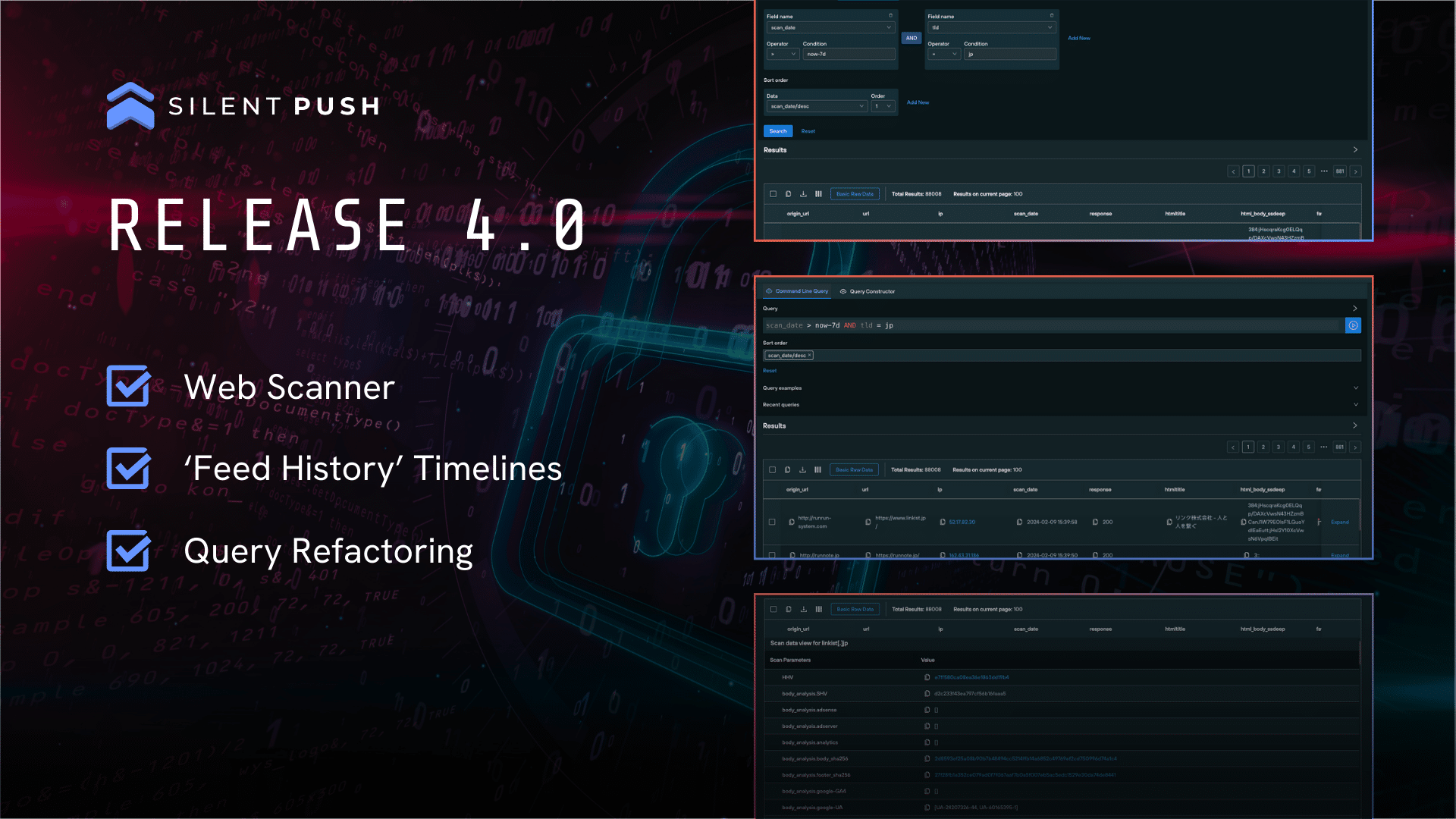
Web Scanner
Web Scanner allows Community and Enterprise users to execute command line or constructor queries that interrogate our web content database, and hunt for malicious websites impersonating their brand or attempting to circumvent certificate transparency standards.
We collect data across 90+ field names, including (but not limited to):
- Body SSDeep data
- Certificates
- HTML titles
If a domain, IP or URL is involved in a redirect chain, Web Scanner doesn’t limit results to a single scanned page, we make all the observable data available so that users can see the path taken through multiple hops, e.g. – Cloudflare holding pages, deferred login pages.
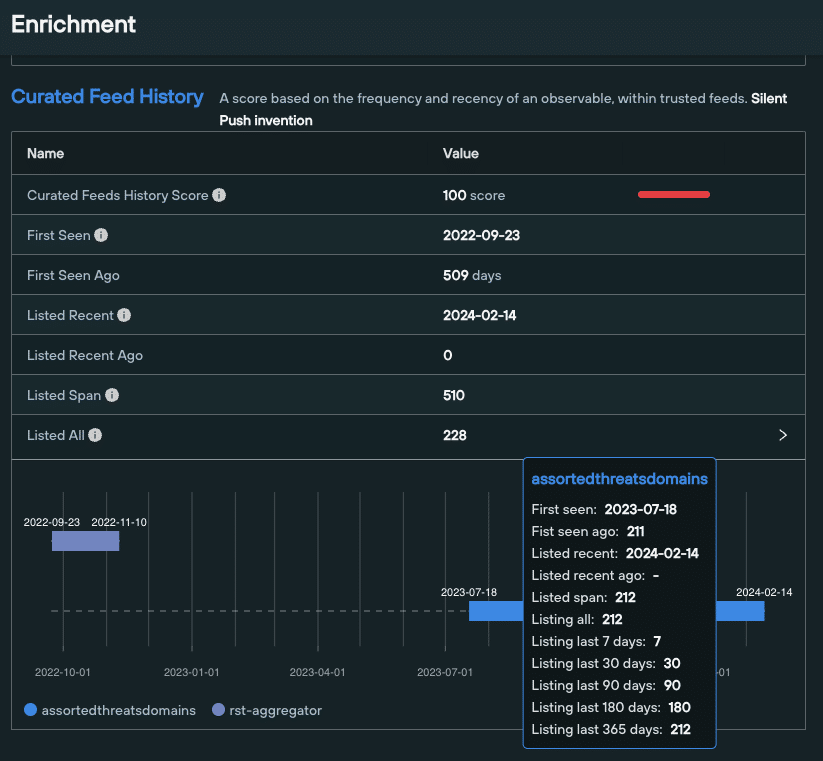
‘Feed History’ timelines
Enrichment > Curated Feeds History now displays a visual timeline of an observable’s presence within trusted threat feeds, along with a contextual menu containing further data.
This allows security teams to get an instant, top-down view of an observable’s function and risk level across a given amount of time.
Query refactoring
Results and parameters have been combined into a single page as collapsible elements, for the following queries:
- Attack Surface Mapping > Digital Footprint for Domain > Hosting Infrastructure – IPs
- Attack Surface Mapping > Potential Vulnerabilities > Discover Shadow IT
Once a set of results has been obtained, users aren’t forced to navigate off-page if to re-run a query with different parameters, saving time and improving usability.