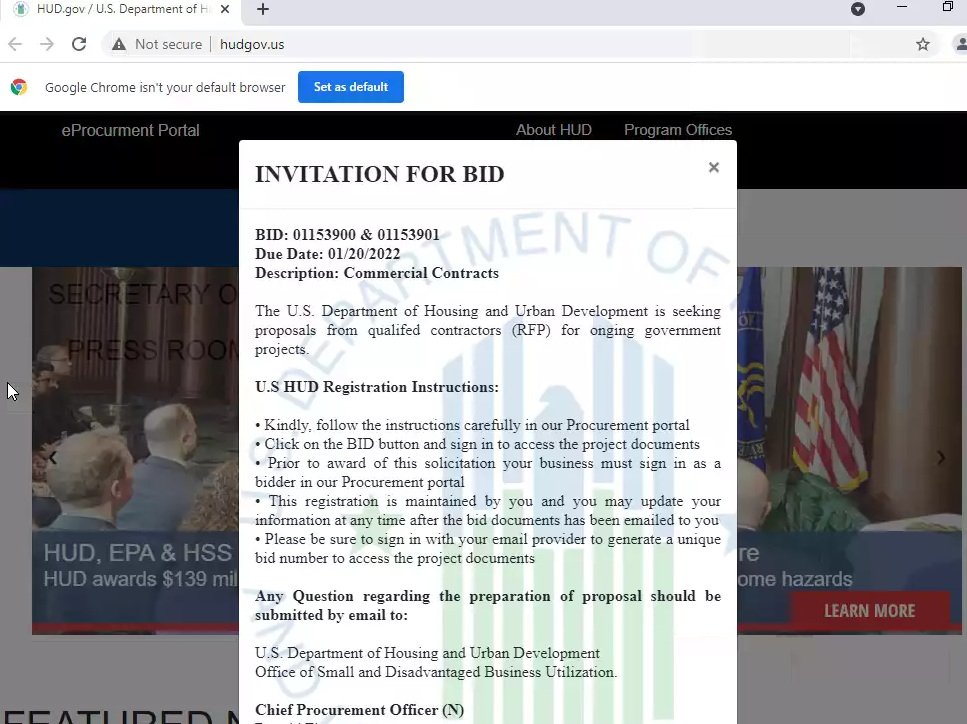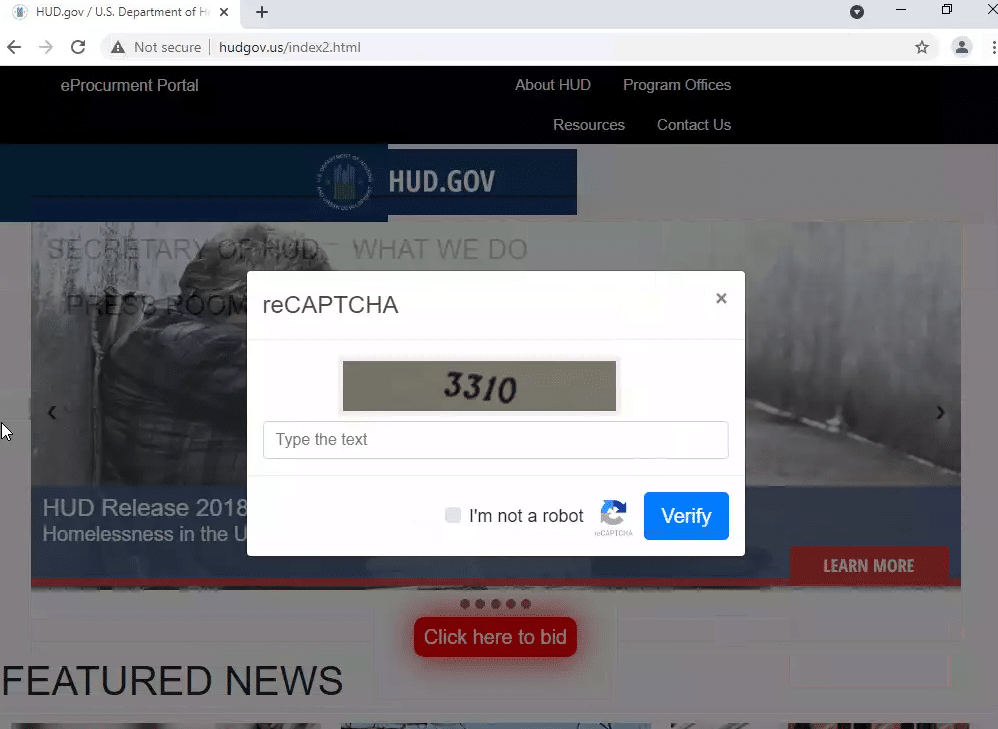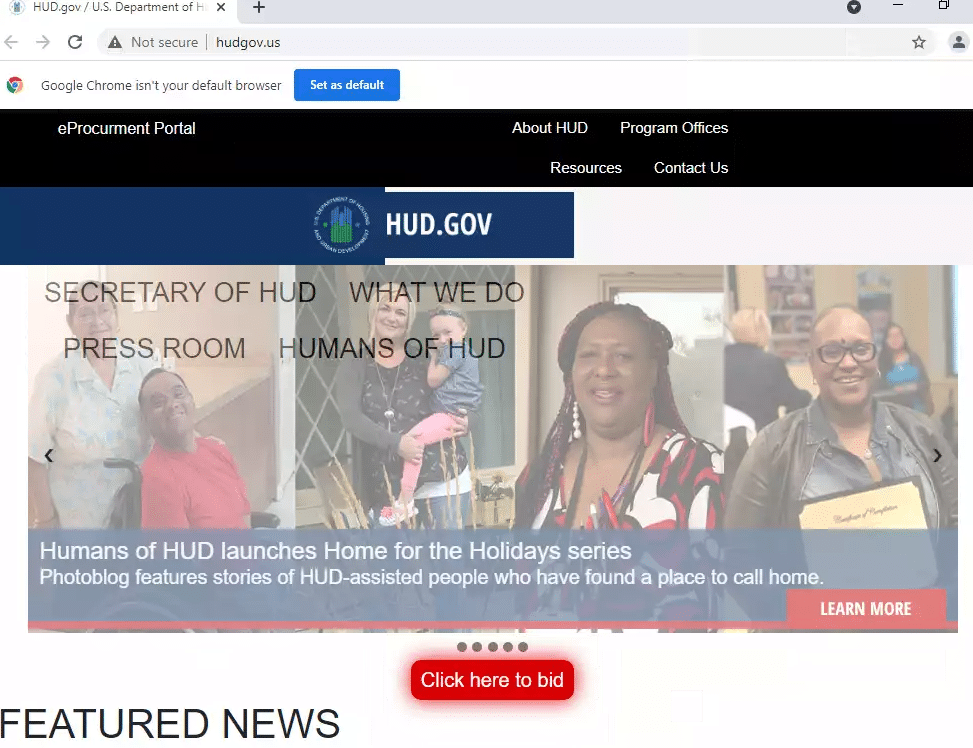
A few weeks ago, security company INKY wrote a blog post about a phishing campaign that used fake invites for the United States Department of Labor as a lure.
The phishing campaign may target a rather niche audience, but it’s not the first of its kind: in 2019, another security company looked into a phishing campaign that also targeted potential contractors for the US federal government, as well as some state and county governments.
INKY listed three domains created by the actors to send emails from:
dol-gov[.]com
dol-gov[.]us
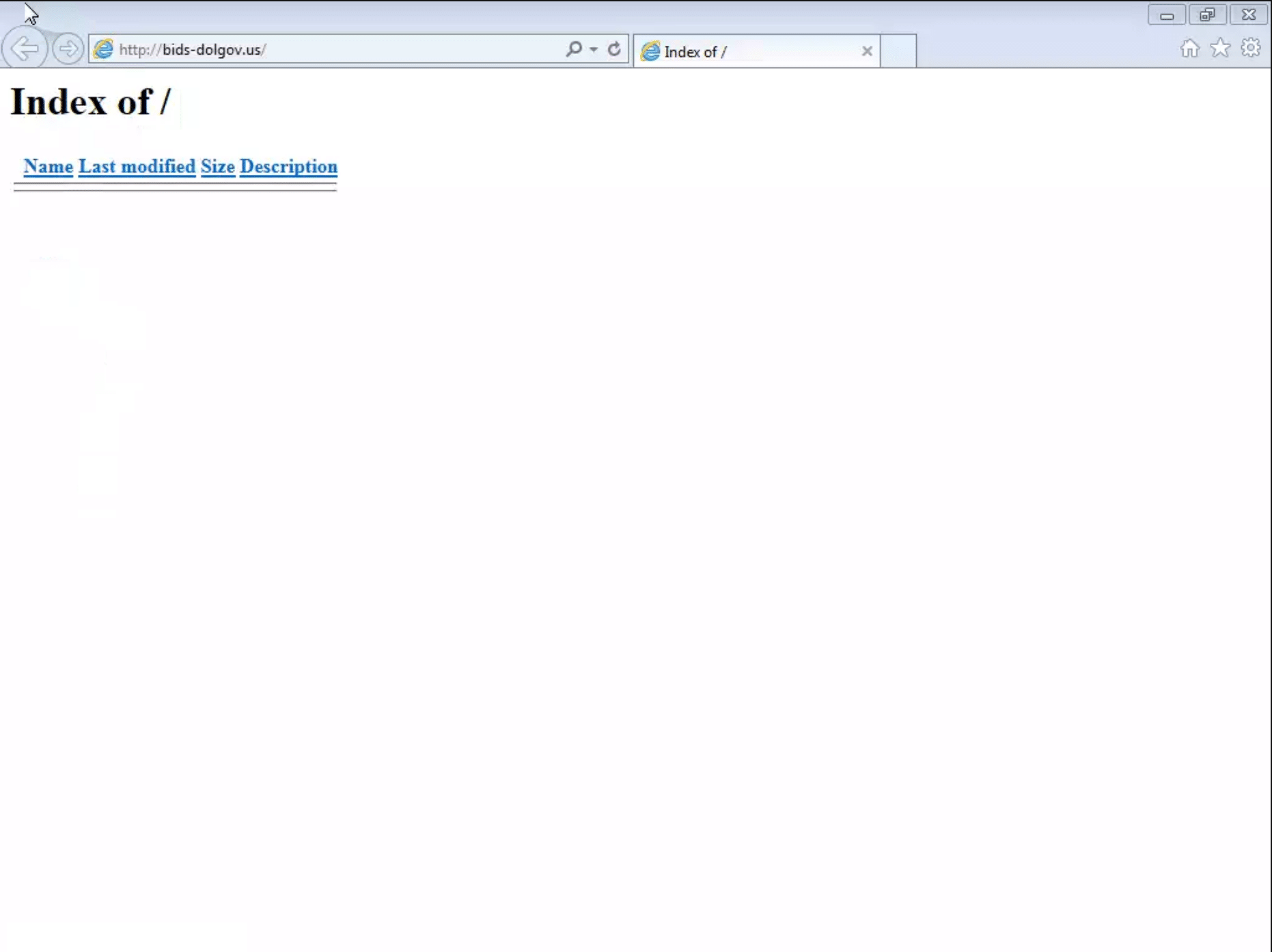
bids-dolgov[.]us
The first one points to a parking site, while the second expired in August last year. The last one, bids-dolgov[.]us, is still active. It uses the name server pair {ns1,ns2}.hugeservernow[.]com and the A record points to 23.29.117[.]114.
Opening the domain name in a web browser shows an empty index page, but it is of course possible that the domain was only used in emails and never intended to be opened in a browser.
Interestingly, both of the name servers point to the same IP address as the domain itself. This kind of set-up is something we see fairly often for malicious domains, especially in phishing campaigns, where domains don’t need to be active for a long time.
INKY’s blog post also lists twelve domains used as landing pages in the campaign. Five of these (bid-dolgov[.]us, openbid-dolgov[.]us, openbids-dolgov[.]com, openbids-dolgov[.]us and usdol-gov[.]com) use the same name server pair as above, while the other seven used Namecheap’s shared hosting. Only one in each group is still live; both show an admin panel for the YOURLS URL shortener:
We decided to investigate the name servers to see what else we could find.
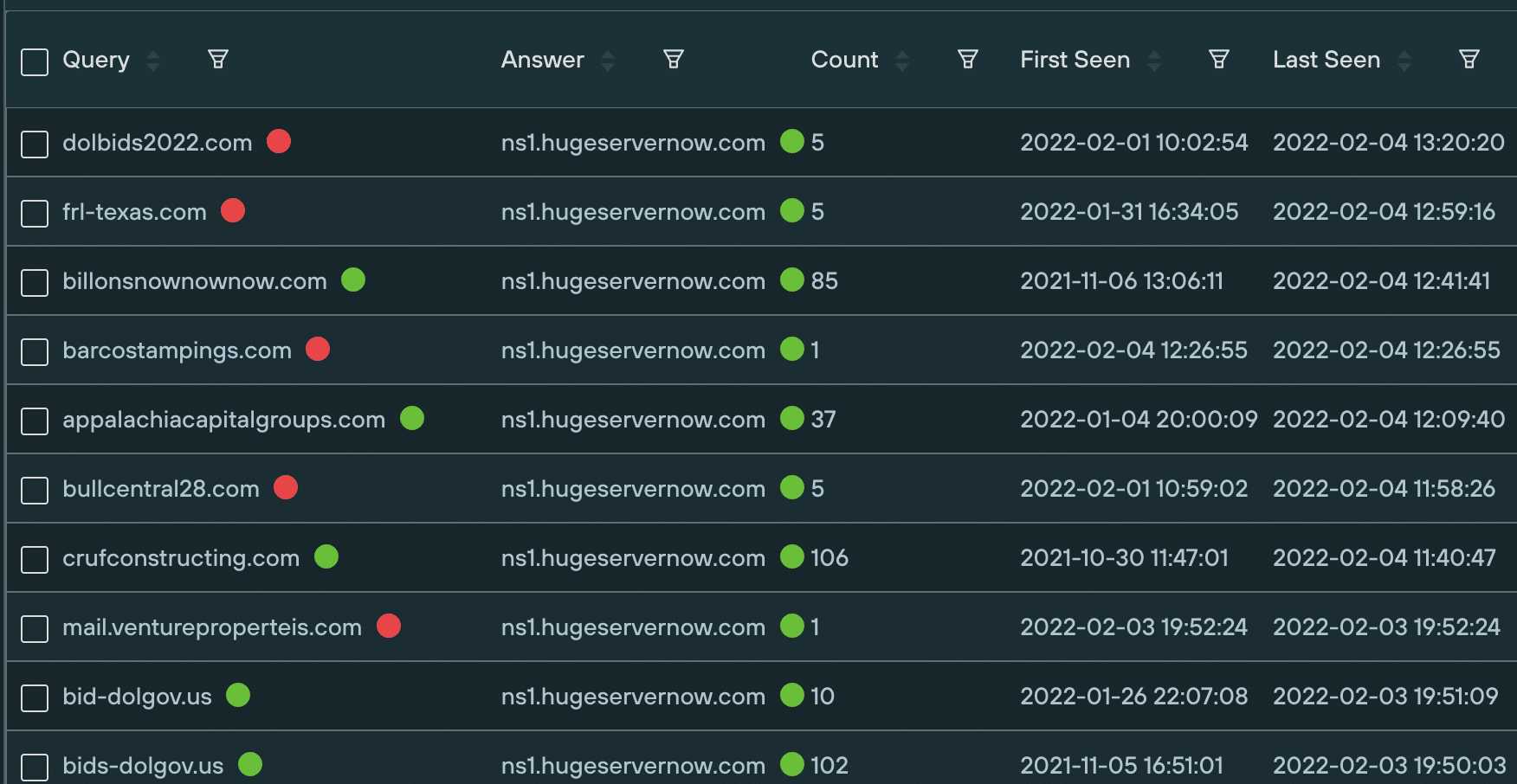
We immediately spotted the domain dolbids2022[.]com, registered only a few days ago, suggesting that the campaign continues to be active. The domain has an active MX record — also hosted on the same IP address — with an empty index page showing when opened in a browser.
It wasn’t the only one. The following six domains were also using the same name servers — though none are still live:
bids-dolgov[.]com
dolgov-bid[.]us
open-bidsdolgov[.]us
us-dolbids[.]com
us-dolgovbid[.]com
usgovbidsdolgov[.]us
We also found other US government departments being targeted, such as the Department of Commerce:
commerce-gov[.]net
doc-gov[.]us
and possibly also doc-link[.]digital though this may refer to another kind of ‘doc’.
The Department of Transport was also targeted:
bid-dot[.]us
bids-dot[.]us
departmentoftransportations[.]us
dot-bid[.]com
as was the Department of Housing and Urban Development:
bids-hud[.]us
hudgov[.]us
There is a lot of phishing activity going on at the moment with many new domains being registered every days. They often share infrastructure and a product like Silent Push makes it really easy to look for related domains.
There are several other domains using the aforementioned name server pair, suggesting the same actor is conducting some unrelated campaigns too. Also using the same name servers was otalebecu[.]com, a domain that has since been taken down.
When it was active, opening the domain in the browser showed an open directory, with subdirectories for several active campaigns:
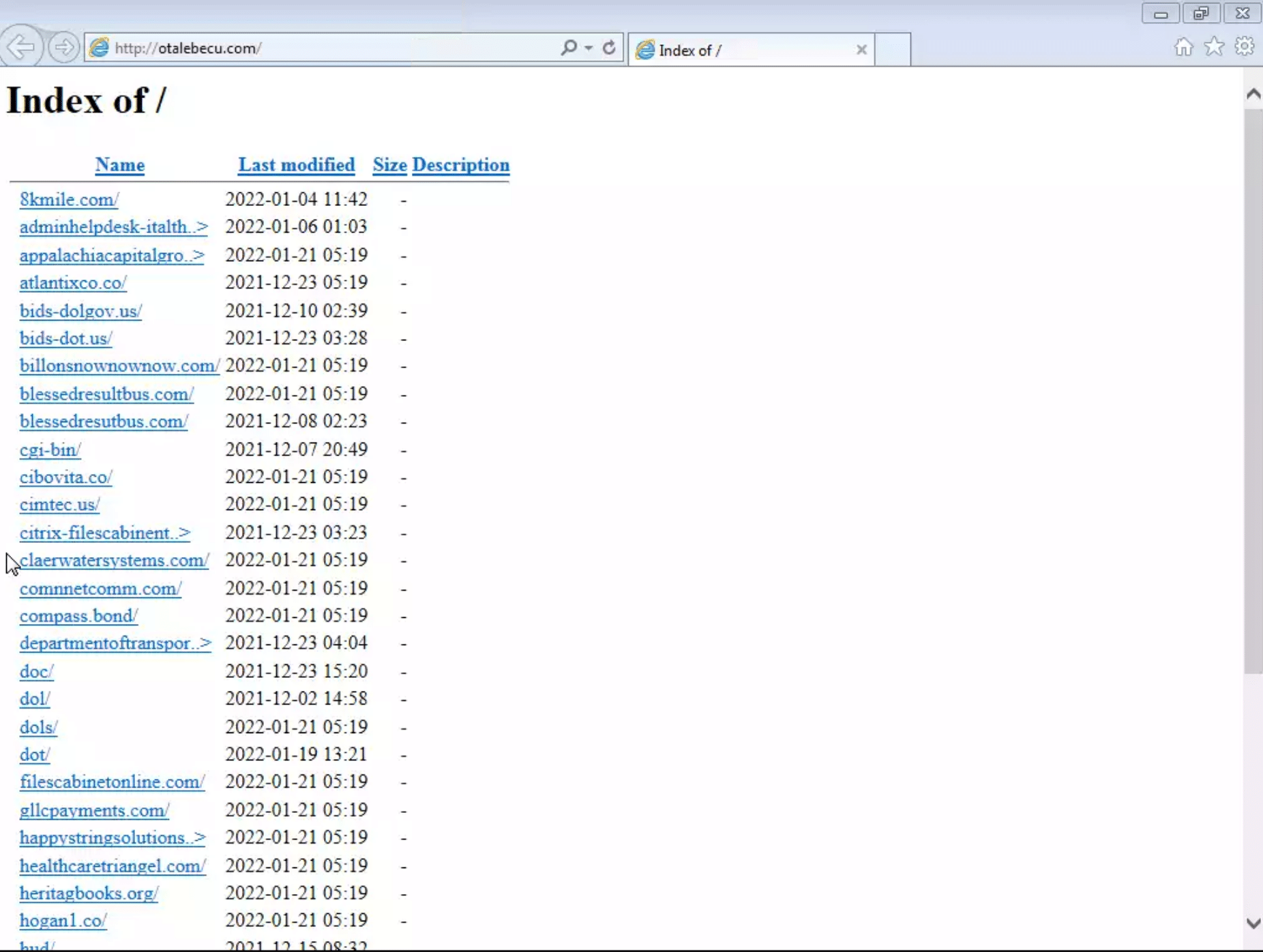
Opening these subdirectories gave the actual phishing sites:

so this may have been an easy way for the actors to manage the various campaigns.
The domains were also registered as subdomains of otalebecu[.]com:
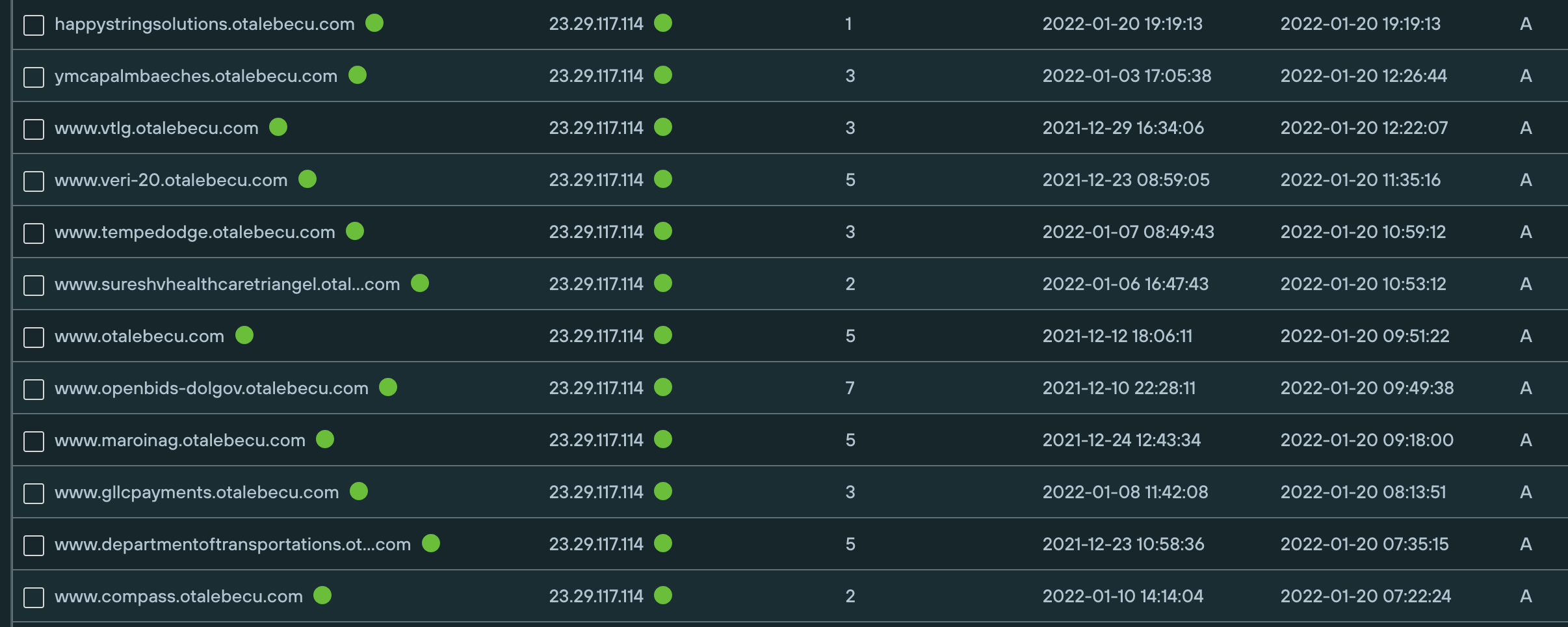
This is yet another reminder that malicious campaigns sometimes leave unexpected traces that a product like Silent Push can help you pick up.