"Ad-versaries": Tracking new Google malvertising and brand spoofing campaigns. New MaaS DarkGate loader, DanaBot, IcedID and more.
- Content scans show an increase in malvertising activity from Q3 2023 onwards.
- New MaaS DarkGate variant adapted for malvertising purposes.
- Brand impersonation TTPs used to inject infostealers, including DanaBot and IcedID.
- Evidence of threat actors targeting various network tools, tech utilities and multimedia suites.
Background
Let’s start with some context. From Q4 2022 through to Q1 2023, Silent Push Threat Analysts tracked a series of malvertisment campaigns that acted as a delivery method for several banking trojans and infostealers – including Ursnif and Vidar – targeting a broad range of organizations and sectors.
So what’s changed since then? Despite the lull in activity, our Threat Analysts have remained on the trail of trojan/infostealer-based brand impersonation campaigns. Our content scans have recently pinpointed a resurgence in malvertisment activity, not limited to the attack vectors and brands discussed in our previous blogs.
Our research shows conclusive evidence of Google ads being used to propagate malvertisment campaigns specifically constructed to deliver a range of malicious executables, including a new variant of the DarkGate commodity loader and two modular banking trojans – IcedID (a.k.a. BokBot) and Danabot.
Let’s take a look at how we used Silent Push to traverse attacker infrastructure, how the malicious code behaves and what organizations need to do in order to counteract this latest spate of attacks.
Tracking new threats
Our previous research focused on the use of spoofed AnyDesk domains and crypto-related browser extensions, among other attack vectors. This time around, threat actors have cast their nets far wider.
Here’s an up top date breakdown of the latest brands affected, gathered from our most recent scan data repositories:
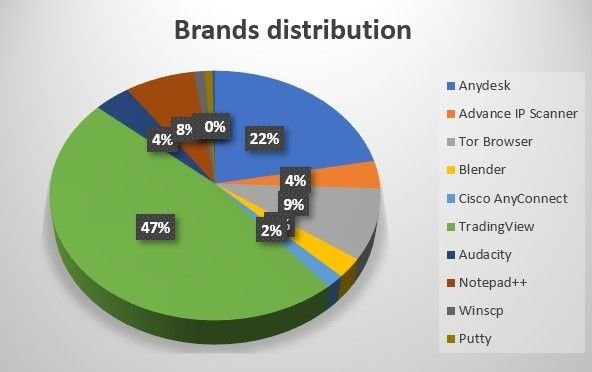
2023 malvertisment campaigns (Source – Silent Push scan data)
Threat actors have regrouped to focus on remote desktop platforms, network tools and miscellaneous tech utilities, including multimedia suites and browsers.
From our dataset, TradingView – the popular financial charting platform – emerges as the most heavily targeted brand throughout 2023. AnyDesk remains a popular attack vector, comprising nearly a quarter of all malicious domains.
Silent Push is actively tracking these new domains, and all associated infrastructure, in a dedicated malvertisment feed. Here’s a snapshot of spoofing domains related to TradingView:
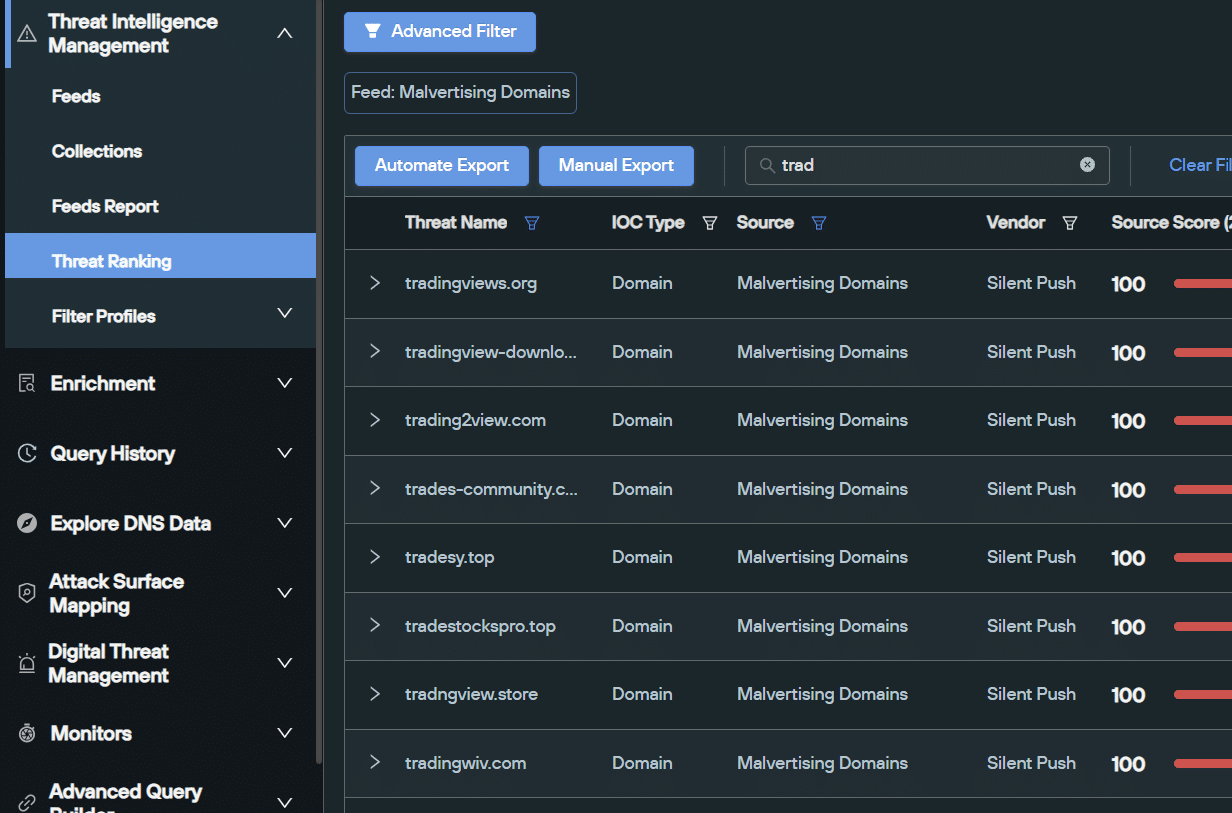
Snapshot of scam domains related to TradingView (Source: Silent Push malvertisement feed)
Google malvertising: Advanced IP Scanner
Our brand impersonation scans are consistently outputting newly registered malicious domains that are appearing as sponsored ads at the top of a Google search.
Let’s take a look at one such brand affected by Google malvertising – the LAN traffic analyzer Advanced IP Scanner.
We discovered a scam domain – advanced-ip-scanner[.]top – attempting to capture traffic intended for the legitimate site advanced-ip-scanner[.]com. As you can see, only the TLD has been changed:
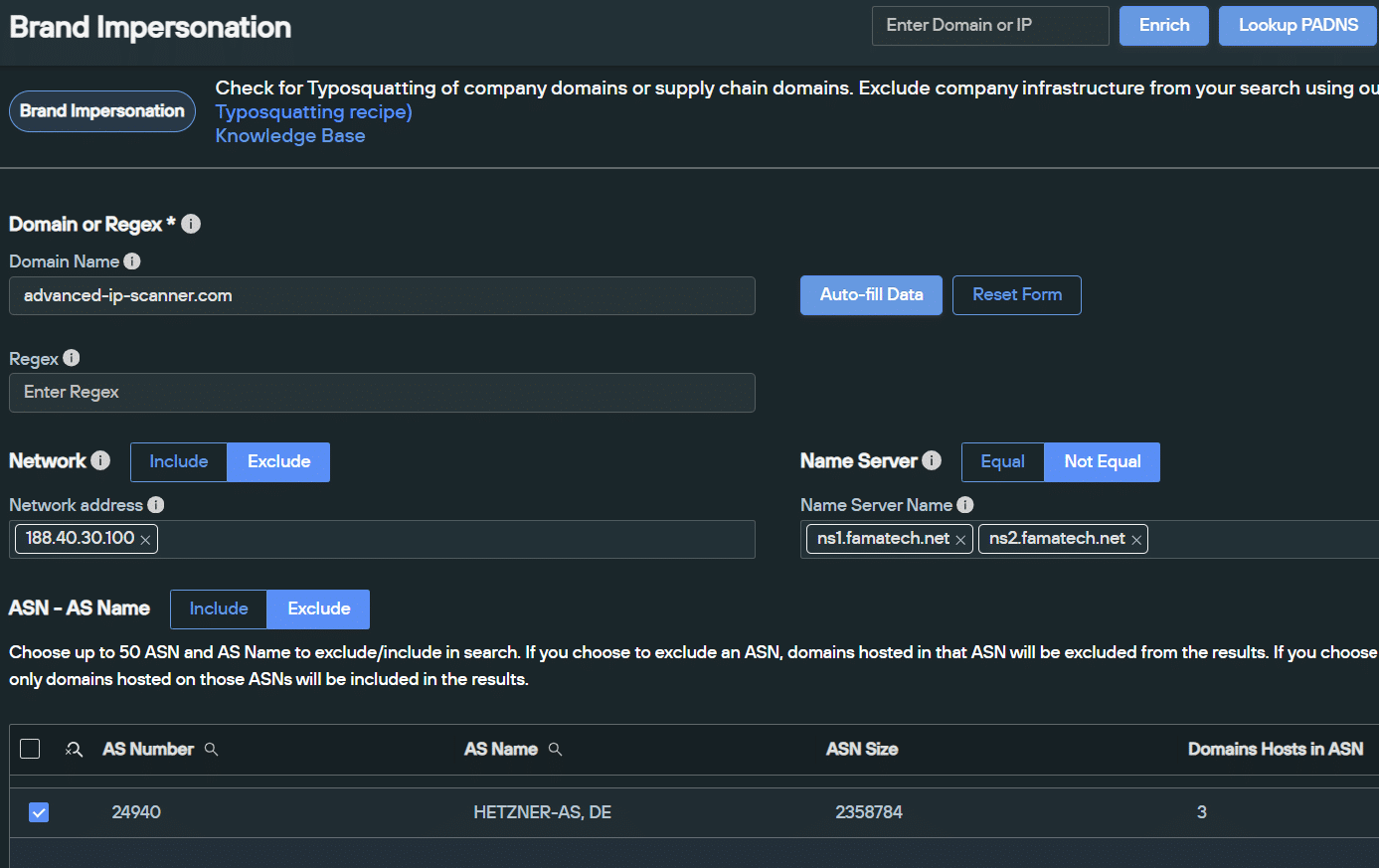
Brand Impersonation scan on advanced-ip-scanner[.]com (Source: Silent Push)
advanced-ip-scanner[.]top redirects to the malicious domain shouman-acc[.]com:
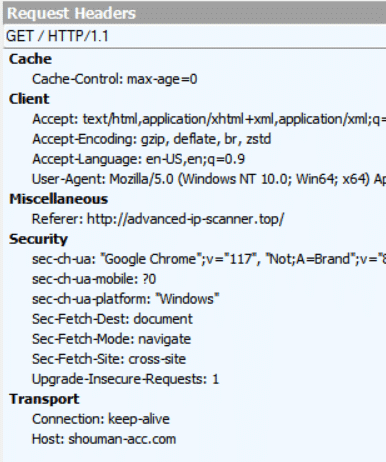
advanced-ip-scanner[.]top redirecting user to shouman-acc[.]com
A quick Google search for ‘scanner IP’ returns a sponsored advertisement for ‘Advanced Scanner IP’, utilising domain that redirects to shouman-acc[.]com:
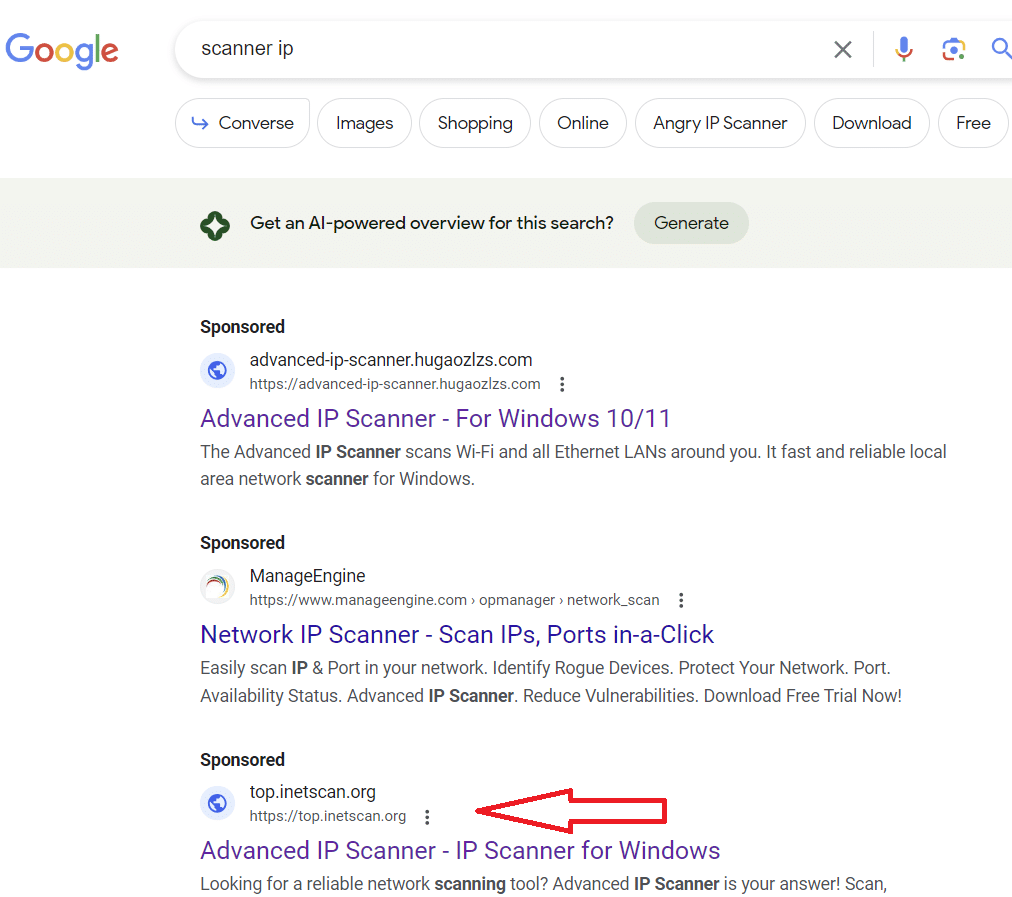
Active malvertisment on Google.com (as of 15 October 2023)
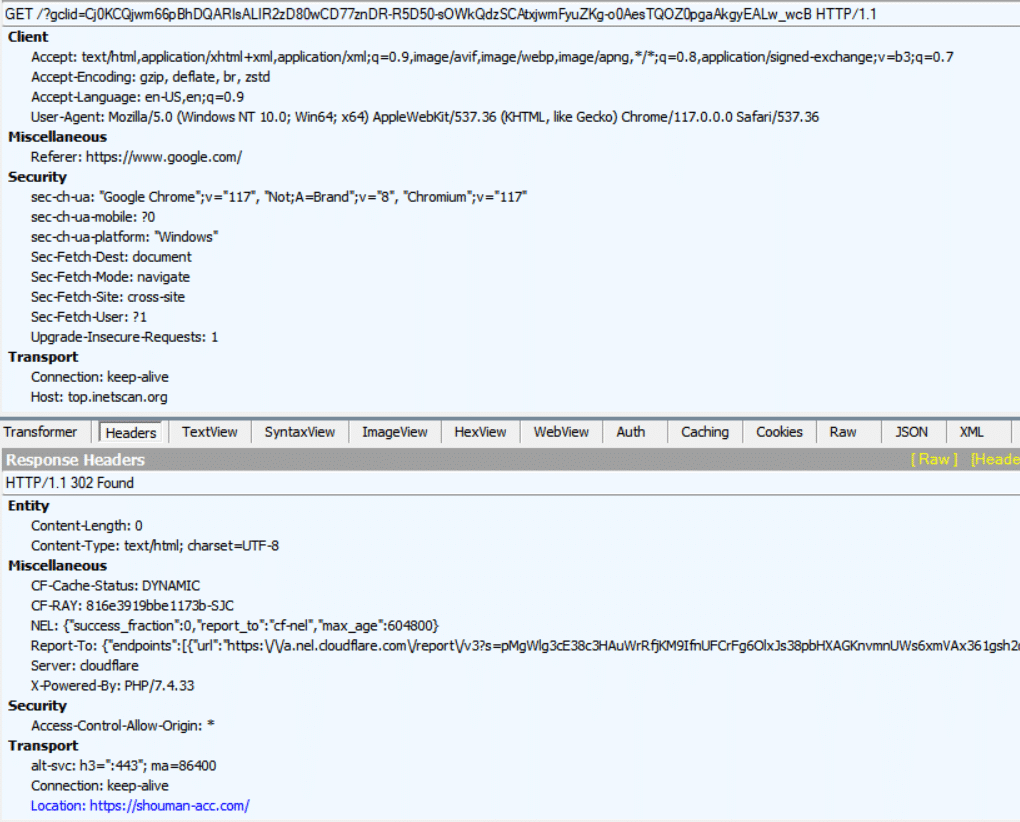
Malvertisement domain using a 302 redirect to shouman-acc[.]com
In this instance, shouman-acc[.]com acts as a delivery method for the IcedID banking trojan, with the hash 86bcd250b70e261d29a20538ffaf9ea3b27b510f02721cc6853bda227deeb118:
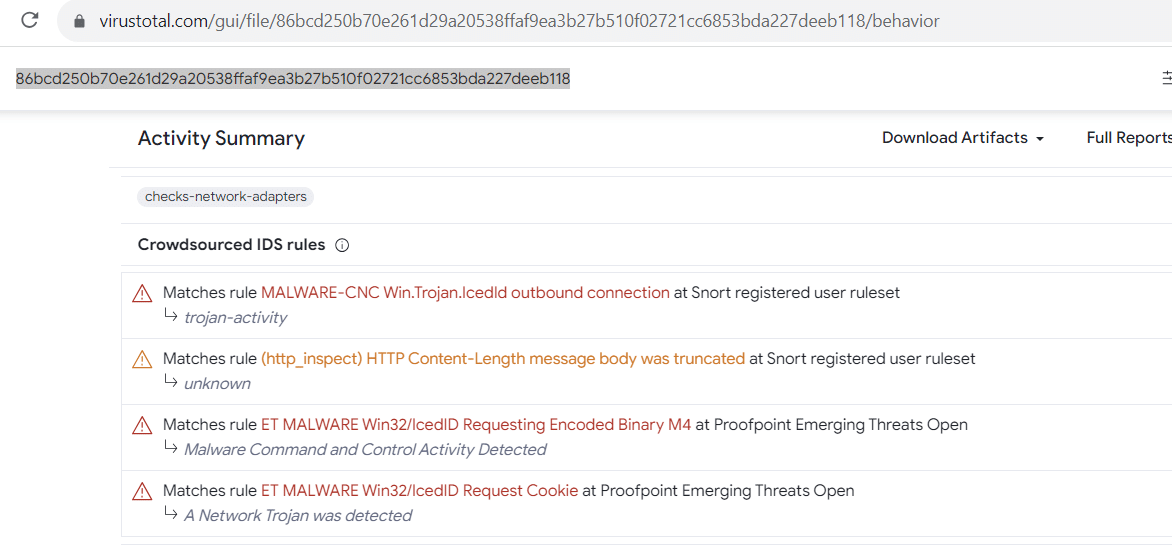
IcedID hash value (Source: VirusTotal)
The content consists of ‘Free Download’ button that instigates the delivery, with a grammatically incorrect CAPTCHA box included for crawler protection:
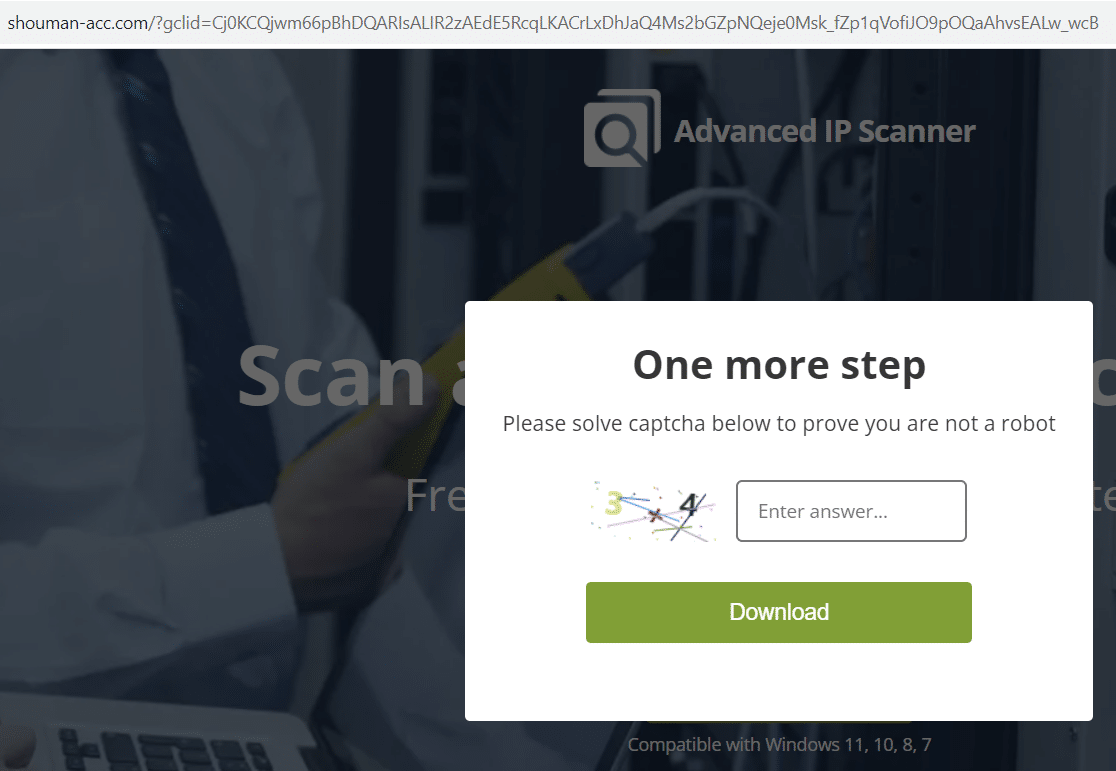
shouman-acc[.]com delivering IcedID trojan
DanaBot (a.k.a. BokBot) malvertising
In July, security researchers unearthed a new variant of the Malware-as-a-Service infostealer, DanaBot, featuring a modular subscription model and adversary support utilities, via the Russian language ‘Exploit’ forum.
Our investigation shows evidence of threat actors adapting this new variant for malvertising purposes, again targeting Advanced IP Scanner.
Let’s take a look at how it’s being used. In September, we observed sponsored Google ads for ‘scanner IP download’ pointing to domains spoofing Advanced IP Scanner:
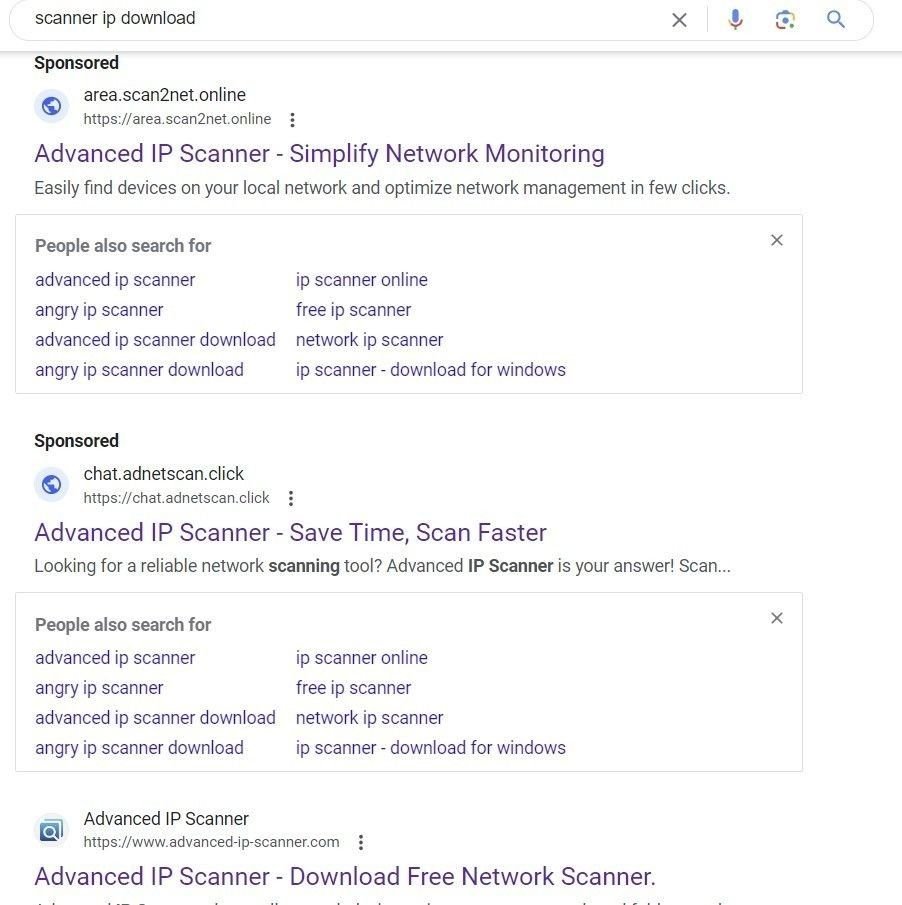
Malvertising results for ‘scanner ip download’ on Google
A Fiddler traffic capture shows traffic redirected from google[.]com leading to the typosquatting domain advancde-ip-scanner[.]com:
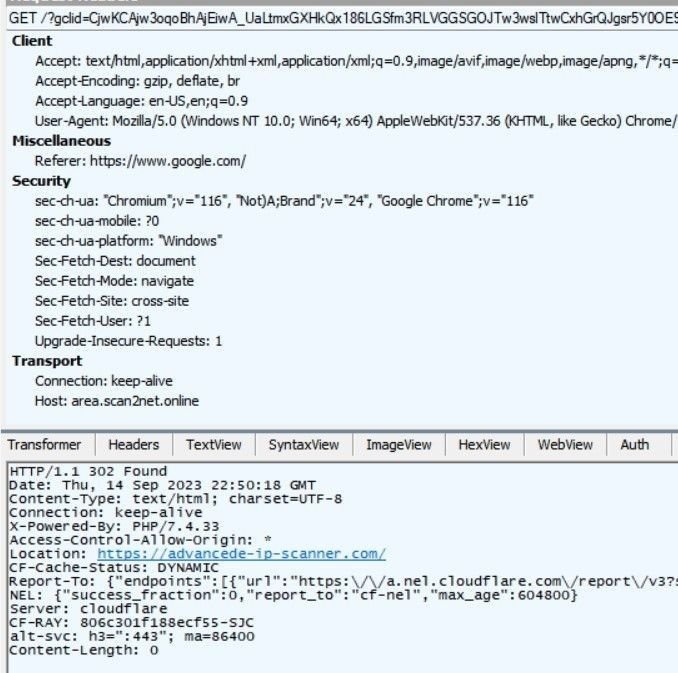
Fiddler traffic analysis of advancde-ip-scanner[.]com
As is the case with the IcedID attack, the destination domain, advancde-ip-scanner[.]com, features a download link that injects a malicious file with a hash value of 123b285236757f7ac0c4f2107756a0ed661c9190aad81914c54debdd3bfa00f4.
This new DanaBot version attempts to read credentials and cached browser data:
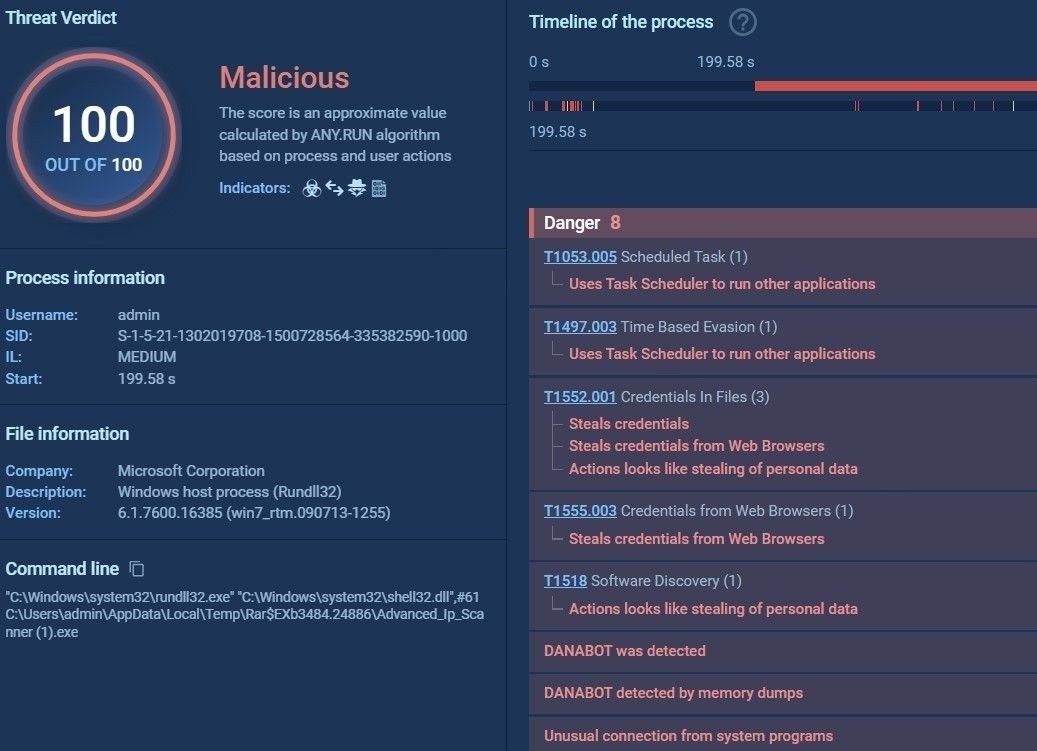
DanaBot analysis (Source: any.run)
The malware uses the following C2 IPs to exfiltrate data:
- 172[.]86[.]121[.]218
- 45[.]61[.]160[.]115
- 172[.]86[.]97[.]119
- 91[.]212[.]166[.]96
In the above case, the Google ad remained active for more than a week. We also observed another DanaBot hash – 183276d2ea0740a8e92b3cff7abef725 – featuring the same ad, and the same domain, using the following C2 IPs:
- 185[.]225[.]69[.]33
- 5[.]189[.]253[.]176
- 5[.]189[.]253[.]131
- 185[.]225[.]69[.]230
New DarkGate variant
In July of this year, our content scans started to return large datasets that indicated a resurgence in malvertising activity. This renewed activity coincided with the emergence of a new variant of the DarkGate loader, also observed by other malware analysts and threat researchers throughout August.
TreeSize spoofing
Among the brands targeted with DarkGate injections in our dataset is Jam Software’s popular disk management too TreeSize Free. Here’s a domain – jam-software[.]net – that was flagged in our malvertisement sweeps as being malicious:
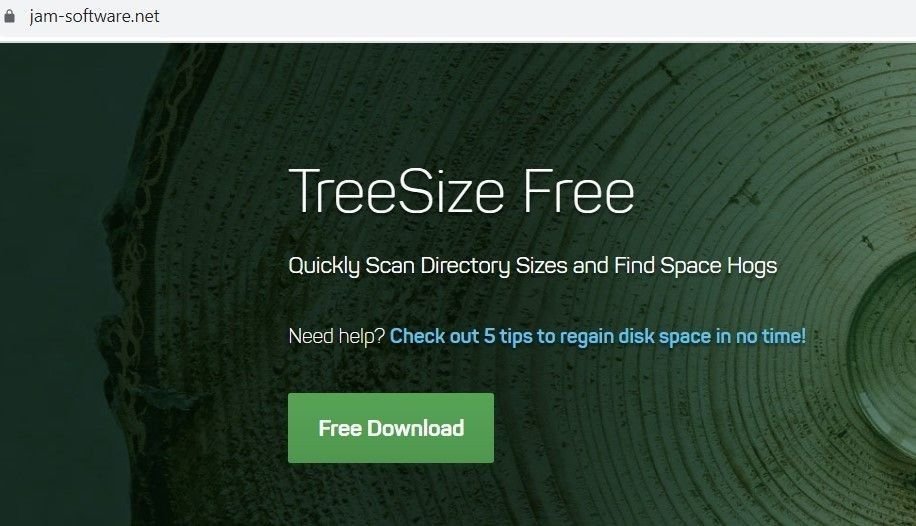
Scam TreeSize domain hosting DarkGate loader
Sandbox analysis of an executable downloaded from the above domain identifies the hash as a DarkGate variant:
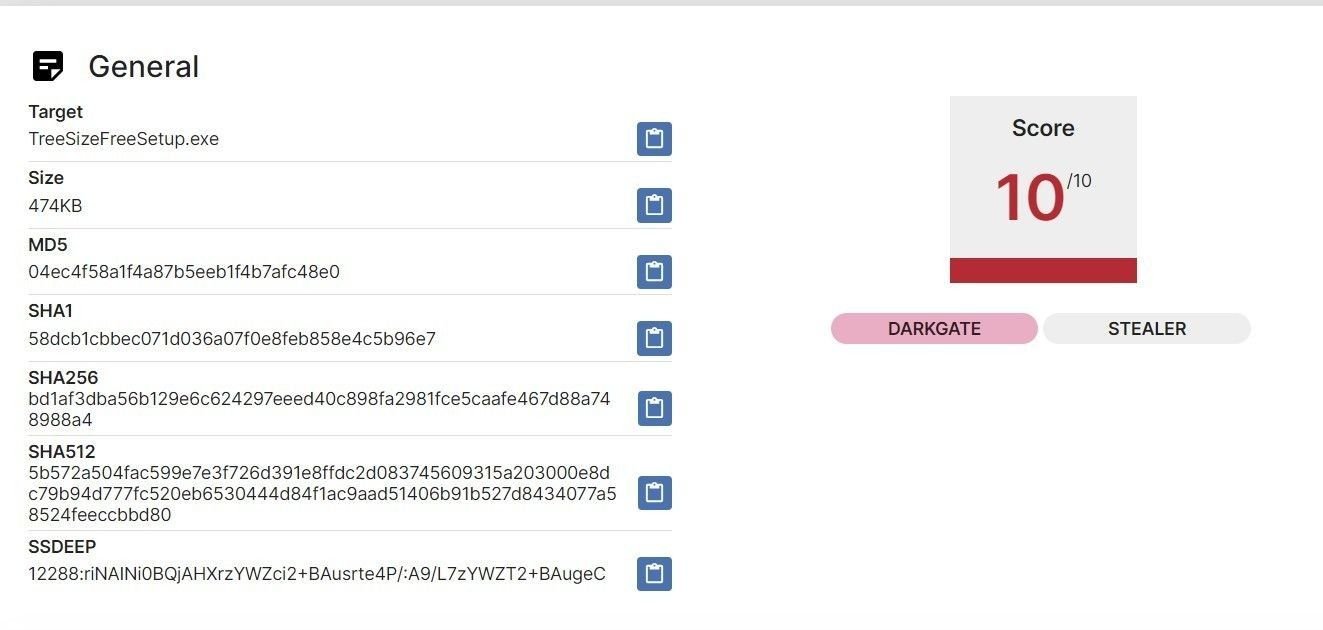
Sandbox analysis of an executable from jam-software[.]net (Source: tria.ge)
Remote desktop spoofing
Threat actors have always considered network tool impersonation to be low-hanging fruit, and this latest series of campaigns is no different.
Recent content scans have flagged up numerous domains impersonating winscp[.]net the open source FTP, scripting and file manager utility, WinSCP
One such domain is winscphub[.]com (currently offline). Here’s a Silent Push DNS scan for the aforementioned domain, including reputational data:
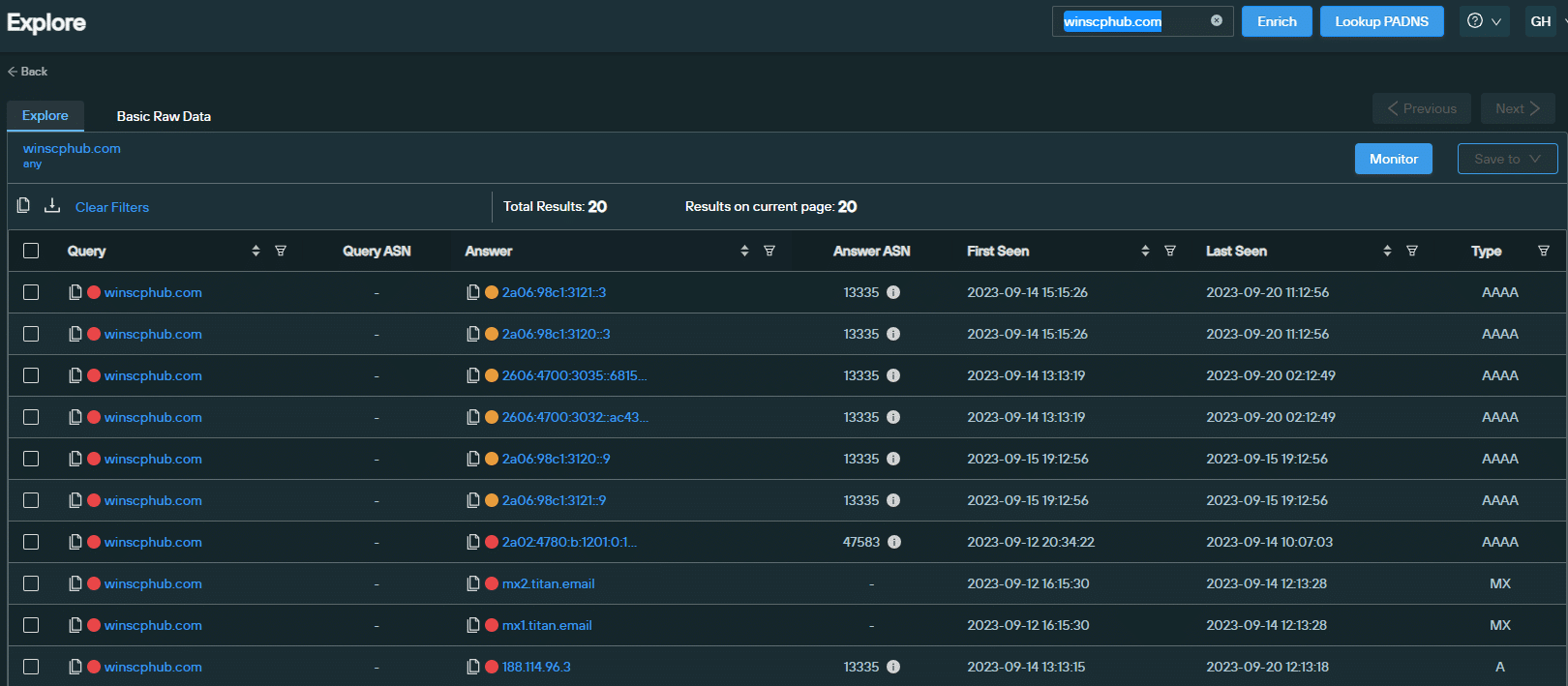
DNS and reputation data for winscphub[.]com (Source: Silent Push)
The website features a download link that delivers a DarkGate variant with evasion and credential harvesting capabilities, with the file hash 2b6830970820af8d43ab710507ee19ca:
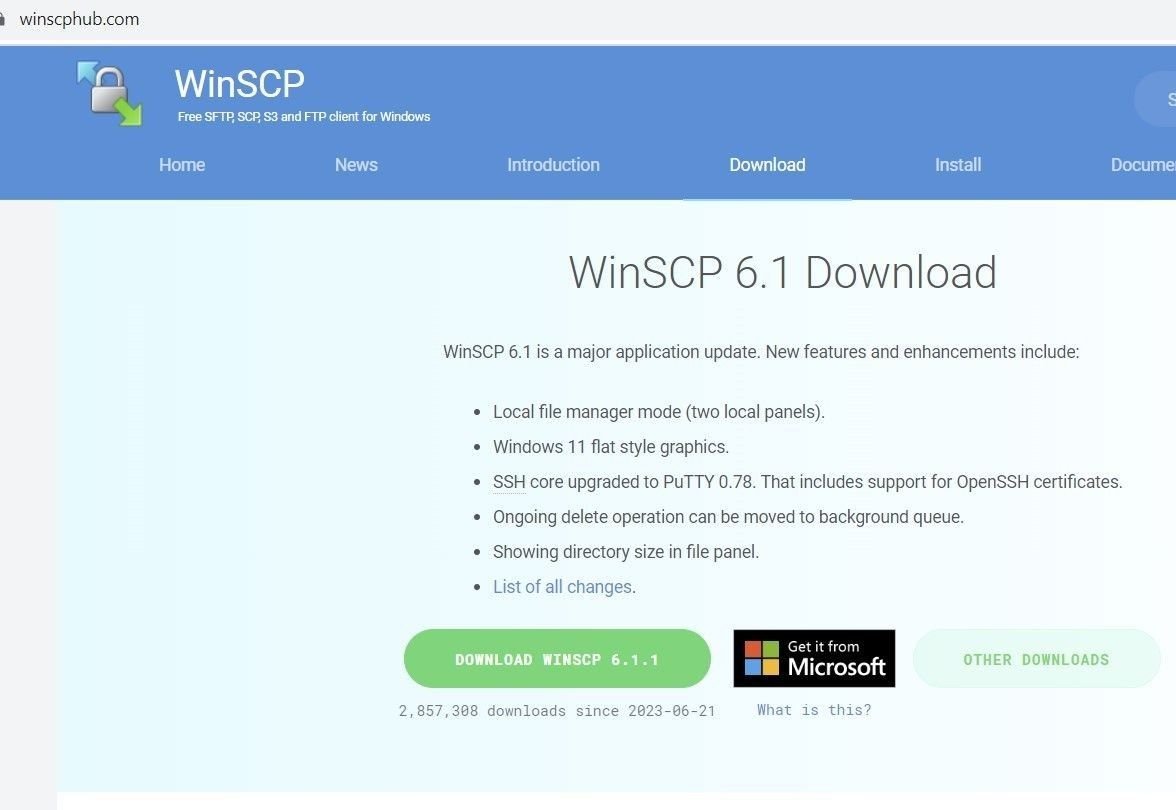
Spoofed WinSCP domain – winscphub[.]com
Malware analysis
Created in the host machine’s temporary files, the malware uses ICACLS.EXE (a Windows command-line utility that IT admins use to change access control lists on files and folders) to provide the malware with elevated privileges:
C:\Windows\system32\ICACLS.EXE” “C:\Users\Admin\AppData\Local\Temp\MW-c7688c81-6868-4efd-899f-aa889e84eda9.” /SETINTEGRITYLEVEL (CI)(OI)HIGH
Consistent with other DarkGate variants, the dropped file also contains an AutoIt executable and a corresponding .AU3 script in the same location:
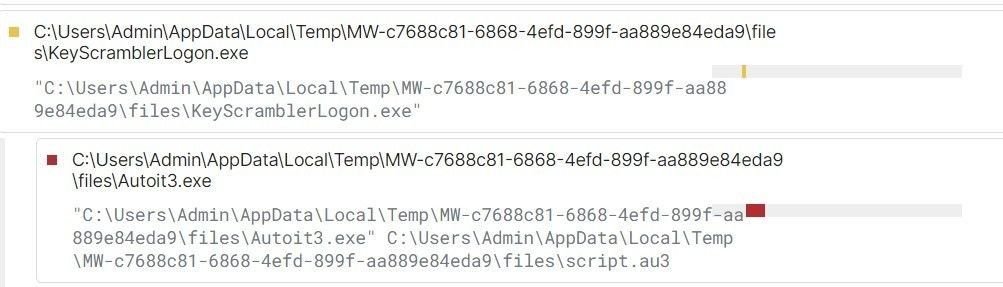
AutoIt script (Source: tria.ge sandbox report)
To embed itself in the host machine and maintain optimal persistence levels, the malicious executable ‘regsvr32.exe’ loads it’s DLL with a COM entry in registries containing a CLSID (a serial number that represents a globally unique identifier for any application component in Windows):
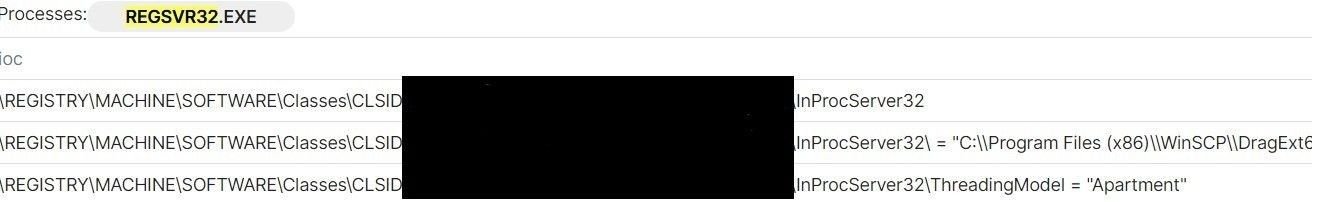
Persistence activity (Source: tria.ge sandbox report)
The variant also creates a shortcut file under ‘C:\Users\Admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\’.
The malware also attempts to read the location of Putty passwords, by attempting to locate registry paths used by the application:
- HKLM\SOFTWARE\WOW6432Node\Martin Prikryl\WinSCP 2\DisablePasswordStoring
- HKCU\SOFTWARE\Martin Prikryl\WinSCP 2\Configuration\Interface\PuttyPassword
- HKCU\SOFTWARE\Martin Prikryl\WinSCP 2\Configuration\Interface\AutoSaveWorkspacePasswords
Conclusion
Our scans show a noticeable and worrying uptick in the use of sponsored Google ads to deliver infostealing malware in the third quarter of this year, most notably IcedID and a new version of the DarkGate loader adapted for malvertising purposes.
Threat actors are continuing to spoof legitimate domains through Google using a variety of TTPs, including typosquatting, the strategic placement of malicious links and hidden redirects.
To combat such tactics, affected organizations need to adopt security protocols that track the underlying infrastructure involved in the attack – registrars, ASN data, nameservers etc. – rather than relying on isolated lists of IOCs that are easily replaced by any adversary that uses them.
IOCs
- winscphub[.]com
- jam-software[.]net
- advancede-ip-scanner[.]com
- advanced-ip-scanner[.]top
- shouman-acc[.]com
- aptekoagraliy[.]com
- 172[.]86[.]121[.]218
- 45[.]61[.]160[.]115
- 172[.]86[.]97[.]119
- 91[.]212[.]166[.]96
- 185[.]225[.]69[.]33
- 5[.]189[.]253[.]176
- 5[.]189[.]253[.]131
- 185[.]225[.]69[.]230
Using Silent Push to combat malvertising
Silent Push Community Edition features many of the queries and enriched data types that we used to track malvertising activity. Sign-up free here.
Silent Push Enterprise customers benefit from curated feeds that track malvertising infrastructure as it’s deployed, prior to weaponization (Tags: #seo-poisoning, #malvertising).

