Silent Push maps 2000+ vulnerable IPs linked to GlobalProtect CVE-2024-3400. Active attacker IOFAs caught in PAN-OS honeypot.

Executive summary
On April 12, Palo Alto Networks published an advisory on CVE 2024-3400 – a file creation vulnerability in the GlobalProtect feature of PAN-OS, the software that runs all Palo Alto Networks’ next-generation firewalls.
The vulnerability (with a severity score of 10) enables an unauthenticated attacker to execute arbitrary code, with root privileges, on PAN-OS firewalls.
In this blog we’ll explore how Silent Push Threat Analysts were able to pinpoint 2000+ PAN-OS firewalls open to exploit, identify Indicators of Future Attack (IOFA) targeting affected firewall instances, and cluster all associated CVE-2024-3400 data into three distinct threat feeds that highlight attacker infrastructure and vulnerable IP addresses.
Tracking vulnerable PAN-OS firewalls
Palo Alto Networks have confirmed that the vulnerability is only applicable to PAN-OS 10.2, PAN-OS 11.0, and PAN-OS 11.1 firewalls configured with GlobalProtect gateway, or GlobalProtect portal (or both).
| Versions | Affected | Unaffected |
|---|---|---|
| PAN-OS 11.1 | < 11.1.0-h3, < 11.1.1-h1, < 11.1.2-h3 | >= 11.1.0-h3, >= 11.1.1-h1, >= 11.1.2-h3 |
| PAN-OS 11.0 | < 11.0.0-h3, < 11.0.1-h4, < 11.0.2-h4, < 11.0.3-h10, < 11.0.4-h1 | >= 11.0.0-h3, >= 11.0.1-h4, >= 11.0.2-h4, >= 11.0.3-h10, >= 11.0.4-h1 |
| PAN-OS 10.2 | < 10.2.0-h3, < 10.2.1-h2, < 10.2.2-h5, < 10.2.3-h13, < 10.2.4-h16, < 10.2.5-h6, < 10.2.6-h3, < 10.2.7-h8, < 10.2.8-h3, < 10.2.9-h1 | >= 10.2.0-h3, >= 10.2.1-h2, >= 10.2.2-h5, >= 10.2.3-h13, >= 10.2.4-h16, >= 10.2.5-h6, >= 10.2.6-h3, >= 10.2.7-h8, >= 10.2.8-h3, >= 10.2.9-h1 |
Silent Push scans the global IPv4 range every day, and categorises the data using SPQL – a free-form query language our customers use to search for associated web content, HTML, SSL, and certificate data. Click here for a full list of searchable fields.
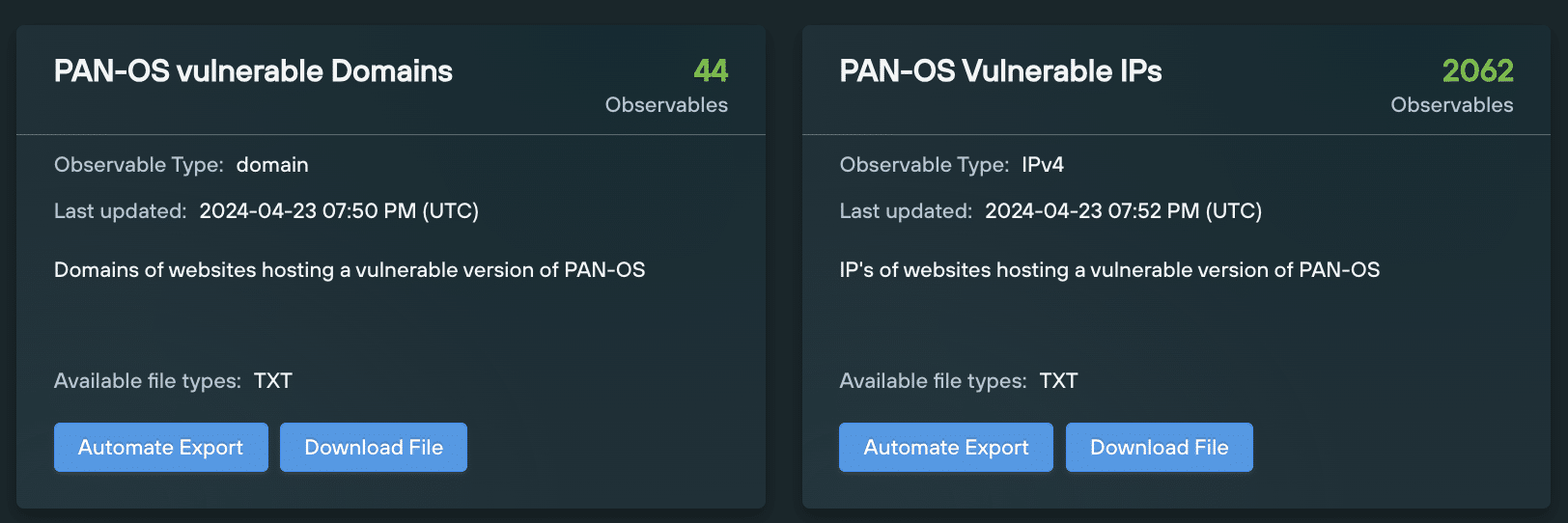
We used the above version information to construct a custom query that scans for exploitable PAN-OS instances exposed to the Internet, before collecting the domains and IPs together in two Bulk Data Feeds that Enterprise customers can use to improve their security posture:
- “PAN-OS Vulnerable Domains”
- “PAN-OS Vulnerable IPs”
As of writing our PAN-OS Bulk Data Feeds contain over 2000 vulnerable PAN-OS instances exposed to the Internet.
Tracking PAN-OS attacker infrastructure
Unit 42 – Palo Alto’s threat research team – has published guidance for all affected PAN-OS users on how to mitigate the threat of intrusion on affected devices.
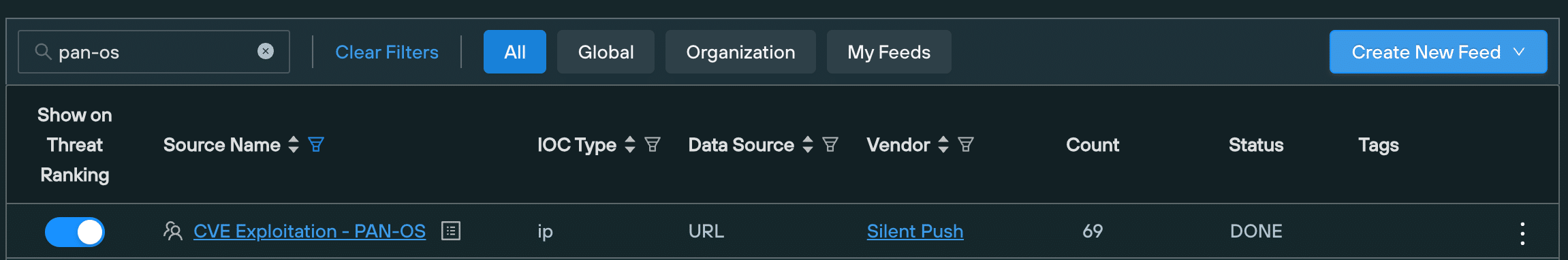
To help minimize the global impact of CVE-2024-3400, Silent Push Threat Analysts have implemented an Early Detection Feed (“CVE Exploitation – PAN-OS”) containing the IP addresses of threat actors who are actively attempting to exploit vulnerable PAN-OS instances.
Scroll to the bottom of this blog for a sample of attacker IP addresses.
Note: An IP address is only placed in our PAN-OS feed if an attacker attempts to access the specific URL that triggers the vulnerability.
Mitigation
Silent Push provides users with bilateral view of infrastructure linked to CVE 2024-3400 – both vulnerable firewall instances, and the IPs involved in launching an attack.
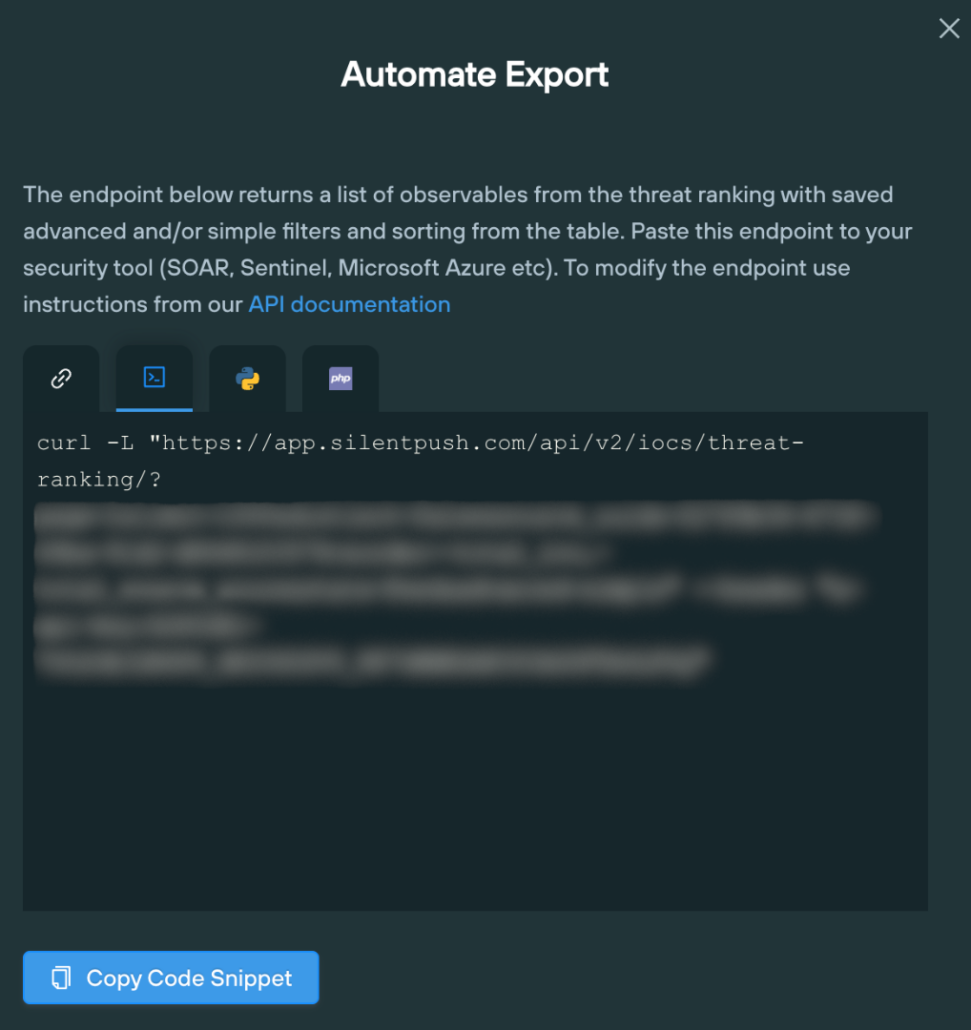
Enterprise users are able to use the Silent Push API to ingest the PAN-OS attacker Early Detection Feed into their existing security stack, or download a list of all related CVE-2024-3400 IPs and domains from the Bulk Data Feeds mentioned for further analysis.
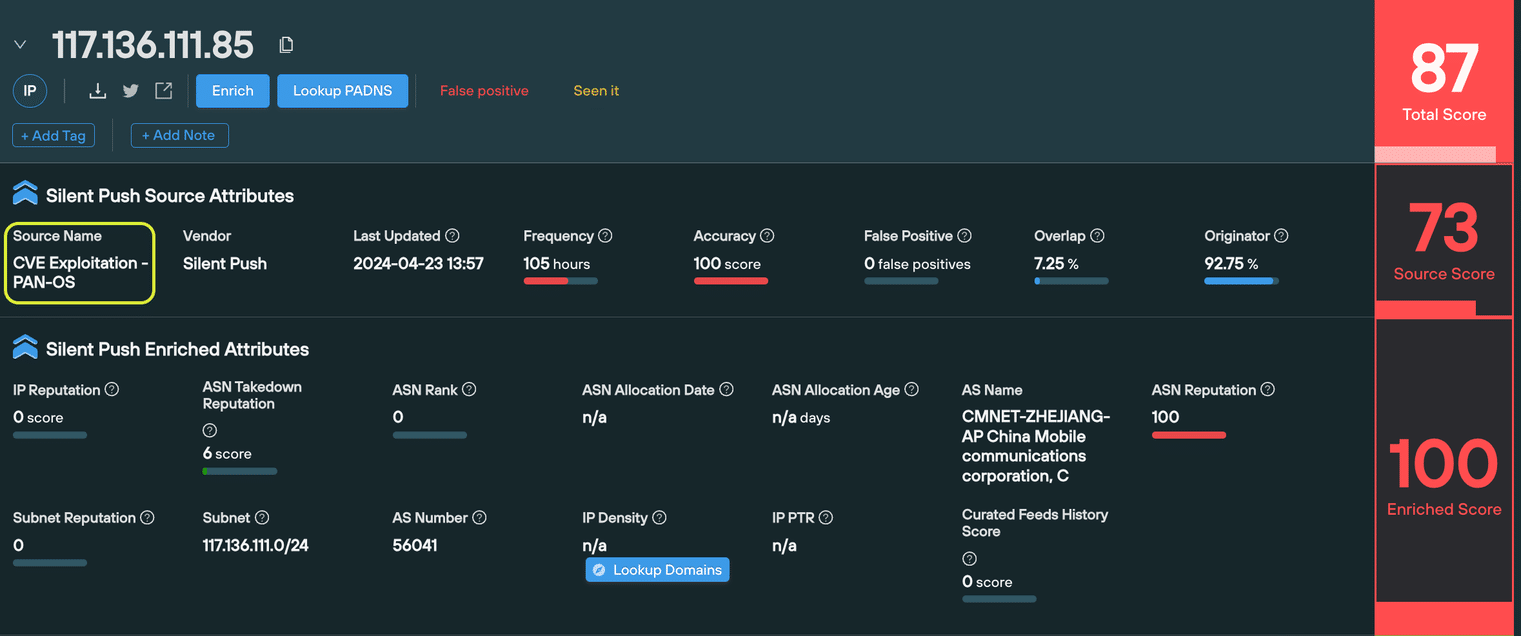
Enterprise users can also use the Silent Push console to quickly search across an enriched PAN-OS dataset using the ‘Threat Ranking’ screen, and correlate the data with other known threat activity to discover associated infrastructure.
Register for Community Edition
Silent Push Community Edition is a free threat hunting and cyber defense platform featuring a range of advanced offensive and defensive lookups, web content queries, and enriched data types, including Silent Push ‘Web Scanner’ and ‘Live Scan’.
Click here to sign-up for a free Community Edition account.
IOFA Sample
117.136.111[.]85
107.155.55[.]118
154.90.49[.]108
107.155.55[.]111
187.130.181[.]29
18.143.129[.]154
104.28.157[.]195
104.28.160[.]182
121.28.181[.]90
146.190.114[.]191
165.227.44[.]48
128.199.45[.]40
68.183.227[.]9
202.103.95[.]217
106.104.162[.]35
35.234.3[.]5
8.222.152[.]55
8.208.112[.]87
103.29.68[.]12
103.29.68[.]126
172.233.56[.]195
212.64.28[.]57
193.43.104[.]199
176.97.73[.]198
38.180.29[.]229
165.154.205[.]202
23.94.158[.]73
221.216.117[.]106
172.245.240[.]166
111.204.180[.]253

