Scanning the public web and dark web for ransomware infrastructure in Silent Push Community Edition

If you’re an independent security researcher, blogger, or part of a security team conducting initial investigations, Silent Push Community Edition is a free threat hunting tool that gives you the ability to locate and traverse malicious infrastructure across the public internet (“clear web”) and dark web simultaneously, and uncover hidden domains and IPs for further investigation.
In this blog, we’ll take a quick look at how we used Silent Push Web Scanner to scan .onion and public sites for DragonForce infrastructure, and the different ways you can query the Silent Push scan data repository to achieve laser-focused datasets.
Sign-up for a free Community Edition account
Silent Push Community Edition is a free threat hunting and cyber defense tool featuring a range of advanced queries and lookups – built on a powerful first-party database of enriched DNS and web content data – that allows users to locate known and hidden threat infrastructure on the public web and dark web.
What is Silent Push Web Scanner?
Silent Push Web Scanner provides historical insight into how threat actors build, manage and deploy their infrastructure over time, through syntax-based queries built on 200+ parameters, including:
- HTML titles
- SSL certificates
- Favicons
- JavaScript files
- Geolocation data
- Proprietary server and certificate hashes
- Body SSDeep data
- On-page content hashes
Crucially, our Web Scanner also provides the capability to uncover malicious threat infrastructure across both the clear web and the dark web, all within a single query.
We scan and collect dark web and public web data into separate repositories, but you can combine these data sources into one query and hunt for infrastructure across both, using the same parameters.
Revealing hidden ransomware portals
Let’s take a look at a quick example of how you can use Web Scanner to conduct dark web and public web scans side by side.
DragonForce is a cybercriminal group that has transitioned from its origins as a Malaysian-based hacktivist collective into a prominent Ransomware-as-a-Service (RaaS) operation.
Initially known for politically motivated attacks, the group has shifted its focus toward financially driven cyber extortion. DragonForce’s RaaS model provides affiliates with customizable ransomware payloads and infrastructure support, facilitated by access infrastructure across the public and dark web.
1. .onion HTML title query
We can use Web Scanner to execute a query using the datasource and htmltitle parameters, that returns .onion sites with matching content that contains “*DragonForce*” in the page title.

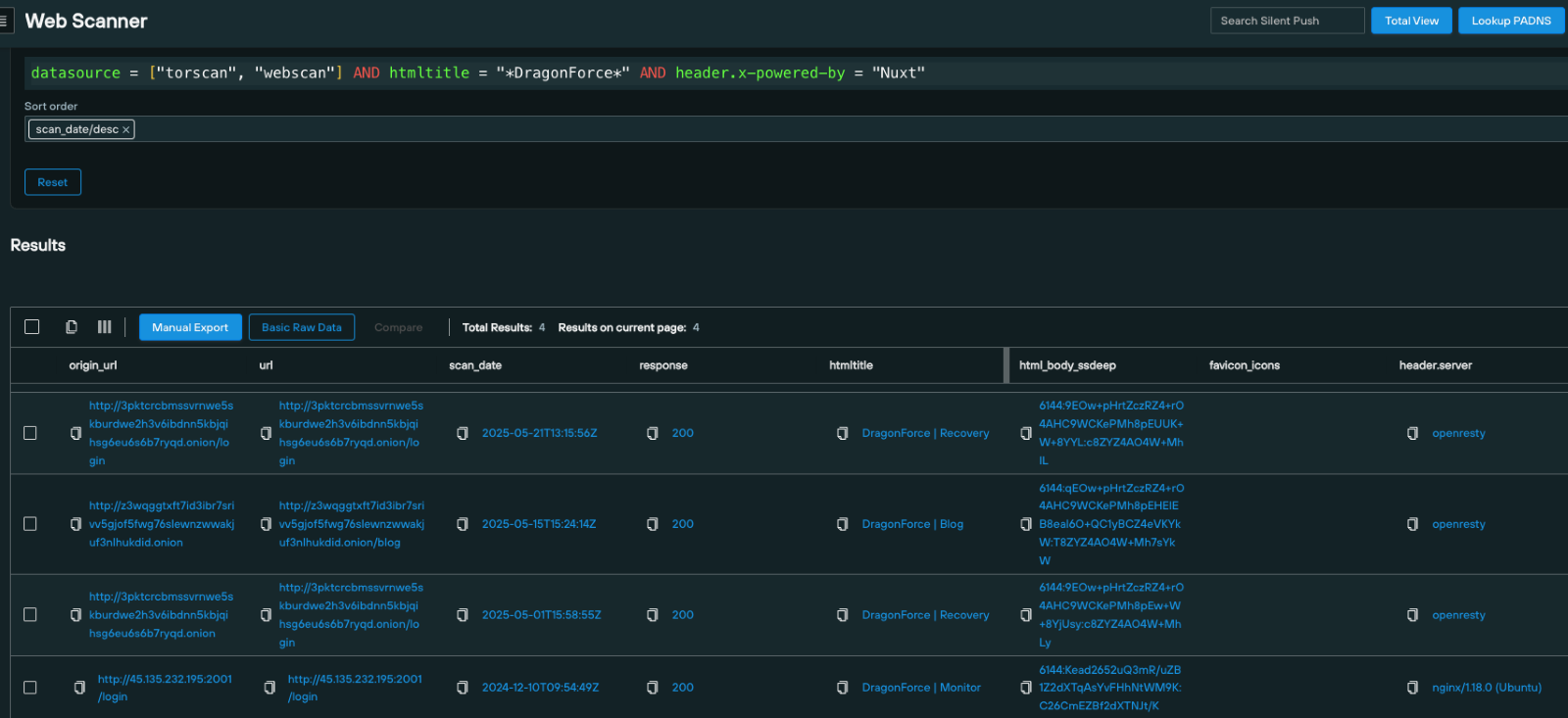
2. Pivot onto the clear web and dark web
From the dataset, we know that certain components of DragonForce utilizes the Nuxt.js application.
We can take this intel and use the header.x-powered-by parameter to search for infrastructure using Nuxt across both the public and dark web:
Join our Community Edition workshop on June 10: Scanning Dark Web Infrastructure to Detect Hidden Threats with Silent Push. Register today.
Web Scanner use cases
Web Scanner isn’t limited to public and dark web ransomware scanning. Here’s a few other key use cases that can be fulfilled with scanning via a free Community Edition account:
1. Tracking and stopping brand impersonation attacks
Cybercriminals often set up domains that mimic legitimate brands to deceive users. Web Scanner allows analysts to identify these malicious domains by analyzing patterns in SSL certificates, favicon usage, and HTML structures.
By detecting these behavioral patterns, organizations can take swift action to protect their brand reputation and customers.
2. Mapping attacker infrastructure over time
Web Scanner provides historical datasets that reveal how threat actors evolve their infrastructure over time, helping analysts to anticipate future threats and adapt their defense strategies accordingly.
3. Identifying DNS vulnerabilities
You can use Web Scanner to assess the security posture of a public DNS presence or supply chain operation.
By scanning for exposed services, outdated software, or misconfigurations, organizations can identify and mitigate potential vulnerabilities that could be exploited by attackers.
Ready to take threat hunting to the next level? Book a demo today.
Ready for deeper intel, IOFA feeds, TLP:Amber reporting, seamless integration capabilities and more? See the power of the Silent Push Enterprise Edition — book a demo today.

