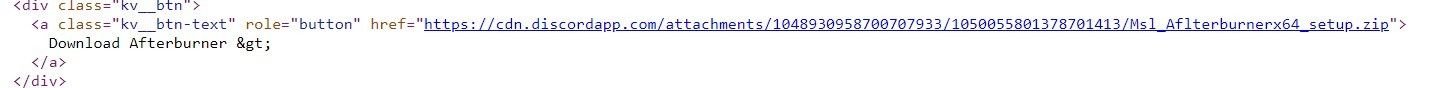
In many cases, malware is being hosted on legitimate services such as Dropbox and Discord – domains hosted on 45.15.156[.]55 feature download links to an archive file hosted on Discord.
New attacks vectors
At the time of publication, both Dropbox and Discord have taken down multiple links involved in the campaign, but we are still seeing evidence of numerous new domains that are dropping similar infostealers.
Threat actors seem to be using DDOS-Guard’s services to propagate malicious activity.
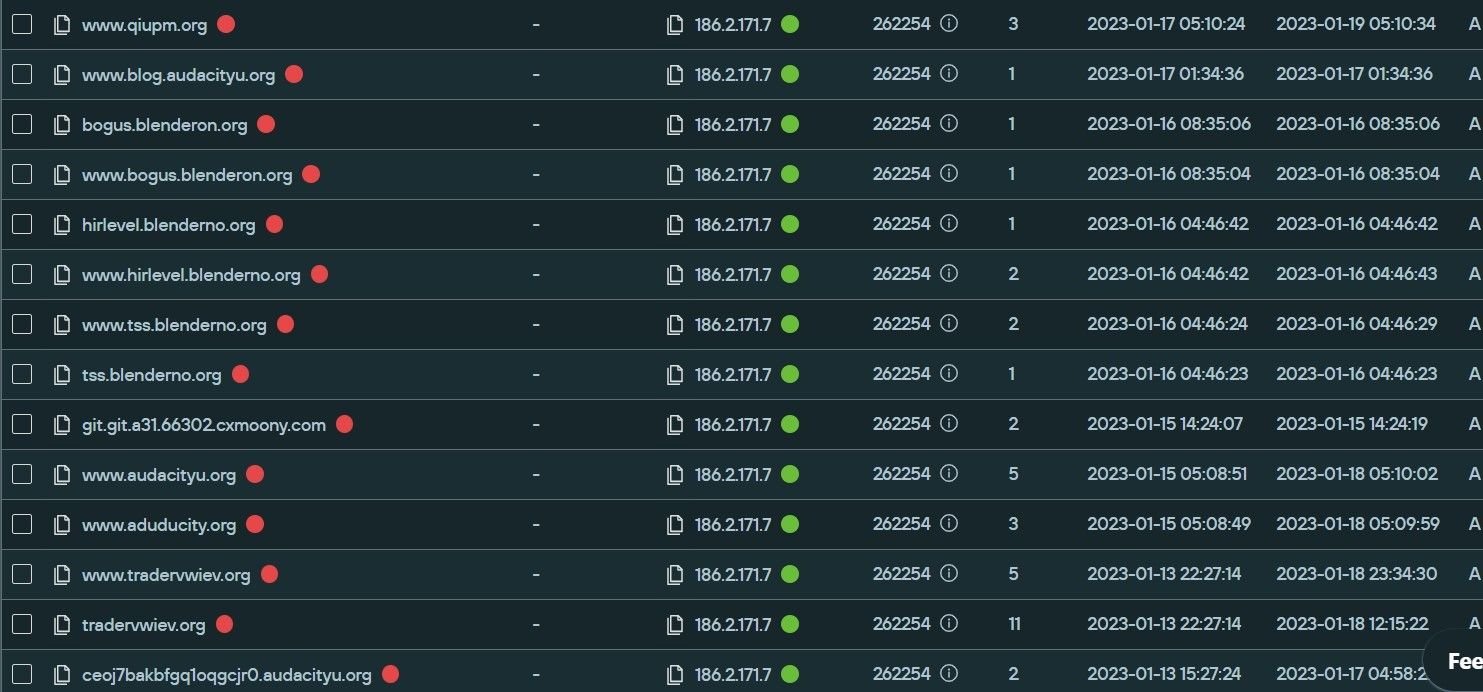
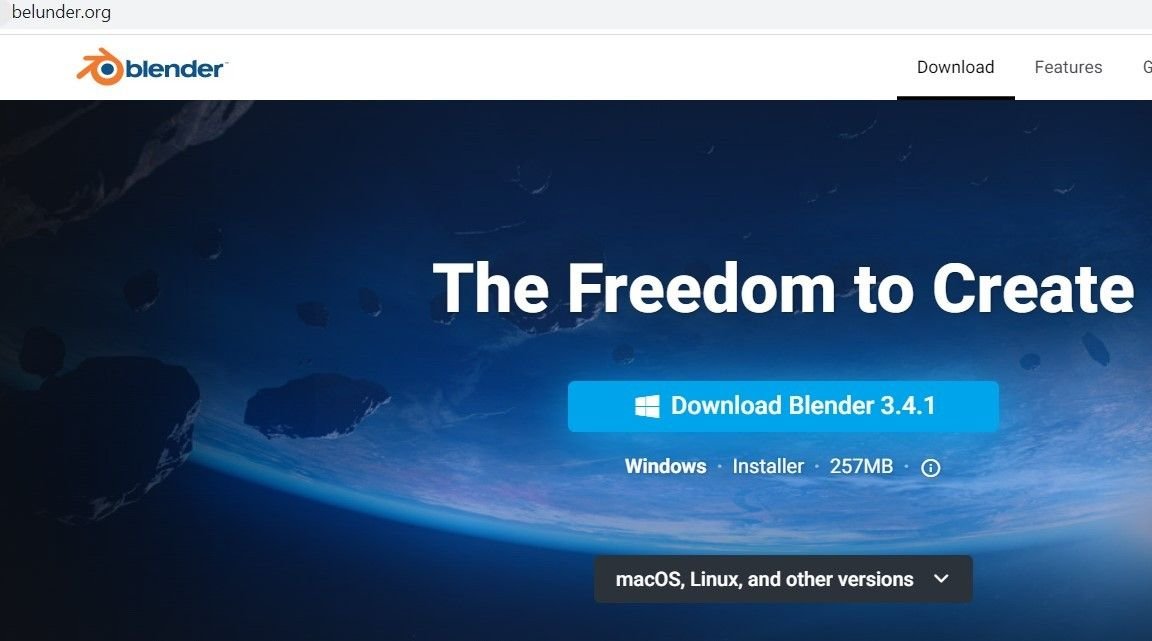
We discovered multiple domains hosted on one of its IPs – 186.2.171[.]7 – targeting open-source software platforms such as Blender 3D, Digital Audio Editor Audacity, the Brave browser and the image editor GIMP, among others.
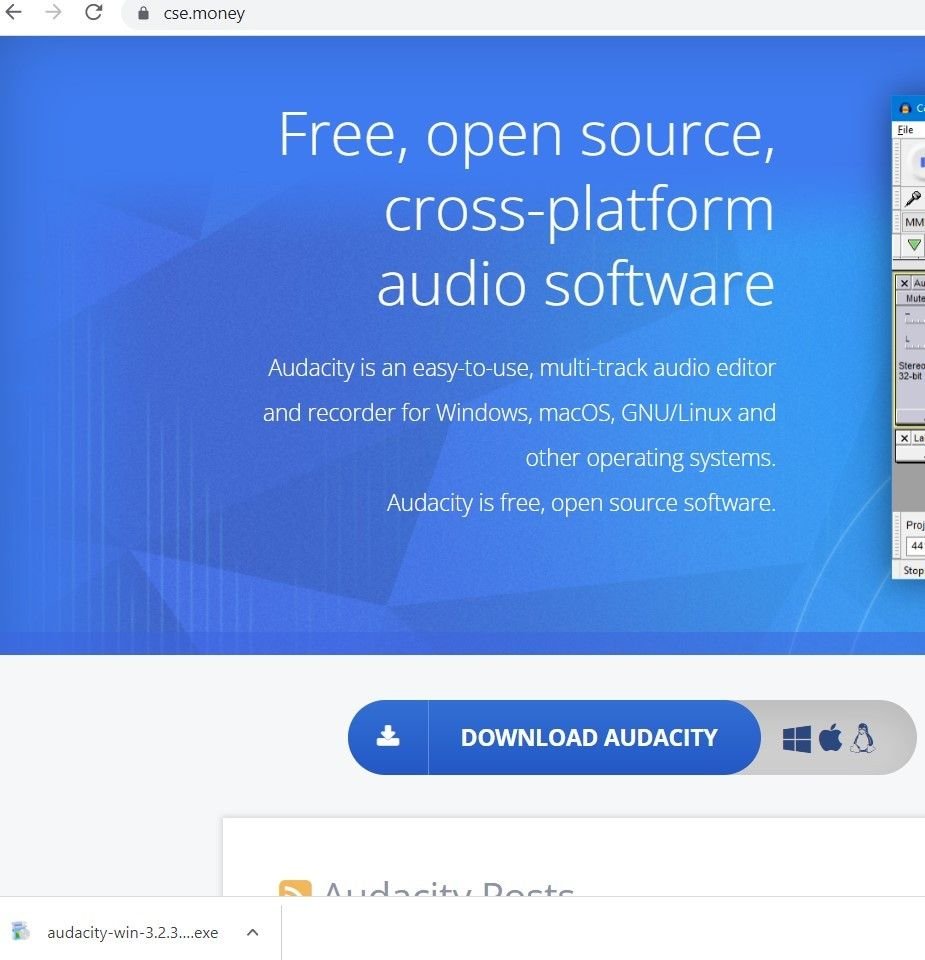
Even the spoofing domains that do not feature open source platforms – such as numerous typosquatted domains targeting the Steam community marketplace CS.Money – host malicious content similar to the spoofed open-source domains.

Infostealers and crypto wallets
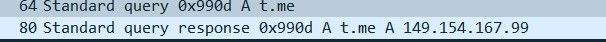
In all these cases, download links prompt an install of a version of the Vidar infostealer, which in turn attempts to connect to a Telegram account (t[.]me/jetbim) and a Steam profile steamcommunity[.]com/profiles/76561199471266194
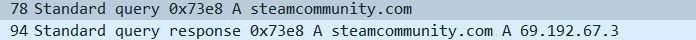
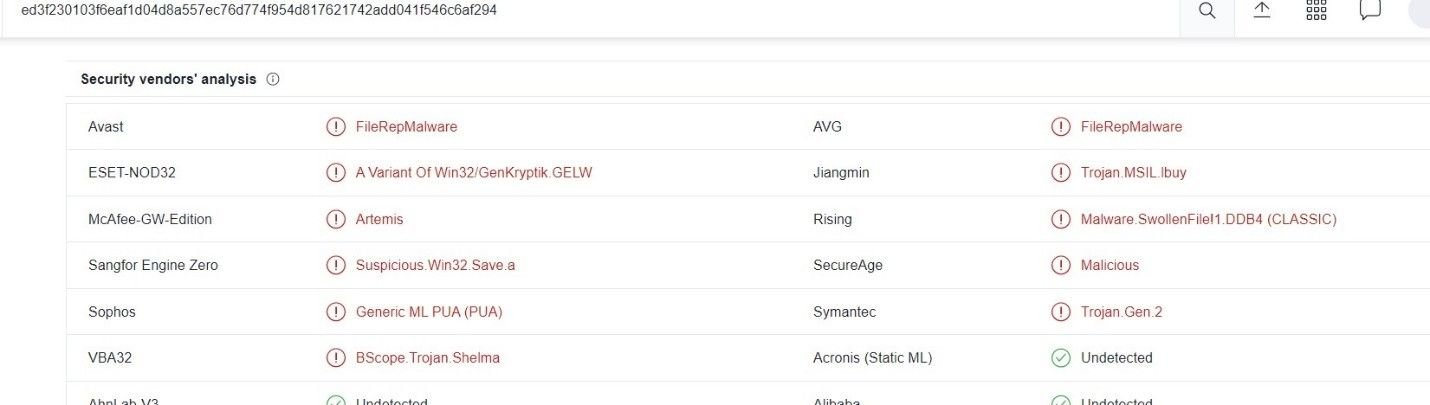
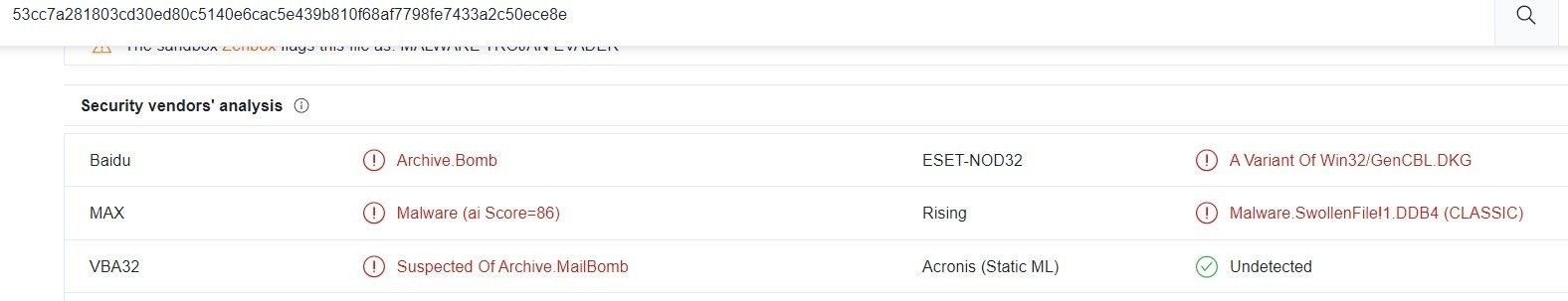
The malware is equipped with evasion capabilities, as well as resulting in a timeout in most open-source sandboxes:
“C:\Windows\System32\cmd.exe” /c timeout /t 6 & del /f /q “C:\Users\Admin\AppData\Local\Temp\blender-3.4.1-windows-x64.exe” & exit
The infostealer attempts to access a crypto wallet as it tries to read files and directories:
C:\Users\Admin\AppData\Roaming\Electrum\wallets\
C:\Users\Admin\AppData\Roaming\Electrum-LTC\wallets\
C:\Users\Admin\AppData\Local\Coinomi\Coinomi\wallets\
Similar infostealers have been involved in spoofing brand domains redirected from Google ads. We anticipate that these brands will soon be targeted with SEO-poisoned malvertisements.
Cybersecurity-focused social media accounts have recently posted about the open-source Brave browser (one of the brands spoofed on this IP), redirected from Google Ads, which connect with the same Telegram and Steam community account highlighted above, hinting that the campaigns could be linked to the same group of threat actors.
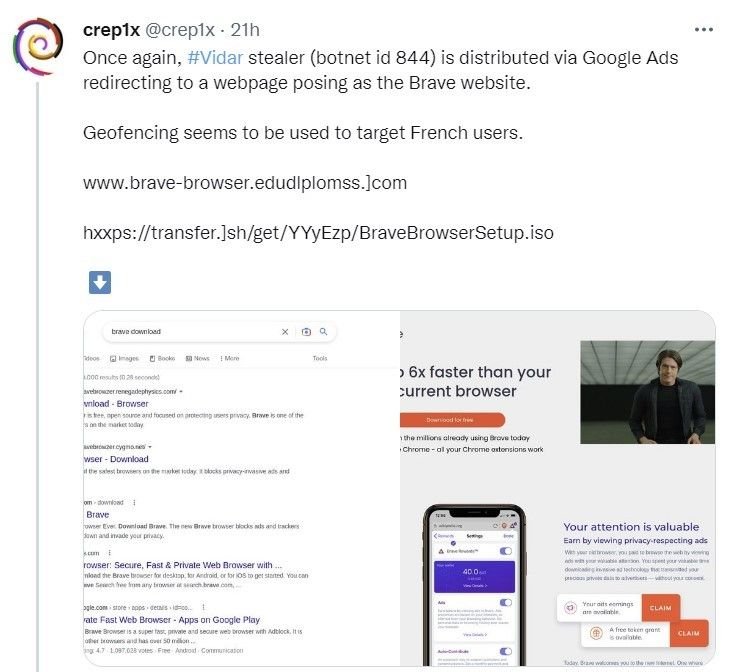
Old campaigns still active with new IoC’s
As global attention turns towards active campaigns, threat actors are showing signs of resilience by moving on to new IoCs and previously unaffected infrastructure.
Banking trojans distributed through fake AnyDesk ads were one of the first malvertisment attack vectors we observed, and new spoofed AnyDesk domains are still being created – wvww.anydeskcom[.]top, featuring the IcedID banking trojan, is only 24 hours old at the time of writing, but the domain is already being distributed through Google ads.
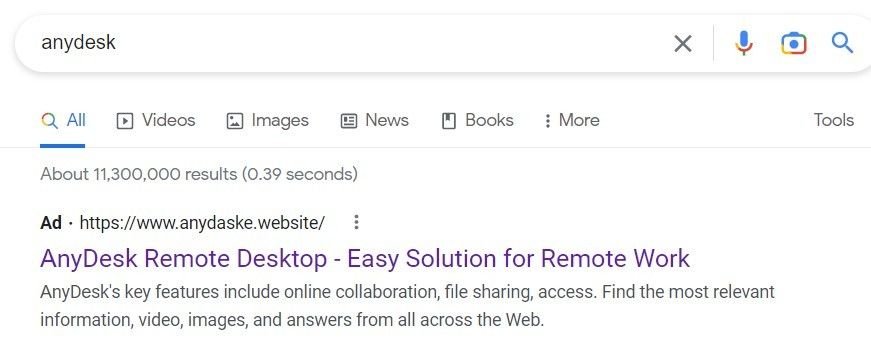

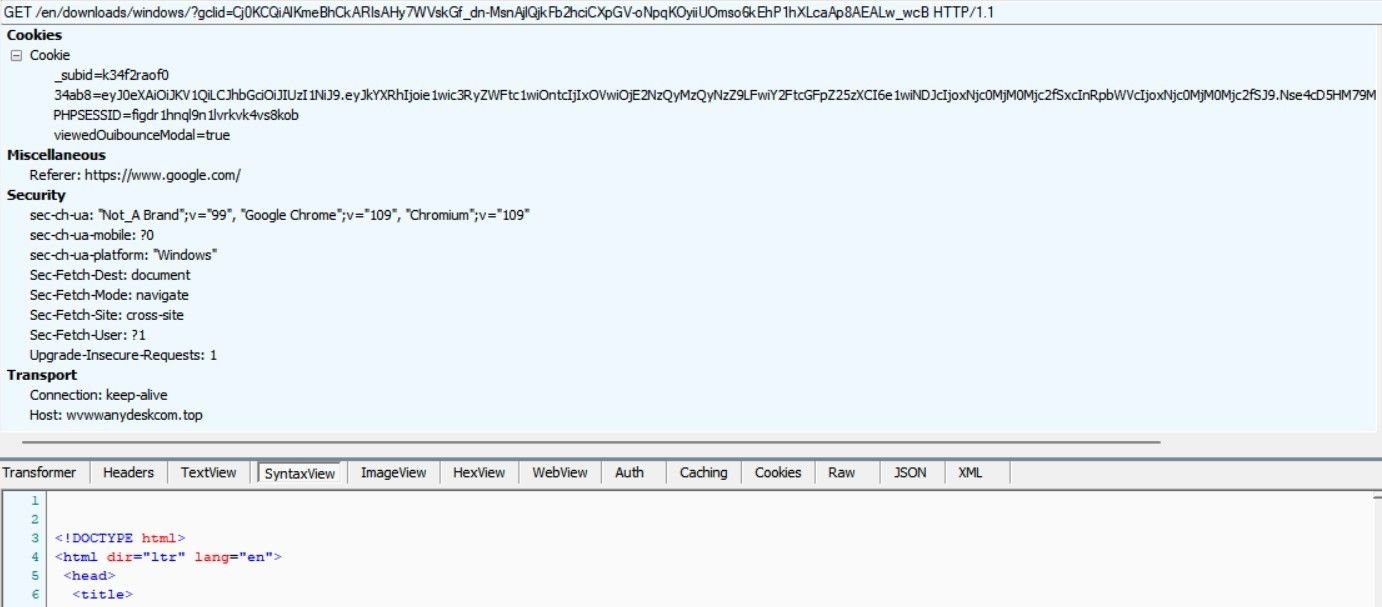
The anydaske[.]website is visible from a Google ad, but the redirect points to a new domain in an attempt to keep one step ahead of researchers and security teams, by creating new IoCs that don’t appear in most global feeds.
Clicking on ‘Download Now’ injects the malicious archive file, containing the IcedID banking trojan.
The domain is hosted on 46.173.218[.]229, which proves the infrastructure consists of domains and brands that were involved in the previous malware distribution campaigns, such as Microsoft Teams, the IRS and Adobe.
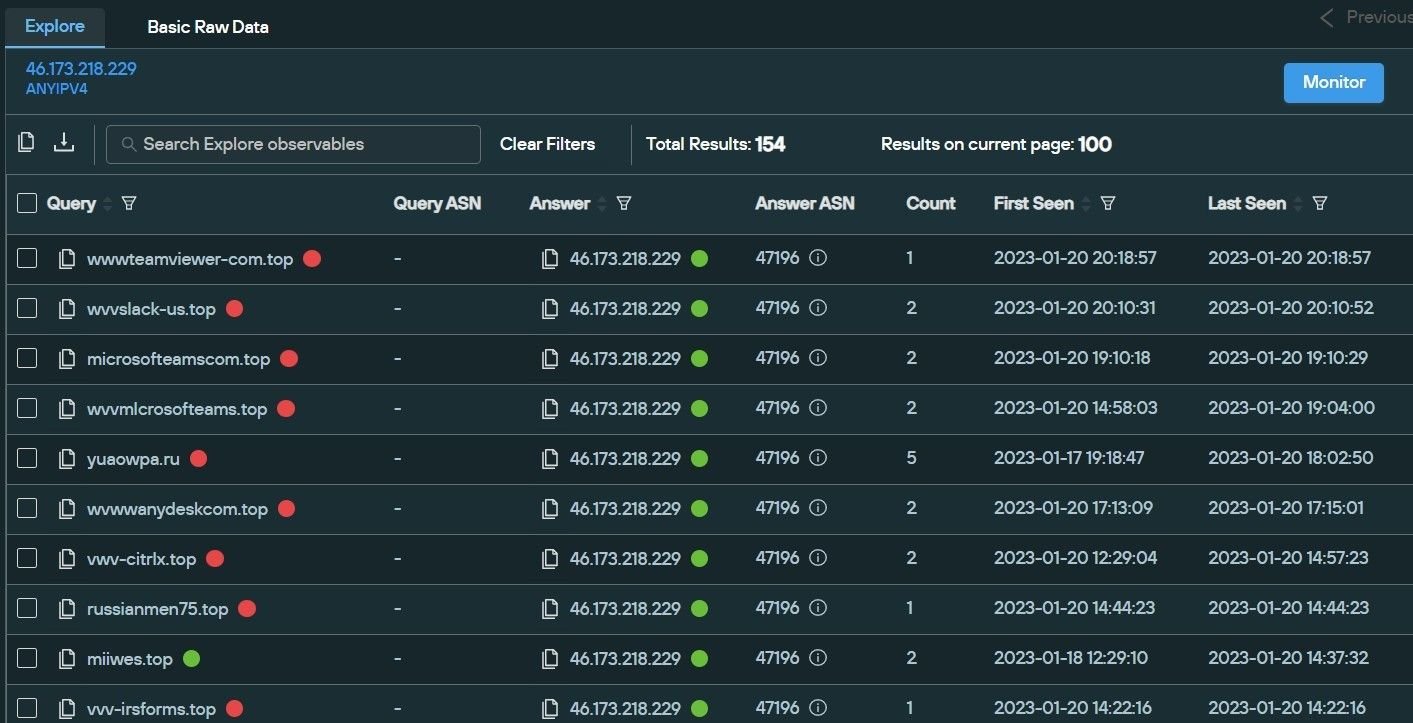
Through enriched scanning, we have identified pages being spoofed in numerous different languages, indicating typosquatted domains across multiple distinct global regions.
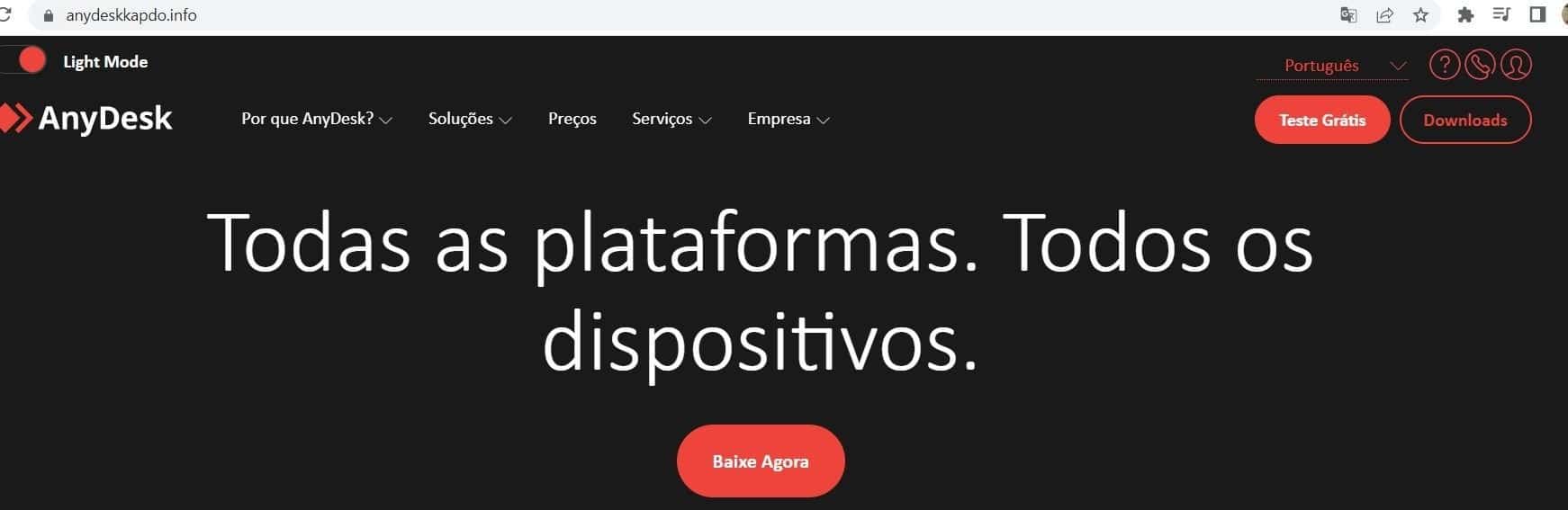
MetaMask browser extension scam
Malware delivery is not the only attack vector utilised by threat actors looking to abuse search engine platforms with SEO poisoning.
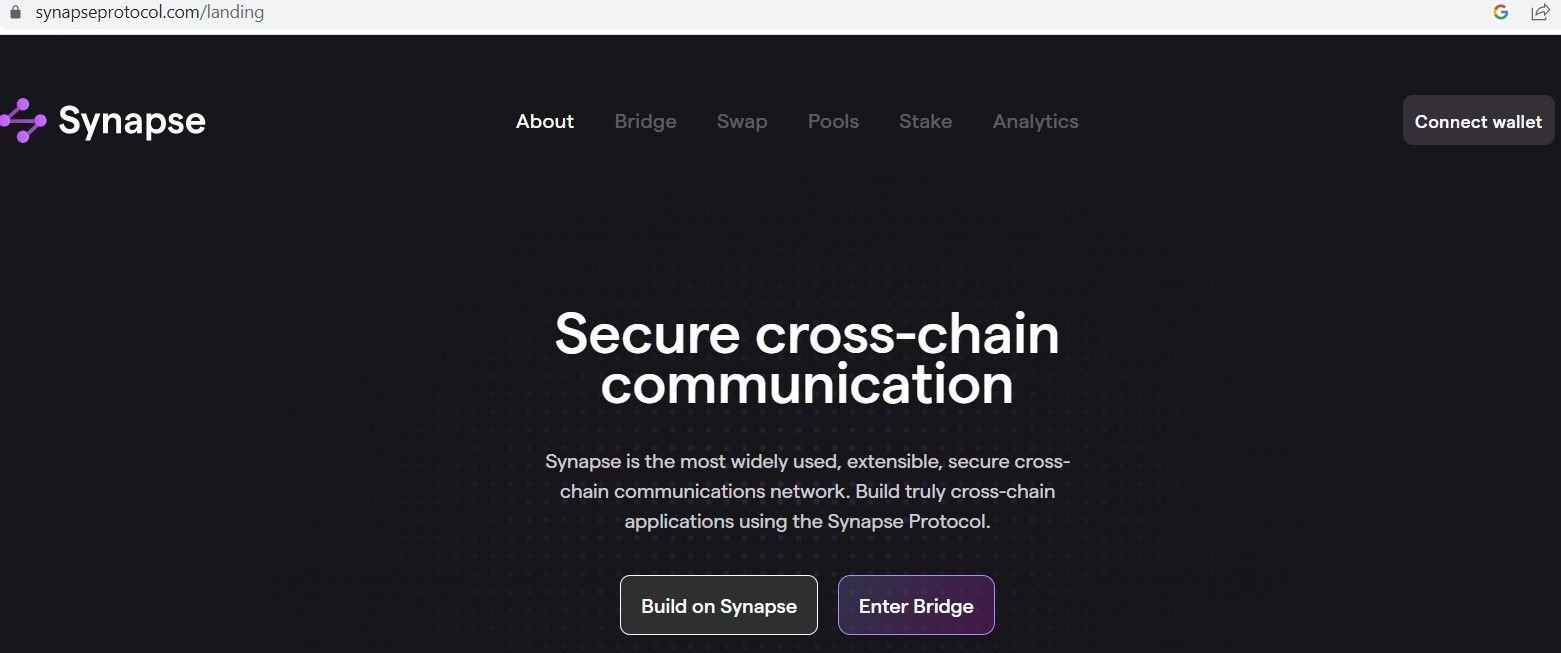
During our Google Ads research, we uncovered a campaign targeting users of the Synapse Bridge Protocol – a popular platform that allows for the transfer of crypto assets between blockchains.
The legitimate Synapse domain asks users to manually connect their crypto wallet of choice to facilitate a secure transaction.
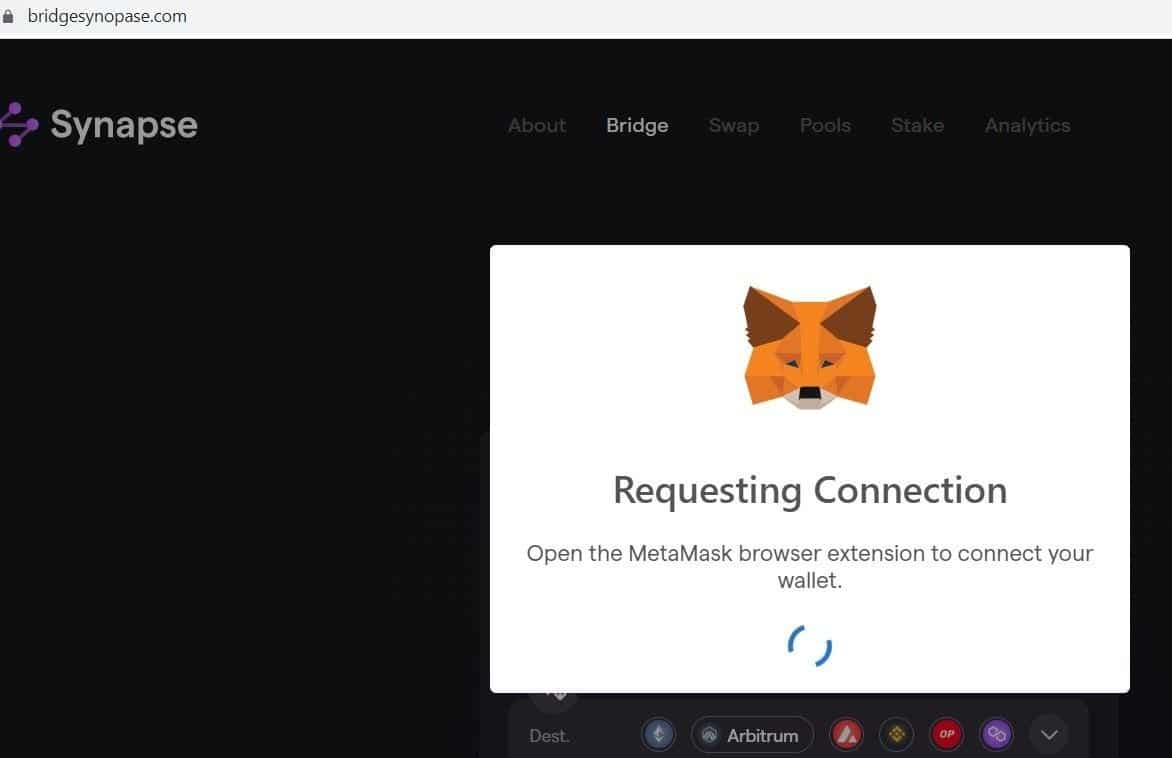
The phishing domain, however, attempts to connect directly with a MetaMask wallet, providing that the MetaMask browser extension is already installed.
Alternatively, the malicious domain asks users to install the extension, if it’s not already enabled in their browser. As the user has been redirected from a legitimate search engine, there is a high chance that many would fall victim to it without manually verifying the correct domain name.
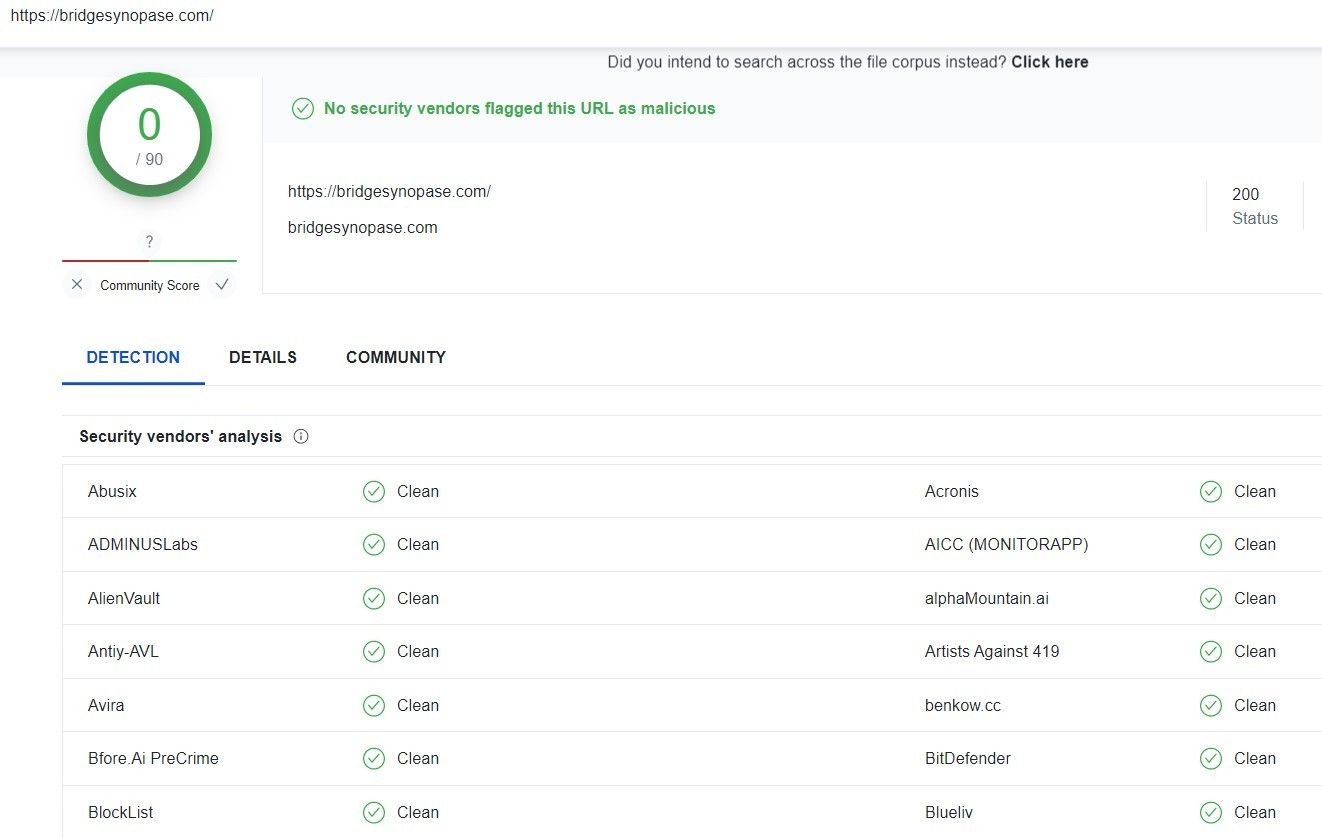
Most domains involved with this scam aren’t flagged on VirusTotal:
Conclusion
SEO poisoning and malvertising are not new techniques, but a recent surge in activity indicates there may be a lot more to come, with numerous new and well-established brands targeted across multiple global regions, languages and applications.
Government authorities such as the FBI have begun to sound the alarm about the rise in cases. Still, the sophistication of the threat actors’ approach and their willingness to switch to new infrastructure means that the number of people affected will inevitably rise.
It’s vitally important for security teams to protect consumers and supply chain operations by deploying proactive modes of defense, including keeping a lookout for any new campaigns utilizing SEO poisoning that are targeting their own or their customers’ infrastructure.
We’ve created a bespoke feed for our paid subscribers to keep one step ahead of threat activity. Our ‘Malvertising Domains’ feed is updated regularly with new IoCs – including suspect domains and IP infrastructure – and we’ll continue to monitor the situation using enriched data from our daily IPv4 scans, featuring billions of nodes across the globe.
Follow us on LinkedIn and Twitter for weekly threat intelligence updates and research.

