US Financial Customers Targeted with Broad Multi-Organization Smishing Scams to Steal Personal Information
Our investigation into a new phishing campaign revealed that the same threat actor is using dozens of domains utilizing Brand Impersonation, including a wide variety of US national banks such as Wells Fargo, Bank of America, Citibank, and Chase, as well as regional banks.
This campaign is harvesting personal and financial information from targeted users, including financial login credentials, credit/debit card info, mother’s maiden name, address, and government ID.
This campaign is a reminder that smishing scams that impersonate well-known financial institutions continue to be an issue for consumers and financial institutions. Smishing attacks provide many advantages over email-based attacks, including higher open rates, a sense of urgency and personalization, and technical advancements such as spoofed phone numbers. The potential rewards are high.
We also observed the same threat actor utilizing domains spoofing the Wirex crypto wallet with debit card functionality. These implementations were much less mature, possibly signaling future crypto attack directions.
Multiple Brands Targeted in Phishing Attempts
A Senior Staff Software Engineer from Trellix recently shared on LinkedIn about receiving an SMS claiming to be a “security notification” from “Wells Fargo” regarding the suspension of their debit card due to “unusual activity.”
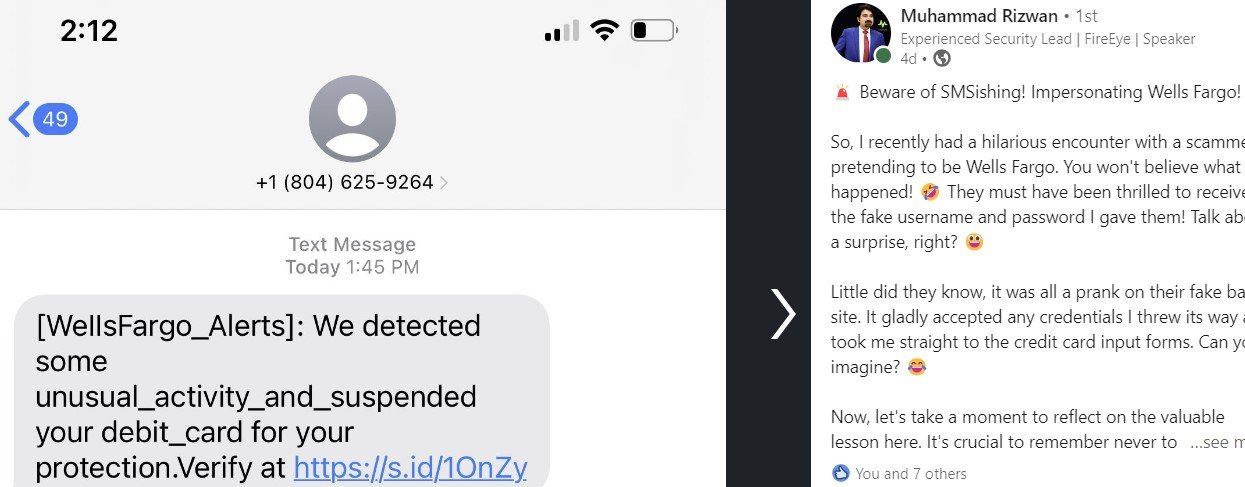
SMS from LinkedIn Post
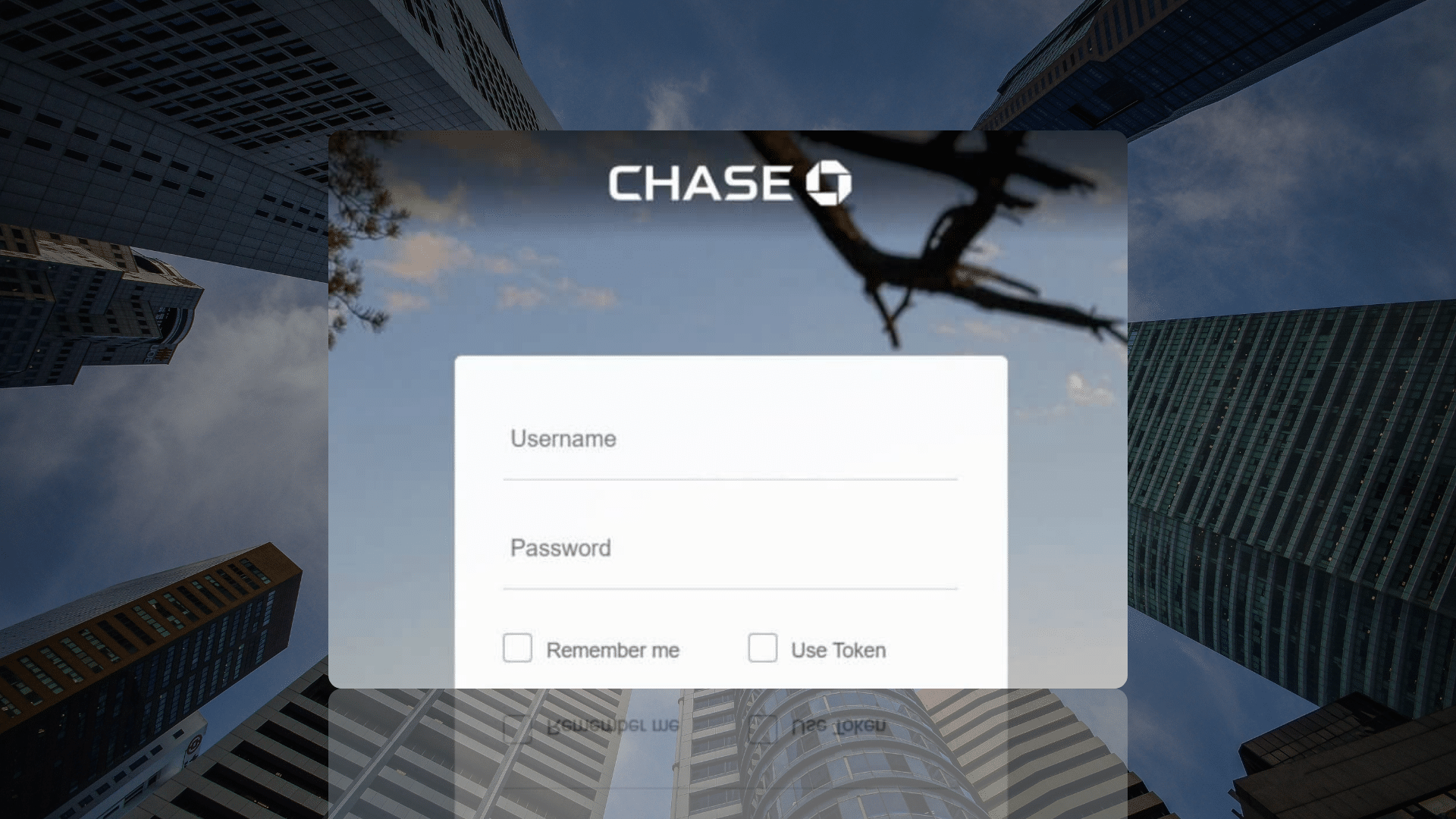
As seen from the original SMS, the URL shortener service was initially used as a first redirect to the phishing page (s.id has terminated the redirect link to the phishing URL at the time of writing). Targeted users are redirected to a page that mimics the Wells Fargo login page.

Wells Fargo fake Login Page
Each user is assigned a unique ‘apitoken’ value in the URI, which is likely tracked by IP address for that user. The URLs involved in the campaign track IP by referencing legitimate sites api[.]org and ipapi[.]co.

IP check in JavaScript
The phishing campaign is not limited to Wells Fargo. By analyzing the JARM value used by the domain cz97sevef[.]online and other header meta information, we were able to identify dozens of other domains linked to the same campaign, involving multiple US national and regional banks.
Our scanners indicate that the campaign started using phishing domains with a banking theme in the second quarter of 2023 and has utilized varied domains associated with different banks. We confirmed that, for all these cases, using the same URI with the same ‘apitoken’ value for the same workstation/IP would successfully load the following pages:
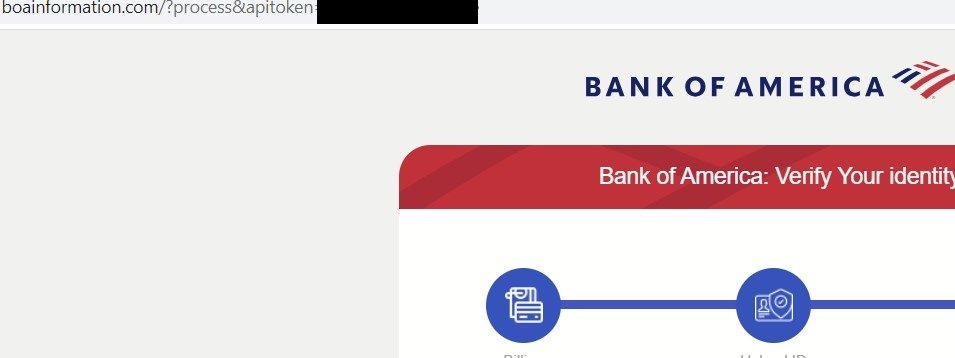
Fake Bank of America Login Page
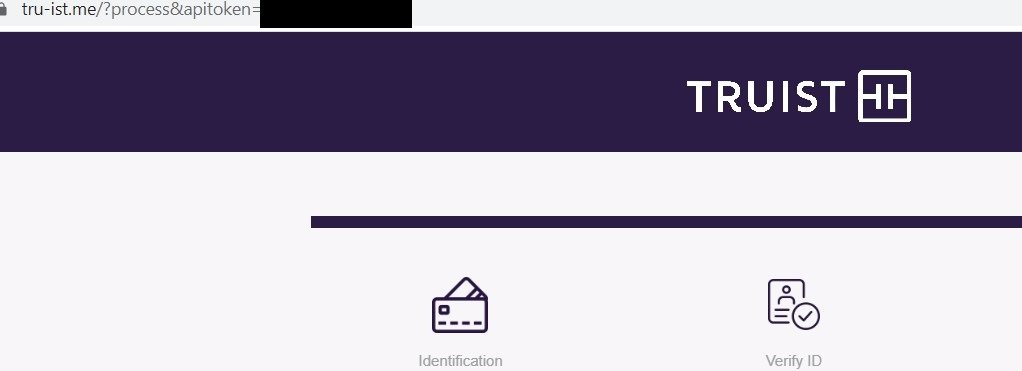
Fake Truist Bank Login Page
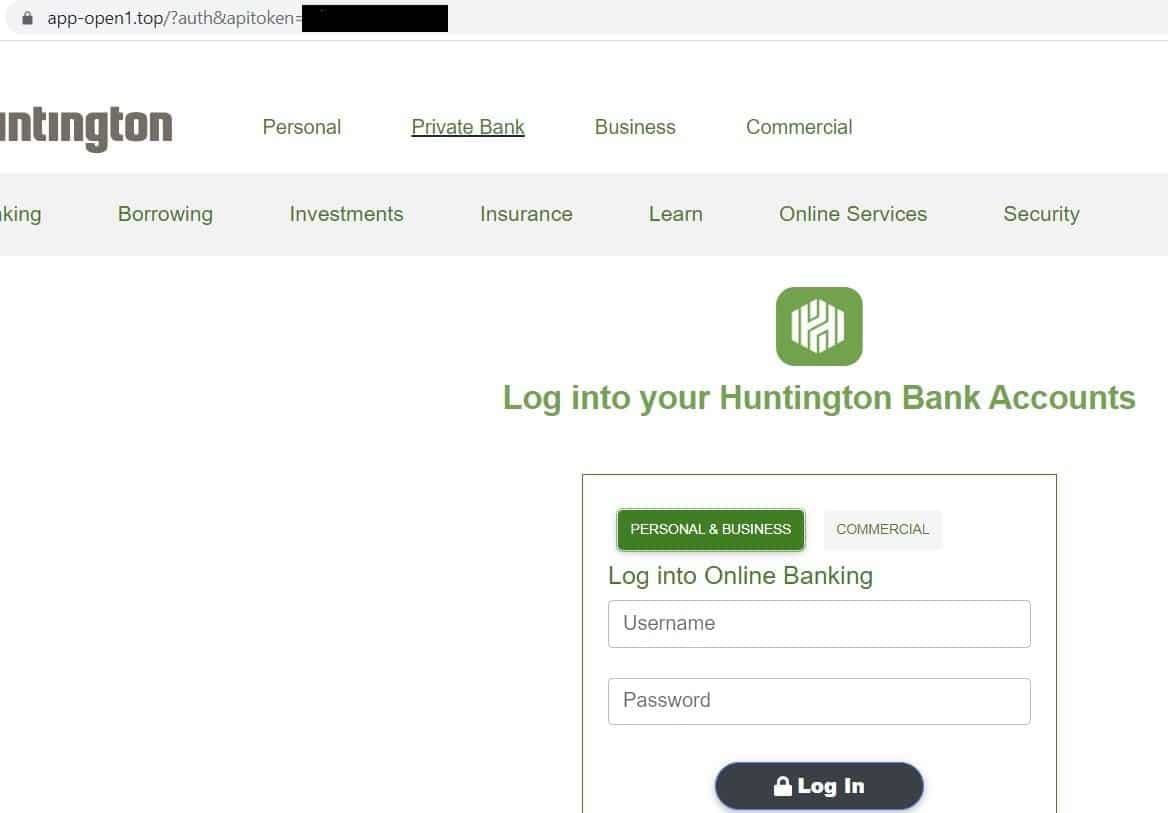
Fake Huntington Bank Login Page
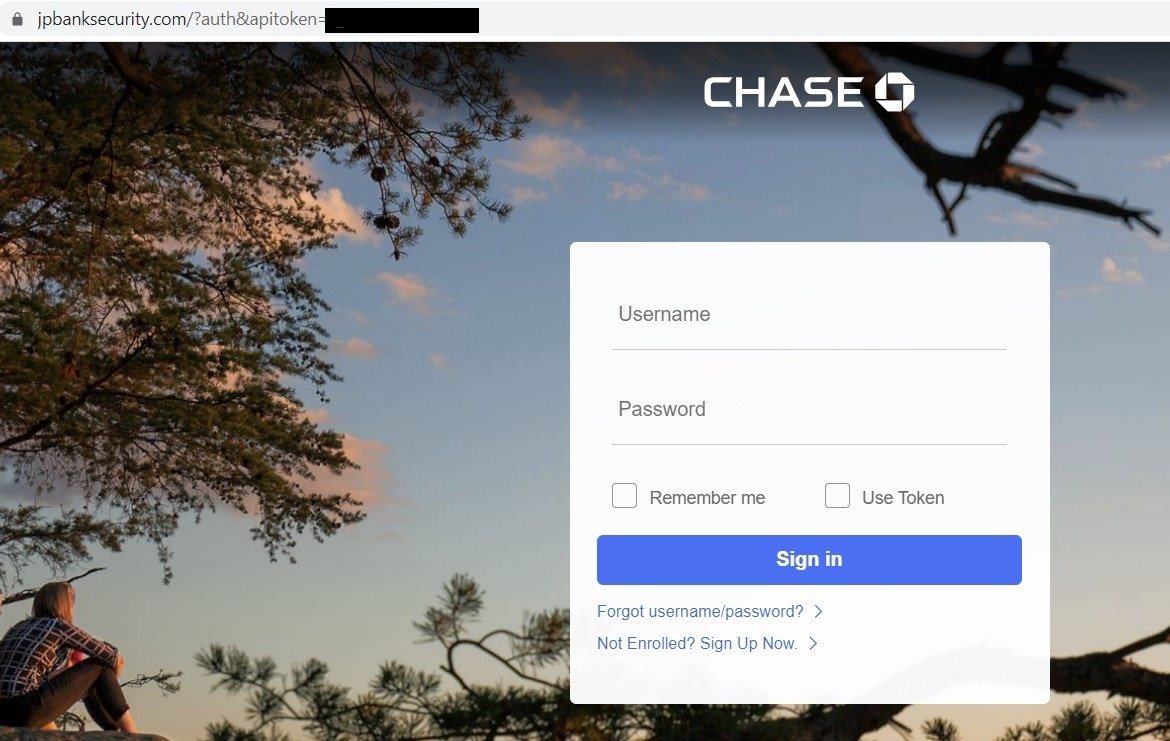
Fake Chase Bank Login Page

Fake Citi Login Page
In addition to traditional banks, brands such as the Wires crypto wallet with a debit card for crypto assets were also targeted in the same campaign.
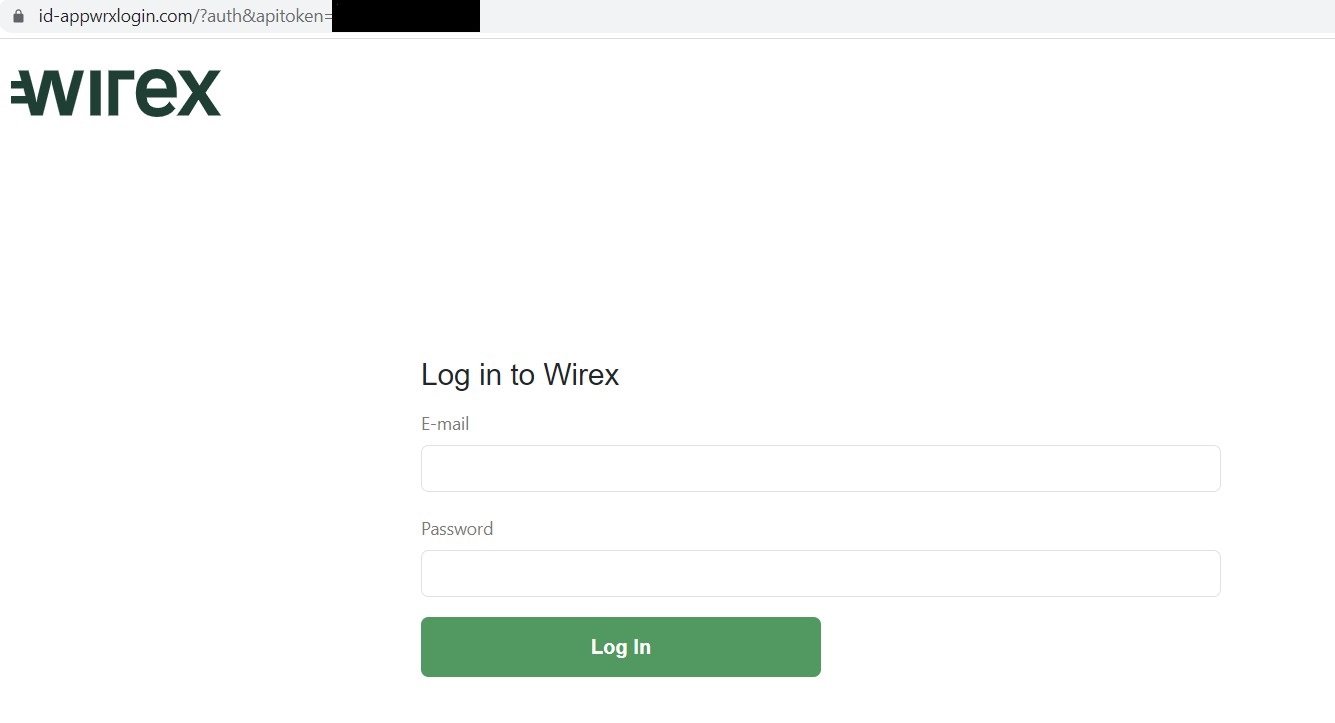
Fake Wirex Login Page
During our testing, we found that the phishing content did not open when URLs were accessed outside of the USA, which is consistent with the nature of the attack. Furthermore, once an ‘apitoken’ is assigned to a workstation/VM IP, bank-spoofing domains will send a ‘403’ error with the same URI if accessed from a different IP/machine.
The threat actors appear motivated to harvest as much information as possible. The login page only serves as a precursor to redirect users to enter credit/debit card information and other personal information, including a picture of a government ID, on the attacker’s controlled website.
For example, a domain spoofing ‘Bank of America’ is boainformation[.]com, which attempts to upload entered personal information to clientarea2[.]site via a POST request through a web form, as seen in the following Fiddler screen grabs:

POST request to clientarea2[.]site generated from submission on boainformation[.]com
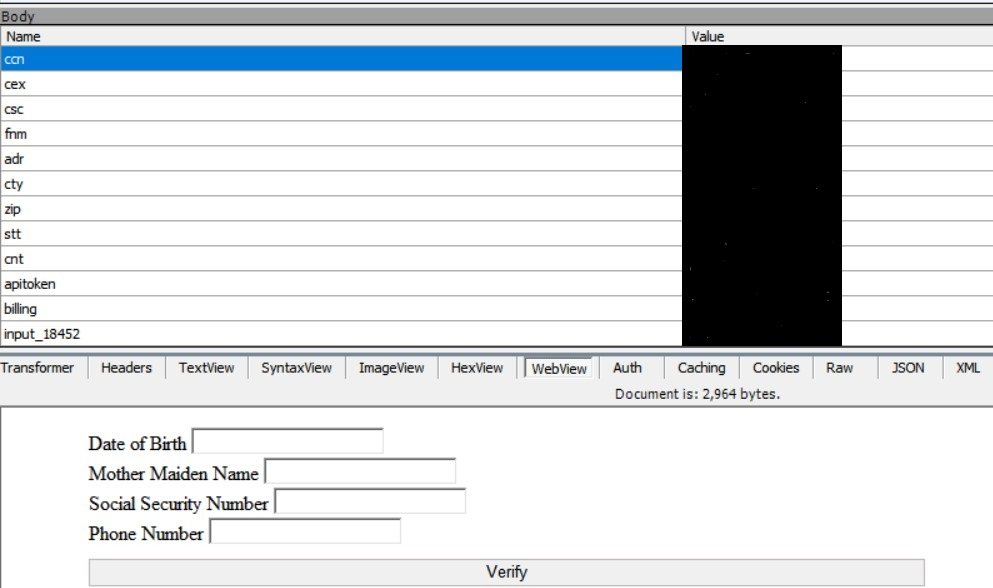
Fiddler’s webform view of information sent in POST request and next information requested
In addition to the personal information provided, the ‘apitoken’ value is also passed via a POST request to associate the user with a unique ID.
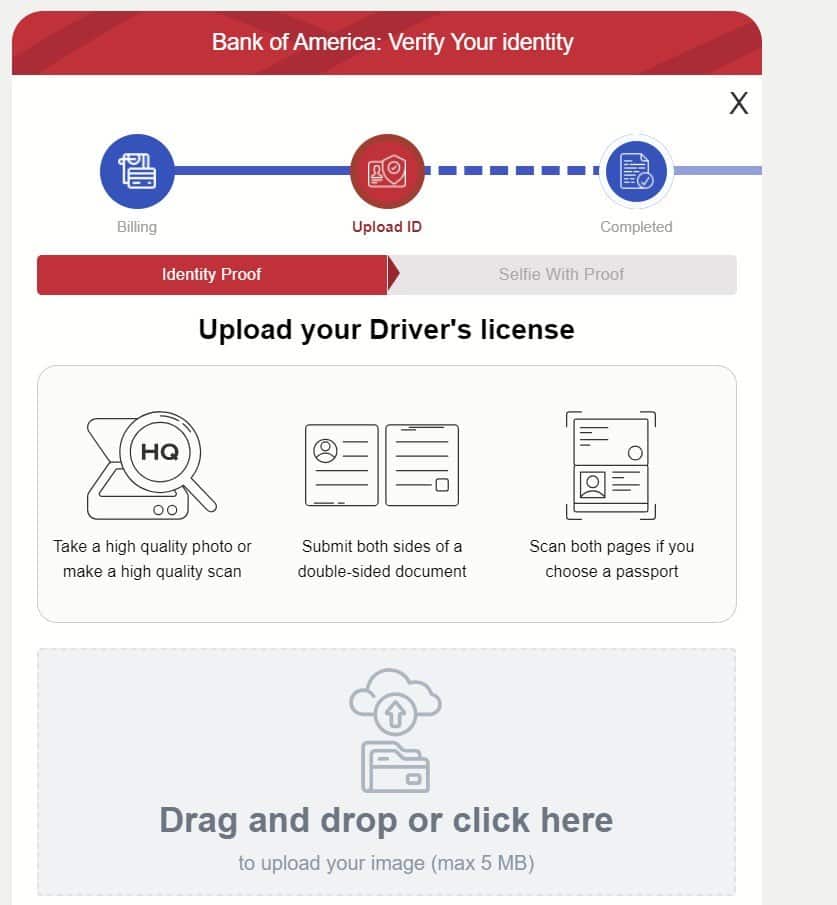
Phishing site asking for Government ID
While threat actors are interested in harvesting all information entered, validation has not been implemented on their servers to check the validity of Government ID or its cross-match with personal information entered previously, which is usually done on legitimate sites.
The value of the ‘apitoken’ associated with the user’s data remains consistent with all bank spoofing domains. If the same URL is accessed with an ‘apitoken’ for which data was previously entered, the user will be redirected to a ‘verified’ page for all the domains connected in the campaign. For instance, once information has been entered by the user on a spoofed Bank of America domain’s URL, opening Citi’s spoofed domain with the same ‘apitoken’ will load the same information entered on the fake ‘BoA’ form.
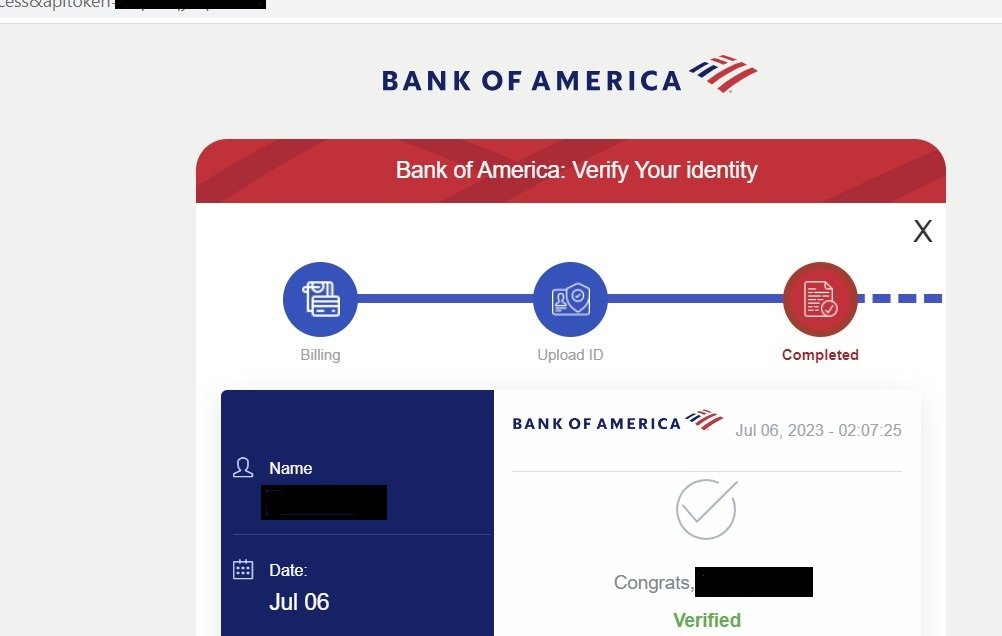

Reusing user information
Most of the IOCs involved, including initial phishing domains as well as domains harvesting personal data, have little to no detection on VirusTotal.
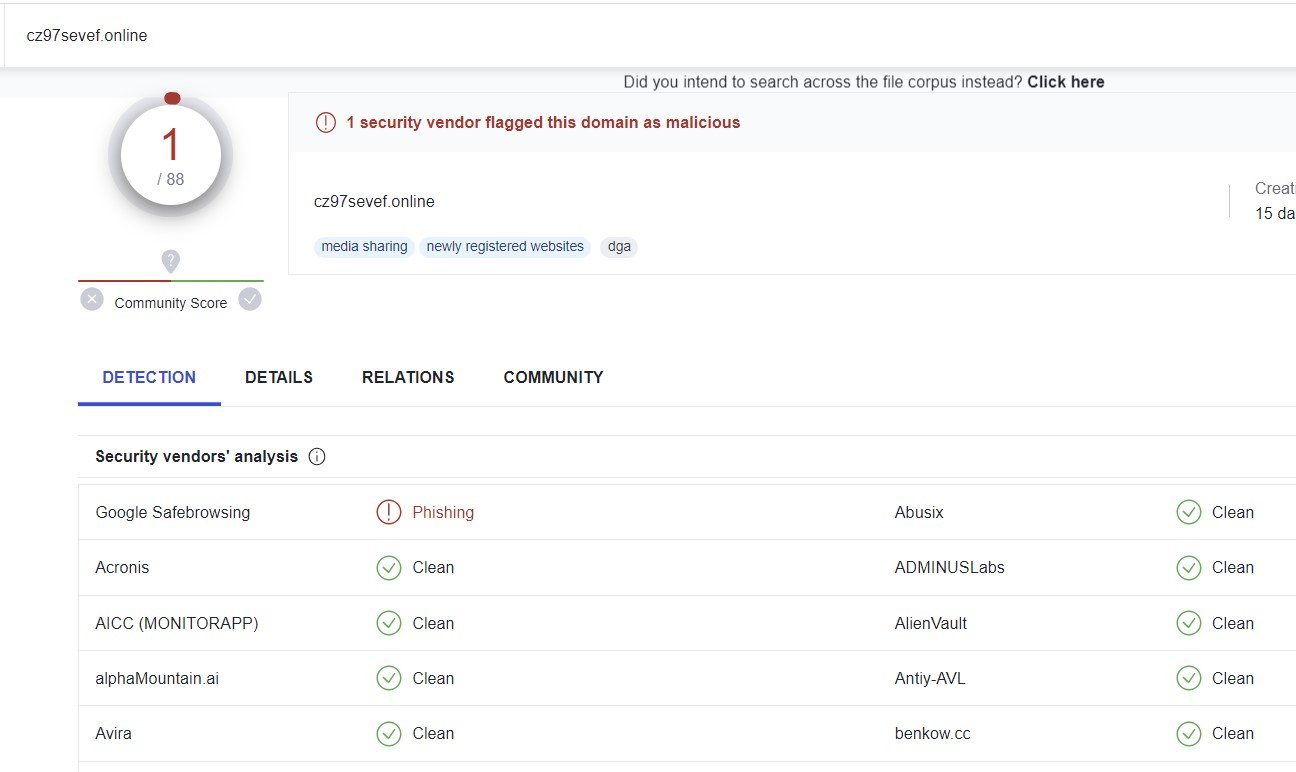
VirusTotal Results
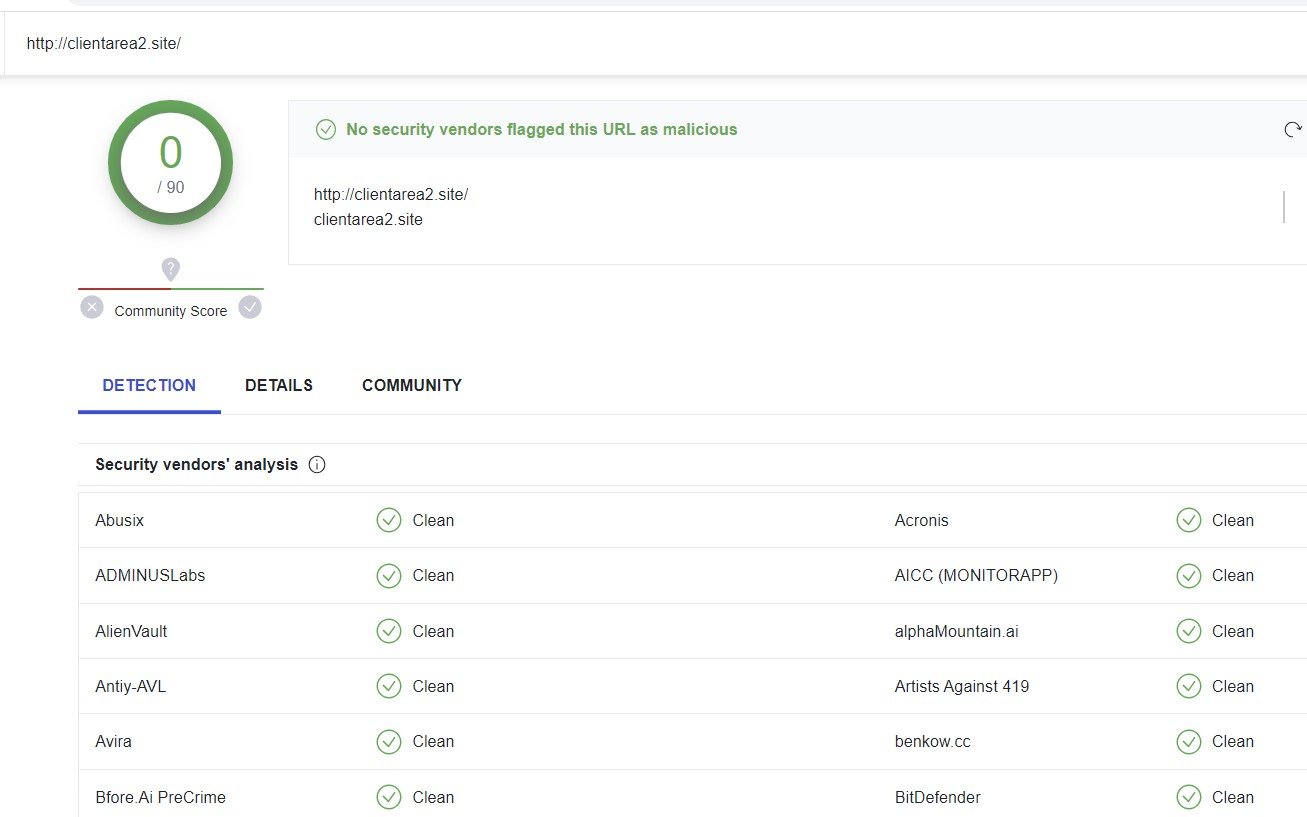
VirusTotal Results
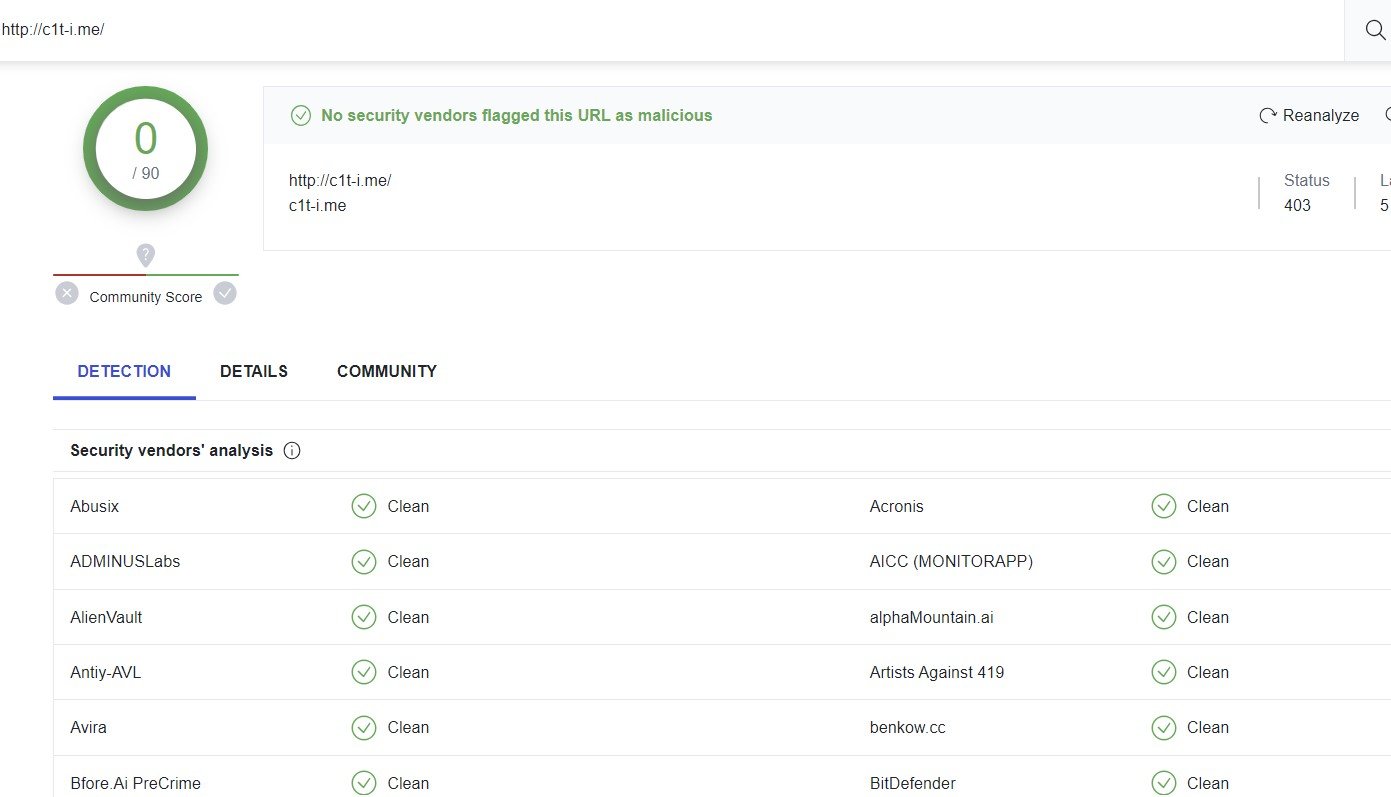
VirusTotal Results
In some cases, domains are only intended for credential phishing purposes and give an error message on the first page, no matter what credentials are entered. At the backend, the same clientarea2[.]site domain is used to upload credentials via a POST request.
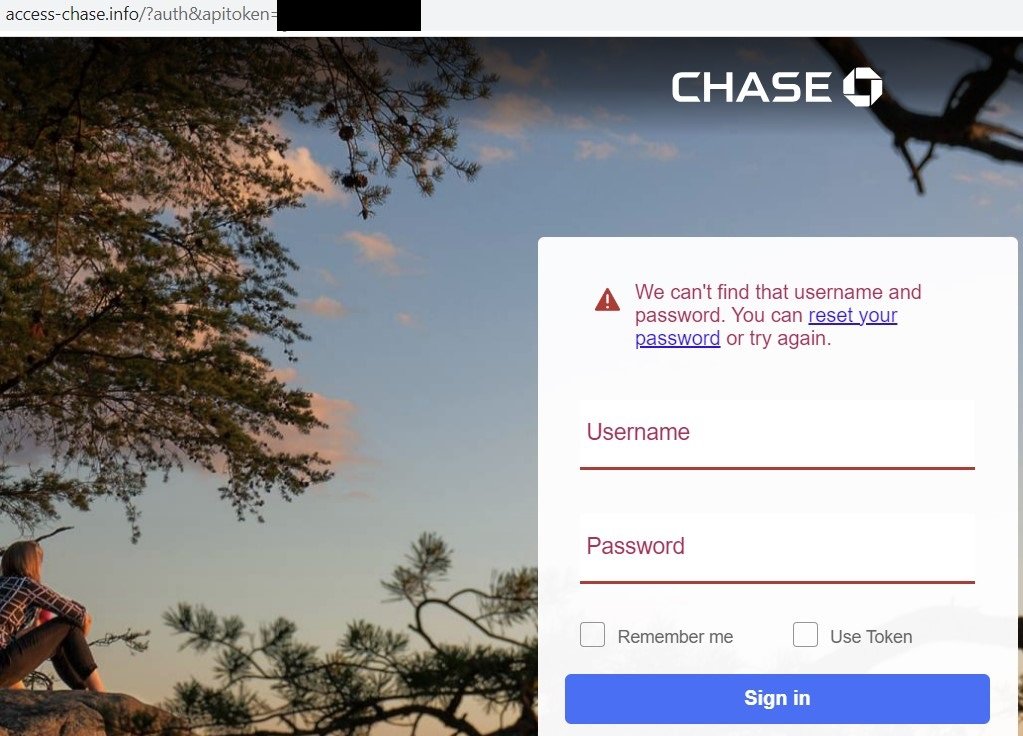
Error message after credential phishing
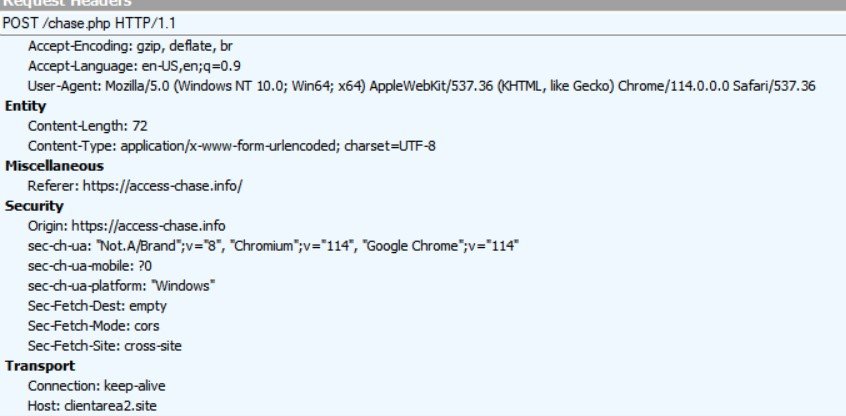
POST request to send credentials
Malicious Infrastructure
The domains connected to the campaign use a wide variety of IPs, ASN services, nameservers, and registrars. Some IPs show a history of being associated with phishing activity related to impersonating postal services and mobile manufacturers like Apple and Xiaomi.
For example, domains associated with the IP address 111.90.143[.]126, which is currently hosting c1t-i[.]me — a domain spoofing Citi Bank — have been observed with a few old domain names likely associated with those previous campaigns, such as myinformedparcl[.]com and www.icloud-com-id[.]us, among others.
Some IPs are dedicated to bank spoofing domains specific to one particular brand, such as 15.223.110[.]65 for Chase. The same IP also consists of the domain alert-usaa[.]info, which is an open directory with an archive file containing details of anti-crawler projects and libraries that may be utilized by threat actors, along with a list of IP ranges, blocked words, and user agents used to identify crawlers/bots.
Smishing Remains Popular
In the ever-changing threat landscape, threat actors operate in a fast-paced environment to host new threats using new infrastructures. Researchers must use tools that comprehensively track attacker infrastructure, applying a wide variety of correlation and fingerprinting capabilities, to uncover all the connecting dots of the attacker’s infrastructure.
Silent Push will continue to help our users by tracking attacker infrastructure to identify campaigns as early as possible.
Silent Push is an early detection-focused threat intelligence solution.
Our platform provides the most comprehensive view of global internet-facing infrastructure available — sign up now and use our predictive analysis to uncover attacker infrastructure and campaigns before they launch.

