Performing a passive DNS lookup (PADNS) allows security teams to collect, analyze and share historical DNS data. Unlike traditional DNS which actively queries servers to translate domain names into IP addresses, passive DNS stores this information over time, creating a searchable historical record of how domains and IP addresses are associated with each other across the global IP space.
A ‘forward’ passive DNS lookup uses a domain or server name as the input parameter and returns an IP address as the ‘answer’, whereas a ‘reverse’ lookup uses an IP address to return a domain or server address.
Passive DNS lookups are the bread and butter of most threat hunting and cyber defense activities. There are, however, several challenges that security teams need to overcome when dealing with DNS records as pieces of digital infrastructure. These range from an over-reliance on incomplete and outdated datasets, to sorting through mountains of DNS records – particularly within enterprise organizations – to produce actionable intelligence.
Silent Push’s passive DNS lookup functionality allows you to perform a deep dive into enriched intelligence datasets, bolstering your cyber defenses, and uncovering emerging threats before they become a problem using a first-party dataset that’s uniquely designed to create searchable spaces related to specific DNS attack vectors.
Summary
In this blog, we’ll delve into different DNS record types, the role they play in the world of cyber threat intelligence, and how to maximise the Silent Push ‘Explore DNS Data’ feature to generate proactive threat intelligence. We’ll then discuss the outcome-focused tools available to you that make the most out of your organization’s passive DNS lookups, including pivoting on datapoints, monitoring results and more advanced query sets.
Understanding DNS record types
Attackers target different DNS record types using a variety of techniques to silently slip past an organization’s security measures. This makes it all the more important for security teams to diversify their defence mechanisms across multiple record types, encompassing their entire attack surface.
Let’s take a look at a selection of common DNS record types, and how attackers seek to exploit them…
A records
A records map a domain name to an IPv4 address. Passive A record lookups help analysts detail any IP addresses associated with a given domain name, detect changes in DNS activity, and associate domains and IPs with a specific threat campaign.
A records play a central role in the cat and mouse game of cyber attack and defense. Adversaries view A records as low hanging fruit, using them to propagate all manner of assaults on a public DNS presence, from domain hijacking, to typosquatting and email spoofing.
CNAME record
A Canonical Name (CNAME) record acts as an alias for another domain name, in lieu of a subdomain. You can’t use a CNAME record to point directly to an IP address – they’re used to map subdomains (such as www.) to apex domains (silentpush.com).
Attackers often use CNAME records when attempting a subdomain takeover – a DNS hijacking technique that can end up with an adversary obtaining access to an organization’s entire public DNS presence.
MX records
Mail Exchanger (MX) records identify which server is responsible for handling emails for a particular domain. Threat actors exploit MX records when propagating DMARC and email spoofing attacks, which involve an attacker making it appear as though an email has originated from a trusted source, when it’s actually been sent by the threat actor themselves.
Nameserver records
Nameserver (NS) records identify the authoritative DNS servers for a domain. NS records are particularly useful when an analyst wants to identify and monitor changes to registrars, hosts, or organizations associated with a particular domain.
Threat actors create searchable patterns by using the same set of nameservers to carry out attacks. By querying NS records via a passive DNS lookup, security teams are able to ascertain the risk level of a domain name, evaluate the reputation score of the NS associated with it, and view how many times a domain has jumped between different NS.
TXT records
TXT records contain any textual information that the domain owner wants to include, such as email addresses, contact information, or security-related information. By manipulating TXT records associated with specific email authentication protocols such as SPF, DKIM, and DMARC, attackers can make fraudulent emails appear legitimate.
SOA records
Start of Authority (SOA) records provide information about the DNS zone in which a particular domain is located, and hold administrative information about the domain. When a change is made to a DNS zone, the SOA serial number is incremented, indicating that an amendment has occurred.
This allows other DNS servers to detect and propagate the change, ensuring that all DNS information is consistent and up-to-date. Subsequently, security teams are able to detect changes to DNS information that may indicate malicious activity, such as the creation of new subdomains or changes to the IP addresses associated with a domain.
Executing a passive DNS lookup
Silent Push allows you to perform powerful passive DNS lookups across a range of record types. Security teams are able to use the console to establish links between disparate records, uncover attacker infrastructure, and obtain granular information on a given domain or IP.
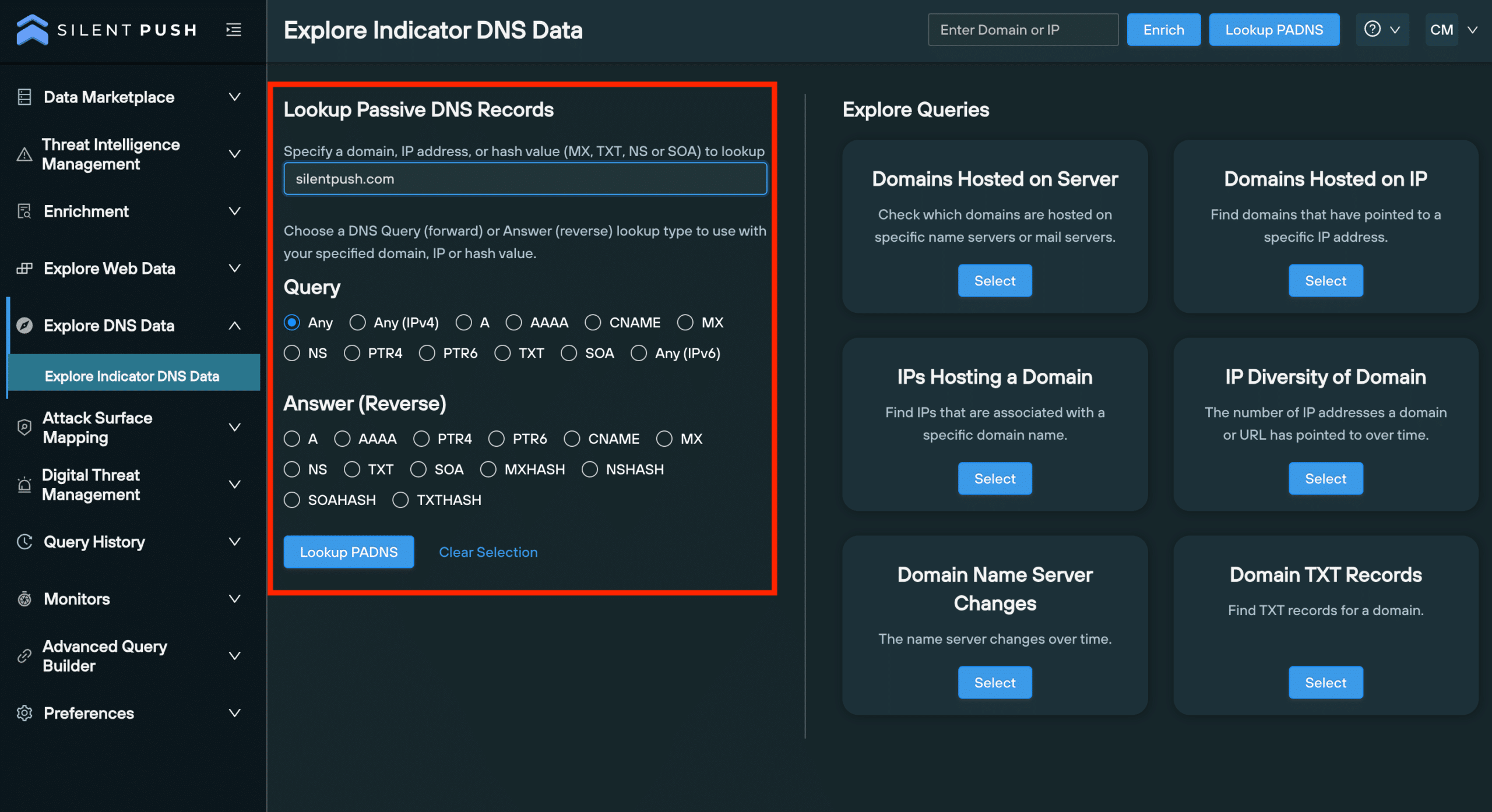
Passive DNS lookup interface
The ‘Explore Indicator DNS Data’ page allows you to perform forward and reverse PADNS lookups, and execute advanced queries, all within a single screen.
Forward and reverse lookups are performed on the ‘Explore Indicator DNS Data’ page, available to both Community and Enterprise users, for the following record types:
- A/AAAA
- CNAME
- MX
- NS
- PTR4/6
- SOA
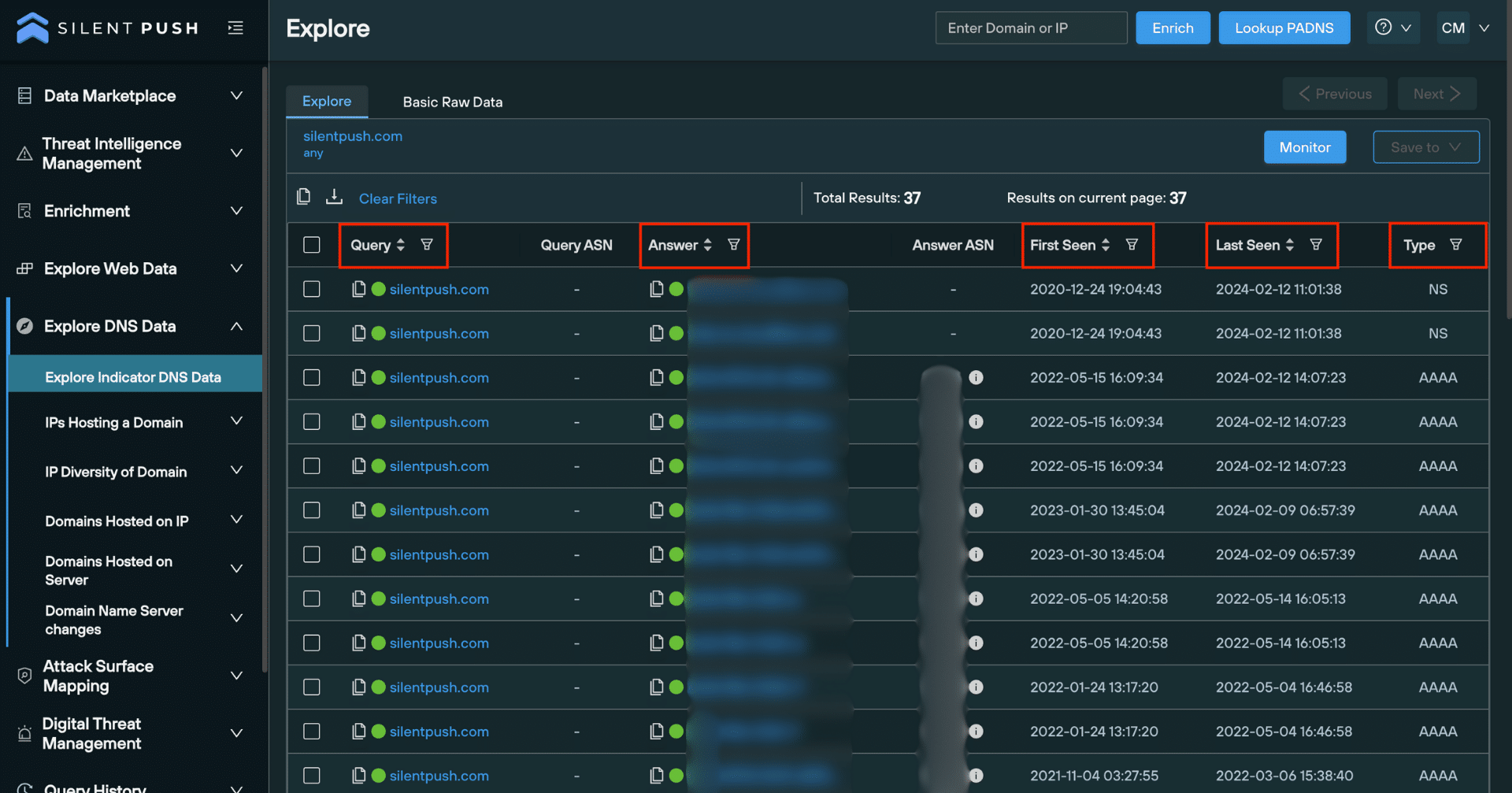
‘Explore’ table
Once you’ve executed a lookup, the Explore table populates results drawn from our first-party database that’s collected, clustered, scored and delivered without third-party intervention.
From here you can monitor and save observables to a feed, perform additional lookups on individual pieces of data, export raw data, obtain risk scores and enrich observables to gather further intelligence across 90+ categories, most of which are unique to Silent Push:
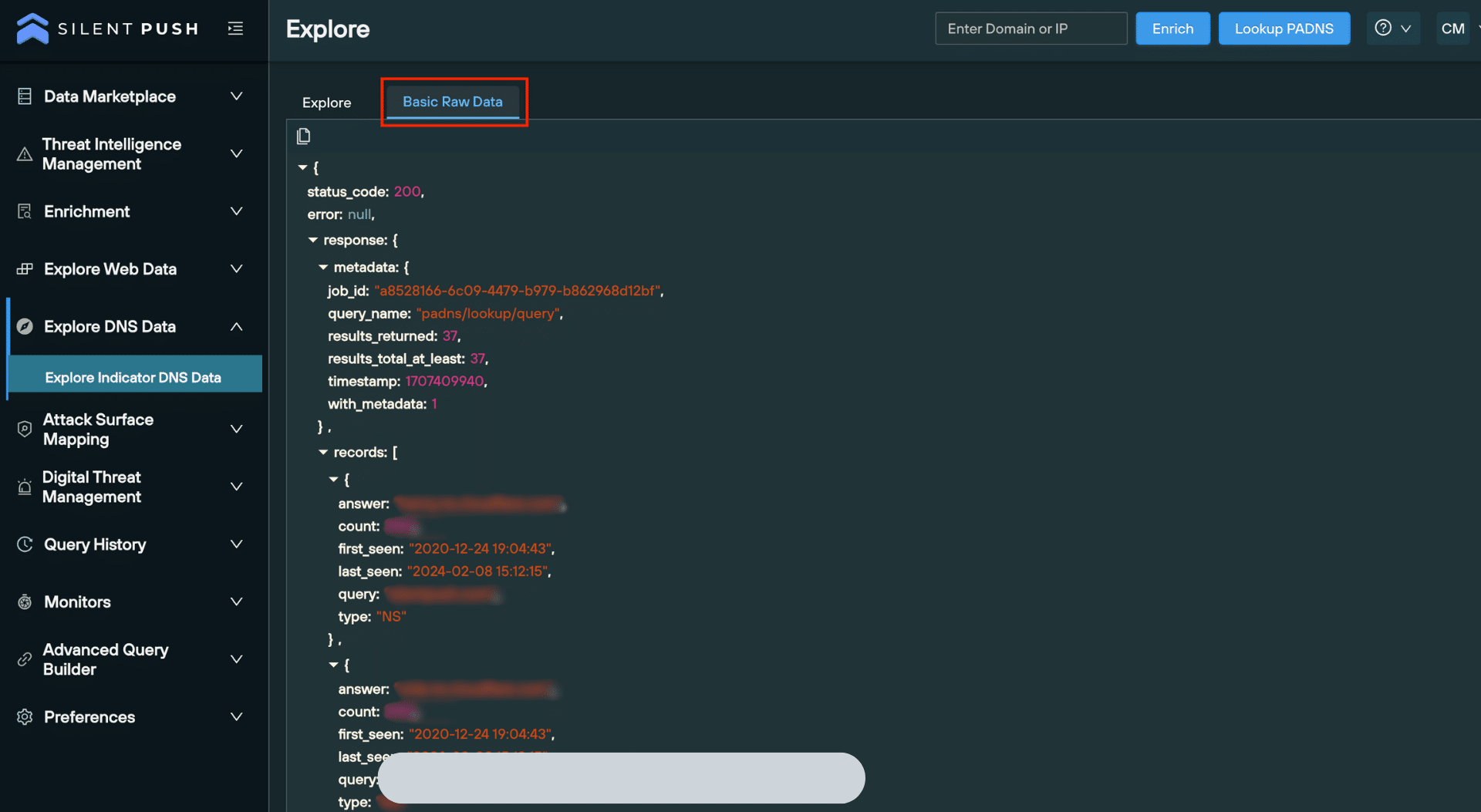
A secondary tab on the Explore screen allows you to view and copy the raw data, either for offline analysis or to facilitate integration with your security stack:
Utilizing results from a passive DNS lookup
Unlike other passive DNS lookup platforms that provide queries in isolation, Silent Push features outcome-focused screens that enable security teams to gather intelligence that can be accessed, saved, and shared in just a few clicks.
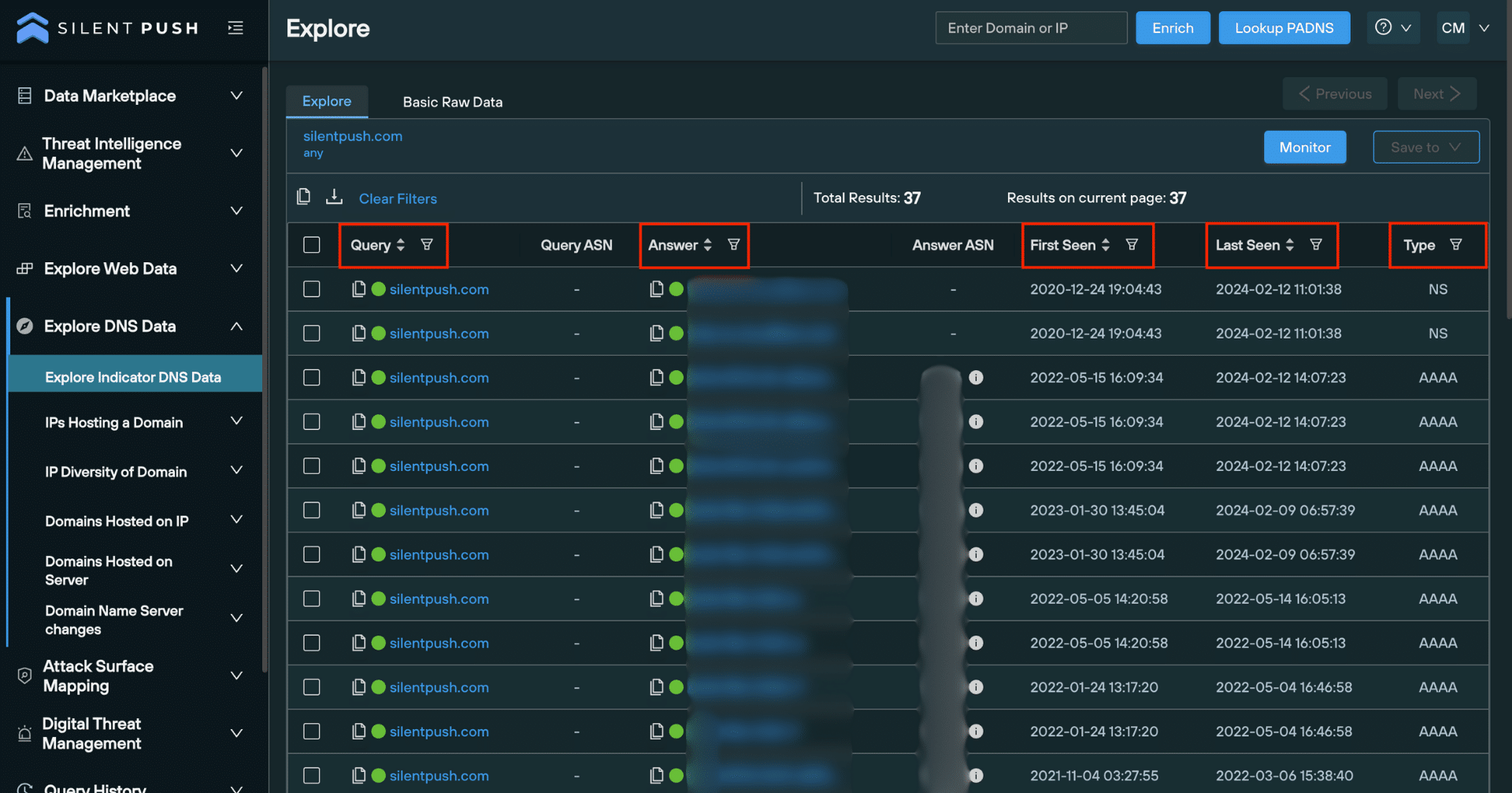
Filtering and searching through results
Filters help you sort data using a range of parameters, including:
- Domain
- IPv4 address
- First seen date (When an observable was first seen in the dataset).
- Last seen date (when an observable was last seen in the dataset).
- DNS record type
Filters can be accessed at the top of the Explore screen. You can also search through individual columns for specific pieces of data:
Pivoting on passive DNS data
‘Pivoting’ involves performing additional queries on a single piece of data, including forward and reverse lookups, and domain or IP Enrichment queries.
Pivoting allows you to unearth intelligence that reveals the origin, function and risk level of a piece of data across a range of categories and sub-categories.
Clicking on an observable opens a pop-up window, featuring a bank of lookups relevant to the data type:
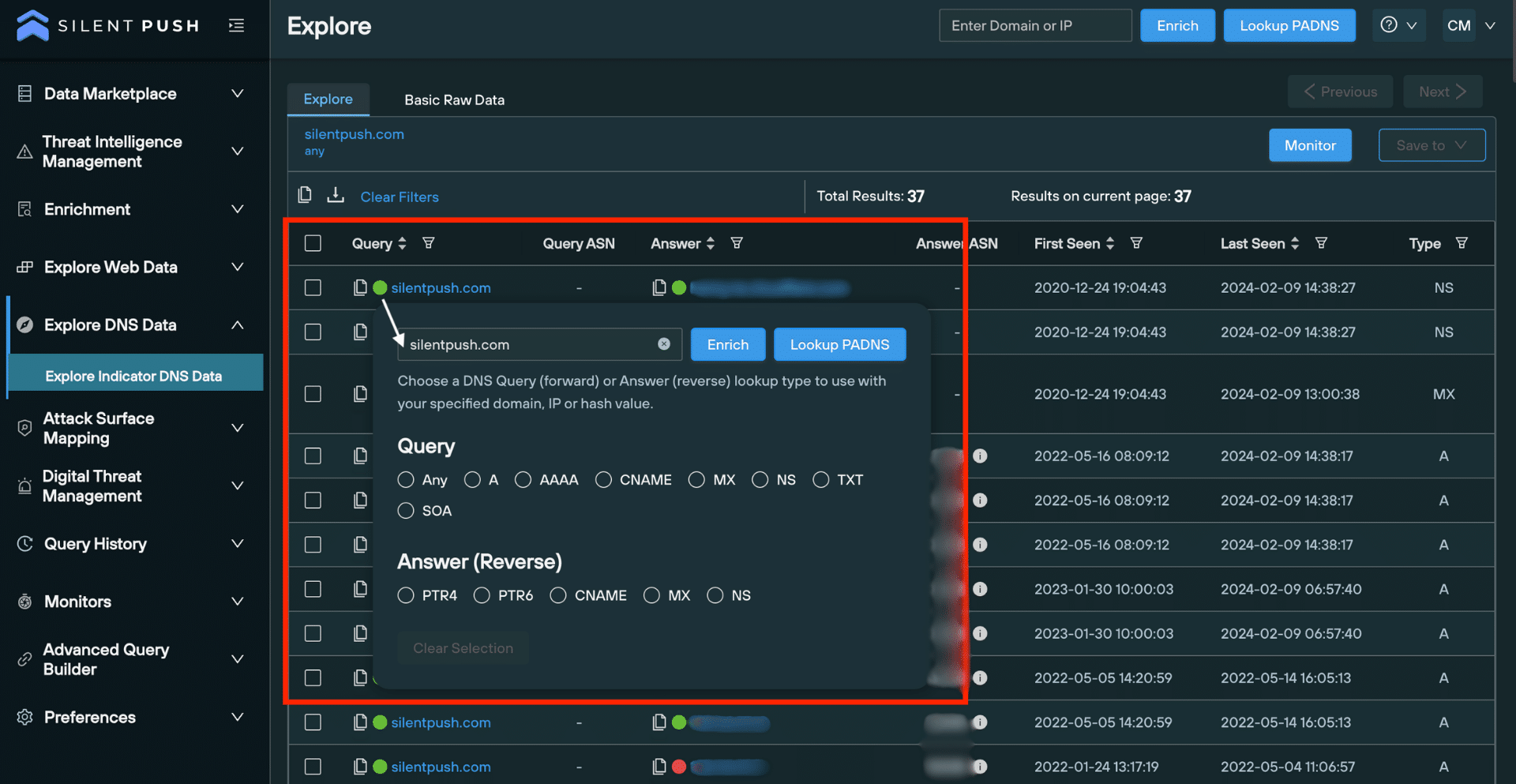
Monitoring a passive DNS lookup
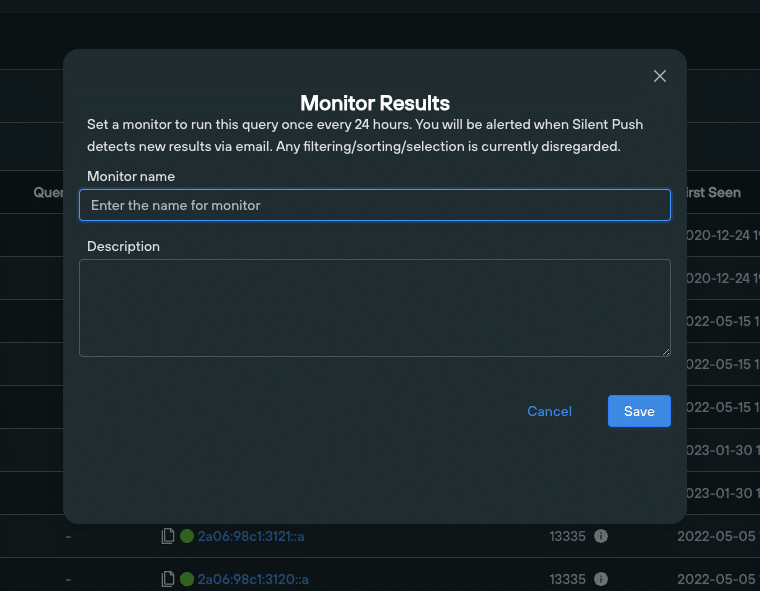
Once you’ve used a lookup to generate a set of results, you can enable ongoing monitoring that alerts you to changes in the dataset every 24 hours. By automating key queries across a range of internal workflows, security teams can save valuable time and resources, and eliminate repetitive tasks to focus on more pressing matters.
Clicking the ‘Monitor’ button on the top right of the Explore screen lets you assign a monitor to a set of results:
Saving and exporting passive DNS data
Critical to any security operation is the ability to share information amongst team members. You can save any piece of data – or even entire datasets – obtained from a passive DNS lookup either to an existing feed, or to a new feed, using a simple drop-down menu.
Feeds can be shared globally throughout your organization:

Passive DNS data can also be exported in raw format, as a JSON, or as a CSV:
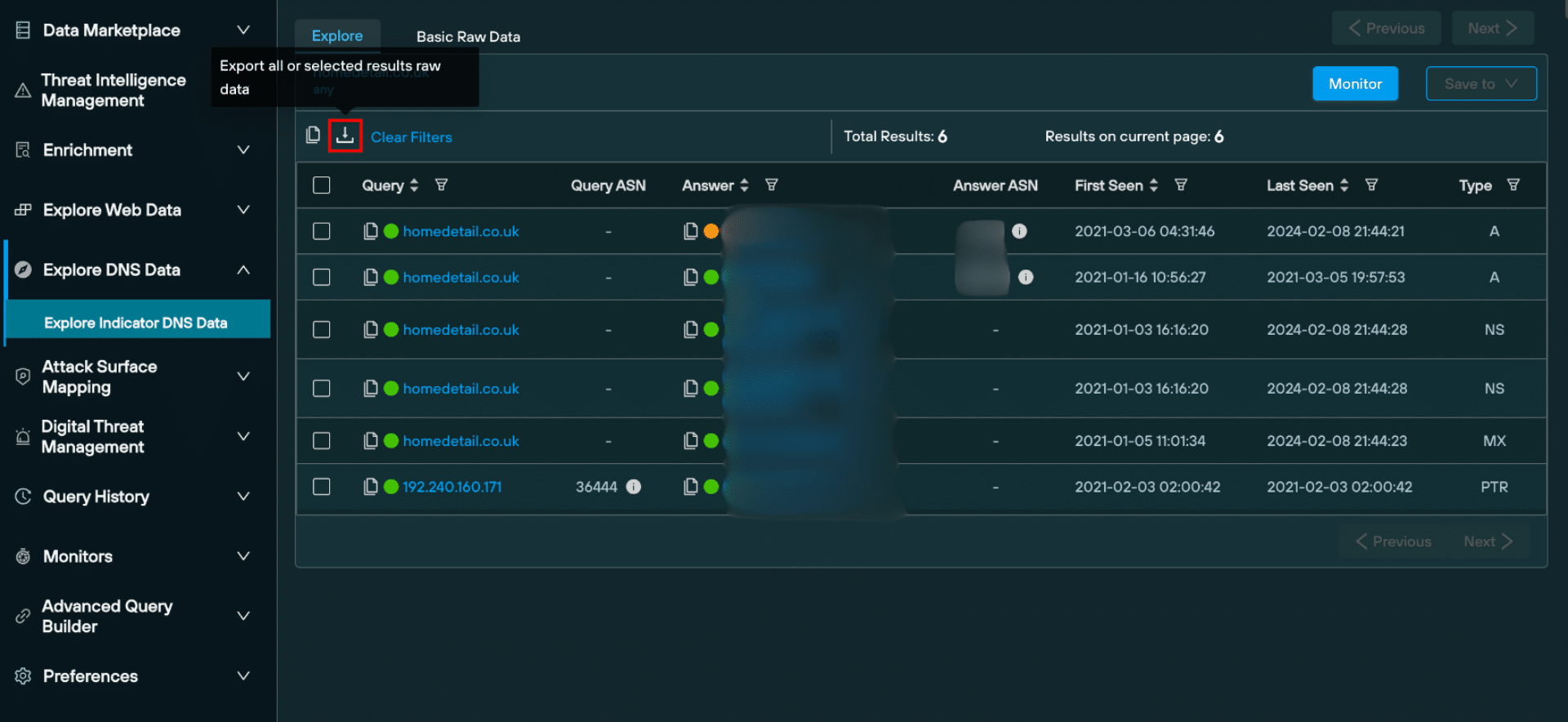
Advanced queries
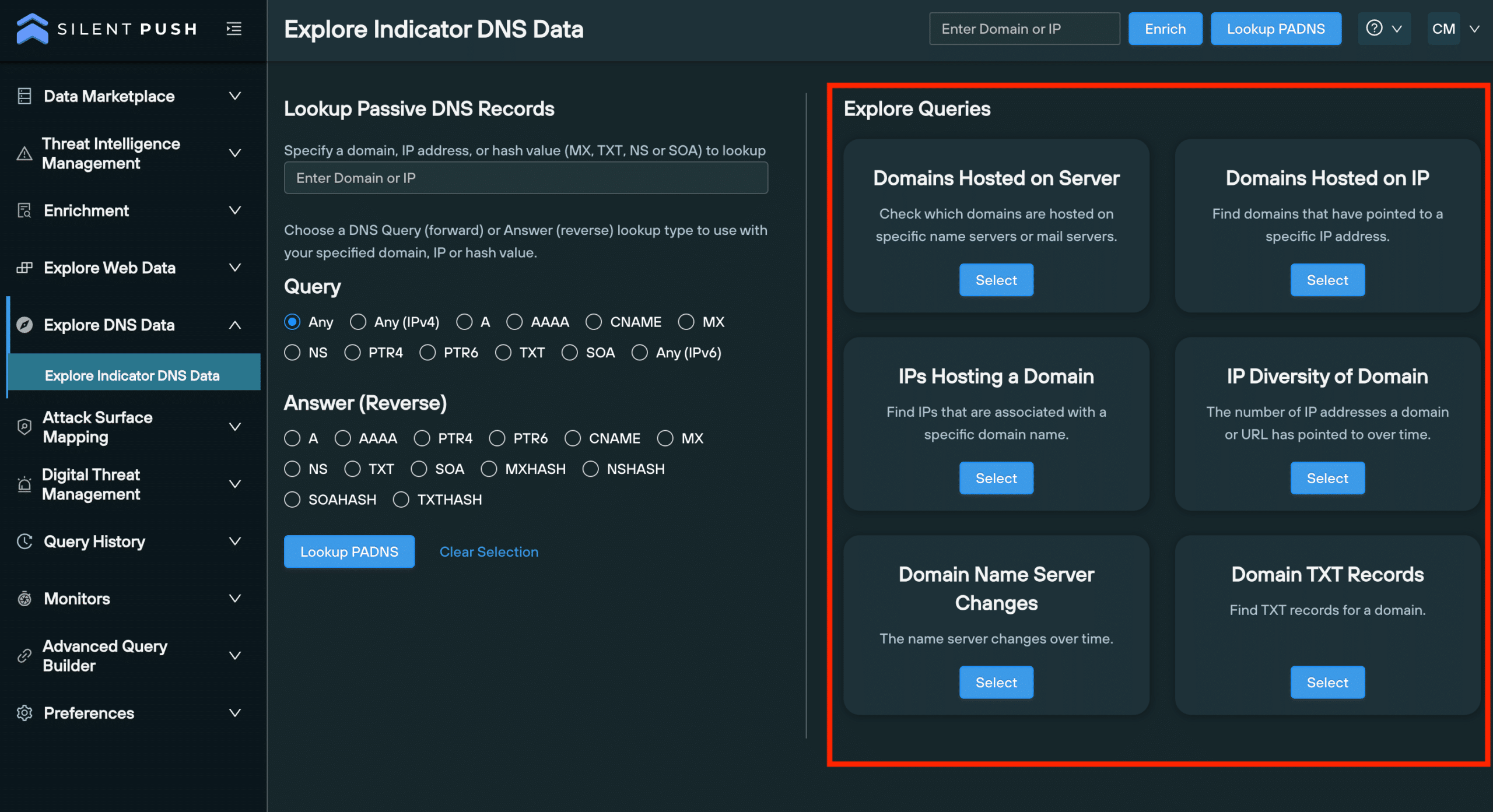
The ’Explore Queries’ menu features a range of advanced DNS queries that allow you to analyze the historical characteristics of a piece of data, including the relationship it has with other data types, and build a behavioural fingerprint of attacker TTPS, including:
- All domains hosted on specific server.
- All domains hosted on an IP address.
- IPs hosting a domain.
- The IP ‘diversity’ of domain (the number of unique IP addresses associated with a particular domain).
- Any nameserver changes.
- All TXT records associated with a domain.
Register for Silent Push Community Edition
Silent Push passive DNS lookups allow you to explore your organization’s and supply chain’s DNS presence in a more timely, accurate and detailed way, and hunt for malicious infrastructure before it’s weaponized.
Silent Push Community Edition is a free threat hunting and cyber defense tool used by security teams, threat analysts, and researchers that features a range of basic and advanced DNS queries which interrogate the Silent Push database, built from our daily scans of the Internet’s global IP range.
Click the button below to sign-up for a free account.


