Risk scoring provides a numerical framework for cyber security teams to better understand observable DNS data, and pinpoint emerging threats.
Assigning a risk score to a domain or IP allows defenders to evaluate attacker infrastructure that’s specific to their organization and supply chain, and make operational judgements based on the likelihood of an observable being involved in malicious activity.
Summary
In this blog, we’ll take you through how the Silent Push console and API outputs risk scores, and how to utilize scoring methodologies to level-up your threat intelligence operation. We’ll explain how each score is calculated, including the different factors we take into account, and how to operationalize the data.
Data independence
Many security teams use CTI platforms that pool data from disparate, third-party sources. Data is often forced through multiple aggregation layers without any concerted effort to convert it into actionable intelligence.
All of our risk scores are powered by a proprietary, first-party database. We own and control our own data, allowing us to add an infinite amount of context to each observable, and provide layers of accurate, timely and complete intelligence data.
Understanding risk scoring in Silent Push
Risk scoring is available across the board to Enterprise users, and to a limited extent for Community users. We’ll explain the difference between the two tiers later, but for now we’ll focus on the main mechanism for obtaining risk scores available to Enterprise users – the Threat Ranking screen.
Scoring categories
Silent Push assigns four different risk scores on the Threat Ranking screen, to every domain and IP:
- Enriched score
- Source score
- Custom score
- Total score
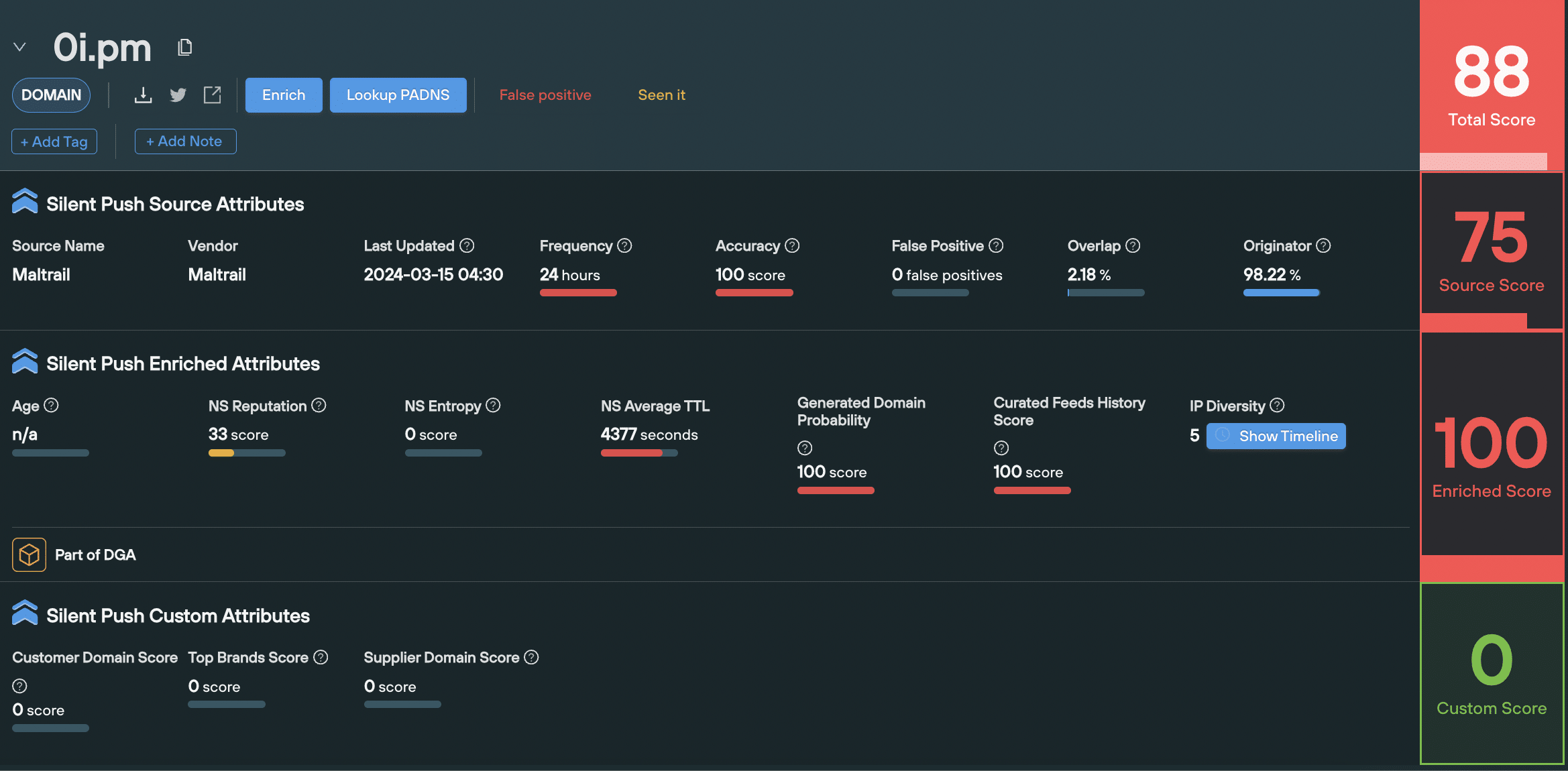
Source, Enriched and Custom scores each have their own unique set of factors that make up the final score for that category. Each factor has a numerical value that allows you to perform a deep-dive into an observables risk level, above and beyond a headline score. More about factors later on.
The Total score is always set at the mid-point between the Source score, and the highest value between the Enriched and Custom score.
Let’s take a look at each category in turn…
1. ‘Enriched’ risk scoring
An Enriched score takes different pieces of information we have available about an observable’s relationship with the rest of the Internet, and provides an overall risk level based on its enriched attributes.
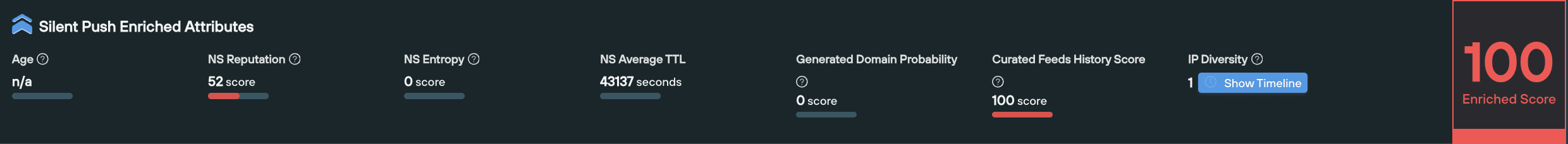
When should I use it?
You can use the Enriched score to better understand the infrastructure used by a single observable, including how it’s being managed, how it’s moved across the IPv4 space, and the likelihood of it being involved in malicious activity.
A domain or IP’s Enriched score is useful for breaking down different elements of an observable, to understand which components raise red flags.
How is it calculated?
The Enriched Score is an algorithmically-calculated number, based on a variety of factors that take into account the underlying infrastructure, and how an observable is being managed. An Enriched score is calculated using different factors for domains and IPs. All of these factors contribute to the final Enriched score.
- Domain-based Enriched scoring considers factors such as domain age, nameserver (NS) reputation, and the presence of automated domain generation algorithms.
| Factor | Definition |
| Curated Feed History Score | The frequency and recency of an observable’s presence within trusted feeds |
| NS Reputation | The ratio of blacklisted domains, taken from the total number of domains using a NS |
| NS Entropy | The recency, frequency, and the number of NS changes |
| Generated domain probability | How likely it is that a domain was created by an domain generation algorithm |
- IP-based Enriched scoring evaluates the threat level of IP addresses based on factors such as Autonomous System Number (ASN) reputation, subnet reputation, and responsiveness to takedown requests.
| Factor | Definition |
| Curated Feed History Score | The frequency and recency of an observable’s presence within trusted feeds |
| ASN Rank | A ranking of ASNs seen to host threats listed on feeds, calculated using a weighted formula based on the type of threat observed |
| ASN Takedown Reputation | A reputation score based on the time it takes for an ASN owner to react to takedown requests related to malicious URLs. A higher reputation score indicates the ASN owner is slow to react to takedown requests |
| ASN Reputation | A measure of the trustworthiness and reputation of the networks associated with a particular ASN. |
| Subnet Reputation | A measure of the trustworthiness and reputation of a specific subnet or range of IP addresses within a larger network. |
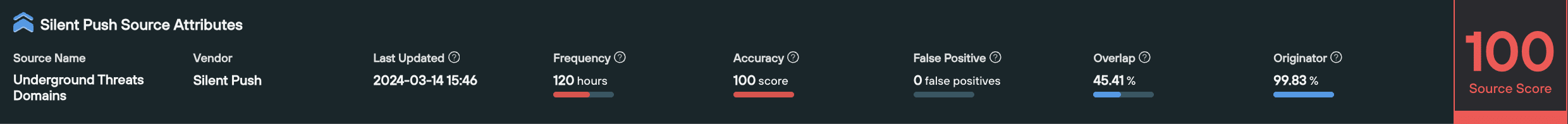
2. ‘Source’ risk scoring
A ‘Source’ is the feed that an observable is listed in. The Source score is a number that tells you the overall value of that feed.
When should I use it?
The Source score offers a quick way of understanding the overall threat level for a group of domains or IPs contained within a feed. This allows you to compare different feeds at-a-glance, and prioritize the most dangerous threat groups relevant to your organization.
How is it calculated?
A Source score is calculated based on the attributes of the feed the observable is listed in (or custom feeds created by a user), using the following factors:
- When a feed was last updated
- How often the feed gets updated
- The percentage of false positives
- The percentage of true positives
- The geographic spread of observables
3. ‘Custom’ risk scoring
A Custom score is based on a set of user-defined parameters that locates malicious infrastructure relevant to their organization and supply chain operation.
When should I use it?
Custom scores are extremely useful when attempting to ascertain the likelihood of an IP or domain being involved in threat activity that is either specifically targeting your public DNS presence, or is involved in threat activity within a given sector.
How is it calculated?
Users are able to define a series of custom indicators within the Organizational Assets menu, that maps out their public DNS presence:
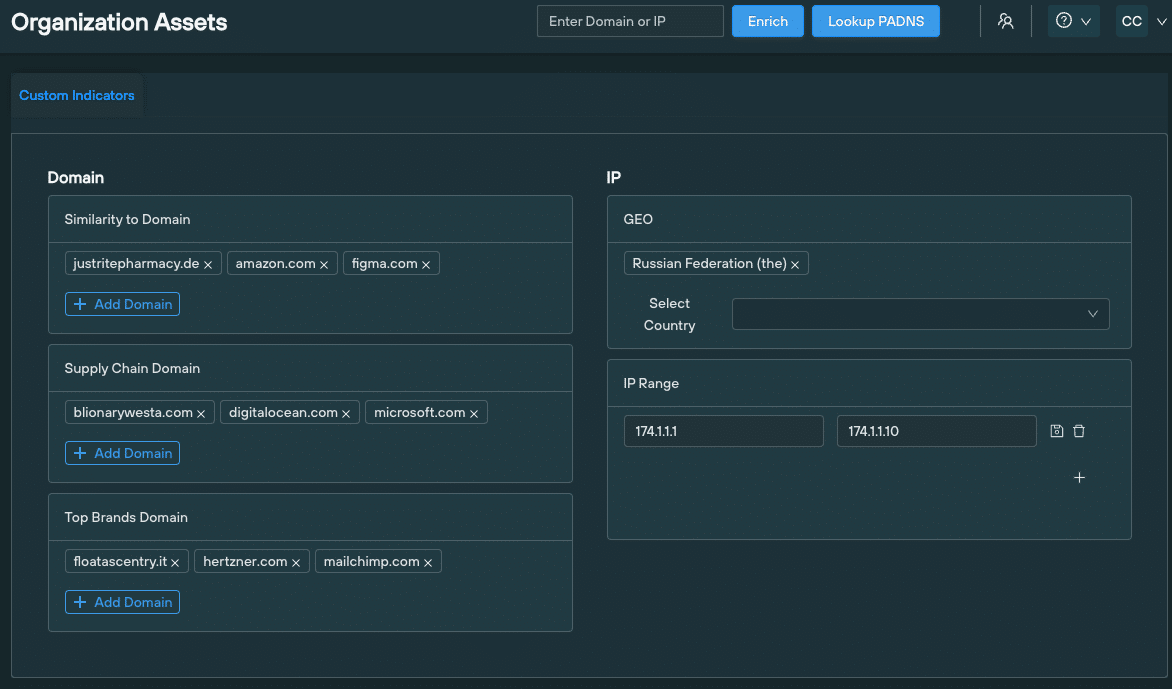
An observable’s Custom score is directly related to how similar elements of it are to any one of these factors. The higher the score, the greater the similarity.
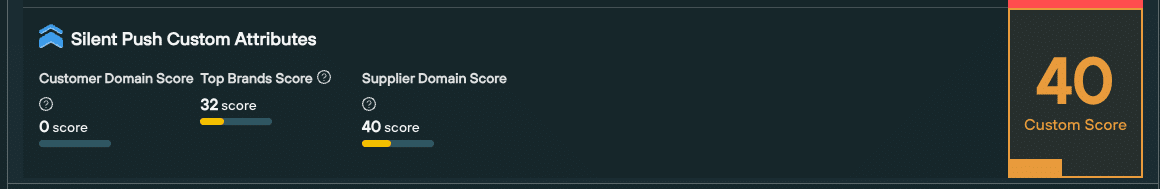
Calculating factors are displayed as part of the score in the Threat Ranking screen, so that organizations can make a value judgement based on all the available data.
4. Total score
The Total score is a headline number that is always set at the mid-point between the Source score, and the highest value between the Enriched and Custom score.
By default, the Threat Ranking page is sorted with the Total score at the top.
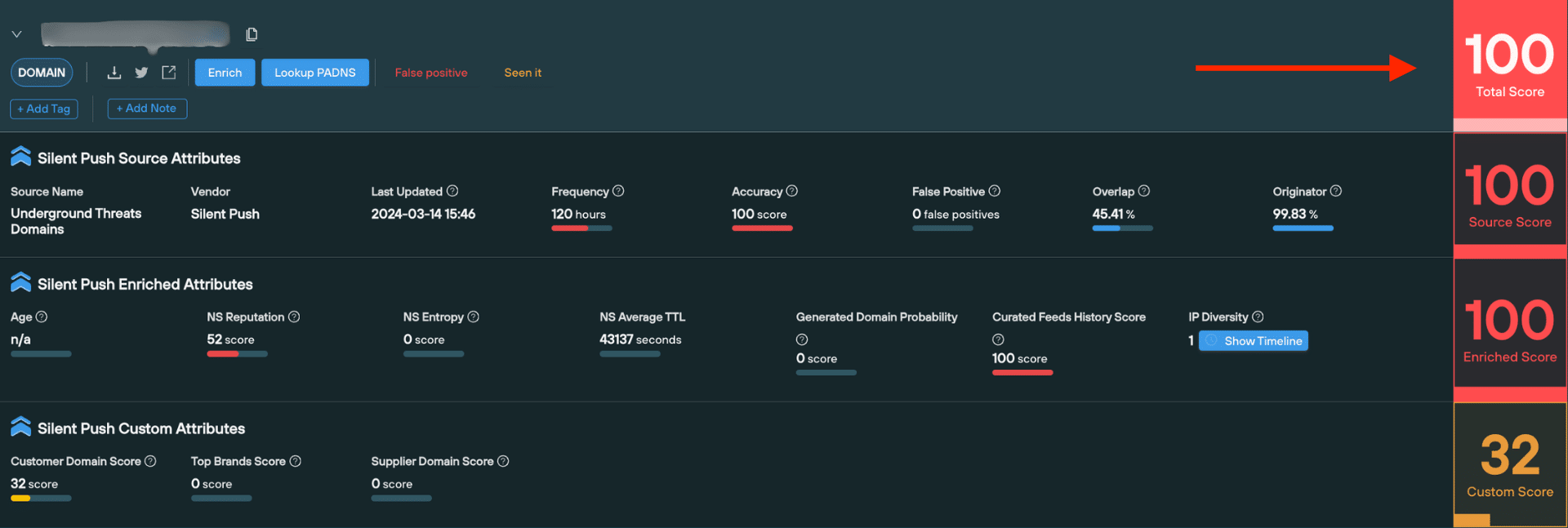
When should I use it?
The Total score is useful for obtaining an “at-a-glance” risk level of a domain or IP, without a need to perform additional analysis.
How it is calculated?
The Total score is the middle point between the Source score, and the highest value between the Enriched and Custom score.
For example, if a domain has a Source score of 50, an Enriched score of 90, and a Custom score of 40, it’s Total score would be 70 – the mid-point between 50 (Source score) and 90 (Enriched score)
How to access risk scoring using Silent Push
You can operationalize risk scores using Silent Push in a variety of ways, either using the console or directly into your security stack via the API.
Passive DNS risk scoring (Community and Enterprise users)
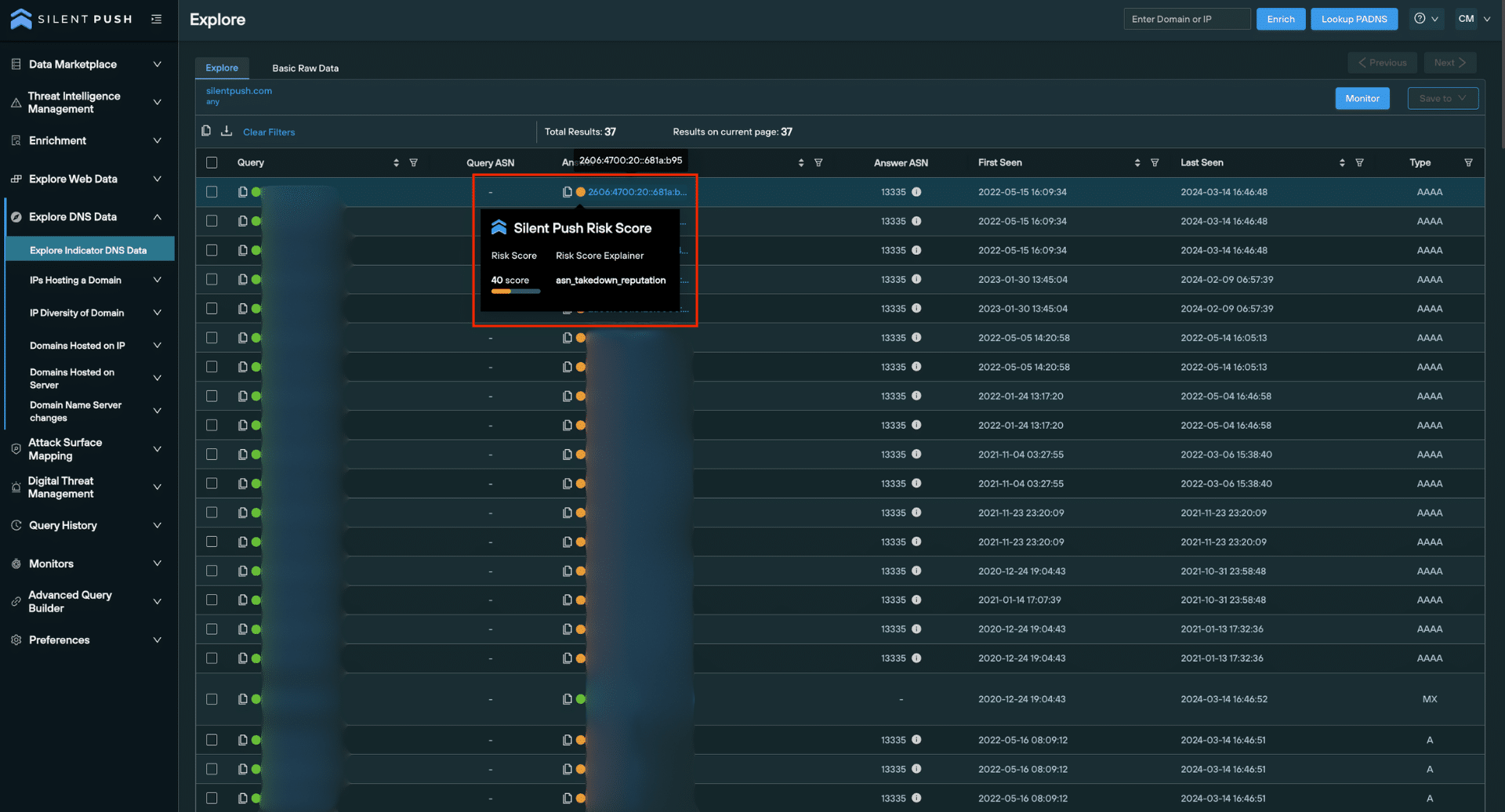
It’s often useful to compare risk scores across a single dataset at a glance. To do this for passive DNS datasets, lookup a domain or IP and take a look at the traffic light system on the Explore screen.
You can hover over the coloured dots next to each observable to get more information. The Silent Push Risk Score is given as the Enriched score, with the primary factor for the score given below the actual score.
In the below example, the Silent Push Risk score is an amber 40, with the observable’s ASN takedown reputation being the deciding factor.
Enrichment highlights (Community and Enterprise users)
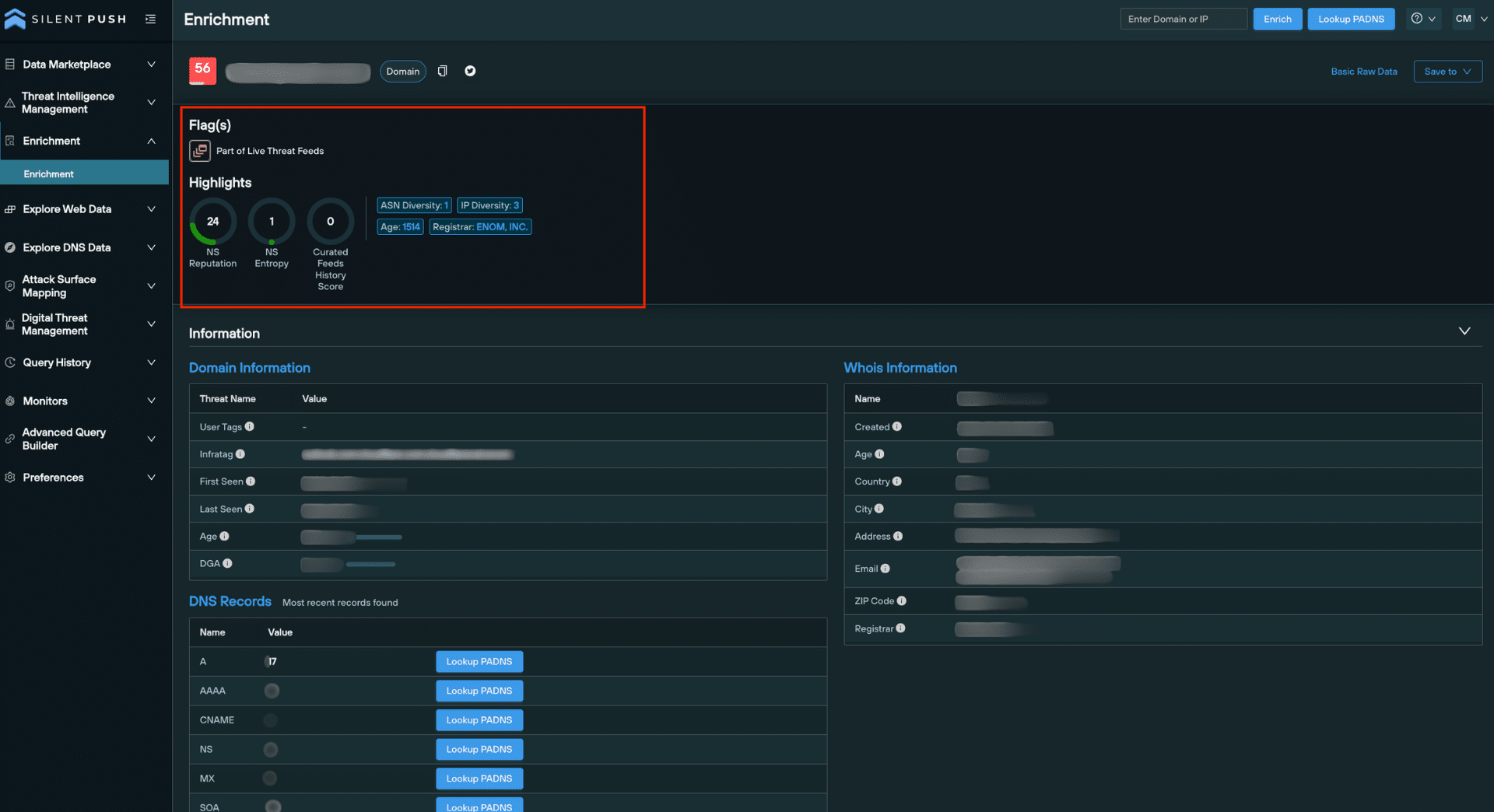
Data enrichment is a threat intelligence mechanism that allows security teams to pinpoint the origin, function and risk level of a domain or IP address, by applying multiple layers of categorization to a domain or IP address.
Enrichment results for a domain or IP include a Highlights section that offers an overview of the most important reputation-based metrics.
Highlights are also available for URLs. If the root of a URL is a domain, then domain-based attributes are shown. If the root of the URL is an IP, then IP attributes are shown.
‘Threat Ranking’ risk scoring (Enterprise users only)
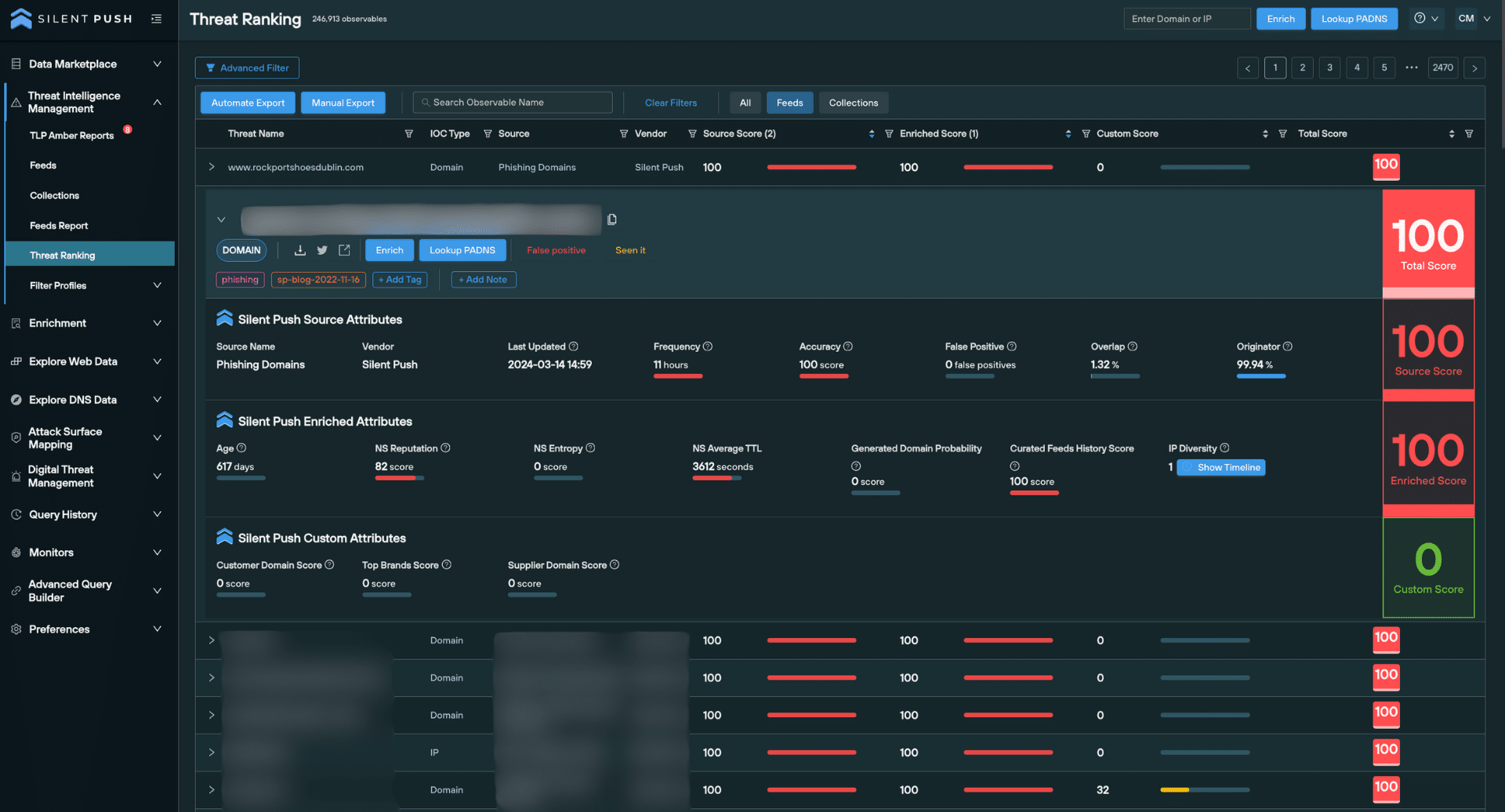
We consolidate malicious domains and IPs into a single indexed and searchable Threat Ranking screen.
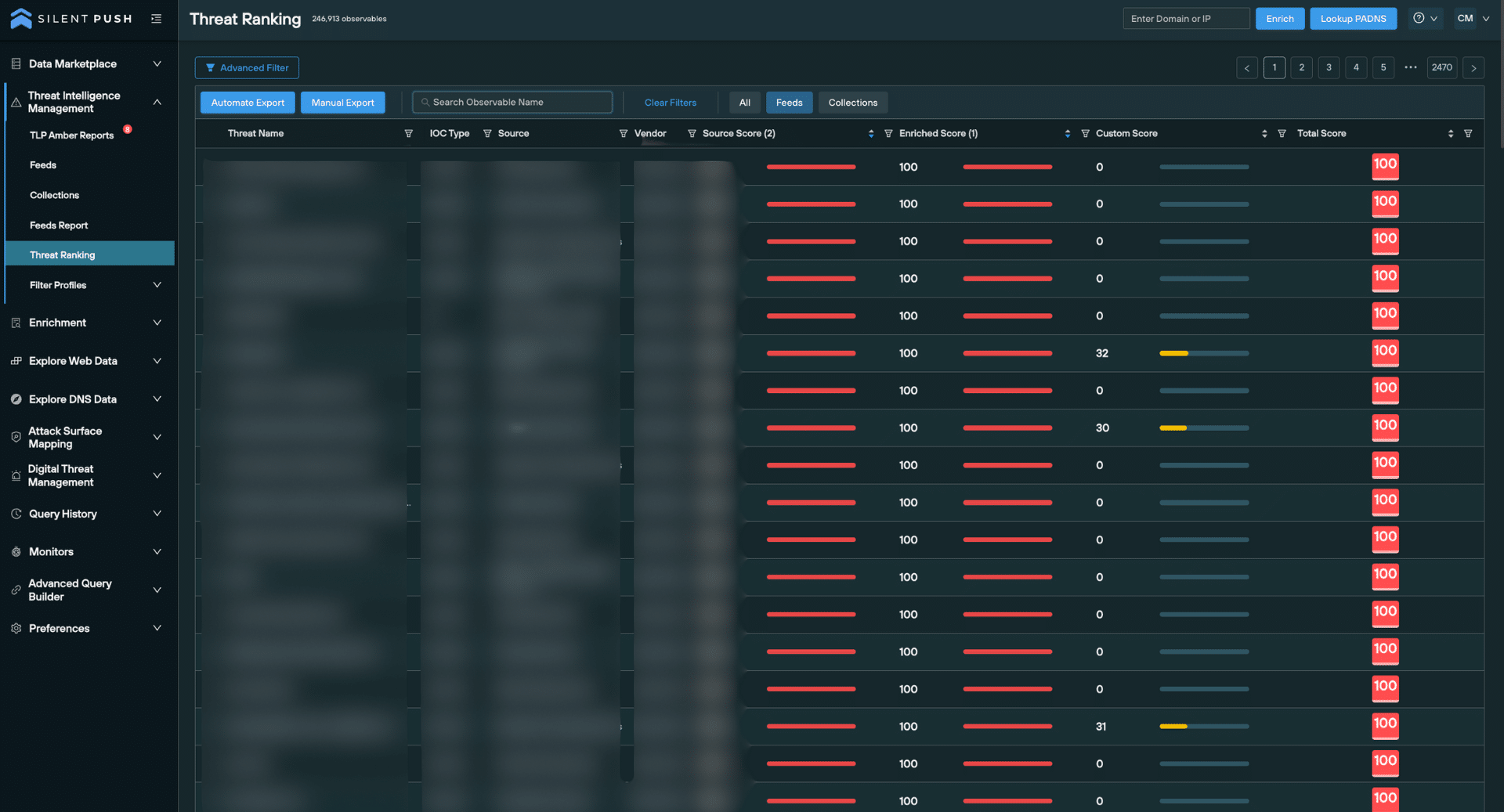
When an observable is expanded from the Threat Ranking screen, over 18 secondary analysis fields are provided, including granular threat data and basic information that provides additional context on a given domain or IP.
Risk scoring is visible on the right side of the screen, along with any factors we’ve used to calculate them.
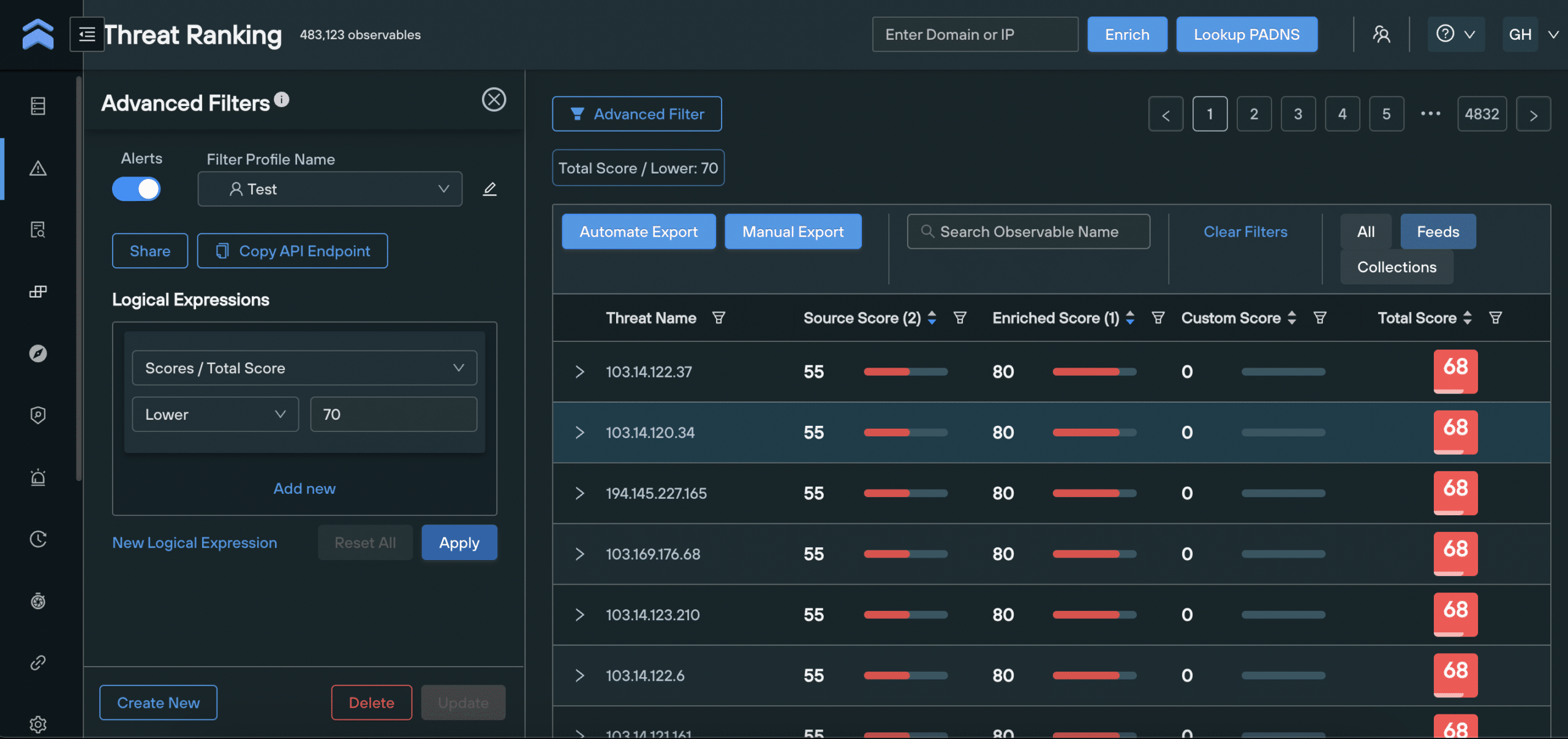
Filtering threat data by score values
Filter Profiles allow you to filter domains and IPs on the Threat Ranking screen by certain criteria, enabling security teams to drill-down into intelligence datasets and create custom workflows at the click of a button.
You can use Filter Profiles to build logical expressions that only show domains and IPs with a certain set of Enriched, Source, Custom and Total scores, along with all the secondary factors that make up each score, and huge range of additional parameters that form a single logical expression.
Here’s an example Filter Profile that displays all IP addresses with a Total score of above 70, and an ASN reputation of below 50.
Register for Silent Push Community Edition
You can access risk scoring using Silent Push Community Edition – a free threat hunting and cyber defense the threat hunting platform that features a range of queries and lookups, the Silent Push Web Scanner, and 90+ data enrichment categories that you can use to track and monitor attacker activity across the global IPv4 space.