From Russia with a 71: Uncovering Gamaredon's fast flux infrastructure. New Apex domains and ASN/IP diversity patterns discovered

Update May 1, 2025:
A recent Joint Cybersecurity Advisory from the NSA, FBI, CISA, along with law enforcement in Australia, Canada, and New Zealand, warns that many enterprise organizations have defensive gaps when it comes to detecting and mitigating Fast Flux techniques, such as those utilized by the Gamaredon Group. These gaps expose vulnerabilities that cybercriminals and nation-state actors can exploit to maintain stealthy, persistent access to systems.
Gamaredon’s Fast Flux evasion techniques involve rapidly rotating IP addresses associated with domain names, making it difficult for law enforcement and security systems to block or trace the group’s malicious activity and ultimately avoid detection. Silent Push’s proprietary infrastructure variance metrics are the perfect counter-measure, being purpose-built for tracking, mapping, and blocking Fast Flux networks as they are spun up.
Interested to learn more? Our team has recently published a new technical report on Gamaredon, available exclusively to our enterprise subscribers, which provides live examples of how to utilize our platform’s advanced capabilities to track and proactively block Gamaredon’s malicious infrastructure.
Key Findings
- Silent Push explored the extent of the Gamaredon Group’s fast flux operation.
- We discovered 300+ new Apex domain indicators of compromise (IOCs) from a single Gamaredon domain.
- Our proprietary fingerprinting techniques exposed the deployment of new attacker infrastructure using wildcard A records.
Background
Gamaredon—also known as Primitive Bear, Actinium, or Shuckworm—is a Russian Advanced Persistent Threat (APT) group that has been active since at least 2013 and more recently in Ukraine, including reported attacks on Western government entities:
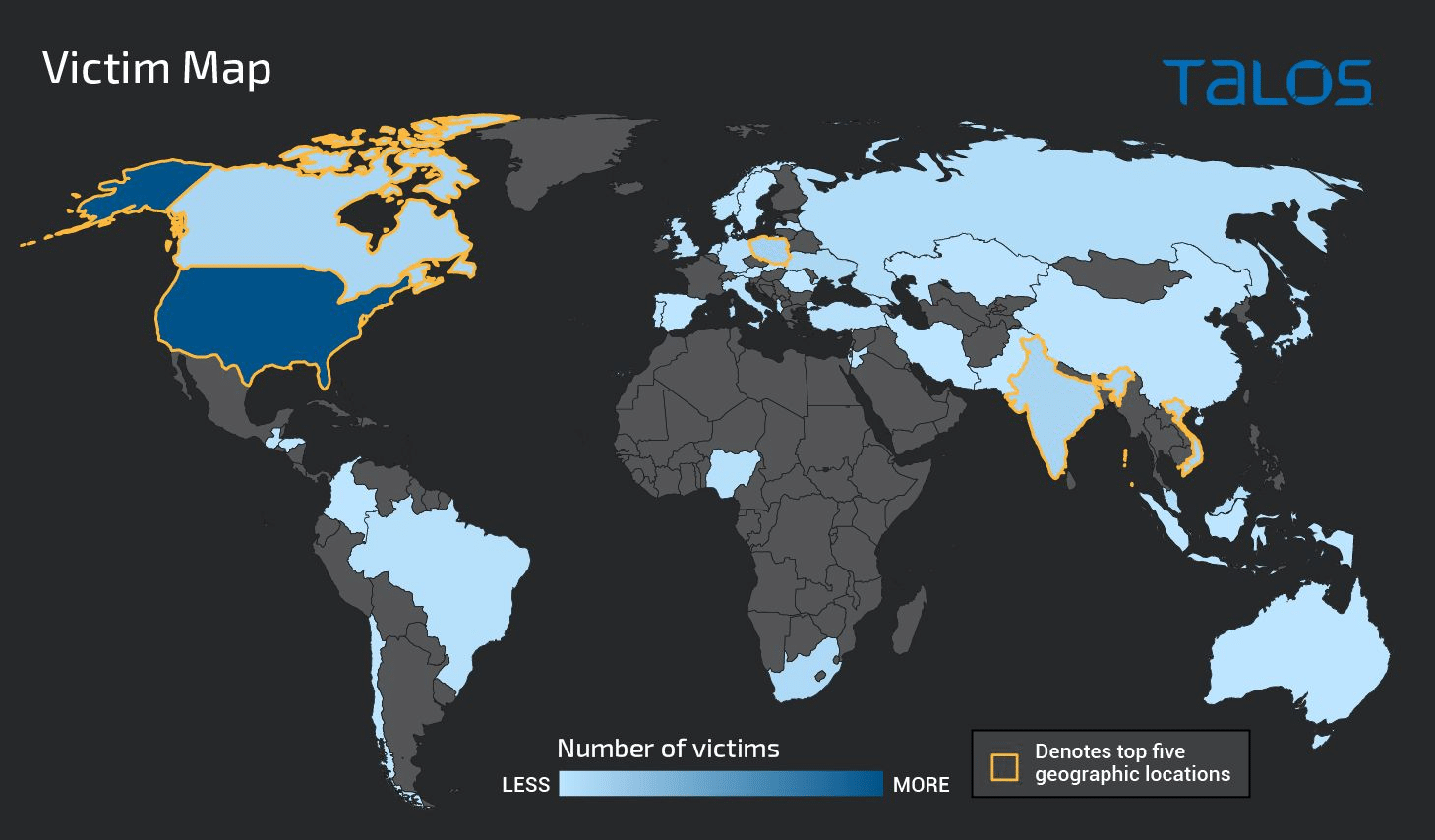
Gamaredon is a highly belligerent threat group that deviates from the standard hit-and-run tactics used by other APT groups by propagating sustained attacks that are both heavily obfuscated and uniquely aggressive.
Gamaredon TTPs
The group uses spear phishing and social engineering to deliver malware hidden within MS Word documents, as referenced below:
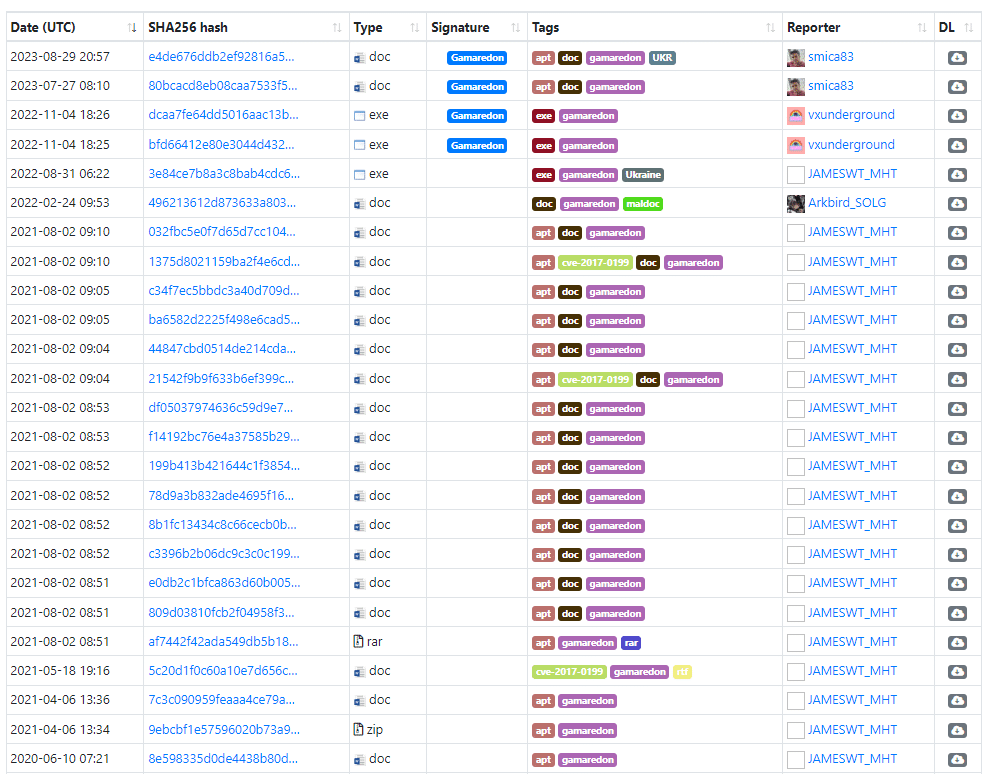
Using MS Word combats static analysis by hosting the payload on a template that is downloaded from an attacker-controlled server; once the document is opened and the user has met one or more conditions, such as geographic location, device type, or system specification, before delivery.
A large number of Gamaredon subdomains used in spear phishing attacks were linked to the top-level domain (TLD) “.ru,” registered via REGRU-RU, and contained the number “71.”
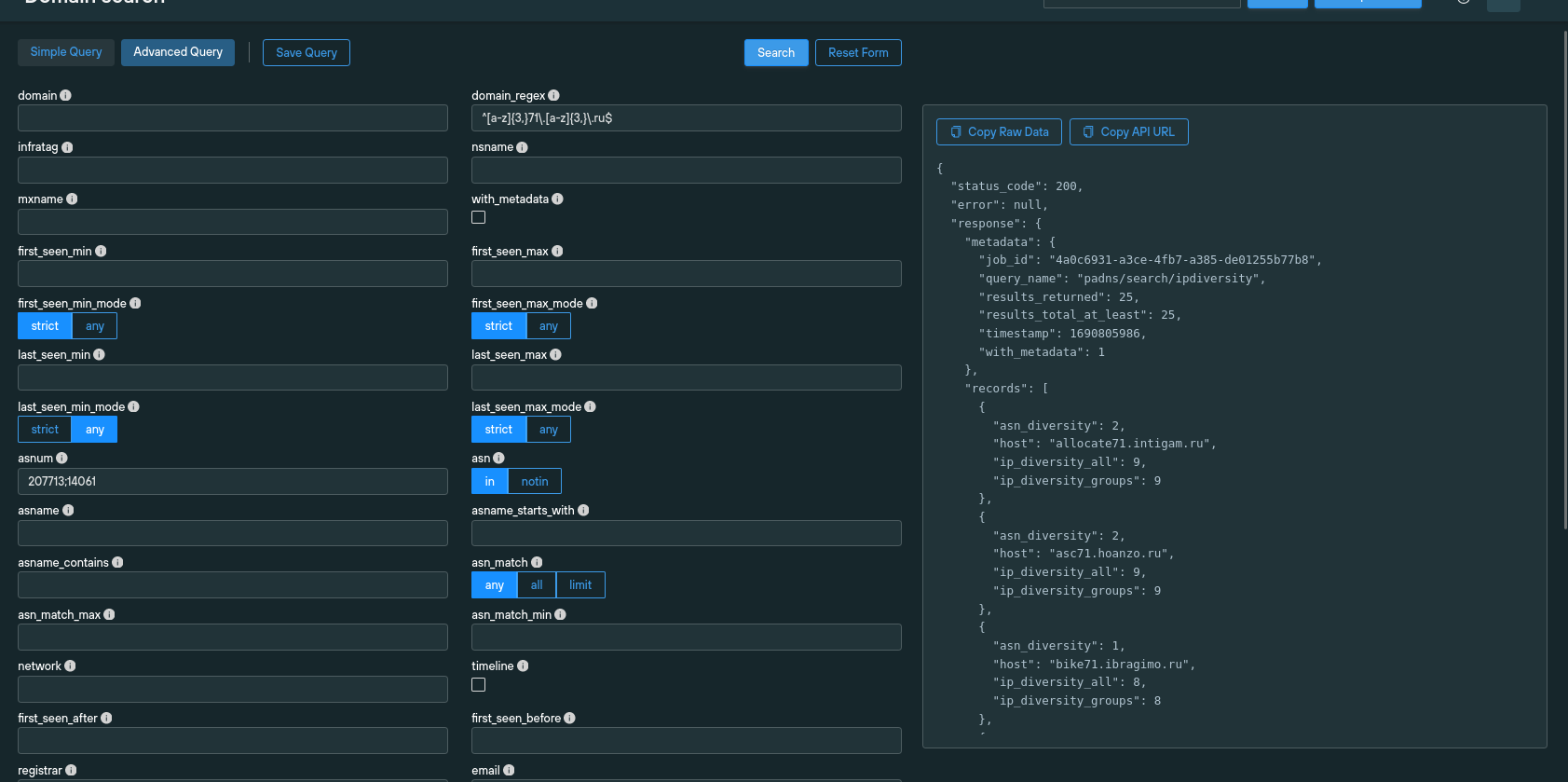
Use of fast fluxing
Gamaredon operates with an innumerable number of IP addresses and uses wildcard A records in place of definable subdomains to evade detection in a technique known as fast fluxing.
A large group of IPs was associated with a single Fully Qualified Domain Name (FQDN) and rotated through an attack at an extremely high frequency via automated DNS resource record (RR) amendments in the zone file.
APT groups employ fast fluxing to circumvent traditional threat detection methods that rely on threat feeds containing full domain names, including subdomains.
Rather than relying on lists of isolated IOCs, organizations need to deploy countermeasures that track the underlying infrastructure that accommodates an attack—Apex domains, ASNs, registrars, and authoritative nameservers—and extrapolate correlative datasets that allow security teams to identify patterns in attacker behavior—such as ASN and IP diversity data or naming conventions.
To defend against fast-flux TTPs, organizations must identify and block Apex domains, regardless of the subdomain. Let’s take a look at how we used Silent Push to do just that…
Deep Dive: samiseto[.]ru
Every investigation begins with a series of observables. Several online sources reported recent attempts by Gamaredon to inject malware, using an MS Word template, from the following domains:
- http://encyclopedia83.samiseto[.]ru/HOME-PC/registry/amiable/prick/sorry[.]83glf
- http://relation46.samiseto[.]ru/DESKTOP-UVHG99D/percy[.]46rra
![Twitter post announcing malware hosted on samiseto[.]ru](https://www.silentpush.com/wp-content/uploads/4-3.png)
Checking VirusTotal confirmed that the domains had been flagged as malicious. This was mainly due to the domains being reported on Twitter as post-breach intelligence:
Traversing Gamaredon’s Fast Flux Infrastructure
We took one of the above domains, encyclopedia83.samiseto[.]ru (hosted on REGRU-RU), and analyzed it by cross-referencing WHOIS information, IP diversity data, and reverse lookups that laid bare a fresh list of domain IOCs:
![Screenshot of the enriching of encyclopedia83.samiseto[.]ru](https://www.silentpush.com/wp-content/uploads/5.png)
We discovered 98 A records associated with *samiseto[.]ru, that were used in constant rotation:
![Web Scanner A record lookup for samiseto[.]ru](https://www.silentpush.com/wp-content/uploads/6-3.png)
Further analysis revealed that IP addresses were used for no more than four days before being replaced with a fresh IP (along with new subdomains). This helped the threat actors evade detection and rendered most isolated IOCs obsolete upon discovery.
To extract actionable IOCs, we created a list of all IP addresses that a subdomain of samiseto[.]ru had ever pointed to. We then applied a reverse lookup to identify all domains associated with those IP addresses, before matching the domains to threat activity using a series of key indicators.
The results returned a list of 375 Apex domains, which we used to populate our Gamaredon early detection feed (available to Silent Push Enterprise customers).
Use of wildcard records
We noticed that any string combination added before .samiseto[.]ru pointed to 5.44.42[.]154. After running a dig command, we were able to ascertain that attackers were using a wildcard A record to point to the domain 5.44.42[.]154:
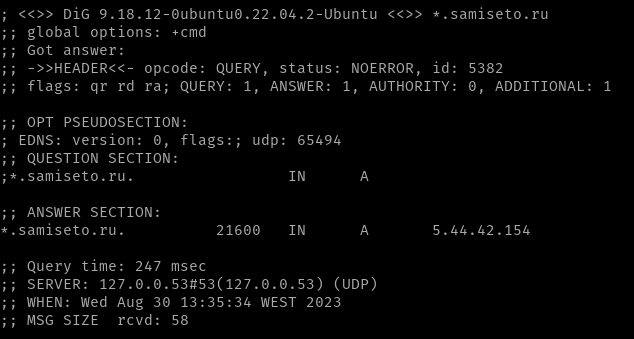
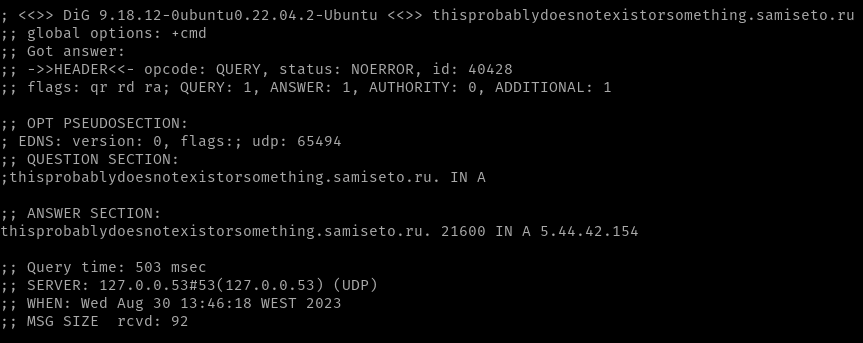
IP diversity and ASN analysis
Using IP diversity data, we established that samiseto[.]ru had pointed to 15 IP addresses within a 30-day period, all of them bar one being hosted on the Russian ASN GIR-AS, RU (207713), with the remainder hosted via Kazakhstan on IT-GRAD, KZ (212819):
![IP/ASN diversity data for samiseto[.]ru](https://www.silentpush.com/wp-content/uploads/10-2.png)
While the majority of IPs over a 90-day period were traced back to GIR-AS RU, we discovered that DIGITALOCEAN US, the New York-based cloud services organization, was also used:
![Historical ASN data for samiseto[.]ru](https://www.silentpush.com/wp-content/uploads/11.png)
Using Silent Push to Combat Gamaredon’s Fast Flux Techniques
Our threat analysts utilized IP/ANS diversity data and advanced DNS fingerprinting techniques to reveal the extent of Gamaredon’s fast flux infrastructure and populate an early detection feed with hundreds of unique malicious Apex domains, using a single reported subdomain as the target IOC.
Silent Push Enterprise users can ingest curated threat feeds containing IOCs related to the Gamaredon group’s fast flux infrastructure using the tags #russo, #gamaredon, and #apt.
The free Silent Push Community Edition also includes many of the lookups used in our research. Sign up here for your complimentary account.
Email [email protected] for further guidance on any of the countermeasures we’ve talked about in this blog article.
Explore our Knowledge Base for in-depth articles on how to use Silent Push to defend against attacks.
Sample Indicators of Compromise List
A sample list of IOCs associated with this threat for a public-facing blog. (A full list of IOCs is available with a Silent Push Enterprise subscription).
- quyenzo[.]ru
- ulitron[.]ru
- bromumo[.]ru
- erinaceuso[.]ru
- ayrympo[.]ru
- caccabius[.]ru
- madzhidgo[.]ru
- amalsa[.]ru
- dedspac[.]ru
- 141.98.233.109
- 46.29.234.119
- 141.98.233.103

