The Silent Push Difference
Silent Push was founded to solve a core challenge in cybersecurity, too many tools rely on reactive data obtained from active incidents and past compromises.
We flip this approach with a preemptive cyber defense that models how adversaries build infrastructure before weaponization, so we can detect repeat setup patterns that indicate another attack.
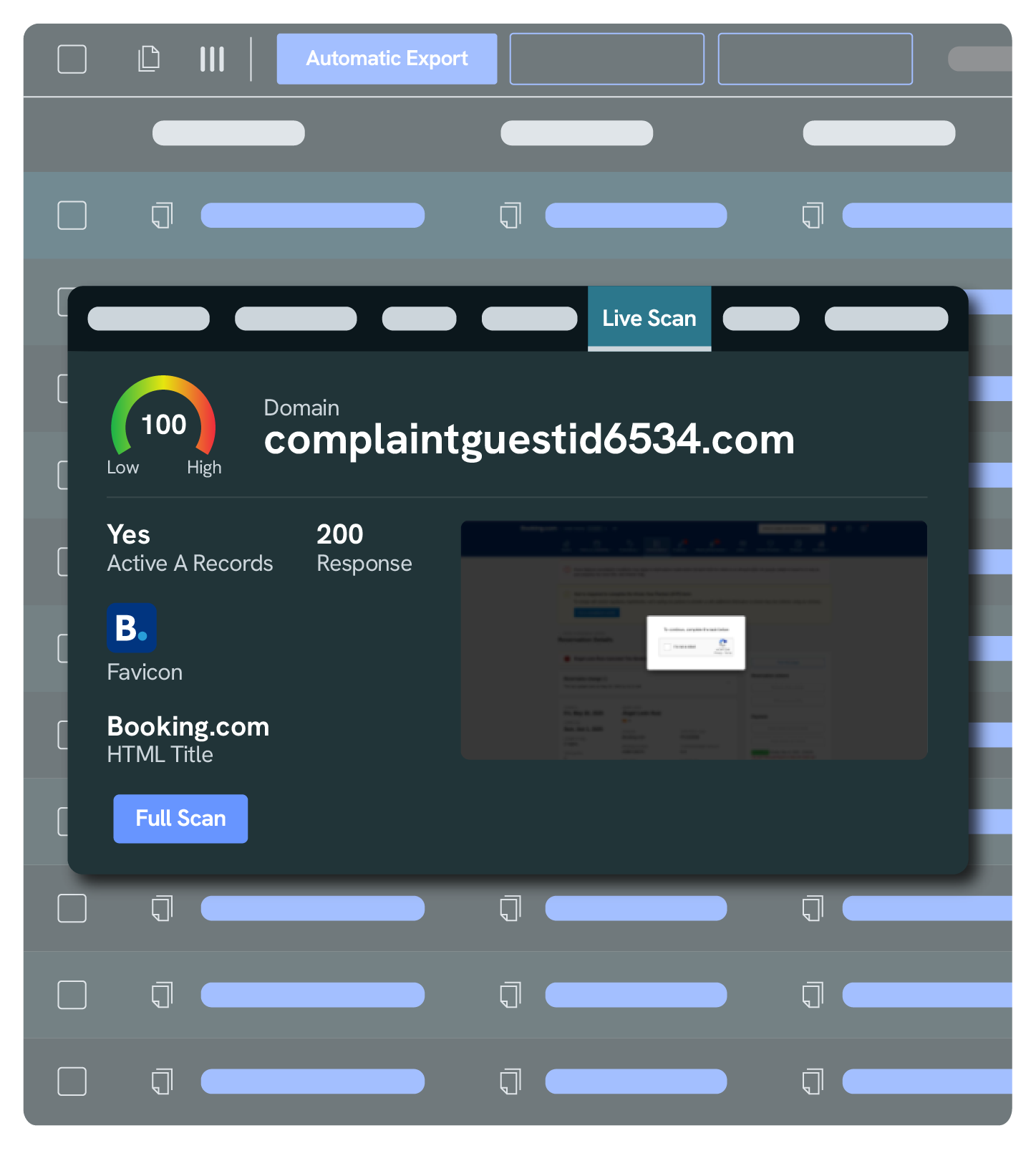
This lets us discover indicators before they are weaponized, which we provide as Indicators of Future Attack (IOFA™)