Cyber defense data is only as useful as the context that surrounds it.
Threat actors shift tactics daily and infrastructure spins up and vanishes in days or even hours. Isolated Indicators of Compromise (IOCs) aren’t enough. Security teams need connected intelligence – insight that illuminates not just a single alert, but the full shape of the infrastructure behind it.
By linking Silent Push’s unrivalled visibility of global threat infrastructure with OpenCTI’s powerful threat intelligence framework, teams can enrich their existing datasets with high-fidelity context – helping to reveal 100% of an adversary’s digital footprint, including elements that go unnoticed by traditional toolsets.
What Is OpenCTI?
OpenCTI (Open Cyber Threat Intelligence) is an open-source platform built to centralize, visualize, and correlate Cyber Threat Intelligence (CTI).
The platform supports structured intelligence sharing and collaboration using open standards such as STIX 2.1 and TAXII 2.1, and is used globally by SOCs, CERTs, and threat analysts to manage complex threat data in real time.
OpenCTI includes support for TAXII feeds, file-based imports, API integrations, and offers a flexible way for organizations to analyze threat intelligence at enterprise level.
Why Integrate Silent Push with OpenCTI?
Silent Push provides a uniquely preemptive view of attacker infrastructure, including unseen elements in the staging and early deployment phases
Instead of chasing post-breach IOCs, our platform exposes Indicators of Future Attack (IOFA)™ – early warning signals based on attacker behavioral patterns, observed across our proprietary DNS and web content database.
By integrating Silent Push with OpenCTI, organizations gain the ability to:
- Ingest Silent Push data via TAXII, ensuring it flows into OpenCTI in a structured format.
- Enrich existing indicators in OpenCTI with deeper infrastructural and behavioral context.
- Get curated threat reports via RSS feeds, including linked indicators and APT attribution.
Our bi-directional integration enables analysts to move from reactive to proactive defense, and from juggling alerts to proactive action.
STIX and TAXII: Structured, Scalable Threat Data
At the heart of the integration is support for STIX (Structured Threat Information Expression) and TAXII (Trusted Automated Exchange of Indicator Information).
Silent Push exposes TAXII endpoints that allow OpenCTI to pull in curated indicators, fully mapped to STIX 2.1 objects.
This ensures that indicators from Silent Push – domains, IPs, or URLs – arrive in a standardized format, automatically enriched with threat scoring, and metadata such as hosting details, DNS context, and campaign links.
Our integration enables correlation at scale. Indicators brought in through TAXII can be immediately cross-referenced with existing data inside OpenCTI, powering visualizations, alerts, and investigative timelines.
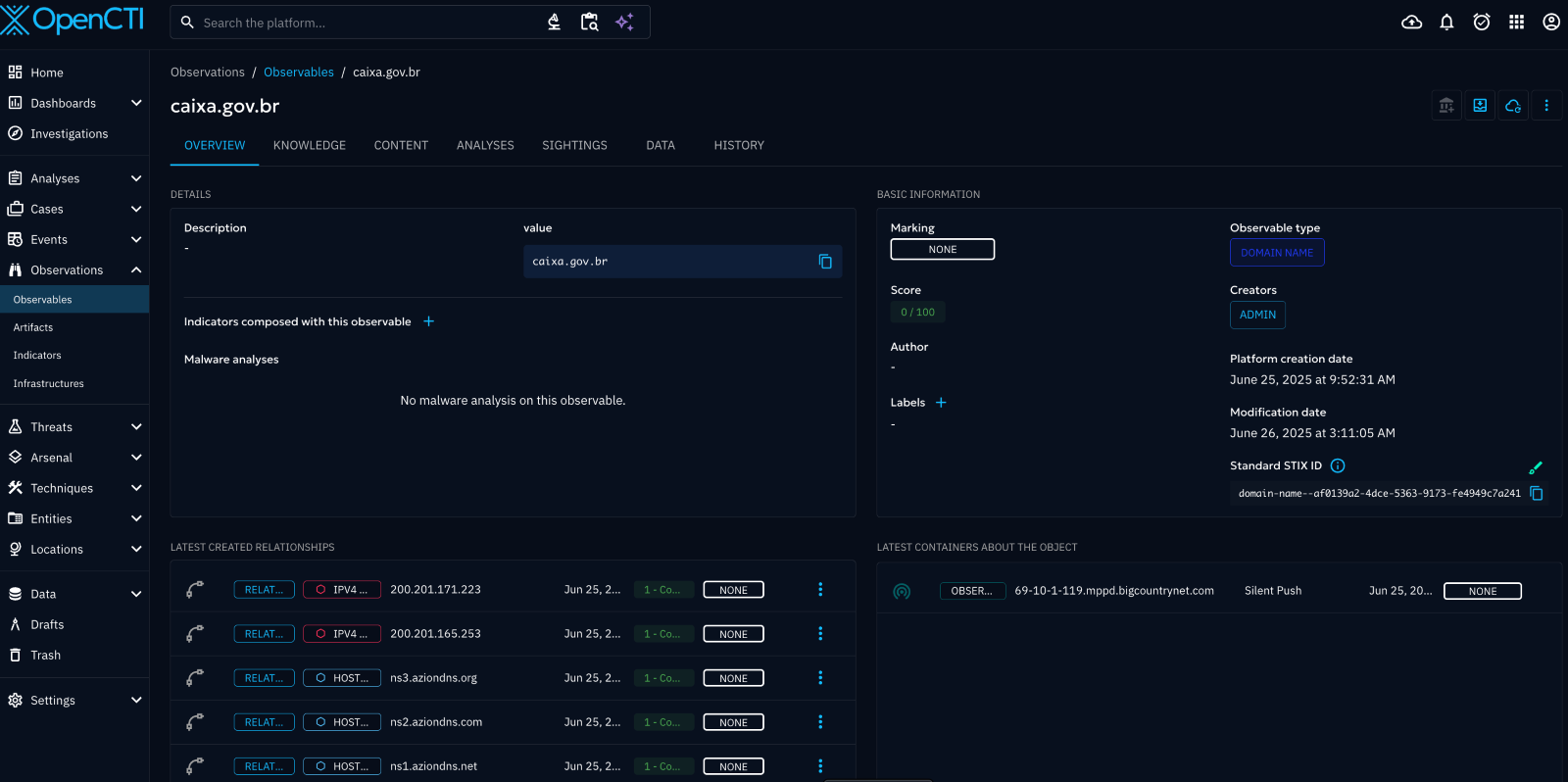
End-to-end Indicator Enrichment
The Silent Push Enrichment Connector, officially part of the OpenCTI ecosystem, is designed to deliver contextual intelligence precisely when analysts need it – during investigations.
Once deployed, the connector monitors domains, IPs and URLs already present in OpenCTI and, on a scheduled or manual basis, retrieves matching enrichment from the Silent Push API.
Enrichment is delivered in the form of STIX 2.1 bundles, integrated into OpenCTI via its internal processes. This means analysts don’t need to leave the platform or perform manual queries – context flows directly into their workflows.
Enriched categories include:
- Hosting infrastructure history
- Behavioral classification (e.g., C2, phishing, typosquat)
- Threat tags and reputation scoring from Silent Push
- Discovery of associated infrastructure and campaign patterns
The result is faster triage, better attribution, and higher confidence in decision-making.
Threat Reports via RSS: Human-Readable, Machine-Usable
In addition to structured indicators, Silent Push also supports RSS-based ingestion of threat reports, providing strategic context and narrative intelligence directly within OpenCTI.
These feeds enable organizations to:
- Automatically ingest new threat reports as they’re published
- Parse and convert data into structured STIX objects
- Link any threat entities – such as APT groups, malware, or tools – to active indicators
This allows analysts to see the bigger picture: not just what indicators exist, but why they matter, how they relate to ongoing campaigns, and what tactics they support.
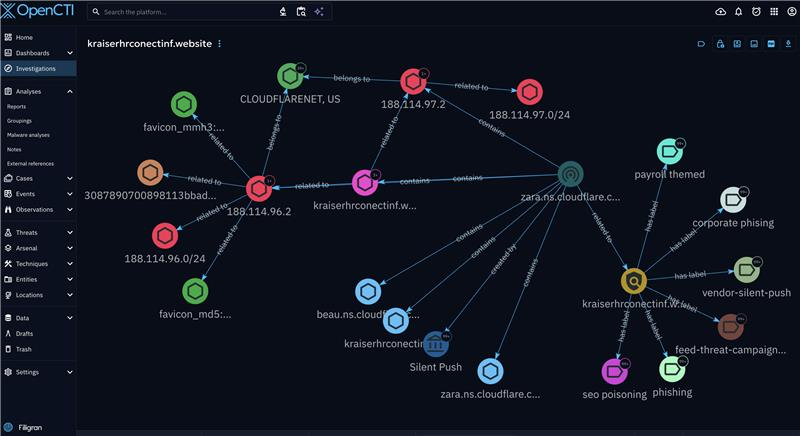
Insight Through Visualization
Once ingested, Silent Push data comes to life through OpenCTI’s powerful visualization features, allowing analysts to:
- Build dashboards tracking threats by source, type, and confidence
- Use timeline views to trace infrastructure changes over time
- Filter indicators by tags, campaign, or observable type
- Explore heatmaps and geolocation overlays, if location data is available
These views make it easier to spot trends, detect anomalies, prioritize threats, and make it easier to collaborate on threat investigations across internal security teams.
Easy Deployment, Continuous Enrichment
Deploying the Silent Push connector is straightforward, whether via Docker or manual setup. Once installed, the connector:
- Enriches observables automatically at scheduled intervals
- Can be triggered manually from within OpenCTI
- Logs activity for transparency and debugging
Ingested data is transformed into STIX 2.1, ensuring native compatibility from the get-go.
Whether you’re pulling indicators via TAXII or enriching observables in place, Silent Push fits directly into the OpenCTI data standards – no extra parsing, no manual translation.
Book An Integration Demo
Ready to transform your threat intelligence workflows? Get in touch to see how the Silent Push and OpenCTI integration brings attacker infrastructure into full view, before it becomes an incident.
We’ll show you how to enrich your existing threat data with IOFA™ insights, automate observable enrichment via STIX/TAXII, and visualize connected infrastructure inside OpenCTI.


