Fake links and compromised messenger accounts: Investigating a recent Facebook phishing campaign

Phishing campaigns are a dime a dozen, but that doesn’t make them any less dangerous for the individuals and organizations affected by them.
Our Threat Intelligence Team recently discovered a campaign targeting social media users on Facebook Messenger, so we decided to take a closer look at the threat actor’s tactics, and the infrastructure used.
Enterprise risk
Whilst phishing attacks are often considered a consumer threat, many campaigns specifically target organizations and their supply chains.
Enterprises especially overlook vulnerabilities native to mobile and social media, either because they occur in employees’ personal networks or because they aren’t overtly linked to an organization’s overall security.
Large-scale threats caused by phishing attacks include:
- compromised accounts used as an entry point to target employees further along the org chart and supply chain;
- hijacked social profiles used to create reputation damage or leak sensitive information;
- employee data opening the door for further attacks such as invoice fraud or malware propagation.
Attack Vectors
Fraudulent DMs
In the campaign we discovered, threat actors send phishing links to the contacts of previously compromised Facebook accounts.
These DMs include a short message referring to what appears to be a linked video. Whilst the domains contained within these links use differently themed typosquatting attack vectors (based on the phrase “tiktok”, for example), the content they preview is made to look like a Facebook post:
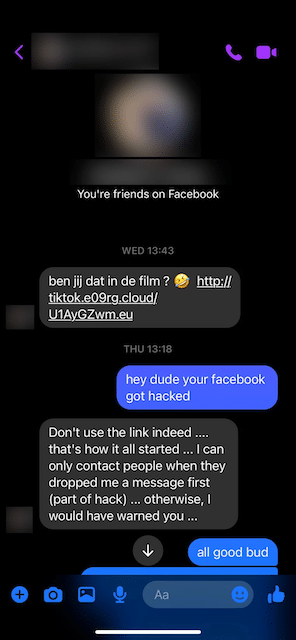
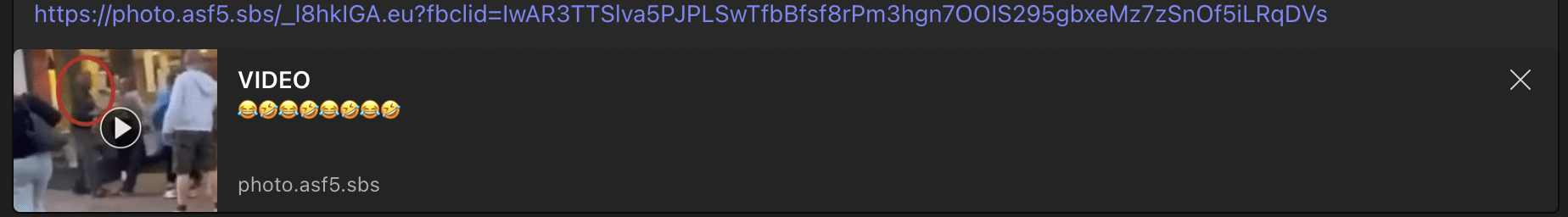
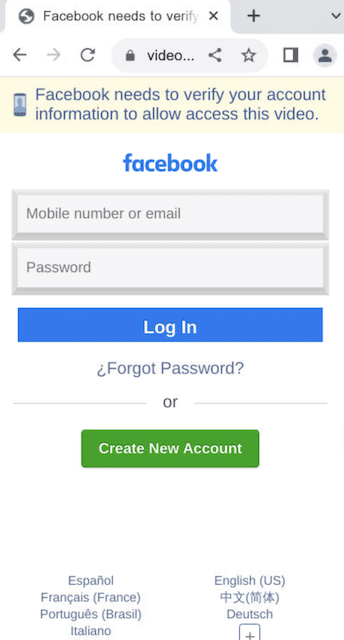
Clicking the phishing link sends users to a fake Facebook login page, seemingly to access the video in question.
When users enter their credentials, the data is forwarded to the threat actors, who access the user’s account for malicious purposes and to propagate the campaign via the victim’s Facebook contacts:
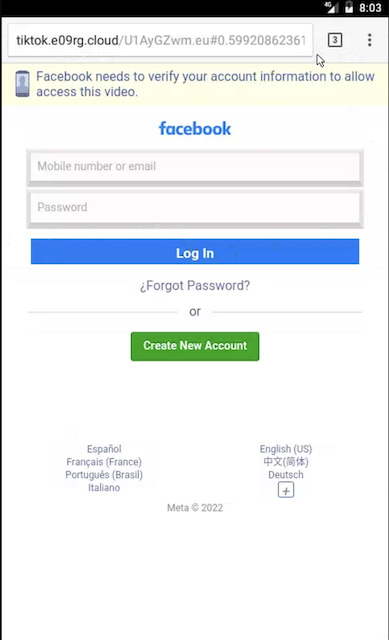
Those falling for the scam are left in the dark and are either shown an infinite loading screen, or a notification saying that a wrong password was entered.
Exploring the Domain Infrastructure
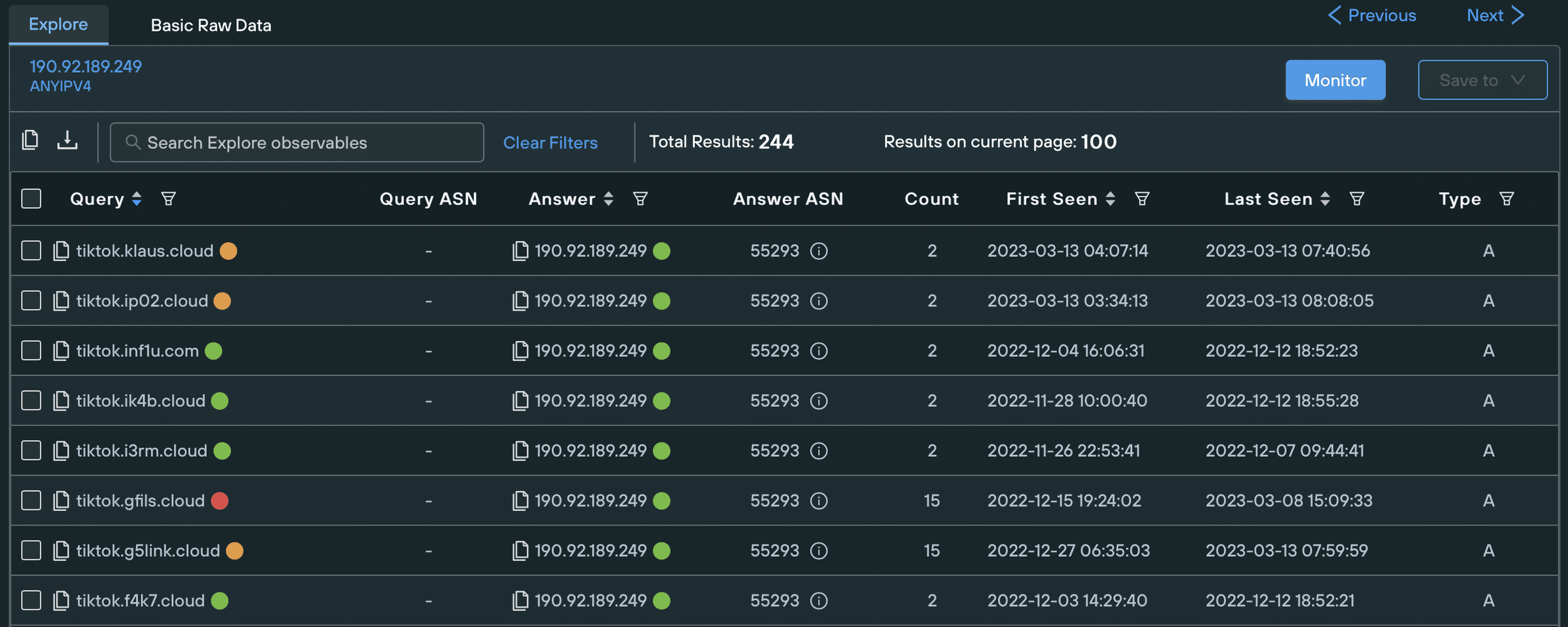
Investigating the campaign revealed that the initial IoC domain tiktok.e09rg[.]cloud was registered in Porkbun late last year and hosted on 69.57.163[.]217, an IP address on Namecheap (22612) ASN with multiple domains associated with the campaign pointing at it:
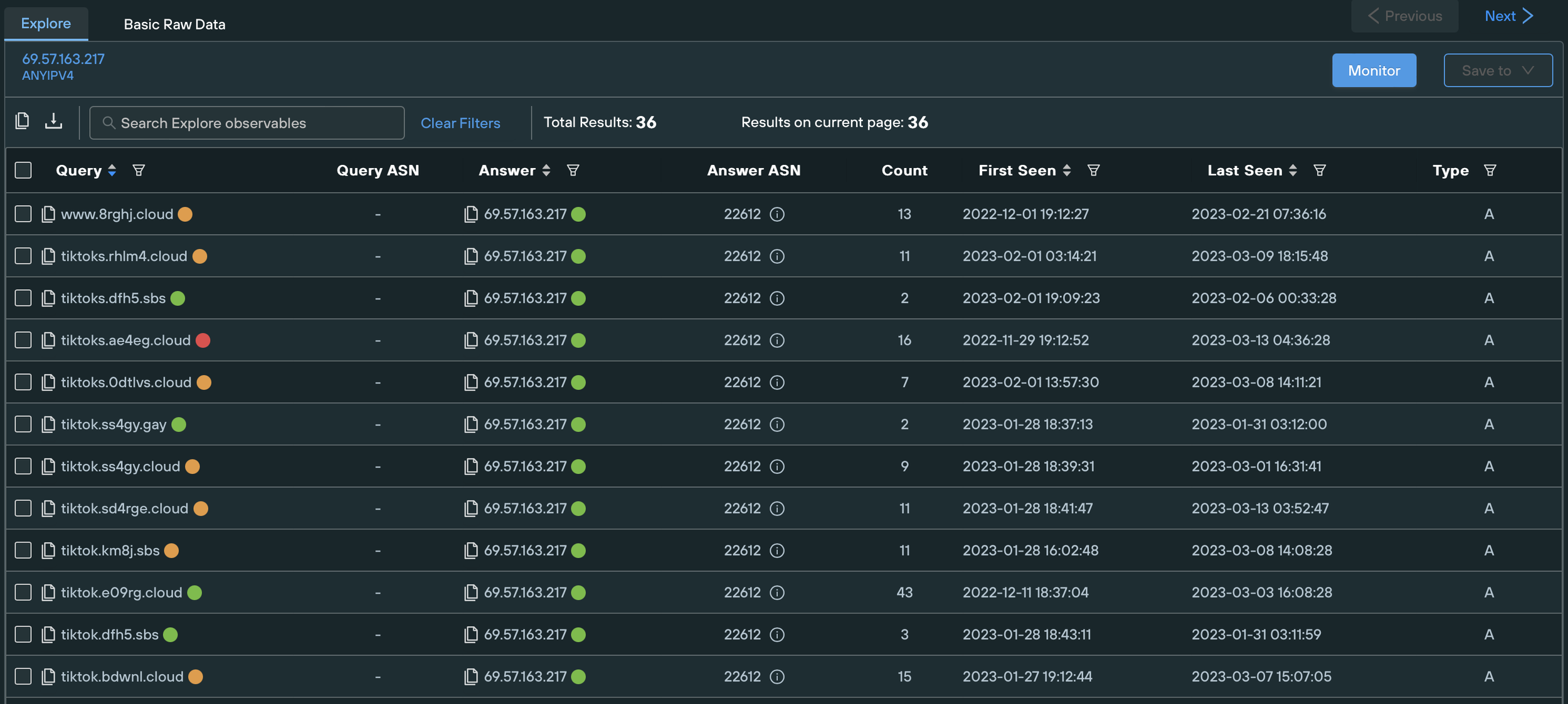
By tracking similar threat activity in different autonomous systems and using content similarity techniques, we were able to track additional phishing domains deployed by the threat actors. The domains in question, as well as all other relevant IOCs, are listed at the end of the article.
We found that the domains associated with the campaign all contain the words “tiktok”, “video”, or “photo”, and searched for infrastructure displaying the same naming conventions. This uncovered other malicious IPs such as:
These domains all point toward the same fake login page when accessed on mobile:
Platform-specific threat
The campaign’s initial infrastructure suggested that it was designed to harvest mobile users’ Facebook credentials. Desktop users and users in certain locations are instead redirected away from the fake login pages.
Fake bicycle brand
We found most domains pointing to the landing page of a non-existent bicycle brand when accessed on desktop. The page has no functionality and only displays partial and repetitive information about the mock-up brand. It didn’t take much work for us to discover that the page is a free template taken from Dribble.
Though this decoy page doesn’t create any damage on its own, it helps to hide the scam from automated threat scanners and users within the wrong target audience, increasing the lifespan of the phish before it is noticed at scale, and reported.
Ad-ware extensions
The phishing domains are geo-blocked and redirect users away from the fake login pages depending on their location.
Users accessing the phishing links from Singapore, for example, are sent to buzzonclick[.]com.
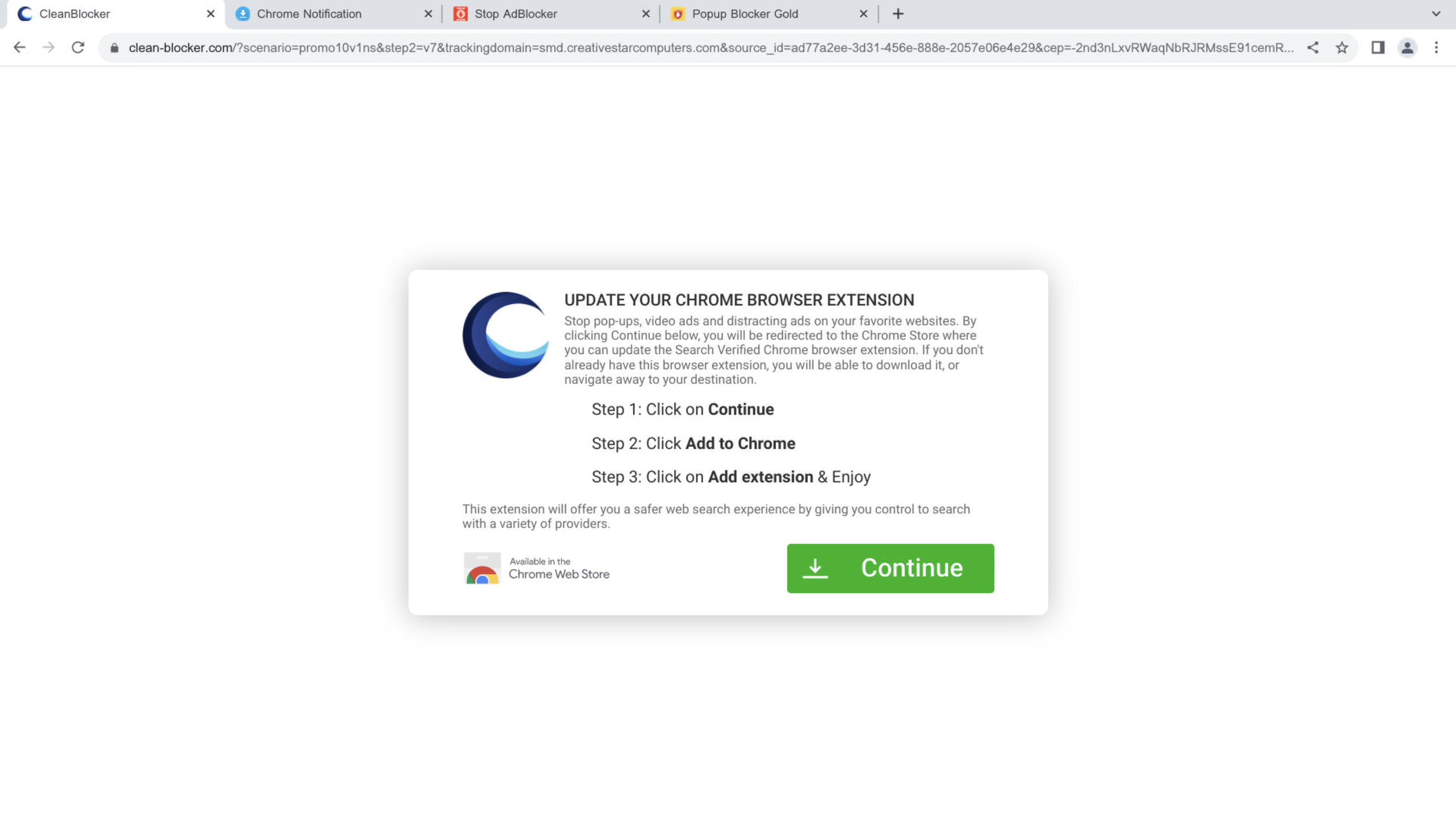
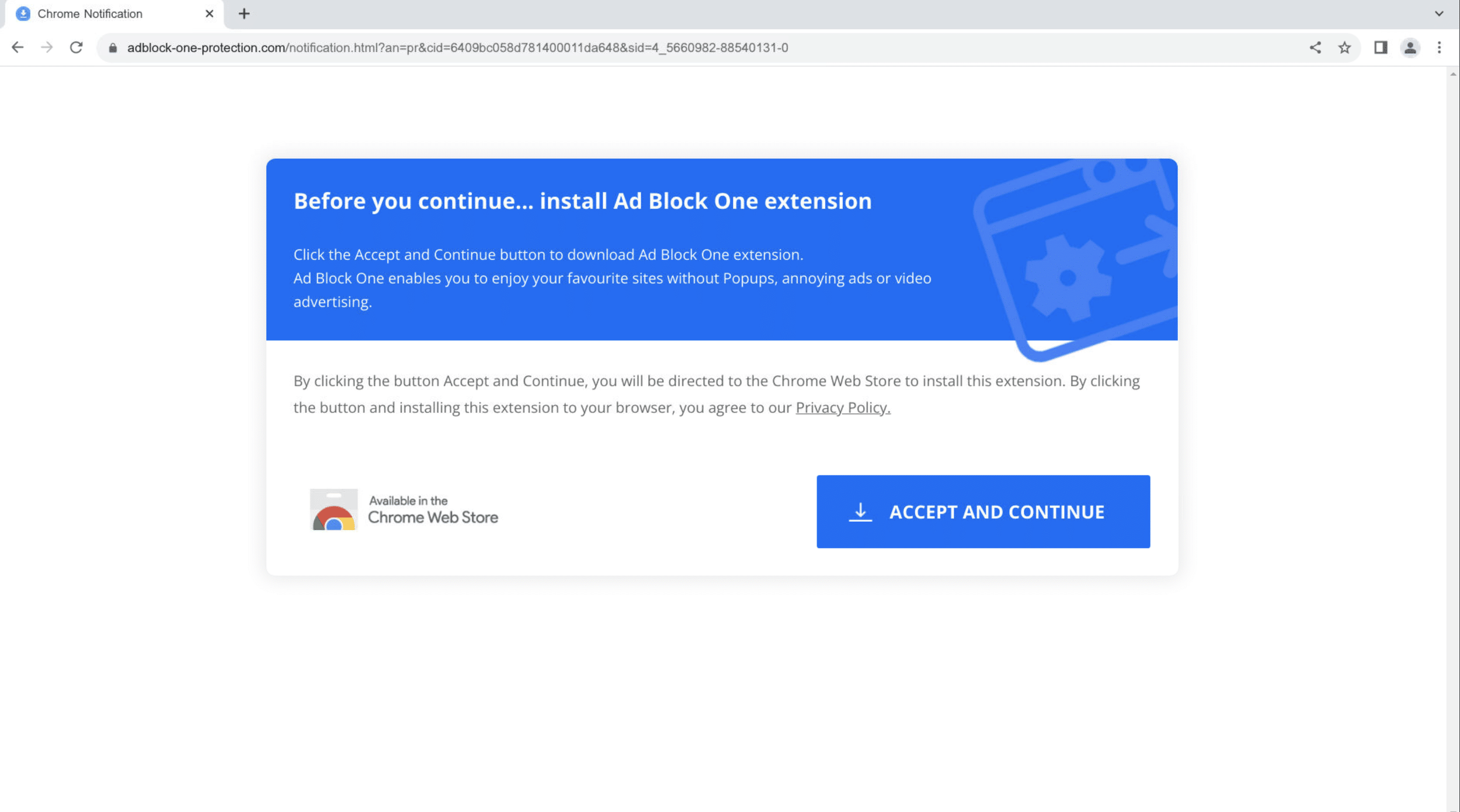
This domain redirects to different fake ad blocker extensions each time it is accessed. These extensions are known adware platforms that perform a variety of harmful actions when downloaded, including:
- populating websites with additional ads;
- unexpectedly redirected users to different websites;
- forcing the use of unwanted browser engines.
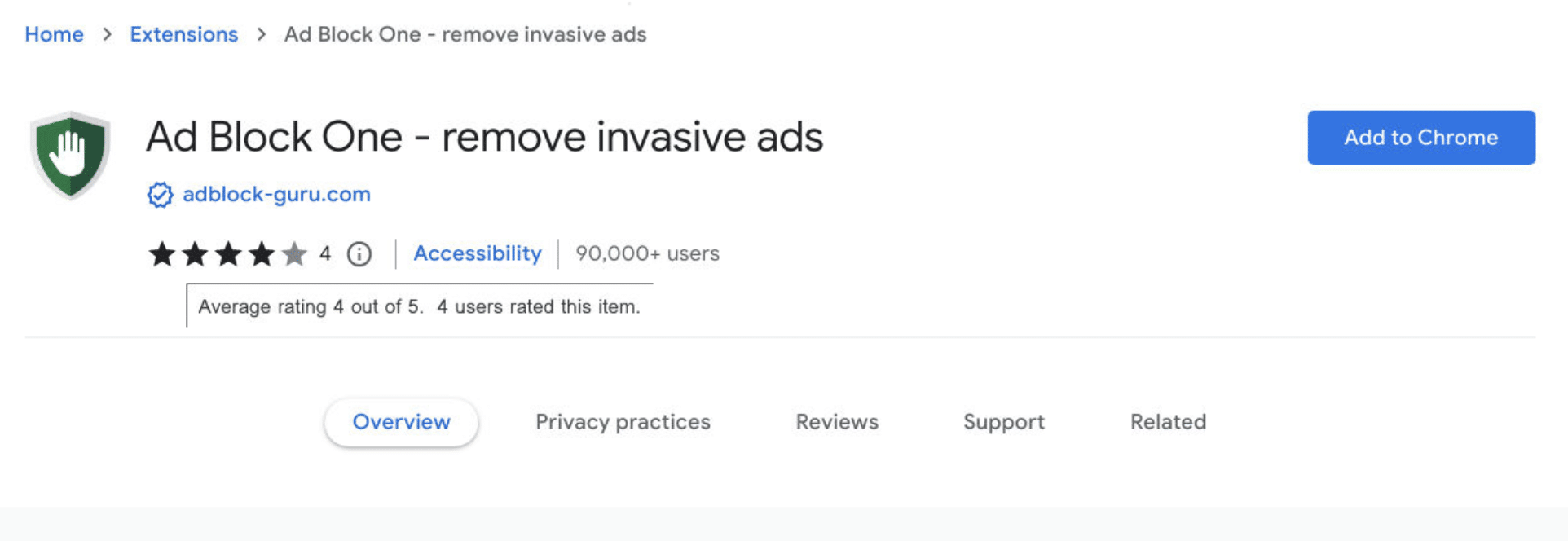
To appear more legitimate, the fake adblockers are installed via the official Google web store, some with over 90k registered downloads and a 4/5 star rating. Further research revealed related adware such as:
adblocker-sentinel[.]net
globaladblocker[.]com
adfreewatch[.]info
Redirects to YouTube
We found that some domains also redirect some mobile users based on their location:
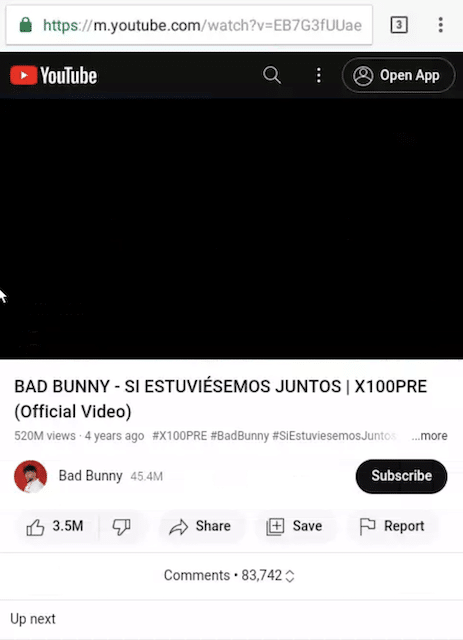
Since the threat campaign is directed at mobile users, the above may be a temporary decoy or placeholder for further attacks.
Fake desktop login
As the campaign evolved, we discovered some domains displaying the fake Facebook login on desktop as well as on mobile, such as tiktok28.ykw3[.]com:
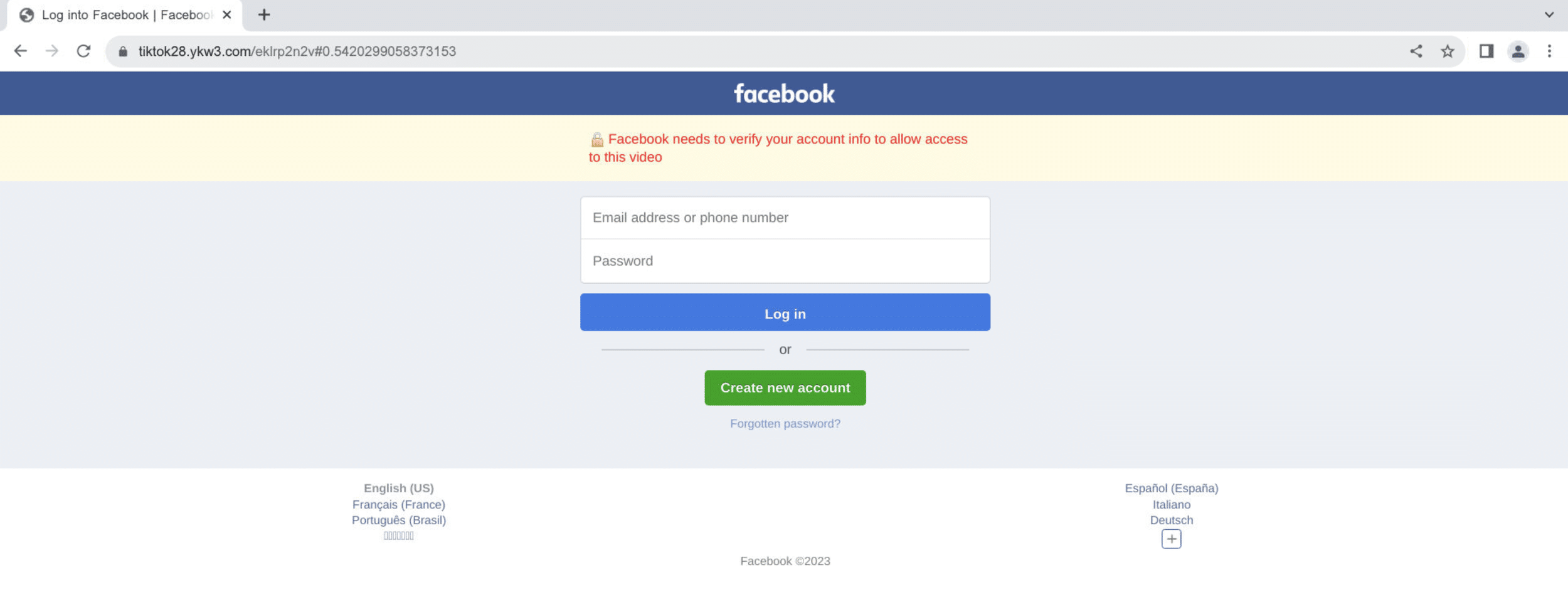
The domain is hosted on 170.10.160[.]83, where we uncovered more than 5000 other domains related to this campaign.
Tracking content and activity similarities uncovered related IoCs such as 190.92.189[.]251, which hosts 3retc[.]com and its subdomain tiktokl.3retc[.]com.
Optimizing for location and user agents
Whilst still launching at scale, phishing campaigns are increasingly deploying geo-blocking and mobile optimization tactics to hone in on specific target groups.
Threat actors are focusing on these TTPs for numerous reasons:
- It saves resources otherwise wasted on suboptimal targets.
- It increases effectiveness within the right audience.
- It reduces the attention drawn to the campaign and increases its longevity.
Except for the third point, this is the same thinking that digital marketers use when localizing the content and language of their ad campaigns and optimizing them for an increasingly mobile landscape.
Takeaways
Phishing attacks remain a persistent threat to all enterprises, regardless of revenue, size, or headcount. The campaign investigated in this article is only one of many recent Facebook scams focused on stealing user credentials through fraudulent links and DMs.
Threat actors constantly adjust their campaigns to match changing digital habits, and better exploit enterprise vulnerabilities. Next to employee training, it is key to stay informed about the security tools available to your organization to stay ahead of potential attacks.
This campaign was uncovered using the Silent Push App and dataset. Silent Push enables businesses to detect malicious infrastructure before it is activated, and proactively check for vulnerabilities within their digital presence.
Take advantage of Silent Push’s vast array of threat defense tools by signing up for our free Community App.
Indicators of Compromise
Below is a categorized list of the IoCs discussed in this article. Please note that the actual number of IoCs is far greater.
We track several malicious groups and threats. Comprehensive lists of real-time IoCs relating to the Facebook campaign and others are available with a Silent Push Enterprise Subscription.
Enterprise users can search for IoCs related to this campaign using the tag sp-blog-2023-03-21.
Browse our complete Threat Intelligence Catalog here.
Domains
adblocker-sentinel[.]net
adfreewatch[.]info
buzzonclick[.]com
globaladblocker[.]com
newwvideos[.]com
photo.asf5[.]sbs
tiktok.0dtlvs[.]cloud
tiktok.2rkb[.]cloud
tiktok.4fbg.cloud
tiktok.4ope9v[.]cloud
tiktok.8rghj[.]cloud
tiktok.8rghj[.]sbs
tiktok.bdwnl[.]cloud
tiktok.dahaak.sbs
tiktok.dfh5[.]sbs
tiktok.fre3[.]sbs
tiktok.km8j[.]sbs
tiktok.sd4rge[.]cloud
tiktok.ss4gy[.]cloud
tiktoks.0dtlvs[.]cloud
tiktoks.ae4eg[.]cloud
tiktoks.dfh5[.]sbs
tiktoks.rhlm4[.]cloud
video.tv1d30[.]sbs
videolass[.]com
videolost21[.]com
videosdidi[.]com
videospriv8[.]com
workspacevideo[.]email
IPs
69.57.163[.]217
190.92.189[.]249

