Challenge: Stopping phishing attacks using only IOCs
A U.S.-based financial services company were being targeted by several Advanced Persistent Threat (APT) groups – mostly notably Scattered Spider – in phishing campaigns that were specifically directed against the organization’s online presence.
Due to a diverse set of commercial interests that include investments, insurance, and annuity products, the organization’s security team were tasked with defending a vast amount of highly sensitive financial information, spread over a broad attack surface that was steadily growing, against an adversary with several high-profile intrusions on public record.
Using their incumbent provider, the organization deployed an IOC-led approach to threat detection that relied on post-breach data, and was not able to provide early warning of new APT infrastructure as it was being set up against the brand and supply chain, and before it was fully weaponized.
Additionally, the SOC team were struggling to sift through large amounts of data – most of it out of date – to correlate IOCs and validate alerts as worthy of further investigation.
Solution: Using IOFA™ to identify hidden threat infrastructure at scale
Once onboarded, our customer gained extensive visibility through our platform cross several key metrics, including MTTD and MTTR for the above attack vectors, and resulted in a far more insightful CTI data streams that didn’t feel like swimming through treacle during critical incidents.
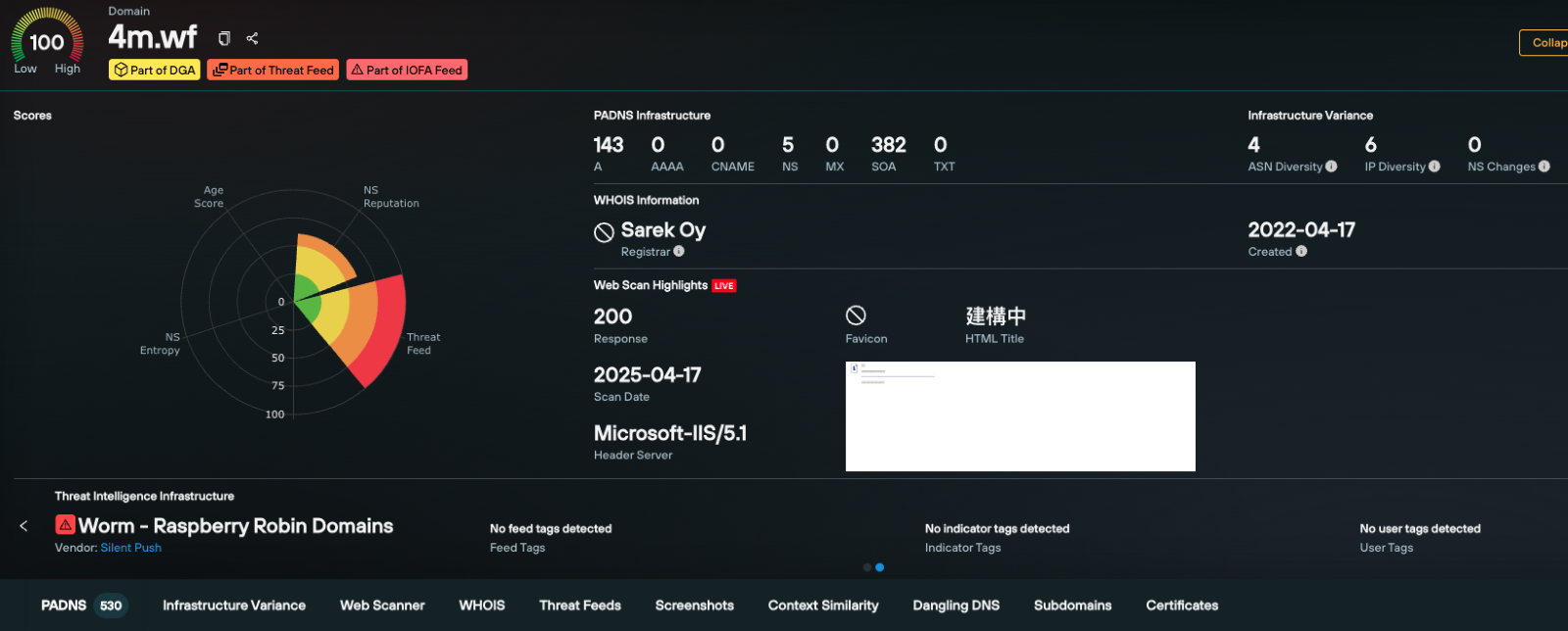
Using our Indicators Of Future Attack™ data, the customer was able to create workflows that tracked and monitored the Tactics, Techniques and Procedures that APT groups were using to initialize and deploy their infrastructure, and revealed hidden brand impersonation domains and IPs that were not previously on their radar.

The security team were also able to integrate a dedicated Scattered Spider IOFA™ Feed into their security stack, created and maintained by Silent Push Threat Analysts. This provided automated alerts on new infrastructure as it was being deployed, and a wealth of true positive pivot points for further investigation.
The Silent Push Difference: Know First with IOFA™
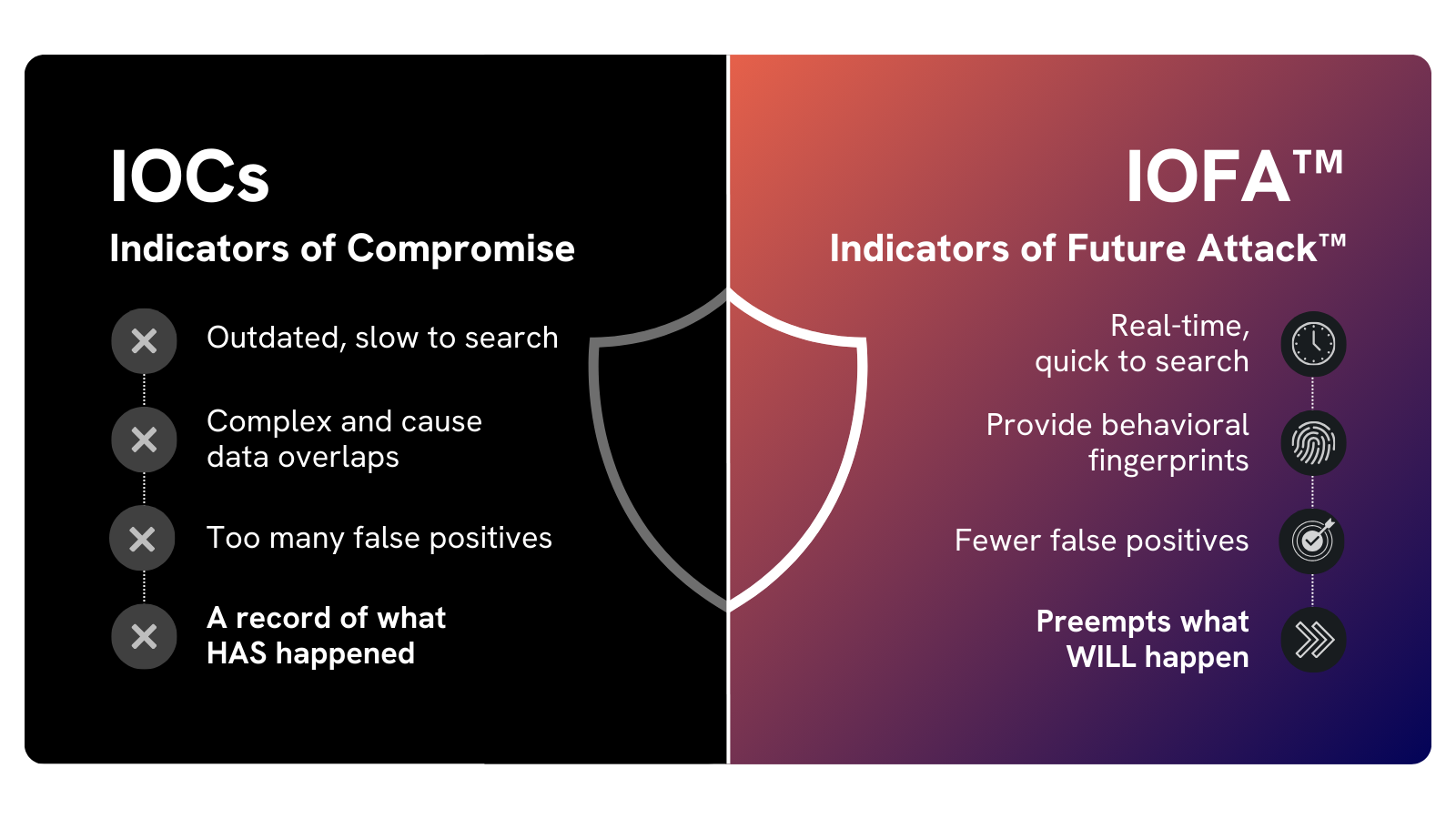
Silent Push is the only cybersecurity platform that features IOFA™ – preemptive threat intelligence datapoints (hostname, domain, IP etc.) that reveal where an attack will be launched from in the future, based on how an adversary manages and deploys their infrastructure.
IOFA™ are used to create digital fingerprints of attacker activity, which security teams can use to track and monitor the searchable patterns that emerge as threat actors plan and execute a cyberattack, including brand impersonation attacks.
IOFA™ go way beyond traditional IOCs, and allow brand defenders to locate and block linked spoofing and phishing domains, avoiding loss and reputational harm.
Learn More About Our Unique Approach to Preemptive Threat Intelligence
Find out how Silent Push helps you to locate hidden and known threat infrastructure, and stop digital assaults at the source before they occur using Indicators Of Future Attack (IOFA)™.
Contact us here for more information.
Further Resources
We’ve published extensive research on Scattered Spider APT activity. Click here to read our blog.


