At Silent Push, we track various kinds of bulletproof hosting infrastructure. Such infrastructure is a popular place to host phishing pages and by tracking the infrastructure rather than waiting for the phishing URLs to appear in emails or text messages, we are able to add domains to the feeds we provide to our customers before the domains are blocked by other services such as Safe Browsing.
Today, we look at a number of recent phishing domains from a feed that we internally refer to as ‘Sasha’.
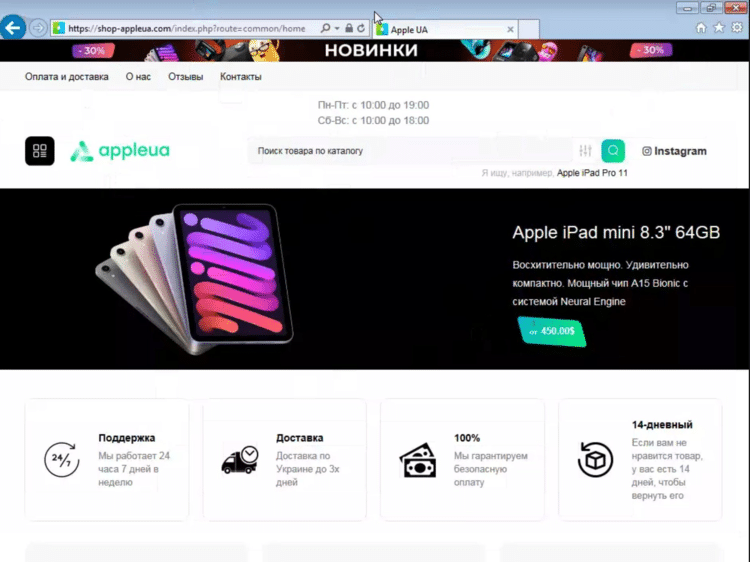
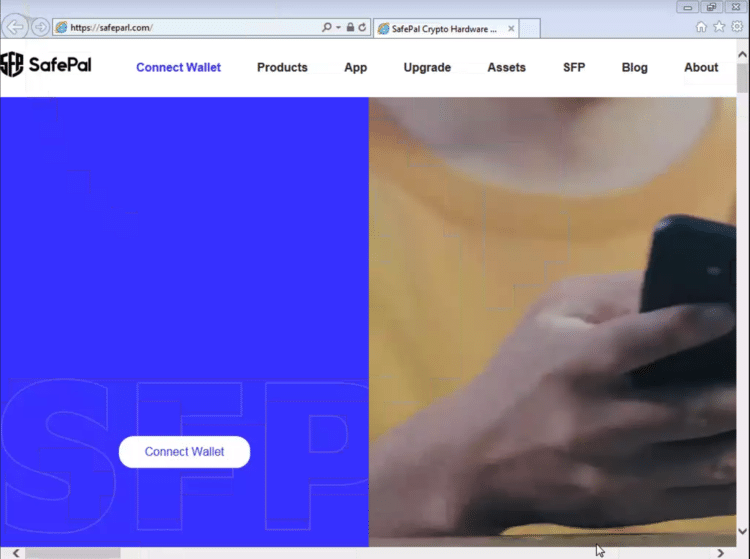
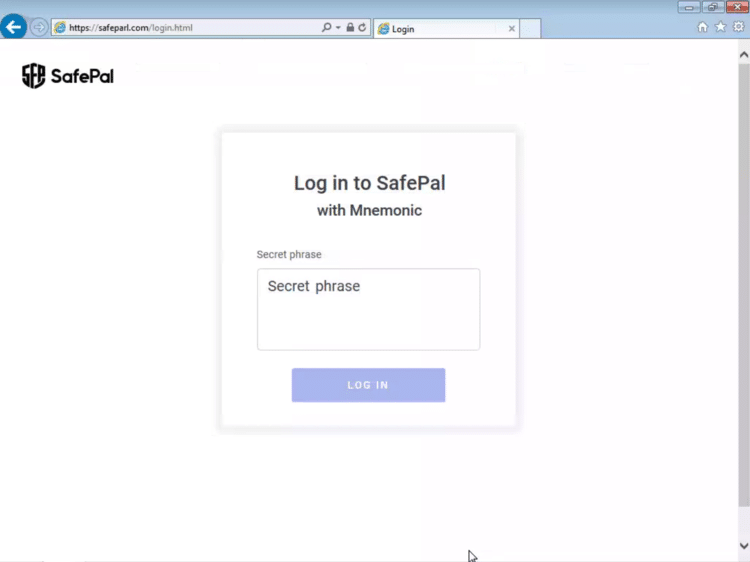
The first is safeparl[.]com, a phishing site for safepal[.]io, a company that sells hardware wallets to store cryptocurrencies. Unlike the real SafePal site though, the phishing site asks users for the Mnemonic passphrase for their wallet, after which the user is sent to the real SafePal site.
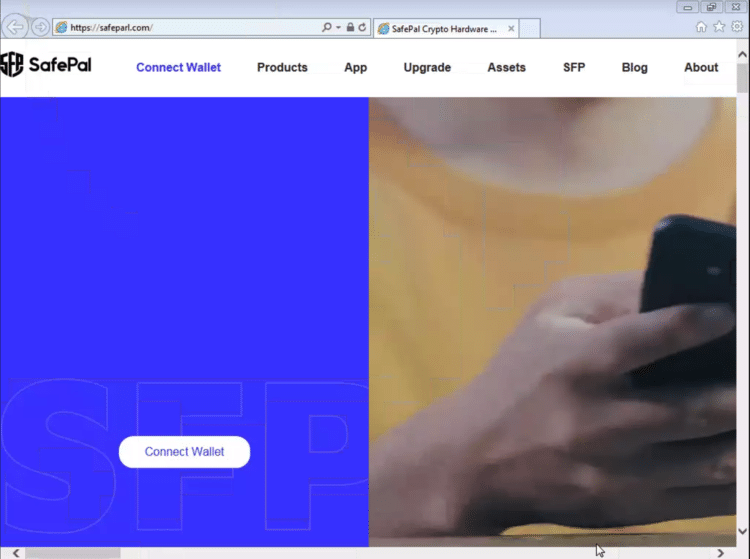
A second new phishing site is the latest instance of a series of sites that use the NHS Covid Pass as a lure to steal credit card details and other personal information. We wrote about this campaign last month and the fact that new domains keeps being registered suggests the actors have at least some success.
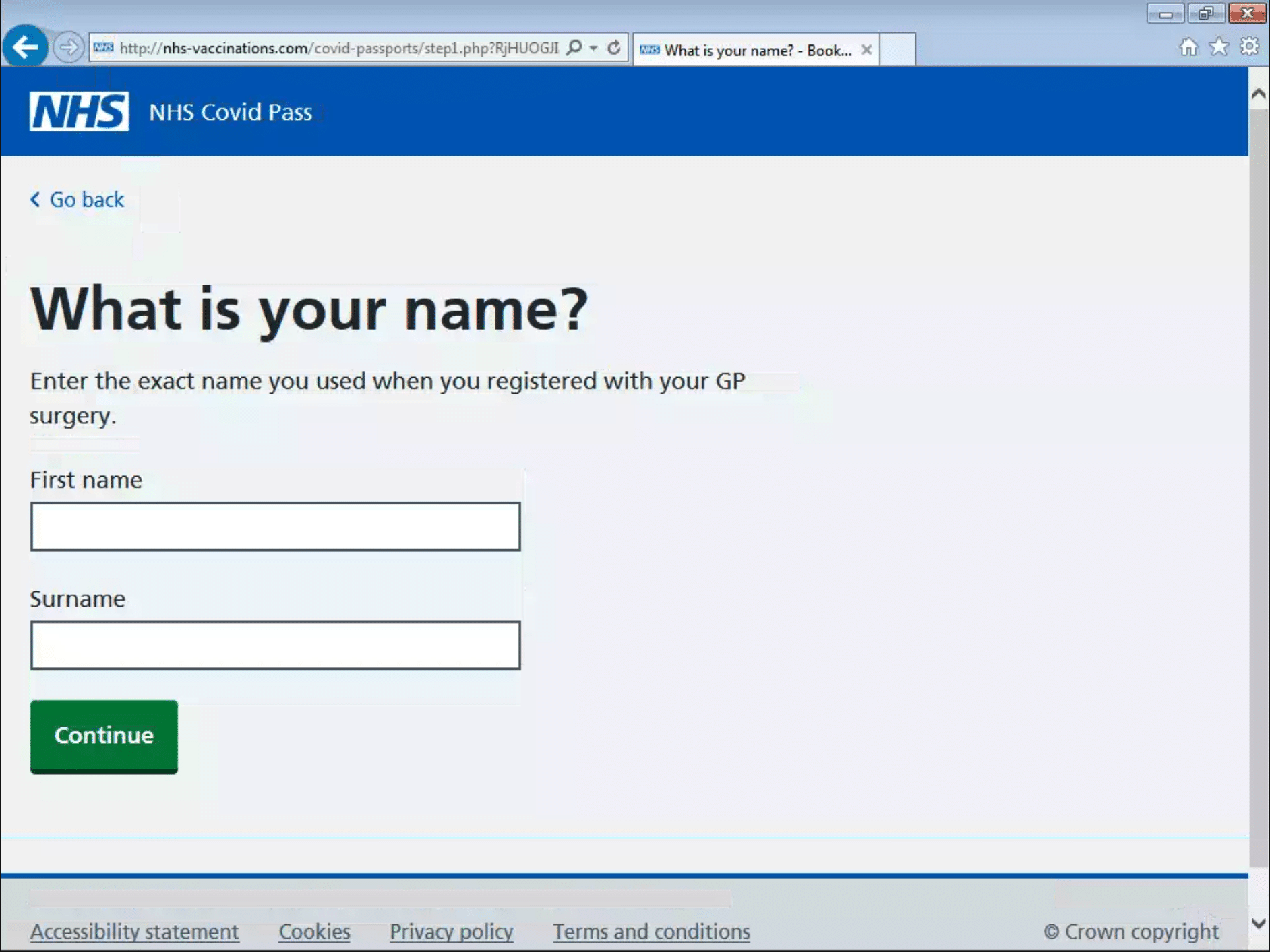
A third phishing site is an example of most archetypal phishing scam, which tries to obtain online banking details through a fake website that looks identical to the original one. This phishing site was targeting customers of UK’s Santander bank. We saw a similar phishing site a few days ago and the similarity in domain names suggests they are operated by the same actors, though interestingly they are hosted on different infrastructure.
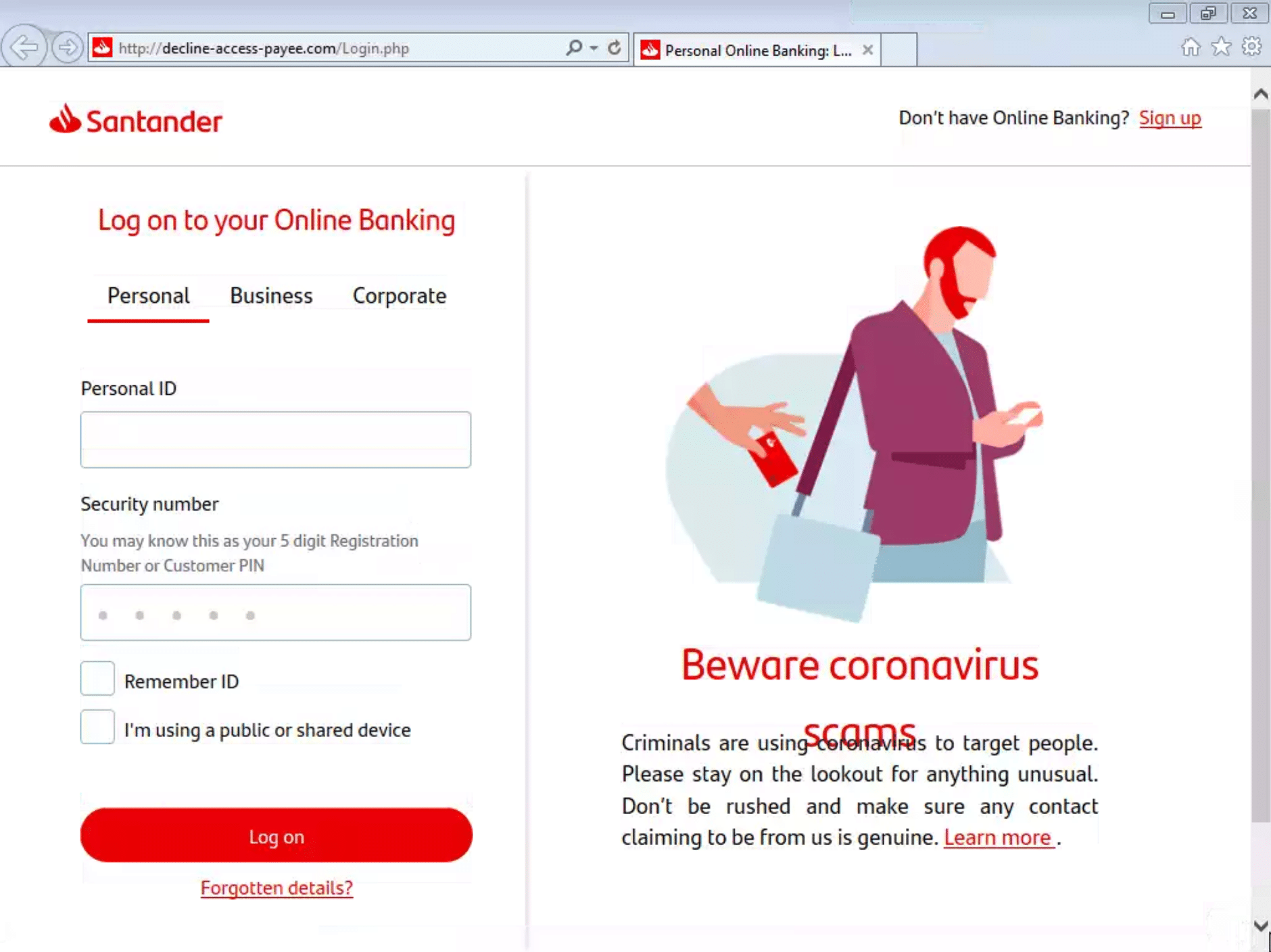
Finally, with so many security companies writing about digital (and non-digital) threats against Ukraine, one would easily forget that for many Ukrainians, life continues as normal. And that normal includes phishing scams, such as this fake Ukrainian Apple Store that links to a phishing site tar Prom, a popular e-commerce platform in the country.
Silent Push customers not only get access to the feeds the Threat Intelligence team creates, they can also create and maintain their own feeds, thanks to the Silent Push app and the very powerful API, which makes finding missing links in threat intelligence research very easy.
Indicators of compromise
SafePal phishing
safeparl[.]com
NHS Covid Pass phishing
apple-covid-status-pass[.]com
apply-covid-form[.]com
apply-mycovidpass-nhs[.]com
covid-client-application[.]com
covid-client-updated[.]com
covid-form-info[.]com
covid-nhspass[.]com
covid-passport-form[.]com
covidpassnhs[.]com
covidpassnhsapply[.]com
mypassapply-nhs[.]com
nhs-covid-pass-71672[.]com
nhs-covidapply[.]com
nhs-covidpass-uk[.]com
nhs-covidpassapply[.]com
nhs-testing[.]com
nhs-vaccinations[.]com
nhsapply-covidpass[.]com
nhscovidpass-apply[.]com
nhscovidvaccinations[.]com
Santander phishing
access-device-reject[.]com
access-reject-device[.]com
decline-access-payee[.]com
request-payee-reject[.]com
Ukrainian Apple Store and Prom phishing
shop-appleua[.]com
prom-pau[.]store
prom-paumment[.]store
prom-paumments[.]store
prom-payer[.]store


