In the modern threat landscape, reacting to cyber attacks AFTER they’ve occurred is simply not good enough. Waiting for alerts to drop, and chasing incidents, leaves critical gaps in an organization’s cyber defenses. SOC and IR teams need to take a proactive approach to threat hunting, and focus on anticipating and neutralizing threats before they cause harm. This, however, is not an easy fix.
Let’s look at proactive threat hunting in an operational capacity, and how Silent Push facilitates early attack detection.
Reactive vs. Proactive Threat Hunting
Traditional IOC-based security models rely heavily on detection-and-response workflow – a system triggers an alert, analysts investigate, mitigation steps follow. While important, this process is inherently reactive – the attack is already underway, or worse, already successful.
Proactive threat hunting flips the script.
It’s about actively searching for unknown threats, identifying adversarial infrastructure, and disrupting attack campaigns early. It involves deep analysis of external signals – such as newly registered domains, anomalous certificate issuances, and links between hosting clusters – long before a threat actor launches a phishing campaign, spins up a malware server, or exploits a vulnerability.
Adopting a proactive stance shortens the attack window dramatically, and can prevent incidents altogether.
Proactive Threat Hunting as a Preventative Measure
Most cybersecurity strategies today are like smoke detectors in a building. They’re important – they alert you when something bad has already started, like a fire breaking out. But by the time the alarm sounds, smoke is filling the room, and damage is already being done. The best you can hope for is a fast response to minimize loss.
Proactive threat hunting, on the other hand, is more like fire prevention.
It’s about identifying and fixing the faulty wiring, removing flammable materials, and enforcing safety measures before a fire ever ignites. Rather than waiting for the warning signs of an active threat, proactive hunters are focused on detecting the early indicators – the unsafe conditions – and stopping incidents from happening at all.
At Silent Push, we empower organizations to practice this kind of cyber “fire prevention”, by offering the most comprehensive DNS and content-based threat intelligence database available anywhere in the world.
Our first-party dataset delivers finished SOC and IR intelligence across your organization’s security stack, that minimizes the need for manual pivots and provides high-confidence telemetry that helps to reveal the full extent of any given attack surface.
By monitoring newly registered domains, on-page content and domain metadata, malicious hosting activity, and other signs of infrastructure deployment, we help organizations detect the conditions for an attack while it’s still in the planning stage – long before traditional tools would trigger any alerts.
Why settle for reacting to fires when you can stop them from ever starting?
Key Elements of Proactive Threat Hunting
- External Visibility: Proactive hunters look outside the perimeter to monitor attacker activity in the wild. They track threat infrastructure across the open internet to catch adversaries in their preparation phases.
- Threat Attribution: By analyzing patterns in domain registration, hosting choices, SSL certificate use, and other artifacts, SOC and IR teams can attribute infrastructure to specific threat actors or malware families.
- Automation and Scale: Threats evolve quickly, and across massive scale. Effective proactive hunting depends on automated analysis and data enrichment to spot connections human analysts might miss.
- Preemptive Disruption: The goal is not just to detect but to neutralize threats before they can mature into full-blown attacks – blacklisting infrastructure, notifying partners, or otherwise hardening defenses in advance.
How Silent Push Empowers Proactive Threat Hunting
Silent Push was founded on the belief that the future of cybersecurity lies in preemptive intelligence.
Our platform is built specifically to support proactive threat hunting at scale, with IOFA™ and proprietary attacker fingerprinting that uses an adversary’s own TTPs against them to reveal pre-attack patterns and management techniques.
Here’s how we enable defenders to stay ahead of emerging threats:
Comprehensive Attack Surface Monitoring
We provide SOC and IR teams with unmatched visibility into emerging infrastructure – domains, subdomains, IPs, SSL certificates, and more – tied to adversarial activity. Silent Push tracks changes across the internet in real-time, helping you spot an attacker’s behavior before they target your organization.
Threat Infrastructure Attribution
Silent Push correlates global infrastructure signals with historical threat actor patterns, campaign fingerprints, and malware infrastructure to anticipate adversary deployment patterns, and provide teams with a cyber early warning system.
This allows defenders to not only detect risky assets, but attribute them to specific actors or attack trends – a critical advantage in proactive threat modelling.
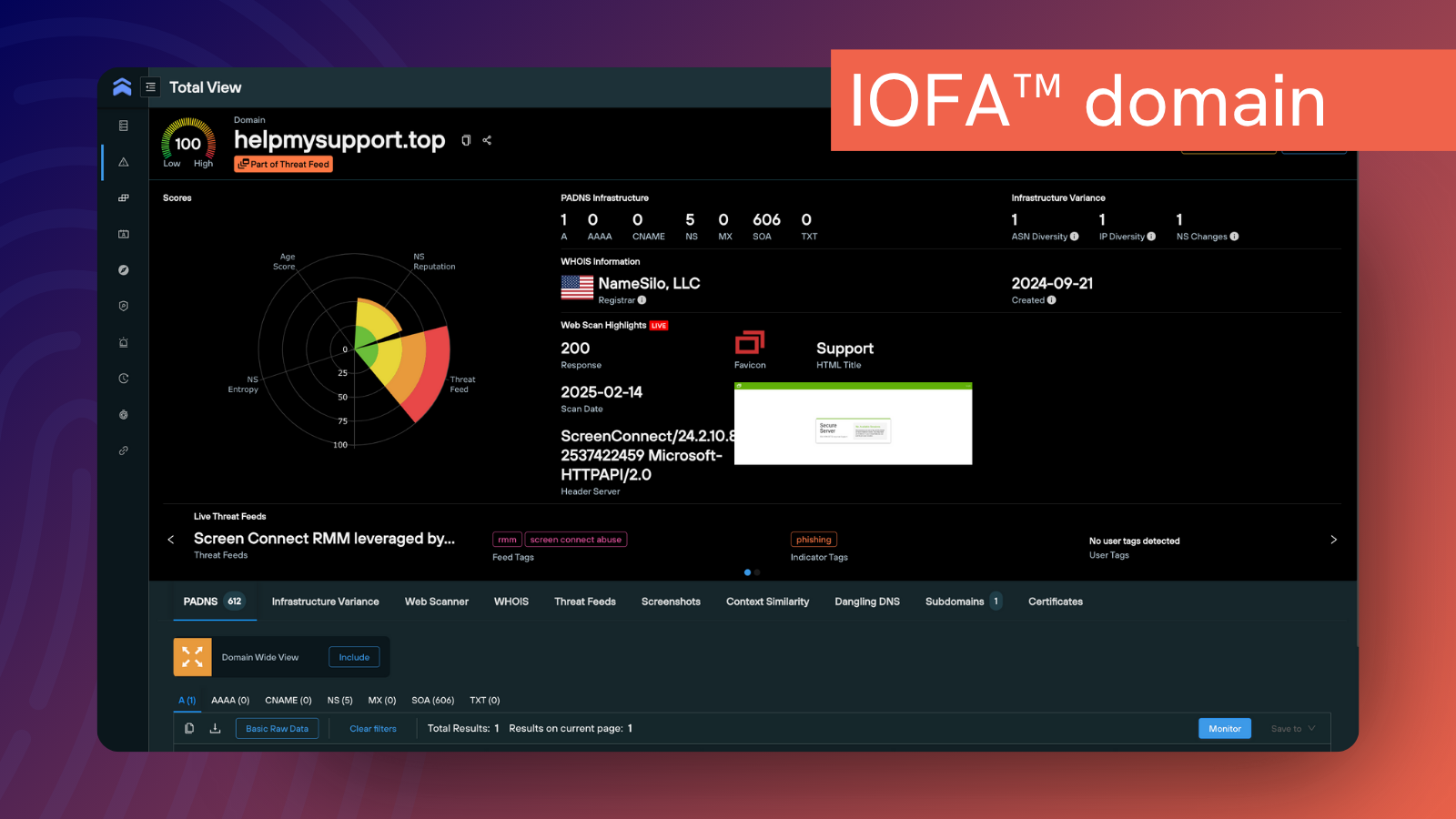
Finished IOFA™ Intelligence
Rather than feeding you yesterday’s news, Silent Push delivers forward-looking IOFA™ intelligence (including curated IOFA Feeds™) that’s designed to be immediately actionable across a range of cybersecurity workflows.
Our first party datasets reveal emerging threats weeks or even months before traditional threat feeds catch them, giving your teams the time and space they need to neutralize risks before exploitation occurs, without endless pivots and secondary investigations.
Custom Threat Hunting and Discovery
Our flexible APIs and enrichment tools allow SOC and IR teams to run custom queries against massive datasets, pivot between artifacts, and uncover hidden infrastructure links that traditional monitoring would miss.
Whether you’re tracking a specific malware family, ransomware group, or suspicious TTP, Silent Push gives you the proactive threat hunting tools to locate infrastructure smarter and act faster.
Speed and Scale
In a world where attackers move fast, you need data at machine speed. Silent Push is engineered for rapid threat discovery at scale – empowering even small security teams to perform work that once required entire threat intel units.
Get in touch and learn how you can close critical gaps in your cyber defenses
Attackers today are faster, more automated, and are increasingly leveraging modern Internet services (e.g. Ransomware-as-a-Service platforms and cloud hosting) to deploy and launch their campaigns
Relying solely on post-incident response means that you’re always playing catch-up. Organizations that invest in proactive threat hunting are not just defending themselves – they are building resilience, reducing costs, and protecting their brand reputation.
Contact us to learn how Silent Push can transform your proactive defense strategy, and help you stop attacks before they’re launched.


