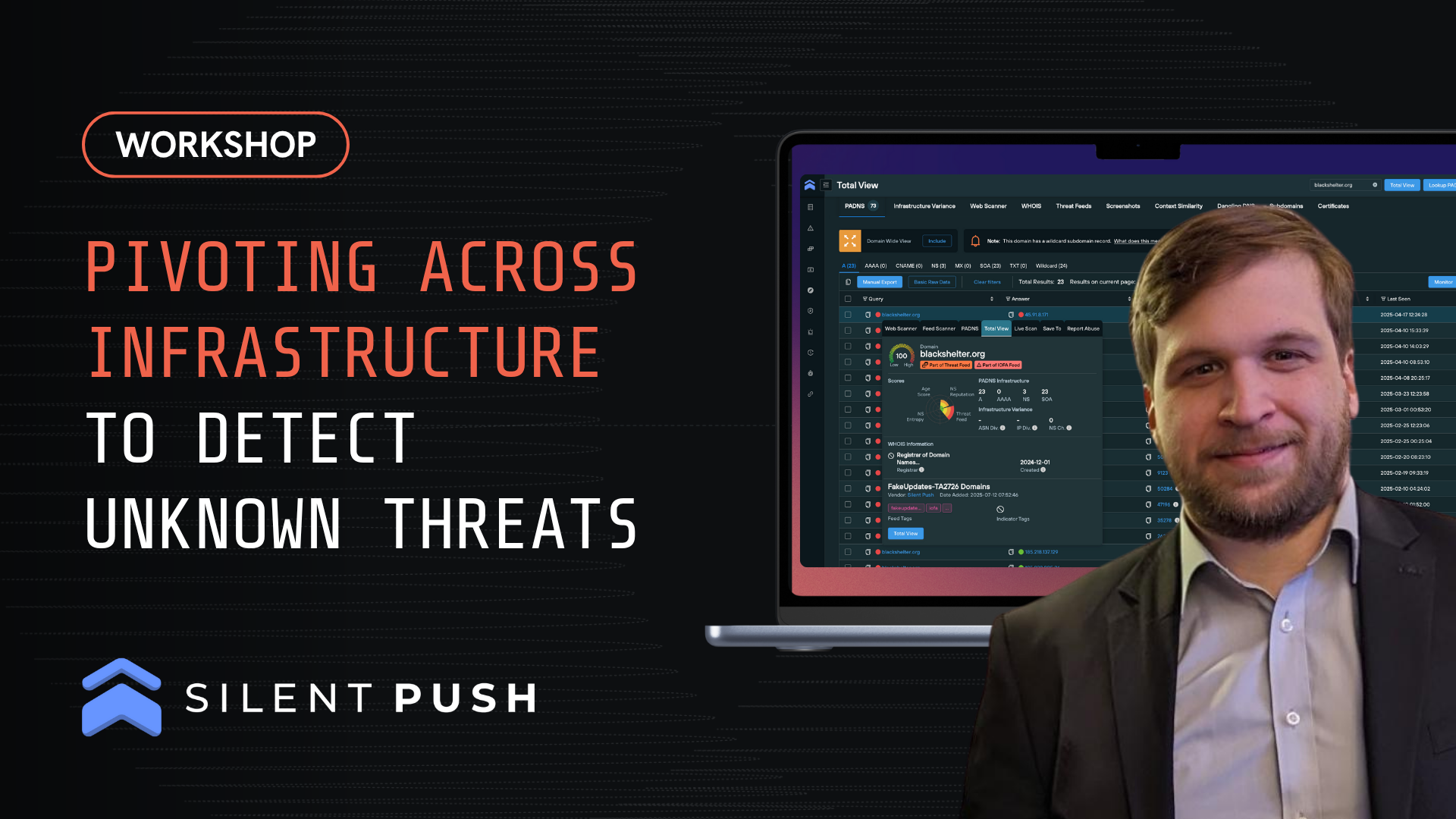
Adversary infrastructure is often hidden or inactive – evading detection by most CTI tools – until it becomes active in an attack.
This is a condensed recording of a previous interactive workshop designed for those new to threat hunting on the Silent Push platform. Full-length workshop videos are available on request at [email protected].
In this session, attendees learned how to uncover the 98% of malicious infrastructure that typically goes undetected. We demonstrated how pivoting – linking data points like domains, IPs, and certificates – can reveal an attacker’s hidden network. Real-time examples showcased the power of pivots within the Silent Push free Community Edition, empowering participants to spot threats before they strike.