'Hunting the Gorgon': Silent Push uses web panel data, Telegram, and ASN info to map out Meduza Stealer C2 infrastructure.

Key points
- Silent Push Threat Analysts uncover 100+ Meduza Stealer MaaS web panels.
- Web content data targeted to map out active C2 infrastructure.
- ASN analysis validates dual operating model across hosting providers.
- Meduza Telegram channel used to map releases to IOFAs.
In December 2023, whilst researching an unrelated threat campaign, Silent Push analysts discovered numerous domains and IP addresses linked to the Meduza infostealer network, which is reportedly being used by the hacker collective Scattered Spider.
In this blog, we’ll explore how our analysts took a single piece of page data, and used the Silent Push Web Scanner and the group’s own Telegram account to map out 100+ Indicators of Future Attack (IOFA) in the form of Meduza Stealer MaaS control panels, over a dozen of which are still active.
Background
The Meduza Stealer first appeared for purchase on a Russian-speaking darkweb forum in June 2023. Written in C++ and around 600kb in size, the malware quickly gained popularity in among cybercriminals for its originality, adaptability and competitive pricing model compared to other infostealers.
Named after its creator’s handle – “Meduza” – the malware infects Windows system files and steals sensitive information, including cookies, login credentials, and data from browser extensions such as password managers, 2FA services and cryptocurrency wallets.
Meduza Stealer reads the geolocation of the host machine and terminates if the machine is located in any of the following countries:
- Armenia
- Belarus
- Georgia
- Kazakhstan
- Kyrgyzstan
- Moldova
- Russia
- Tajikistan
- Turkmenistan
- Uzbekistan
Once it’s decided to proceed with an attack, the executable establishes a connection with an active C2 server, and proceeds with data exfiltration. Data is packaged and sent to the C2 server, before terminating on the host machine.
Meduza possesses a unique ability to evade standard AV detection protocols. Most popular antivirus suites aren’t able to detect the malware using dynamic or static analysis – either within a sandbox environment, or by interrogating its file structure, code or metadata.
Malware-as-a-Service
Meduza’s operators understand the importance of differentiating their “product” from the competition. The malware contains numerous features that set it apart from other executables available for purchase on the darkweb, under the Malware-as-a-Service (MaaS) model – including binary editing, an enhanced web-based GUI, and frictionless access to exfiltrated data.
In addition to underground forums, Meduza’s administrators also run a Russian language Telegram channel that they use to promote the malware, which reads like standard SaaS marketing material. More on this later on.
Gone are the days of “one and done” malware executables that act in isolation, without the benefit of a dedicated team to develop new iterations. Meduza’s operators have their finger on the pulse of the burgeoning MaaS market – a criminal enterprise model that is only a few years old, but is without a doubt here to stay. They know what their users want, they’re willing to interact with them, and they deliver improvements.
Meduza Stealer web hosting
So…. you’re a cybercriminal. Meduza’s operators have convinced you to part with your not-so-hard-earned cryptocurrency for access to their shiny new infostealer.
What happens now?
Upon subscribing, the “end criminal” can either host a Meduza web control panel using their own infrastructure, or rent a server from the malware’s operators.
This dual operating model helps us to understand patterns in ASN distribution, when analyzing the geographic spread of Meduza control panels:
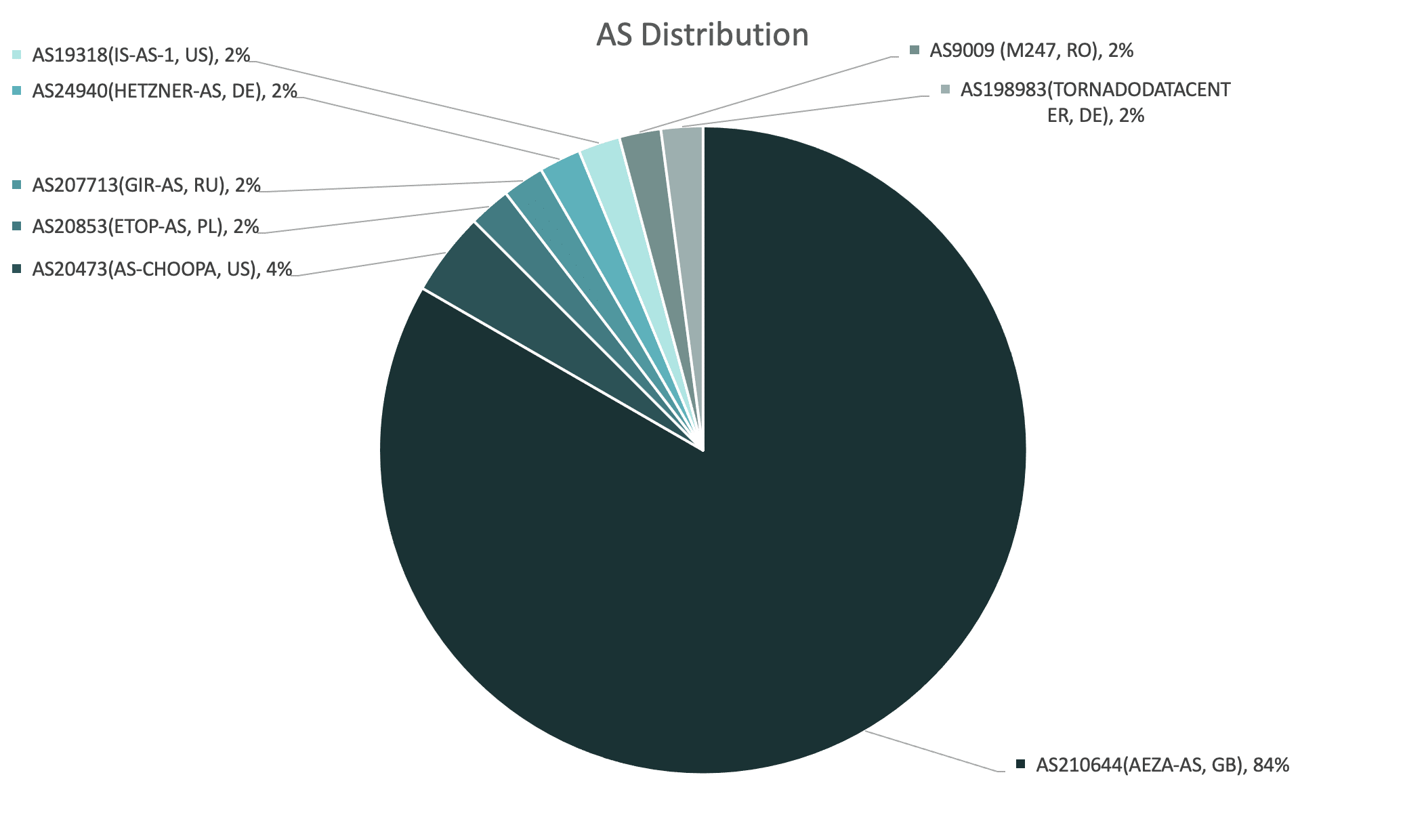
The majority of web panels are hosted via the Russian hosting provider, Aéza, recently cited by Spamhaus for their involvement with C2 botnets. It’s safe to assume that Aéza is the preferred hosting provider among Meduza’s administrators – either for their own exploits, or as an out-of-the-box option for their MaaS customers.
Here’s a list of other ASN providers that we’ve tagged to Meduza infrastructure:
AS20473(AS-CHOOPA, US)AS20853(ETOP-AS, PL)AS207713(GIR-AS, RU)AS24940(HETZNER-AS, DE)AS19318(IS-AS-1, US)AS9009(M247, RO)AS198983(TORNADODATACENTER, DE)
Hunting Meduza Stealer web infrastructure
N.B: For security reasons, throughout this report specific query parameters and result sets have been redacted. Silent Push Enterprise users are able to access a TLP Amber report within the platform that contains links to granular queries and the relevant data fields that facilitate discovery of Meduza infrastructure.
During the 2023 Christmas period our scans started to pick up IPv4 addresses and domains linked to Meduza Stealer, through various content elements.
We followed-up by executing a query using the Silent Push Web Scanner that revealed additional domains with matching content.
| Domain/IP address | First Seen | Last Seen |
|---|---|---|
5.182.86.32 | 2023-12-30 | 2023-12-31 |
77.105.146.152 | 2023-12-30 | 2023-12-31 |
79.137.194.188 | 2023-12-28 | 2023-12-30 |
ii.nggg.fun | 2023-12-25 | 2023-12-25 |
Pivoting on web content data
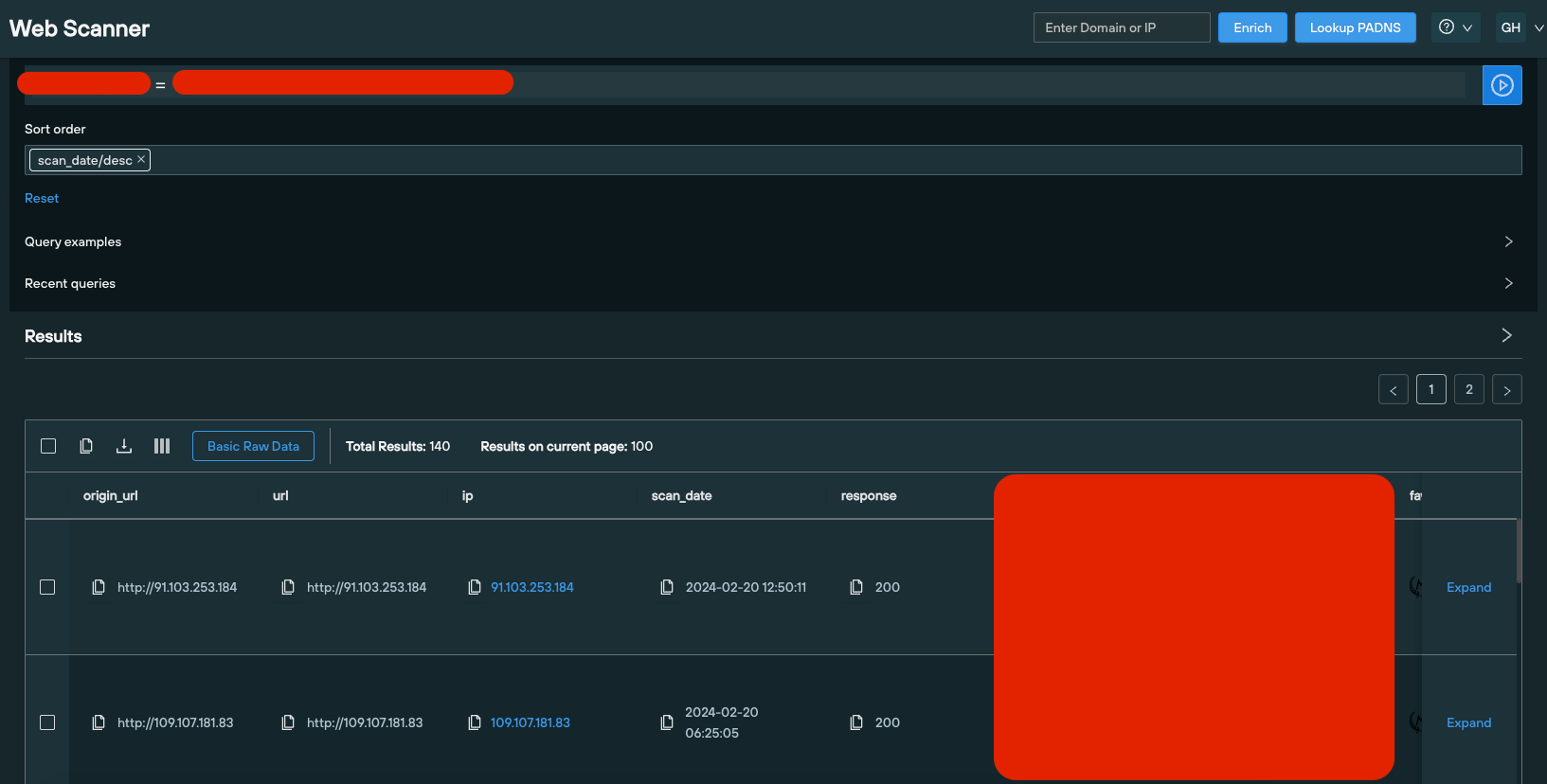
After analyzing the full set of content scanning results, we noticed that all the domains and IPs in the dataset shared a common denominator in the source code of the page.
We executed a content similarity check and uncovered 20 domains and IPs hosting a Meduza control panel, all of them first seen on or after the 23 December 2023:
Corroborating Meduza Stealer datasets
Our analysts also noticed that, from the initial dataset, two IOFAs – 5.182.86[.]32 and ii.nggg[.]fun – both featured matching web content which had changed into a different value.
Further scans on separate elements of the page unearthed 70 domains and IPs hosting Meduza content, scanned since August 8th 2023, with content values that matched the above control panels.
Using Telegram to correlate results
Meduza’s operators use Telegram to communicate malware updates to their user base. This presents an additional layer of intelligence for threat hunters who are able to corroborate announcements with changes in key data types.
While browsing through Meduza’s Telegram channel, we noticed a message from the operators, sent to the group on Christmas Day 2023, announcing a new version of the stealer with a range of bug fixes and updates to Meduza’s build and control panel, including:
- Support for targeting browser-based cryptowallets
- Bug tracking
- Expanded local storage exfiltration

By comparing Silent Push Web Scanner results with Meduza’s release timeline, and analyzing different versions of Meduza’s GUI side-by-side, our analysts quickly established that key content values changed in accordance with updates to the web panel communicated in version 2.x.

Hunting for active Meduza Stealer infrastructure
Our scans have uncovered over a hundred IP addresses and domains that have hosted a Meduza web panel, dating back to August 2023. Of these, a dozen are still active, suggesting that the group purposefully discard elements of their infrastructure to evade detection.
With this in mind, security teams need to target the group’s TTPs and use of web infrastructure, rather than relying on legacy IOCs that are rendered useless after a short space of time.
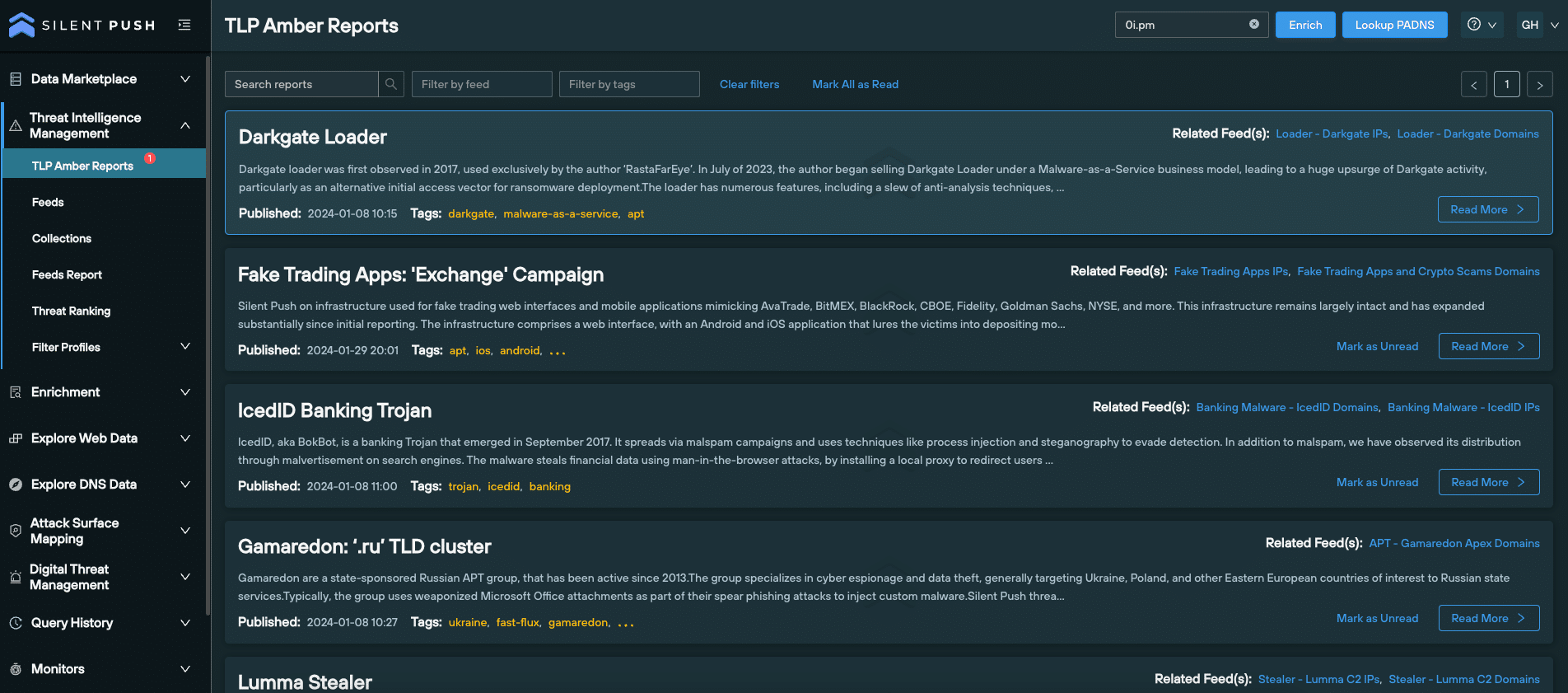
Silent Push Enterprise users benefit from two curated Early Detection Feeds containing historic and active Meduza control panels:
Enterprise users also have access to a TLP Amber report that explains how to uncover Meduza infrastructure, with links to Web Scanner queries, the content data fields we’ve targeted and mitigation actions that instruct security teams on the actions required to counteract Meduza TTPs.
Register for Community Edition
All of the queries and lookups we used to map out Meduza’s C2 infrastructure, including Web Scanner, are available as part of a Silent Push Community Edition – a free threat hunting and cyber defense platform featuring a huge range of advanced offensive and defensive lookups, web content queries, and enriched data types.
A full list of domains, IPs, ASNs and content values are available to Enterprise users in the above Early Detection Feeds and TLP Amber report.
Click the button below to sign-up for a free Community Edition account.

