Key Findings
- Silent Push Threat Analysts are tracking a scam campaign we’ve labeled “Power Parasites” that has been operating through a combination of deceptive websites, social media groups, and Telegram channels, primarily targeting individuals across Asian countries, including Bangladesh, Nepal, and India, with job and investment scams.
- Based on details shared with our research team, our analysts have investigated a series of domains used in 2024 to develop technical methods to track this group’s infrastructure into 2025 and as it evolves.
- Power Parasites have targeted numerous global energy brands, including Siemens Energy, Schneider Electric, EDF Energy, Repsol S.A., Suncor Energy, and a variety of other major brands.
Executive Summary
In 2024, Siemens Energy began publicly warning of a wave of fraudulent pyramid investment and job scams that exploited its name and branding. Operating through a combination of deceptive websites, social media groups, and Telegram channels, these schemes have primarily targeted individuals across Asian countries, including Bangladesh, Nepal, and India.
Silent Push began investigating a series of domains used in 2024 to map the current infrastructure of this ongoing malicious campaign, which we are dubbing “Power Parasites.”
Repsol Energy and Suncor Energy have also been targeted, and both have issued warnings to customers, as well as potential job seekers, about fraudulent hiring and investment scams impersonating their brands.
It is important to note this campaign remains active, targeting prominent brands such as Siemens Energy, AMD Electronics, Schneider Electric, EDF Energy, Repsol S.A., Suncor Energy, Starlink, Ducati Motorcycle, Netflix, ABB Robotics, Air France, Bitfinex, Royal Vending, and Hess Corporation.
Upon further investigation of this campaign, our team has confirmed the methods used herein remain a popular method of attack, with more than one threat actor likely involved in targeting at least one of the energy companies listed here, Repsol, which we will cover later in this post.
Sign Up for a Free Silent Push Community Edition Account
Register now for our free Community Edition to take advantage of all the tools and queries highlighted in this blog.
Table of Contents
- Key Findings
- Executive Summary
- Sign Up for a Free Silent Push Community Edition Account
- Background
- Research Methodology
- Power Parasites Promoted on YouTube
- Initial Pivots into Power Parasites’ 2024 Infrastructure
- Over 150 Domains Active in 2024, Energy Orgs and Other Global Brands Targeted
- HTML Title Pivots led to campaign variations, new targets
- Financial Conduct Authority Report into Repsol Investment Campaign Pivots into Larger Network of Investment-Related Phishing
- Continuing to Track Power Parasites and Other Investment/Job Scam Campaigns
- Power Parasites Mitigation
- Register for Community Edition
- Sample Power Parasites’ IOFA TM List
Background
Siemens publicly put out details about the scamming campaign on September 30, 2024, on Facebook, writing, “We took notice of the recent fraudulent activities being conducted on various online platforms, including Telegram, Facebook, and Instagram, falsely using the name of Siemens Energy and its employees to promote investments. Please note: Siemens Energy does not operate any investment platforms. We strongly advise the public to refrain from investing or depositing money on any social media or offline platforms claiming to be associated with Siemens Energy. Siemens Energy and our employees are not involved in these fraudulent activities. We will not be held liable for any financial losses resulting from these fraudulent activities.”
Siemens also put out details on a “fake job applicant” scam that was abusing their brand, writing, “For all job applicants looking to join us, please note Siemens Energy does not ask for fees prior/during/after the application process. We do not ask for banking details or personal financial information in return for the assurance of employment. Always apply through our Jobs and Careers site or a site which links back to our Jobs and Careers site. These are the only authorized job boards used by Siemens Energy to post open jobs.”
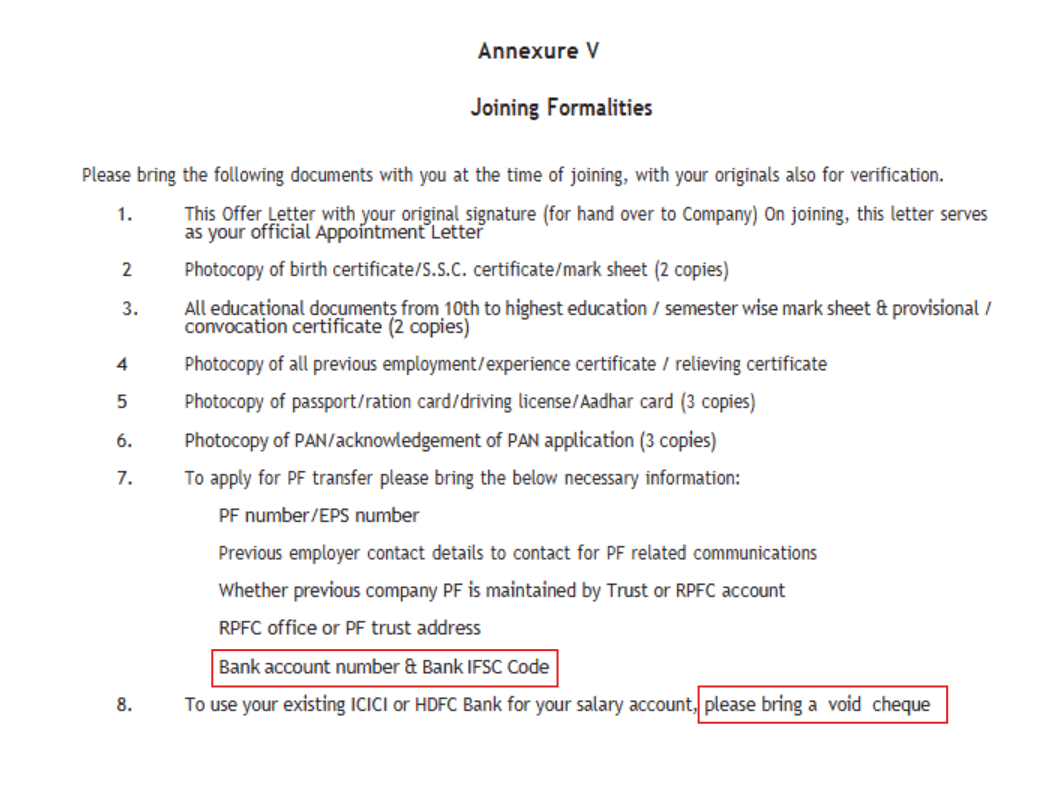
While we cannot share all of the information we received in relation to this campaign, we can share the final page of one of the “employment agreements” used by Power Parasites (see below).
Notice how, in the “Joining Formalities” section, the threat actor requests that the applicant for a supposed job provide a “Bank account number & Bank IFSC Code” along with passport, birth certificate, and a “void cheque.”
Additional Energy Companies Targeted
Repsol S.A.
Two additional companies that Power Parasites targeted were the energy companies Repsol S.A. and Suncor Energy. Of those, Repsol Energy has published a Fraud Alert page on its website warning of hiring and investment scams that abuse its name. According to the alert, “Repsol does not have any platform for making investments or digitally paying users. Messages have been detected which, through the use of artificial intelligence, impersonate the identity of our executive team, offering investment platforms that are fraudulent. Initiatives that involve filling out an online form or transferring personal data may be fraudulent practices, especially if we find them on unofficial pages and social media.”
Repsol continued, referencing the job scam, “Repsol never requires payment to be involved in a Company recruitment process, nor does it communicate changes to bank accounts via email. Also, it is not common practice to request personal information from our suppliers or customers by email or telephone.”
Suncor Energy
Suncor Energy posted on LinkedIn about recruitment fraud targeting its brand several years ago: “Have you received an email that looks like a Suncor job offer but something just seems ‘off’? It offered tips on how to avoid a potential job scam and has a page on its website warning people about the job recruitment scams, writing, “We are aware some applicants have received false employment offers from individuals or organizations posing as Suncor. Please be aware that we will never request money from job seekers, nor request personal information beyond what is required for a resume.”
Additionally, in October 2024, the U.K. Financial Conduct Authority also warned about an investment scam using the Repsol brand under a fake “Repsol Gain” name (via the domain repsolgain[.]com), which is connected to a much larger pool of websites facilitating investment scams.
Many of the domains used in this campaign feature login pages with an “Invite code” field, a classic technique for investment scams:
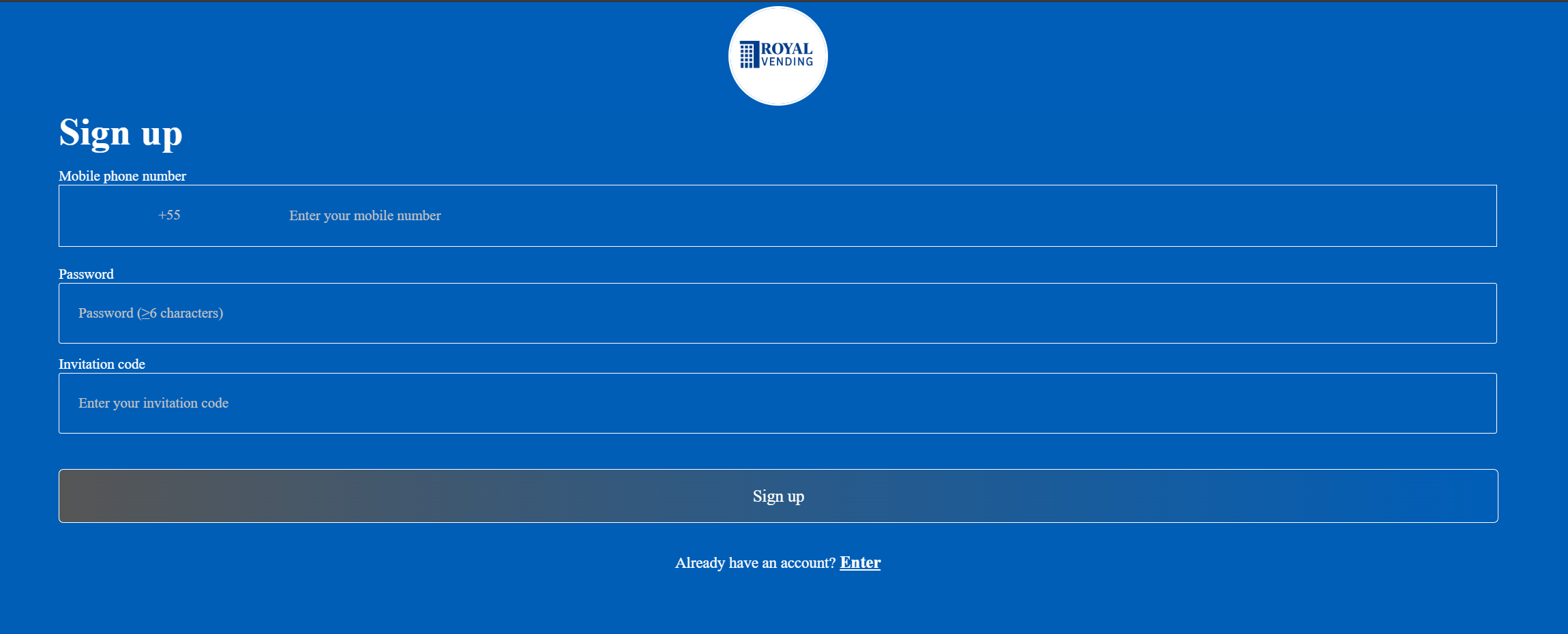
The “Invitation code” field here is used to make it more difficult for defenders to investigate one of these websites without being directly contacted by website operators.
While these domains appeared to be phishing pages, they were actually portals to low-quality investments or job experiences—essentially, additional financial phishing content gated behind a login.
Silent Push Threat Analysts were previously able to gain access to some of these gated experiences for other complex investment scams, often referred to as “pig-butchering campaigns.”*
*Note: Our team is moving past use of the term “pig butchering,” often used by threat actors when referring to their victims, whenever possible. However, the term remains popular and may appear in some of our reports and blogs when such context is needed.
Research Methodology
Investment and job scams, such as the Power Parasites campaign here, rely on aggressive outreach to victims. As a result, these campaigns are typically shared with potential victims on social media networks, over email, or via direct messaging channels.
The research behind this campaign began with some initial leads, from which our team quickly pivoted to new hosts via shared technical characteristics and the public promotion used across these scam websites.
When tracking any malicious job or investment campaign, it is always important to understand that these campaigns often employ a “spray and pray” approach, where threat actors prefer to use numerous websites and typically abuse multiple brand names simultaneously. We approach this type of research with an “and then some” mentality—where every new lead could result in finding dozens of new hosts—and we keep working to find those pivots until the proverbial “threat well” runs dry.
Power Parasites Promoted on YouTube
Some of this campaign’s scams have been promoted on YouTube. Two videos featuring lures to these sites are featured below:
- The first YouTube video, uploaded September 25, 2024, is “https://www.se-renewables[.]info/?ref=53R1yx”
- A second YouTube video, also uploaded September 25, 2024, is “নতুন সাইট থেকে ফ্রিতে টাকা ইনকাম | https://www.se-renewables[.]info/?ref=48Nxbj”*
*Note: A rough title translation from Bangla, which is spoken mostly in Bangladesh and India, would be: “Earn free money from new sites.”
Initial Pivots into Power Parasites’ 2024 Infrastructure
Two domains from the campaign were pointing to a series of Telegram channels, notably with “siemensenergy” in their names. All of the channels have since been banned or deleted. The initial domains were:
- sem-energy[.]net
- se-renewables[.]info
From these two domains, our team created a technical fingerprint that enabled us to pivot into more of the threat actor’s infrastructure.
The initial domains’ structure also showed a wide range of domain suffixes, mainly utilizing two keywords: “SE,” which stands for “Siemens Energy,” and “AMD,” which stands for “Advanced Micro Devices,” a U.S. tech company.
These domains also consistently used other keywords, including: “biz,” “business,” “hub,” “renewables,” and “top.” A small portion of which can be seen here:
- se-biz[.]bid
- sehub[.]top
- se-hubs[.]xyz
- sehub[.]info
- se-biz[.]cfd
- se-biz[.]mom
- se-renewables[.]info
- se-renewables[.]top
- amdtop[.]vip
- amd-biz[.]mom
- amdbizs[.]top
- amdbusiness[.]me
- amd-biz[.]vip
- amdtop[.]info
After reviewing some of the domains and identifying additional shared characteristics, our analysts were able to pinpoint additional infrastructure fingerprints, allowing our team to better understand the scope of this particular campaign.
Note: As a reminder, Silent Push TLP: Amber reports provide details on our research exclusively for our Enterprise customers. For reasons of operational security and to prevent threat actors from learning about how we track their mistakes, we are unable to reveal the details of these pivots in a public-facing blog.
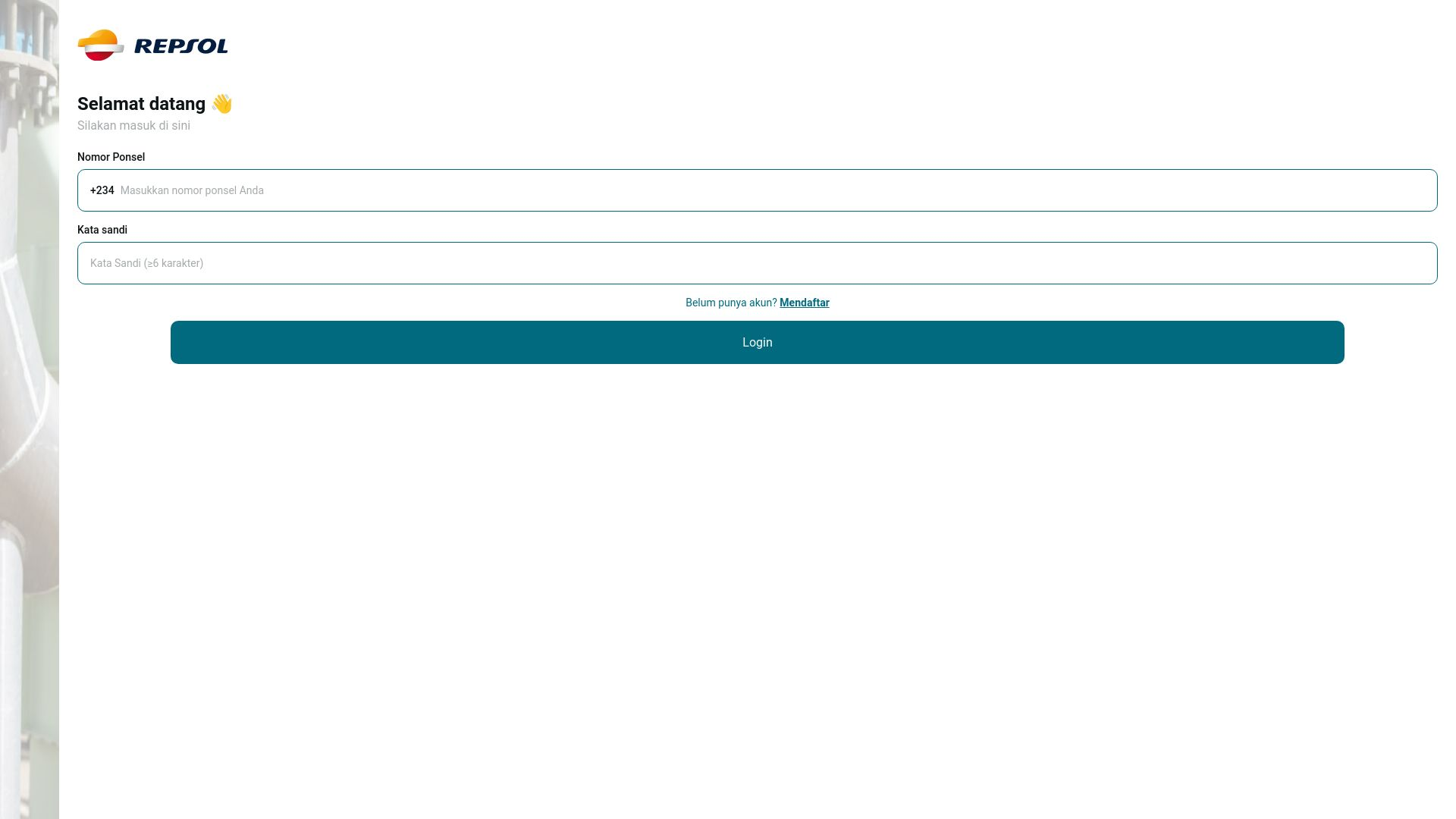
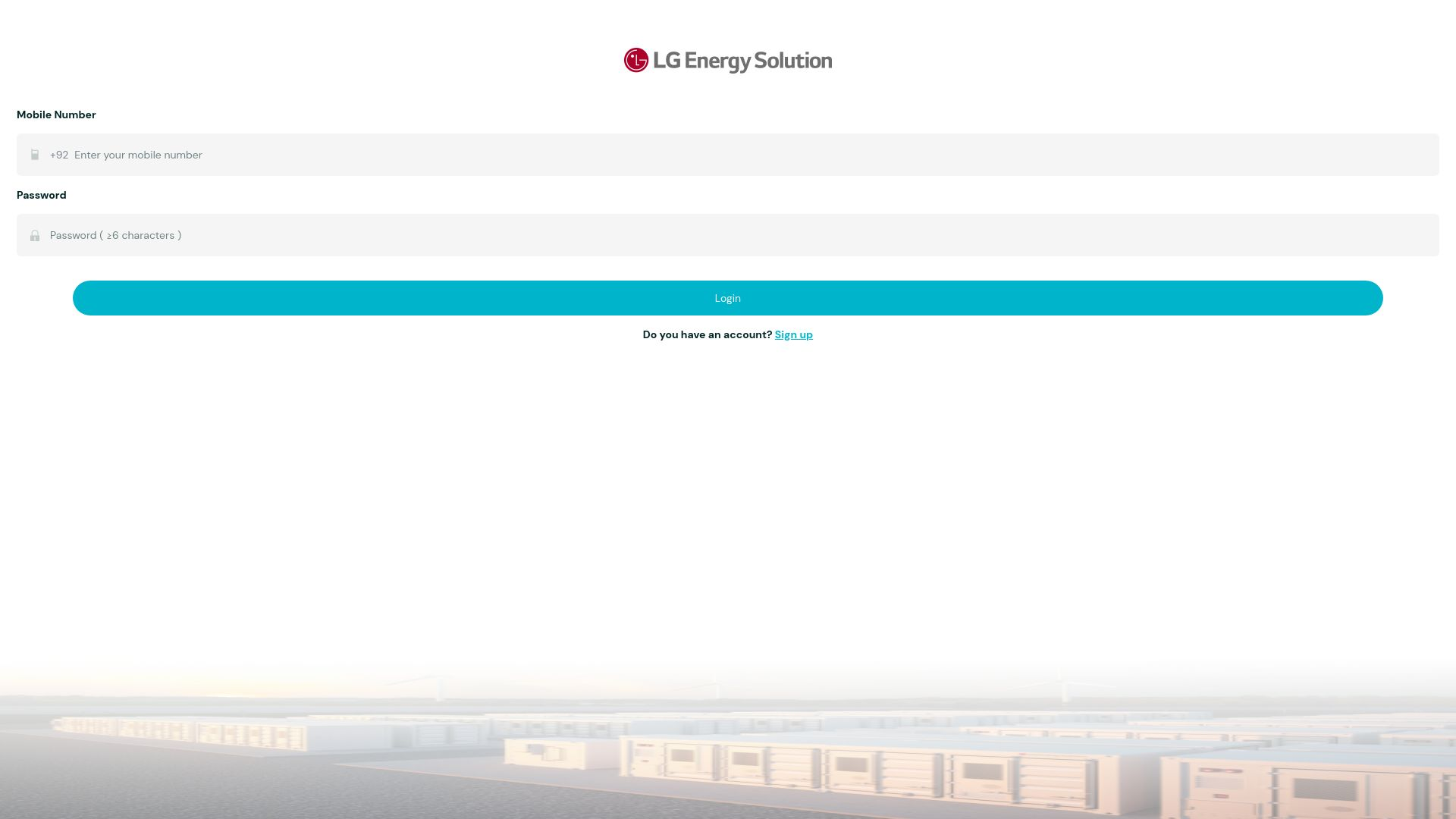
Over 150 Domains Active in 2024, Energy Orgs and Other Global Brands Targeted
During the research, our team found several energy organizations and other major brands that Power Parasites have been targeting. These brands have been included below, alongside a pair of screenshots to show what these sites look like in operation:
- Energy Brands
- EDF Energy
- “Repsol S.A.” Energy
- LG Energy
- Suncor Energy
- Other Major Brands
- Starlink
- Netflix
- Ducati Motorcycle
- ABB Robotics
- Air France
- Bitfinex
- Hess Corp.
HTML Title Pivots led to campaign variations, new targets
By pivoting across the infrastructure seen previously, Silent Push Threat Analysts were able to find a series of HTML titles that were being reused across this campaign, including: “Document,” “Login,” “Documento,” “Dokumen,” “acceso,” “Gabung,” “Log In,” “تسجيل الدخول,” “দলিল,” “وثيقة,” “লগইন করুন,” and “প্রবেশ করুন.”
The languages used on the sites included English, Portuguese or Spanish, Indonesian, Arabic, and Bangla.
Further pivots returned domains like onrobotline[.]biz/login/login.html, which was spoofing the real “OnRobot” brand with a login form that looked similar to the original energy phishing pages:
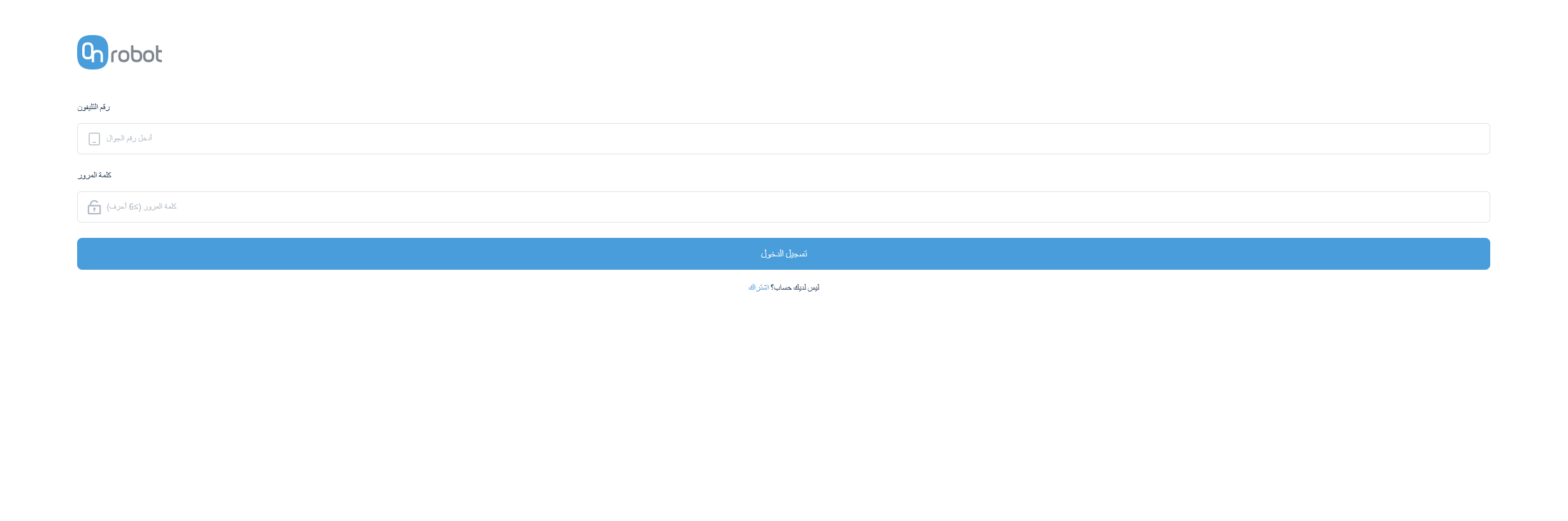
On further analysis, it was clear that a shared template was being used across the sites.
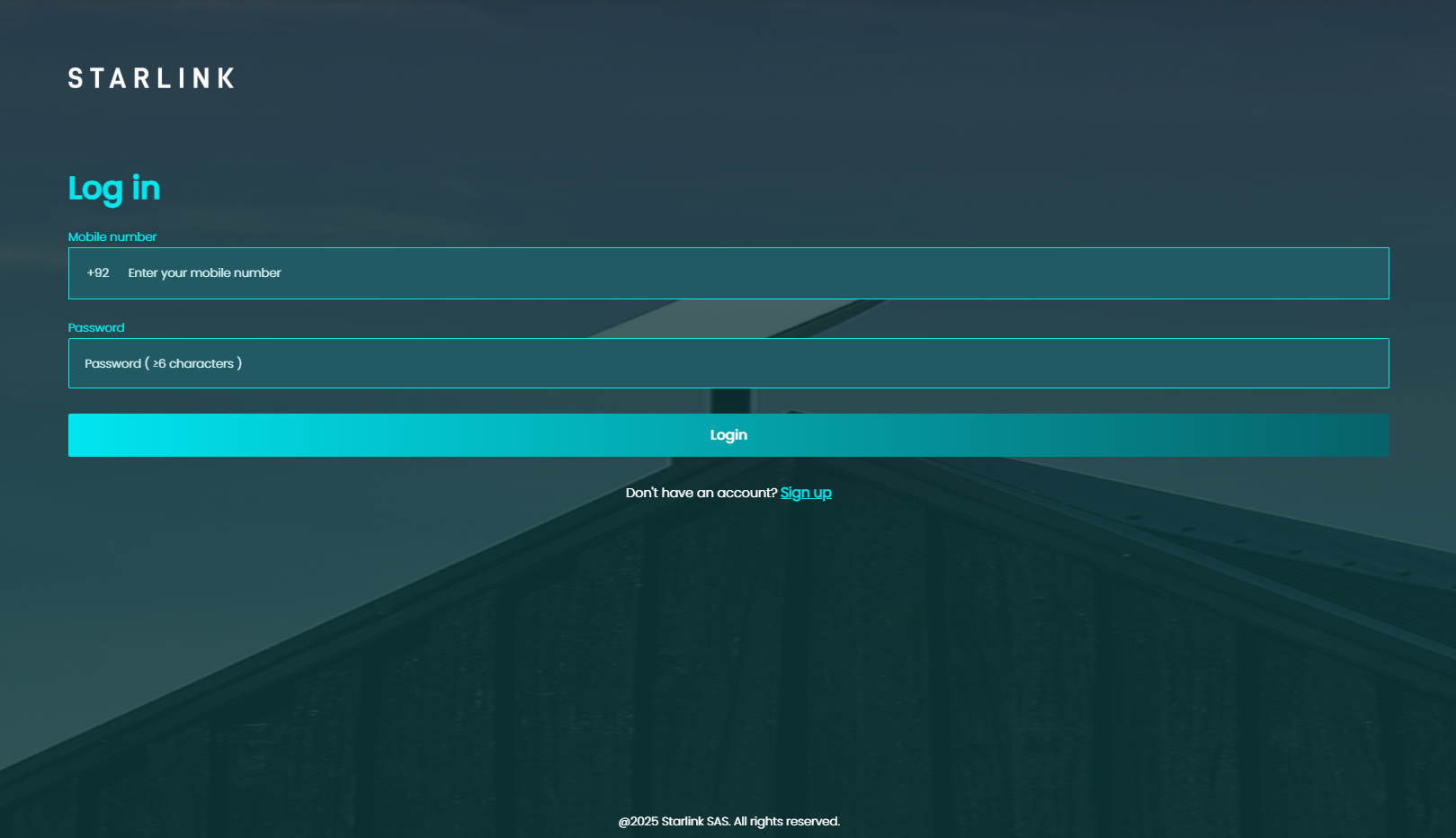
One of the most recent results from our expanded research even included a domain targeting Starlink.
Financial Conduct Authority Report into Repsol Investment Campaign Pivots into Larger Network of Investment-Related Phishing
Throughout this campaign, the energy company Repsol has been targeted with numerous domains. While conducting open-source intelligence (OSINT) research on this threat, our team discovered an alert issued by the U.K. Financial Conduct Authority, an independent financial regulatory body.
The authority’s report, entitled “REPSOL GAIN,” provided details that “This firm may be providing or promoting financial services or products without our permission. You should avoid dealing with this firm and beware of scams.”
The alert provided one domain used by the scammers:
- repsolgain[.]com
Further investigation revealed that the domain had been live for some time, and numerous captures were available in both the Wayback Machine and across Silent Push data.
Visually, the site appeared significantly different from the other templates we have been tracking as Power Parasites, although it did resemble several other investment scam sites.
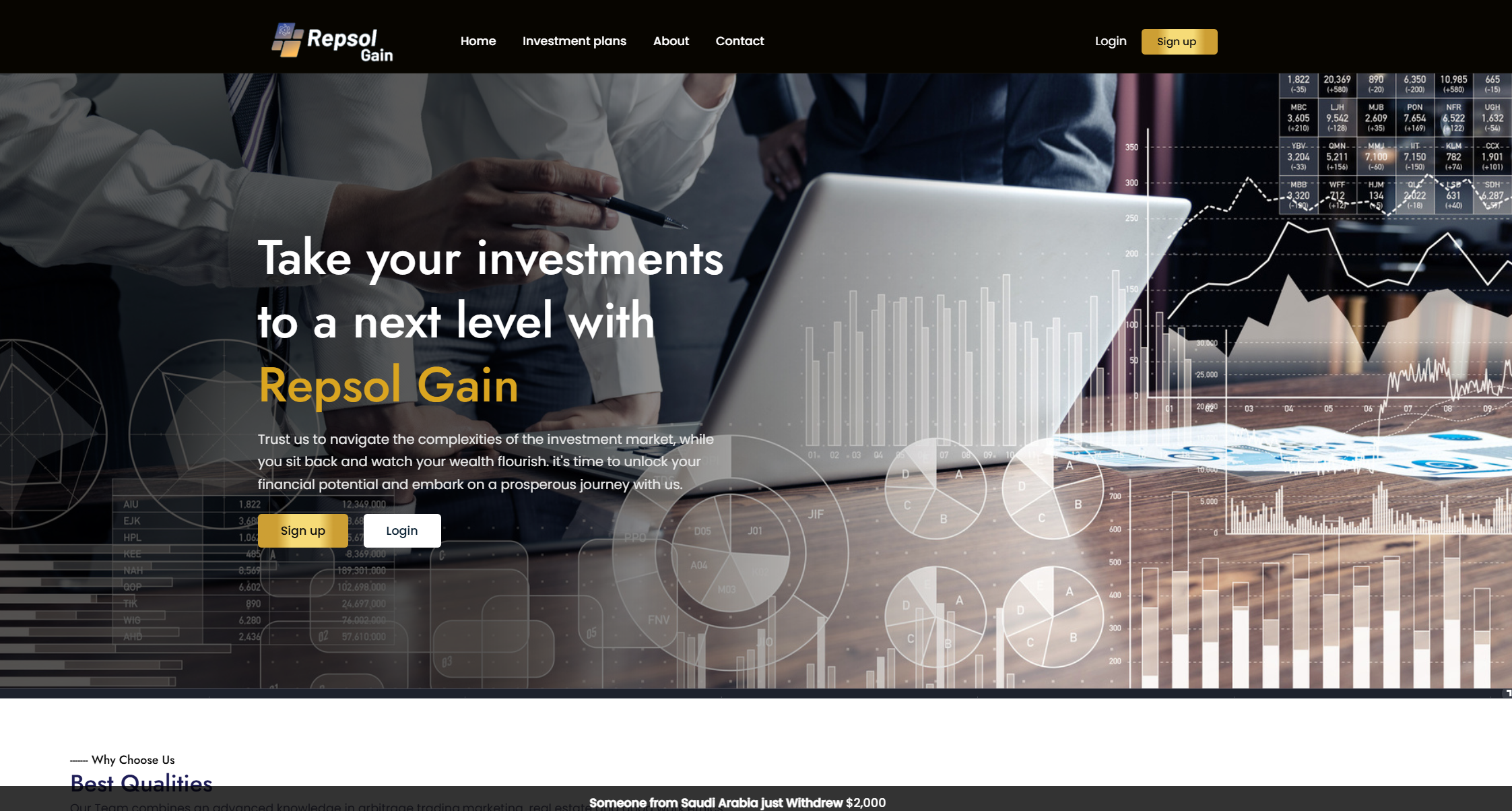
Based on the above, the Silent Push team believes the threat actor behind the “Repsol Gain” campaign is likely to be different from the Power Parasites group discussed in this report.
Subsequently, our threat analysts identified additional fingerprints on the “Repsol Gain” website, enabling them to pivot into other infrastructure used by the threat actor to launch investment scams under the Repsol brand name.
Continuing to Track Power Parasites and Other Investment/Job Scam Campaigns
Silent Push Threat Analysts will continue to track Power Parasites alongside other investment and job scam campaigns. This threat actor group primarily targets consumers, impacting some brands, their associated organizations, and customers.
Power Parasites Mitigation
Silent Push believes all domains associated with the Power Parasites’ campaign represent some level of risk. While the campaign is primarily a consumer-focused phishing threat, it is likely that more than one group of threat actors is involved, and the attack surface will expand into new target areas.
Our analysts have developed a series of Silent Push Indicators Of Future AttackTM (IOFATM) Feeds for these types of phishing efforts.
Silent Push IOFATM Feeds are available as part of an Enterprise subscription. As a result, enterprise users can ingest IOFATM Feed data into their security stack to inform their detection protocols or use it to pivot across attacker infrastructure using the Silent Push Console and Feed Analytics screen.
Register for Community Edition
Silent Push Community Edition is a free threat-hunting and cyber defense platform featuring a range of advanced offensive and defensive lookups, web content queries, and enriched data types, including Silent Push Web Scanner and Live Scan.
Click here to sign up for a free account.
Sample Power Parasites’ IOFATM List
- amdtop[.]vip
- amd-biz[.]mom
- amdbizs[.]top
- amdbusiness[.]me
- amd-biz[.]vip
- amdtop[.]info
- onrobotline[.]biz
- repsol-biz[.]fit
- repsolhub[.]buzz
- se-biz[.]bid
- sehub[.]top
- se-hubs[.]xyz
- sehub[.]info
- se-biz[.]cfd
- se-biz[.]mom
- se-renewables[.]info
- se-renewables[.]top


