Background
An open redirect vulnerability takes place when attackers construct a URL within an application that triggers a redirection to an arbitrary external domain, such as a phishing site.
Open redirect techniques often feature in phishing emails but a new run of attacks has refined the approach by abusing legitimate domains like citi[.]com and performing multiple hops in the redirection process.
M365 login page spoofing
Silent Push has been tracking different phishing campaigns spoofing M365 login pages as final phishing pages to target enterprise users. Some of these campaigns have attempted to target our staff members as well.
Threat actors use images that impersonate notifications from Microsoft, to lure users into clicking hyperlinks embedded in image files.
We’ve observed that attackers often use legitimate websites to redirect to threat actor-controlled intermediate ‘cushion servers’, which lead to the final phishing URLs with fake Microsoft logins.
In one of the cases we investigated, the phishing emails used an ‘Undelivered Mails’ lure that prompted users to click on “Release My Messages”, triggering a series of HTTP and Javascript redirects:

Phishing email received with “Undelivered Mails” lure.
Attacker infrastructure
To evade security solutions, threat actors use legitimate domains as an initial redirect setup. In this case, the first URL uses a subdomain from a legitimate Fortune 500 domain to use a 302 redirect to an intermediate URL hosted on frudyj.codesandbox[.]io:
From enrichment information stored in our app, we get the following details about the IP:
ASN: ASN-CHEETA-MAIL, US
Header Server: BigIP
From the HTTP server header and the cookies, we can see that the BIG-IP service is in use.
In February 2023 the BIG-IP vulnerability CVE-2023-22418 was reported about virtual servers enabled with the BIG-IP AIM access policy allowing attackers to build an open redirect URL. It is possible that the vulnerability was abused in this case to redirect to an intermediate domain.
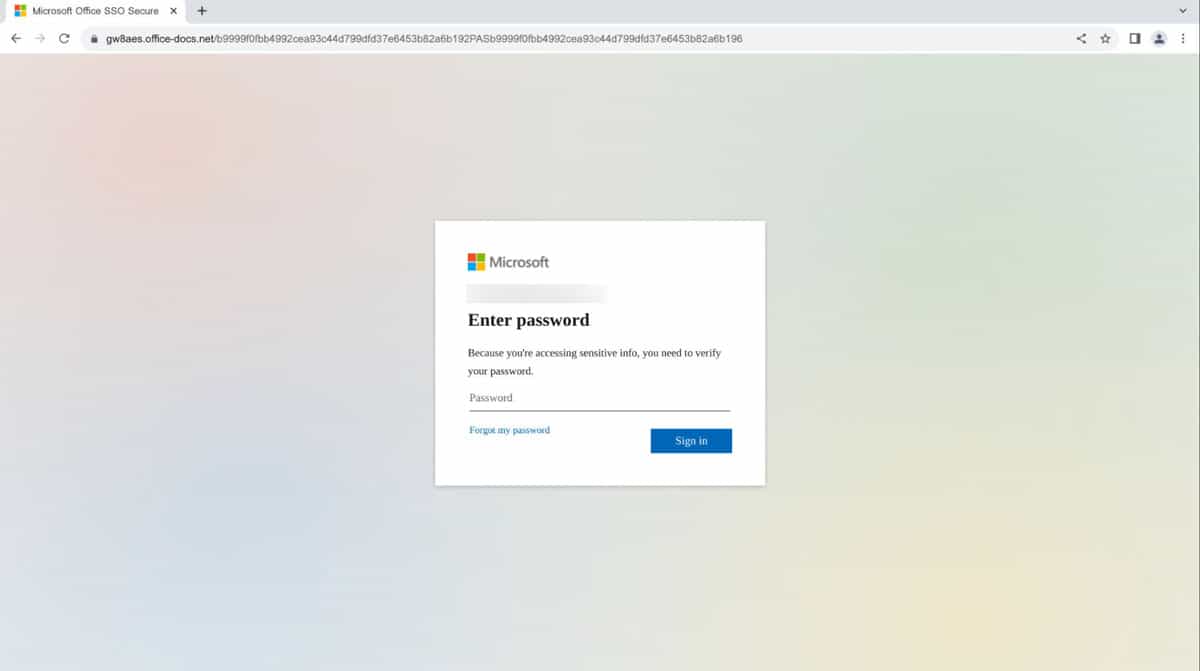
The second redirect occurs when the URL hosted on “frudyj.codesandbox[.]io” uses ‘windows.location.replace’ within its Javascript response to redirect to a phishing page hosted on “gw8aes.office-docs[.]net”:

windows.location.replace function used to redirect to phishing domain
By adding an additional redirect server, threat actors ensure that the phishing domain is not visible via preliminary URL analysis of security solutions, using blacklists for known phishing domains.
The final phishing infrastructure is hosted on the Cloudflare nameserver space, and ASNs with registrar ‘NICENIC INTERNATIONAL GROUP CO., LIMITED’.
To evade sandbox analysis, the phishing URL attempts to validate human interaction by using CAPTCHA services before loading the actual phishing content.

CAPTCHA verification to evade Sandbox environment

Final phishing page, post CAPTCHA
Using registrar and ASN information, along with keywords typical for M365 domains, we can identify more IOCs linked to this variant of the campaign, some of which are still loading similar CAPTCHA and phishing pages at the time of writing.
Neighbouring campaigns
We’ve been tracking a similar Microsoft notification spoofing campaign using the Cloudflare CDN service.
The campaign was first observed in early 2023 and seen using domains registered at the Russian registrar ‘R01-RU’ with ‘.ru’ TLDs and using the Cloudflare CDN. The campaign was first noted on Twitter on January 10:

Twitter message by @dllhijack
Investigations into the infrastructure revealed a pattern of ‘.ru’ TLD domains involved in similar phishing campaigns.
Each domain registers multiple subdomains with a 23-character random alphanumeric prefix used.
Phishing operators continue to choose from a pool of subdomains registered against each domain. Silent Push Enterprise customers remain protected as we map out the length and breadth of the attackers’ infrastructure.
While initially loading without CAPTCHAs, all of the recent iterations include similar checks before loading the phishing page:

subdomain from newfiles[.]ru loading showing CAPTCHA at access
Active campaigns using other infrastructure
We’ve been tracking another active campaign hosted on different infrastructure. Similar phishing lures are used through fake Microsoft notification emails:

Microsoft-themed spoof email using Quarantine Messages lure
The above email sample consists of URL from ‘r20.rs6[.]net/tn.jsp?f=001Uz_oasaa6a5lC37PPsB9z-ZgFhC1pGp9pnfq5i9xZtMr96zXrdKn8CQ58mxOBMHls4KIJEKQYKrQLyGkOHCRdhGHDbs4LbL1gJtM7fltrQaLHqyvPgU2KFr-8phP57bDerZR8leLarR6I9RLnaPQWwm4st97ysy8PS4QDUFp0RUz8i3kKSJWR5EpJgGZl_FrFM-GZz-8rNqTXqkMoLRu4g==&c=FMZVwwhlSnT_R6bt1c-Rusd1q6UoQpgXeh7JNVlfAOelVYnB7At6tQ==&ch=I9P2kmoojtJjpthS-pAffdBgRQXjoCrnpX91-blhUzm_QvuiI-ireQ==&__=?VGLn==’ eventually leading to www;.fixedrepo365[.]art/main.
In this case, the user is also directed to an initial CAPTCHA:

Figure 9 CAPTCHA check on phishing domain if redirected from email URL
If the URL is accessed directly, the user is redirected to a benign office[.]com page.
Threat actors are likely tracking the correct redirection path to load, based on the input it expects to receive from the previous redirected URL from domain r6[.]net.
The URL consists of a 64 bit encoded string at the end of the URL shared earlier (mentioned as for security reasons). In the path where it does get a proper redirection with email address input, once the user verifies the above CAPTCHA likely put up to evade sandboxes, the phishing domain opens a URL with the fake Microsoft SSO login page:

Fake MS Login page
This type of evasion and the CAPTCHA check are mentioned by Microsoft in their finding about the distribution of ‘AiTM Phish kits’. It appears as though threat actors continue to successfully deploy the technique with new domains and new infrastructure.
The phishing domain in this case (ww-wfixedrepo365[.]art) is using dnsowl[.]com nameserver and NameSilo registrar. By investigating the infrastructure, we were able to identify other IPs, i.e. 37.120.234[.]53, 209.141.60[.]219 and domains using Microsoft and Office-themed keywords in their name.

Phishing infrastructure on 37.120.234[.]53

Phishing infrastructure hosted on 209.141.60[.]219
The complete domain IOC list is available to our enterprise customers.
Conclusion
Phishing attacks continue to pose major security risks to organizations of all shapes and sizes. Threat actors are continually adopting new evasion techniques to improve success rates and avoid detection from security vendors, through multiple layers of legitimate redirections, CAPTCHA verifications, and cloaking final URLs.
Silent Push uses enriched threat intelligence and a variety of early detection tools to capture campaign IoCs at source, across a broad range of TTPs, and combat attacker infrastructure before its weaponized.
The contents of this report were uncovered using the Silent Push platform.
Sign up for our free Community App to take advantage of our vast array of threat defense tools.
IOCs
Below is a partial list of IOCs related to the campaign. The full list is accessible to enterprise subscribers of the Silent Push App as part of our threat intel feeds.
IPs
37.120.234[.]53
209.141.60[.]219
Domains
0fvt5.office-docs[.]net
0fvtdvewpt63bb226806dd5.newmaild[.]ru
3lluyhieun63f4d2670a18d.elitbot[.]ru
4d9kl5a7ub6408fba331e98.newfiles[.]ru
4pn2n.dnnfiles[.]com
8w8l.docsteams[.]com
9oxe1.onlinedocsview[.]com
gw8aes.office-docs[.]net
ww-wfixedrepo365[.]art
ww-wmix365leds[.]art