The Challenge: Drowning in a Deluge of APT Investigations
Like many large enterprises, our media services customer faced the daunting task of sifting through vast quantities of raw threat intelligence relating to high-profile Advanced Persistent Threat (APT) groups targeting their organization.
Even with robust security infrastructure, the sheer complexity of data related to APT activity, and their expansive online presence, meant that identifying and responding to APT behavior was a time-consuming and reactive endeavour.
Each investigation was a deep dive, requiring significant manual effort to correlate disparate pieces of information, and extract actionable intelligence that could be used in the organization’s security operation.
This not only put a strain on their Security Operations Center (SOC) team, but also delayed their ability to preemptively mitigate threats, leaving windows of vulnerability open longer than desired.
The existing workflows, while comprehensive, struggled to keep pace with the dynamic nature of APT activity, leading to prolonged investigation cycles and a persistent sense of playing catch-up.
The Solution: TLP Amber Reports within Silent Push Enterprise
Silent Push Enterprise edition features exclusive access to APT and threat-specific TLP (Traffic Light Protocol) Amber reports.
Built on the insight and knowledge we gain through the platform’s ability to reveal and track infrastructure as it’s being deployed, TLP Amber Reports are drafted by Silent Push’s expert Threat Analysts who have collectively produced industry-leading research on high-profile threat campaigns.
Our reports go much deeper than our public blogs, featuring direct links to pivots, queries, scans, and datasets, so that teams can follow along within the platform, along with a comprehensive list of Indicators of Future Attack (IOFA)™ that are exposed during the investigation.
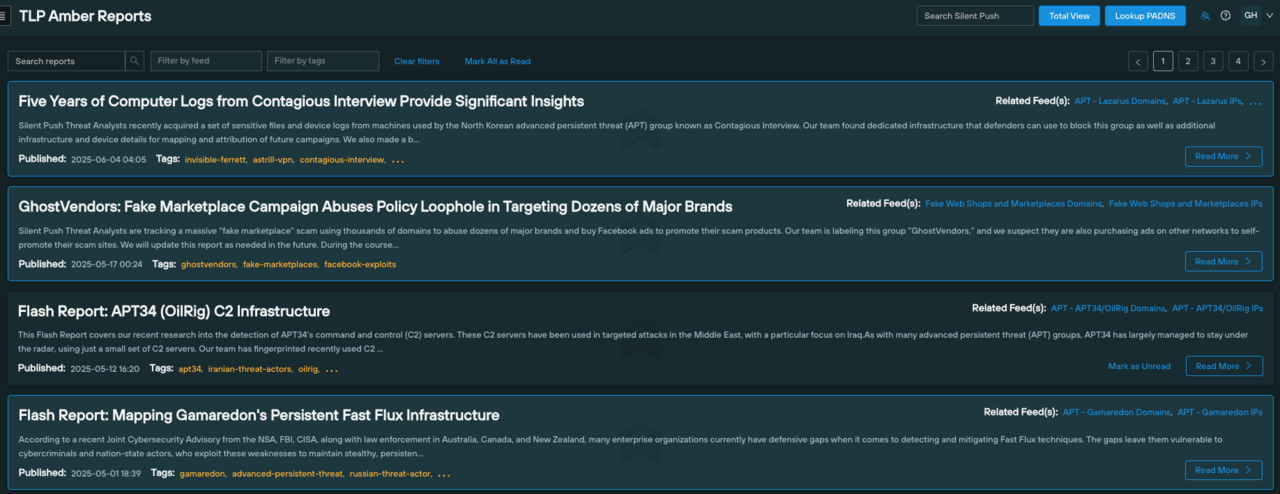
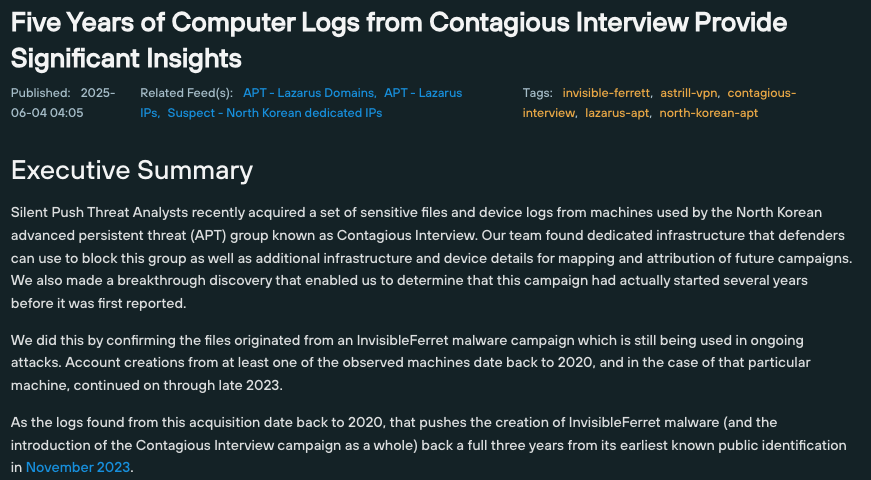
Using our reports as a jump-off point for APT investigations, our customer’s security team no longer had to painstakingly piece together information from multiple sources.
Critical context, including attacker methodologies, tools, and infrastructure, is presented directly within the platform, drastically reducing investigation time. Each TLP Amber report is also tagged with the relevant threat actor or campaign name, and is presented alongside a corresponding IOFA Feed.
Our customer streamlined a time-consuming and reactive process into a short, sharp, review of immediately available intelligence, significantly bolstering their security posture against some of the most highly advanced and prominent cybercriminals currently in operation.
What took days (or even weeks), now took a few hours.
The Silent Push Difference: Ready-made SOC and IR Intelligence
Our TLP Amber reports fundamentally changed our customer’s approach to APT investigations.
With TTPs laid bare and actionable pivots readily available, the time spent investigating APT activity plummeted. Analysts could now quickly understand an adversary’s modus operandi and identify infrastructure for blocking and reporting.
By understanding the patterns involved in APT infrastructure deployment and management, the security team moved from a reactive to a truly preemptive stance, with a newfound ability to predict where an attack was likely to originate, rather than relying on post-breach indicators that were often redundant as soon as they were publicly known..
Intelligence that was previously hard to access – either spread across multiple pieces of research, hidden under the surface of an attack, or requiring extensive manual correlation – became readily available.
Learn more about our unique approach to preemptive threat intelligence
Find out how Silent Push can help you save countless hours of painstaking threat research with customised TLP Amber reports that are specific to your area of expertise.


