Background
We’ve been monitoring the activity of a Kurdish hacktivist collective called 1877 Team.
A Medium article from 2021 picked up on the group’s earlier exploits, but little public information is available on the threat actor’s exploits.
The author of the article claimed the hackers are “(….) unethical, childlike, and pointless (…), nothing more than a mild inconvenience”.
The Silent Push Threat Intel Team has conducted extensive research to establish if that assessment still holds true.
We’ve discovered that the group’s methods and techniques have evolved to become more sophisticated, and instead of being dismissed as frivolous, their actions should be considered as an emerging threat to a range of organizations.
Motives and methods
The 1877 Team are a hacktivist collective that was founded in July 2021 by a small group of Iraqi Kurds.
The hackers initially developed and distributed modified versions of the popular mobile game PUBG, but over time, the group’s activity became significantly more complex, as well as politically driven.
Within the past year, the 1877 Team has claimed responsibility for large doxxing campaigns, website defacements, DDoS attacks, and attacks on the servers and databases of national governments, universities, telecommunication companies, defense organisations, and IT corporations.
The primary targets are situated in the Middle East, but African, Asian, and Western organizations have also been affected. The 1877 Team’s self-proclaimed goals include pressuring governments, spreading public dissent, and gaining notoriety amongst their fellow criminals.
The group has amassed a significant social media following, with 12.000 members on their Telegram channel alone. Hacking tips, exploit scripts, and stolen data are all shared and discussed. The hacktivists also manage a curated presence on TikTok, Twitter, Facebook, Instagram, and YouTube.
The 1877 Team operates a social media service, a defacement exposure website, and a dark web forum for trading exploits, malware, and stolen information, or for seeking advice for launching cyber attacks.
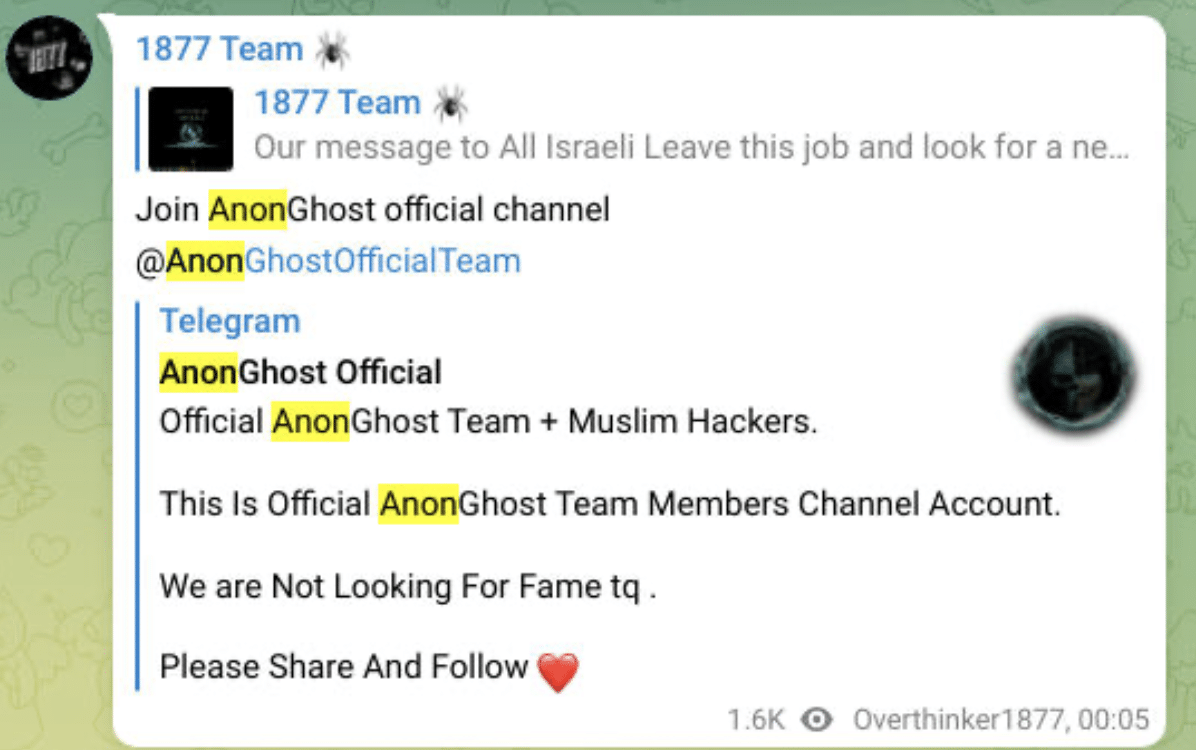
The group has established close links to skilled hacktivist collectives such as Anonymous, AnonGhost (a pro-Palestinian/anti-Israeli hacktivist group), and ALtharea (a pro-Iran hacktivist group).
Attack vectors and cybercriminal activity
The 1877 Team focuses on two simple techniques to gain access to foreign infrastructure:
- scans of web pages for particular vulnerabilities;
- brute-forcing administrator credentials.
Targets include political entities and popular software/services. Their attacks often involve website defacements, DDoS attacks, and leaks of sensitive information.
The group carries out extensive recon to explore vulnerabilities, not all of which are immediately exploited.
Security gaps of organizations and institutions that are not primary targets are collected in large batches and sold or offered for trade on the group’s Telegram channel and dark web forum.
The 1877 team operates several marketplaces for selling hijacked infrastructure, modified malware, and hacking tools. The items on offer include hacked accounts for popular streaming services and bug bounty platforms, stolen credit cards, exploits & zero-day vulnerabilities, and hacking tools such as:
- DDoS tools.
- WordPress brute force functions.
- CVE mass scanning scripts.
- Security/2FA bypassers.
- Modified malware and spyware.
Marketplace examples and timeline
July 2021 – October 2022
- Sold/offered PUBGM in-game cheats and modifications (MODs)
November 2022 – December 2022
- Hijacked and sold/offered accounts for entertainment platforms such as Netflix and Onlyfans, and the bug bounty hunting platform HackerOne.
- Sold stolen/fake credit cards.
- Hacked and sold thousand of cPanel and WordPress administrator credentials.
- Developed and shared a multi-vulnerability exploit for iOS.
- Hijacked the webmail service of an undisclosed government.
- Advertised security and 2FA bypasses for Metamask and Paypal.
- Scanned IoTs with un-patched Fortinet firewalls, susceptible to a vulnerability disclosed in October 2022.
February 2023
- Sold web shells targeting government servers.
- Sold a zero-day-vulnerability exploit targeting WordPress plugins.
Political affiliations and activity
The 1877 team appears to consist of around a dozen Iraqi-Kurdish teenagers/young adults.
- Founder (alias): Overthinker1877
- Social Media: @0x1877 @Ameer1877
- Co-founder (alias): CodeBoy1877
- Social Media: @x1877x @CodeBoy1877x
The group’s activity is strongly dictated by its prevailing political views and affiliations. These appear volatile and at times contradictory.

Hacktivism examples and timeline
Israel/Palestine
The 1877 Team’s social media posts and hacking activity indicate that they are Palestinian-aligned.
The group is affiliated with AnonGhosts, a pro-Palestinian/anti-Israeli hacktivist group whose activity “(…) has primarily involved defacing websites with anti-western, anti-Israel and anti-Semitic messages”, as stated by The Anti-Defamation League.
Note: Although AnonGhost “has always been associated with Anonymous(…), the group has stated multiple times that they are not part of Anonymous, but instead just support some of what Anonymous stands for”, as Binary Defence reinforce on their blog.
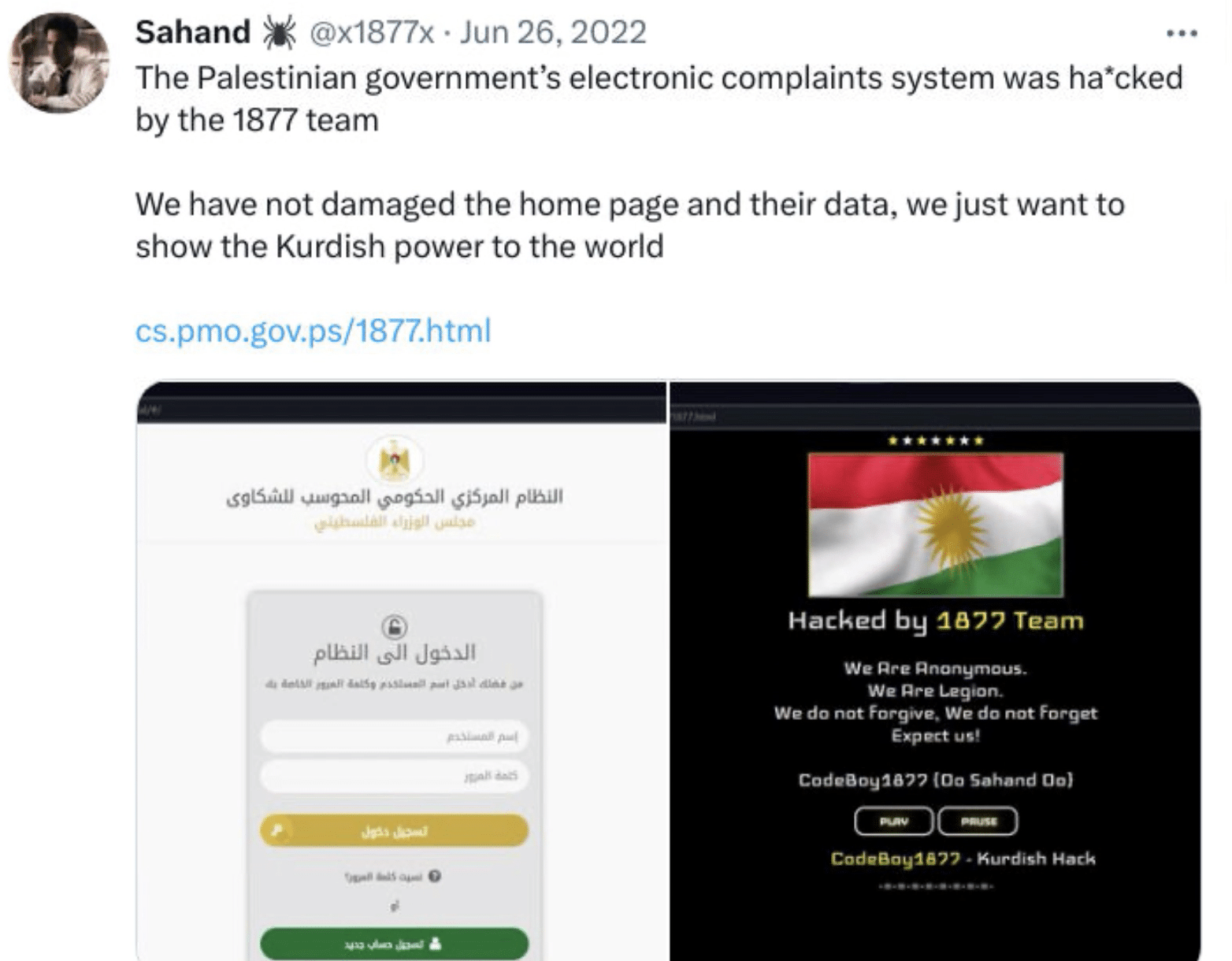
June 2022
- Hijacked the Palestinian government’s electronic complaints system but abstained from damaging the home page or data.
- Attacked the servers of Celebrate, an Israeli Digital Intelligence company, in partnership with the hacking group ALtahrea.
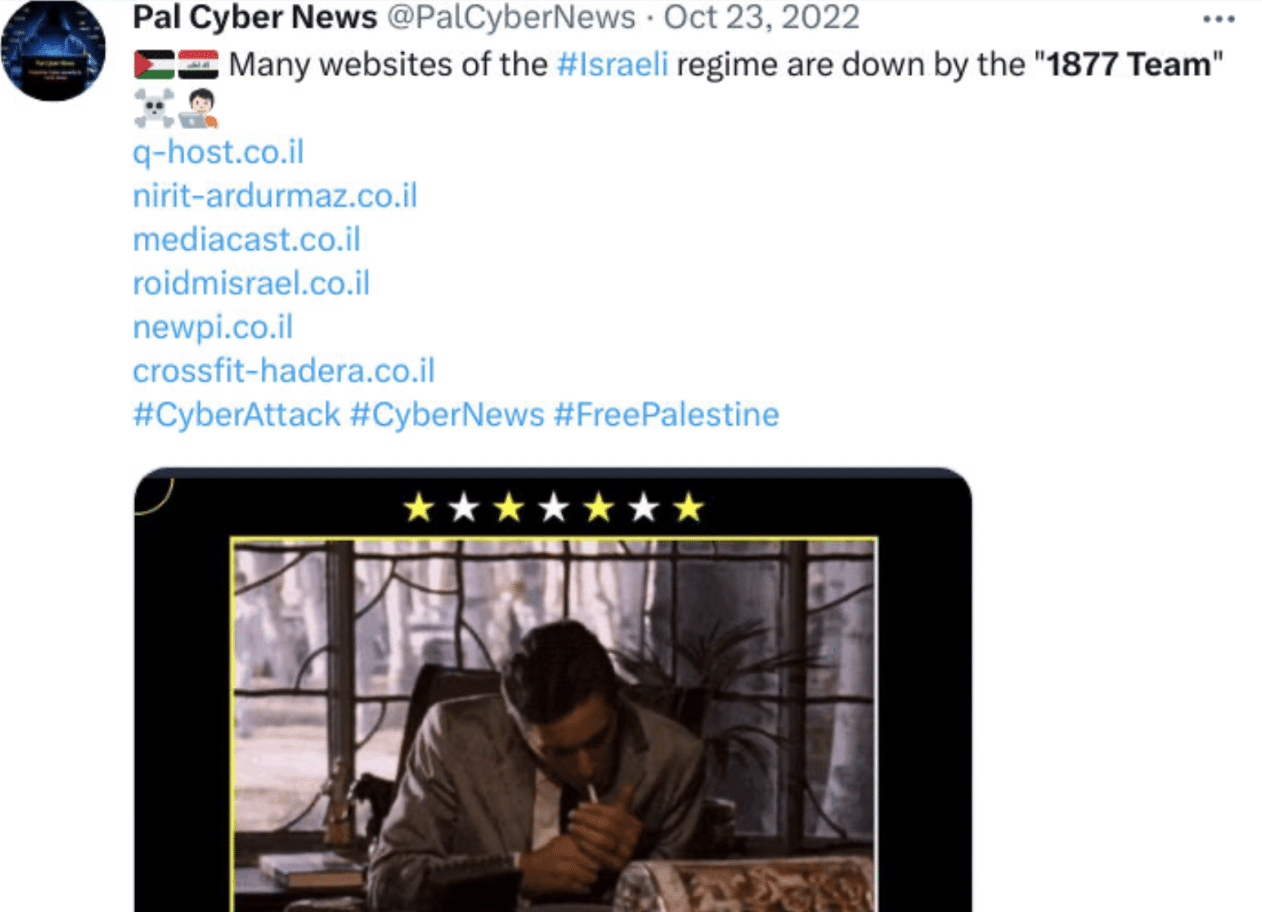
August 2022 – October 2022
- Conducted DDoS attacks on several Israeli websites.
Iran
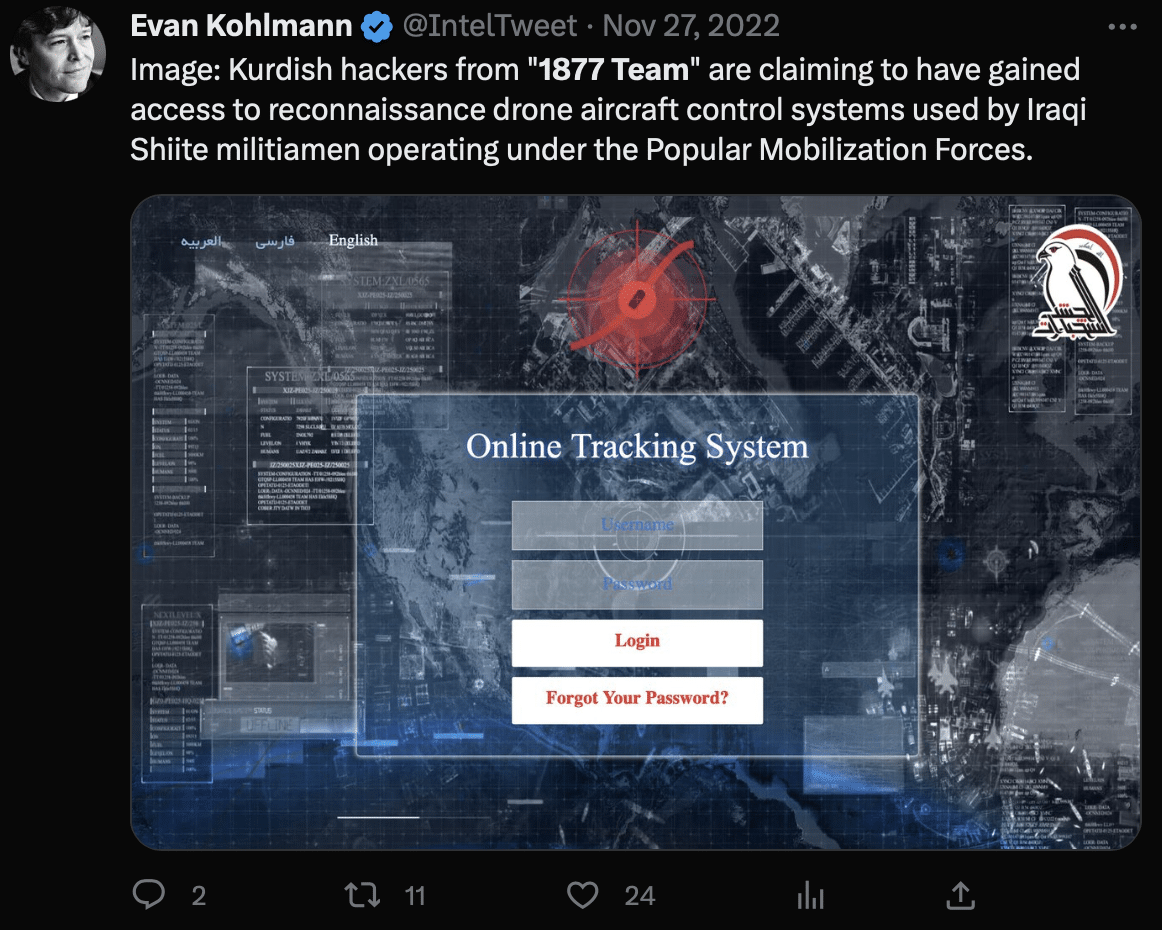
November 2022
- Claimed to have gained access to the reconnaissance drone aircraft control systems used by Iraqi Shiite militiamen, operating under the Popular Mobilization Forces.
February 2023
- Claimed to have hacked the entire databases of AsiaCell, an Iraqi telecom company, and Zain IQ, an Iraqi network and internet provider.
March 2022
- Exposed the personal information of Iranian citizens.
April 2022
- Defaced numerous Iranian websites.
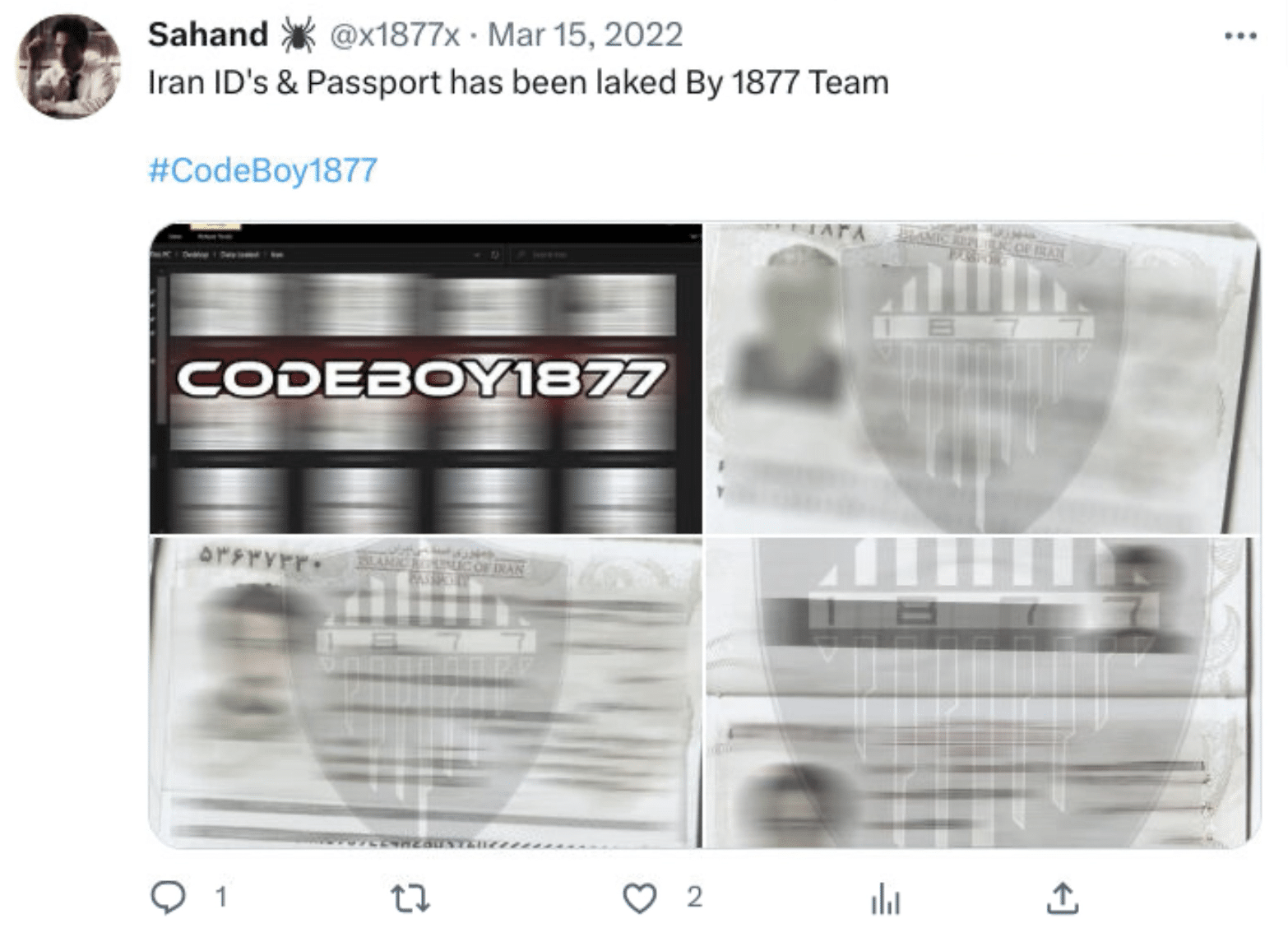
Kurdistan
- January 2023
- Started targeting Kurdish government entities and organizations after allegedly being arrested by the Kurdistan Anti-Terrorism Department (Note: We see no evidence that the group targeted Kurdish entities before 2023)
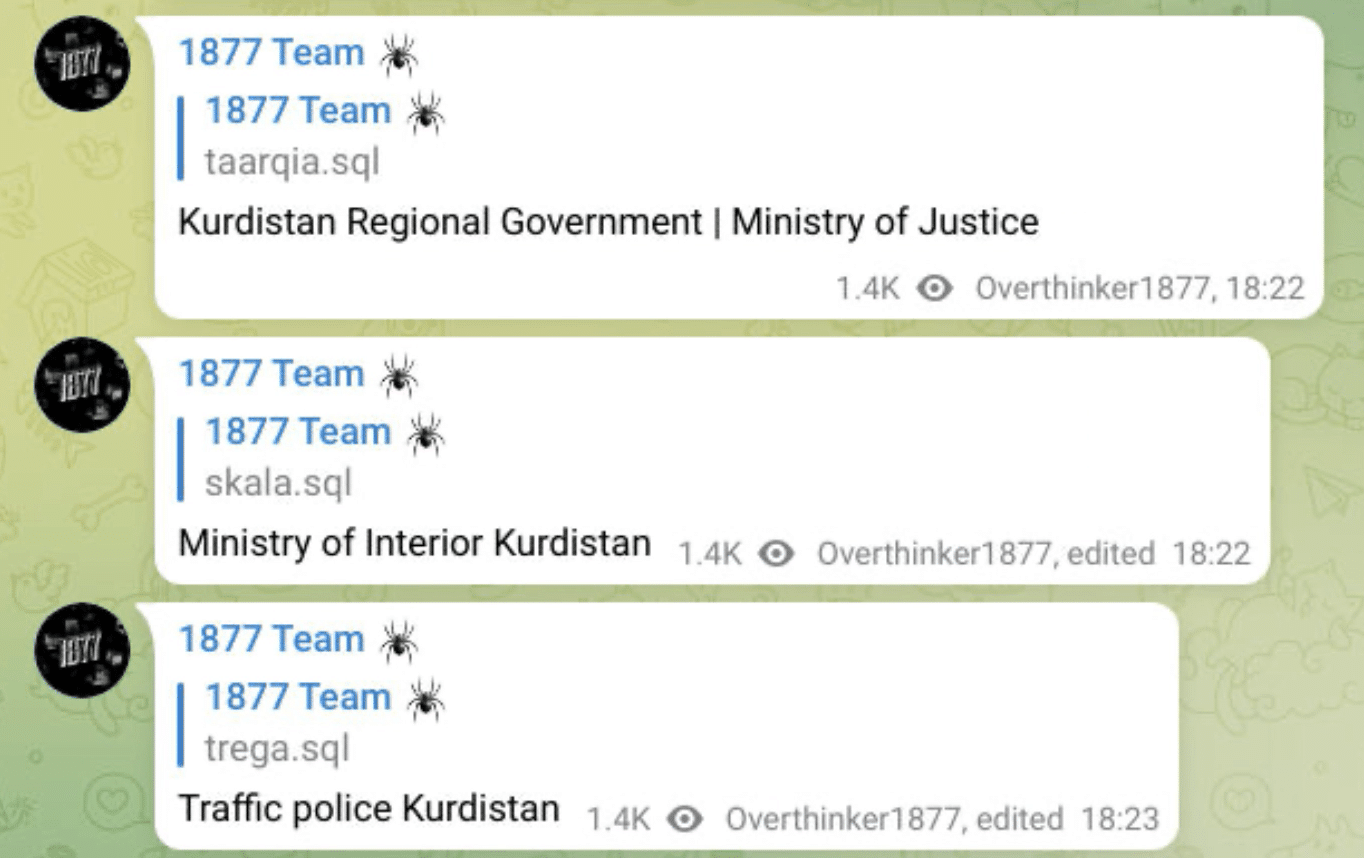
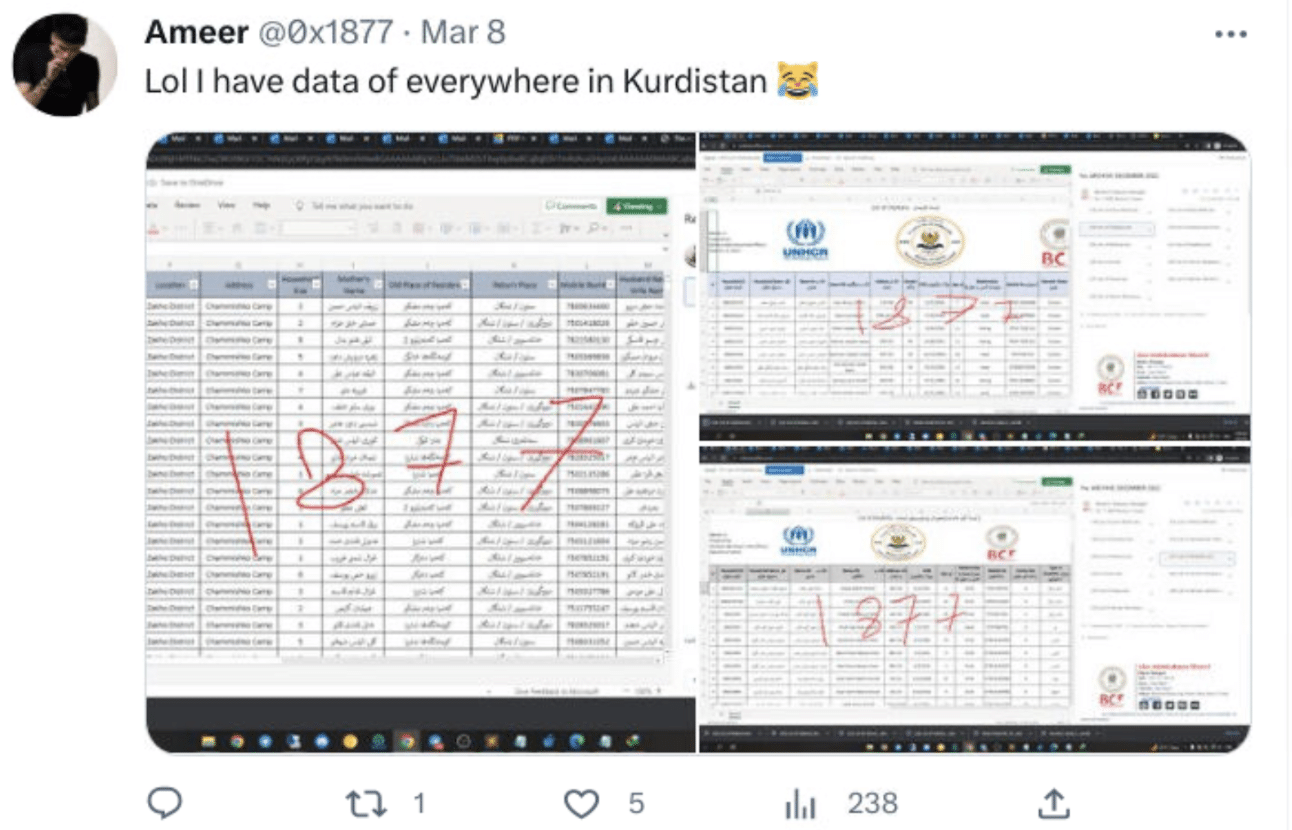
- Leaked databases from the Kurdish Ministry of Justice, Ministry of Interior, and Traffic Police
February 2023 – March 2023
- Asked for data from Korek Telecom, an Iraqi Kurdish mobile phone operator company, in return for data from AsiaCell, an Iraqi telecommunications company.
- Claimed to have breached Korek Telecom.
- Leaked more information from the previously compromised databases from the Kurdish Ministry of Justice, Ministry of Interior and Traffic Police.
- Conducted a DDoS attack against the Kurdish Parliament website.
- Leaked login credentials for Rudaw Media Network, a Kurdish media group.
Turkey
January 2023
- Defaced the Turkish government’s websites.
February 2023
- Continued to deface the Turkish government’s websites.
- Claimed to have breached a server owned by the Turkish government.
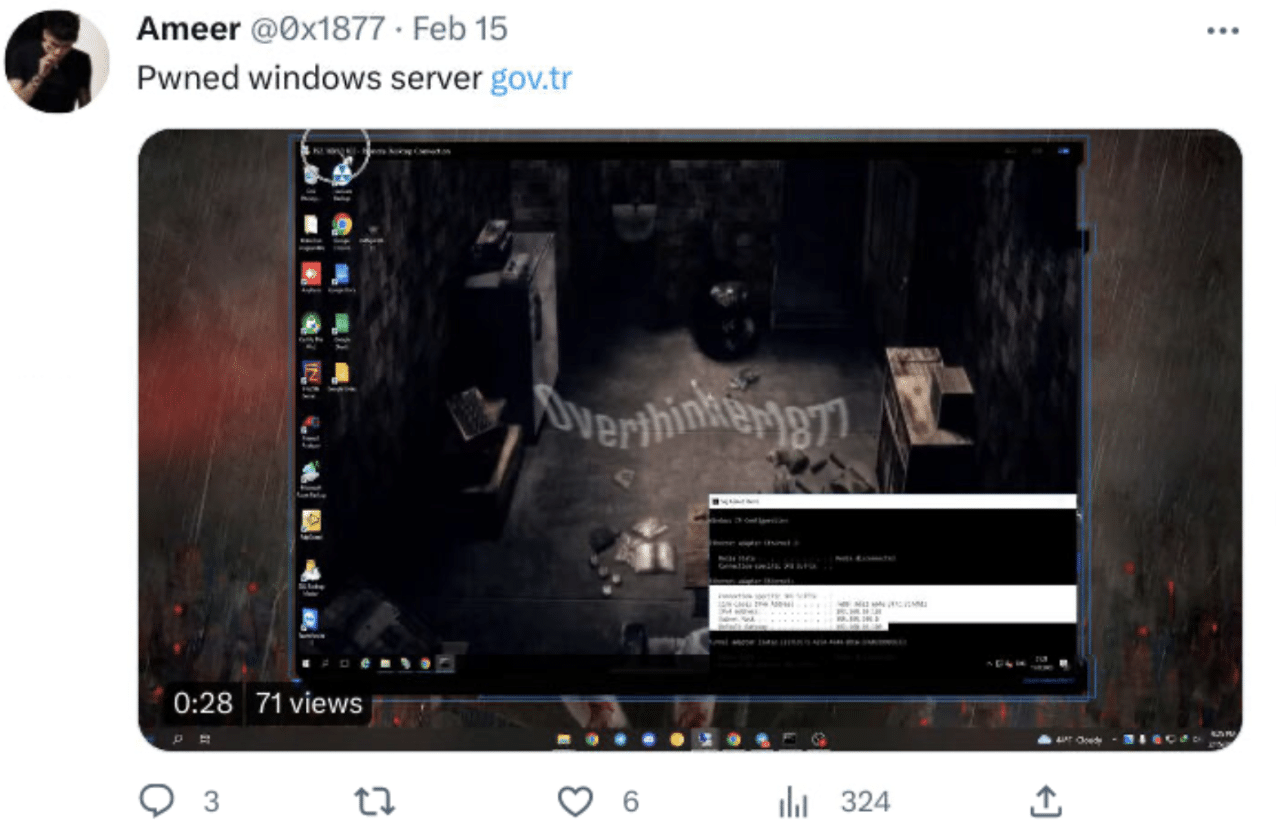
Russo-Ukrainian War
The group’s recent social media interactions indicate they are Russia-aligned.
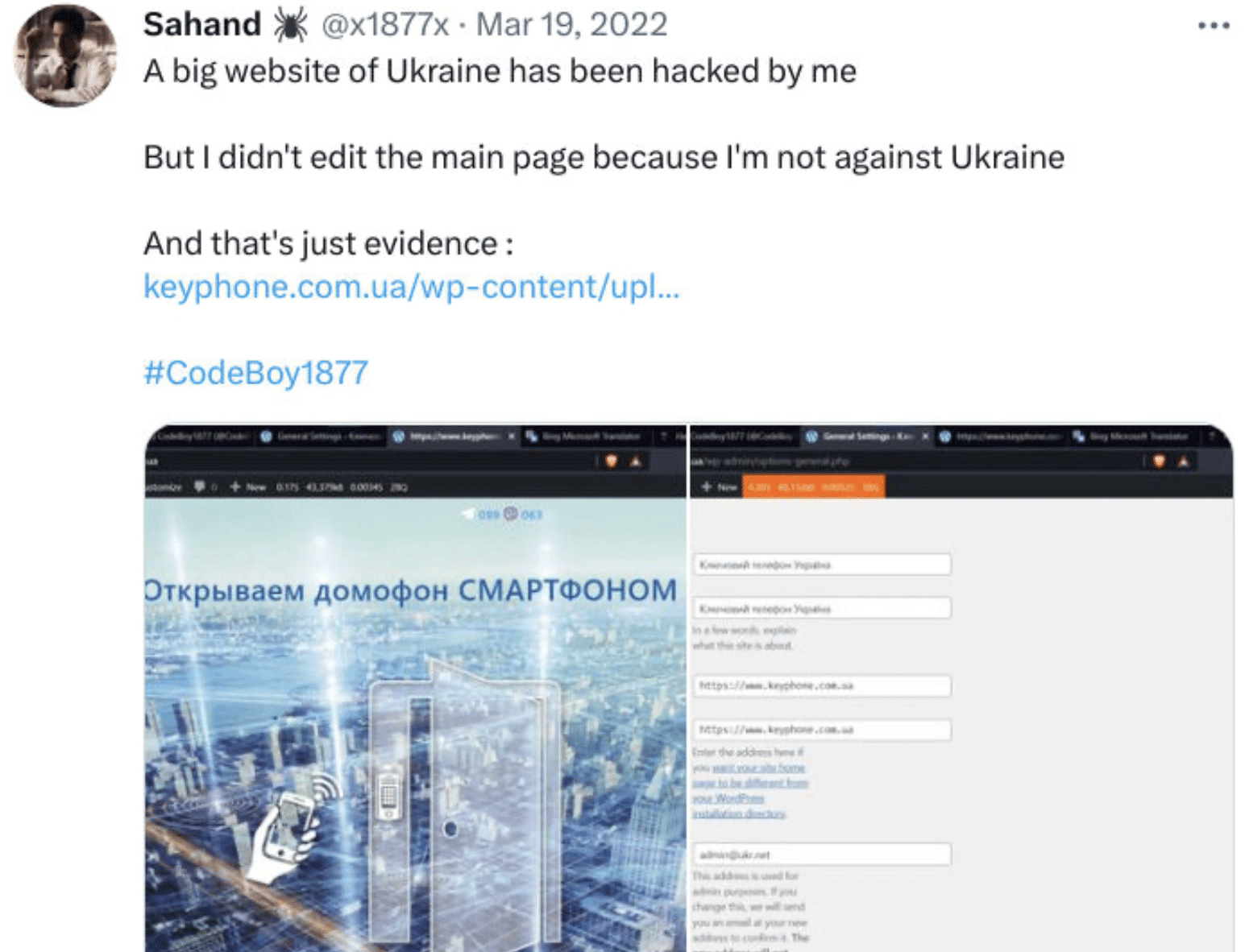
March 2022
- Hacked a Ukrainian website but abstained from defacing the page, claiming “not to be against Ukraine”.
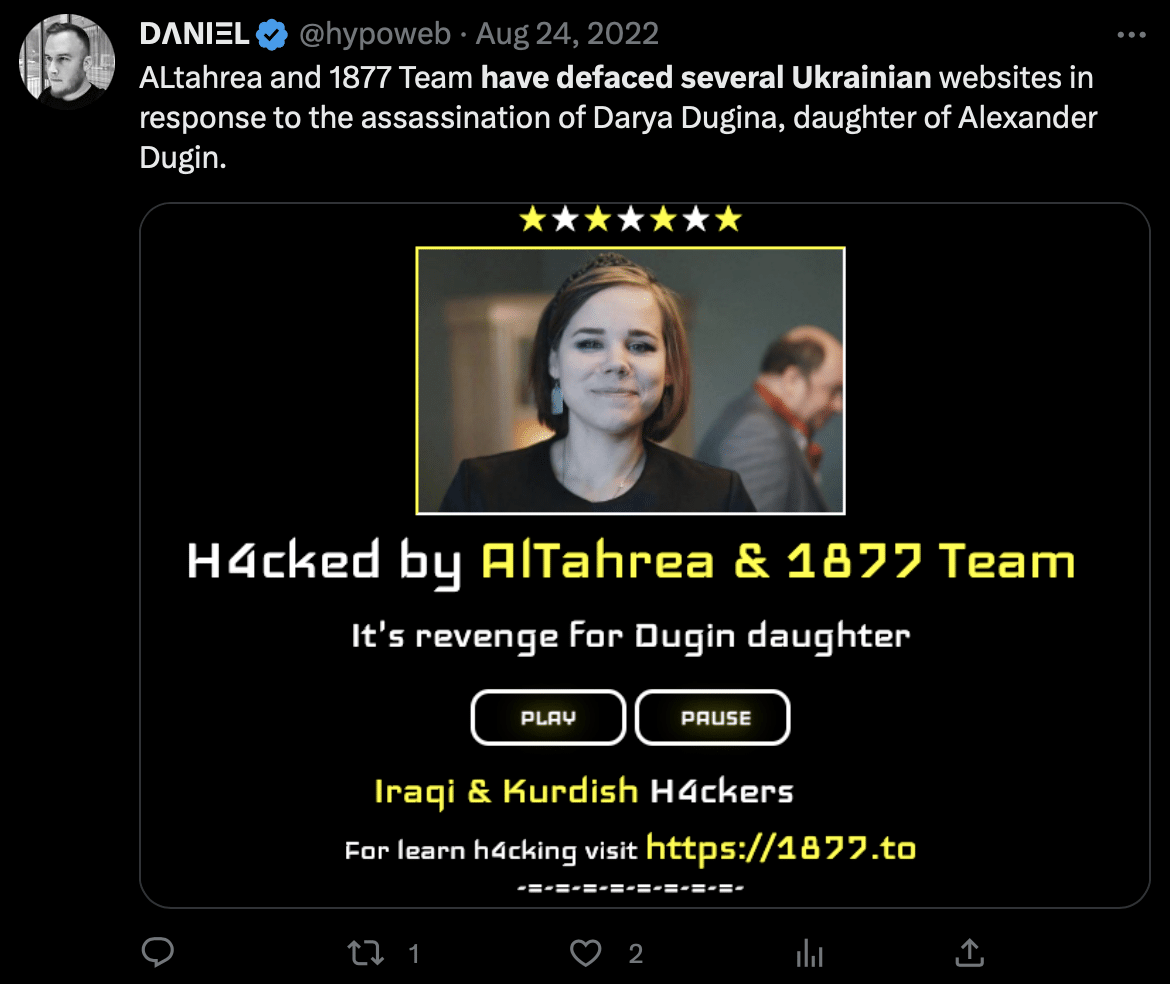
August 2022
- Teamed up with AlTahrea and conducted several defacements against Ukrainian websites following the assassination of Darya Dugina.
December 2022
- Retweeted a link to a Medium blog, where Twitter user “Cyber Known” claims The 1877 team was Pro-Russia.
African, Asian, and Western countries
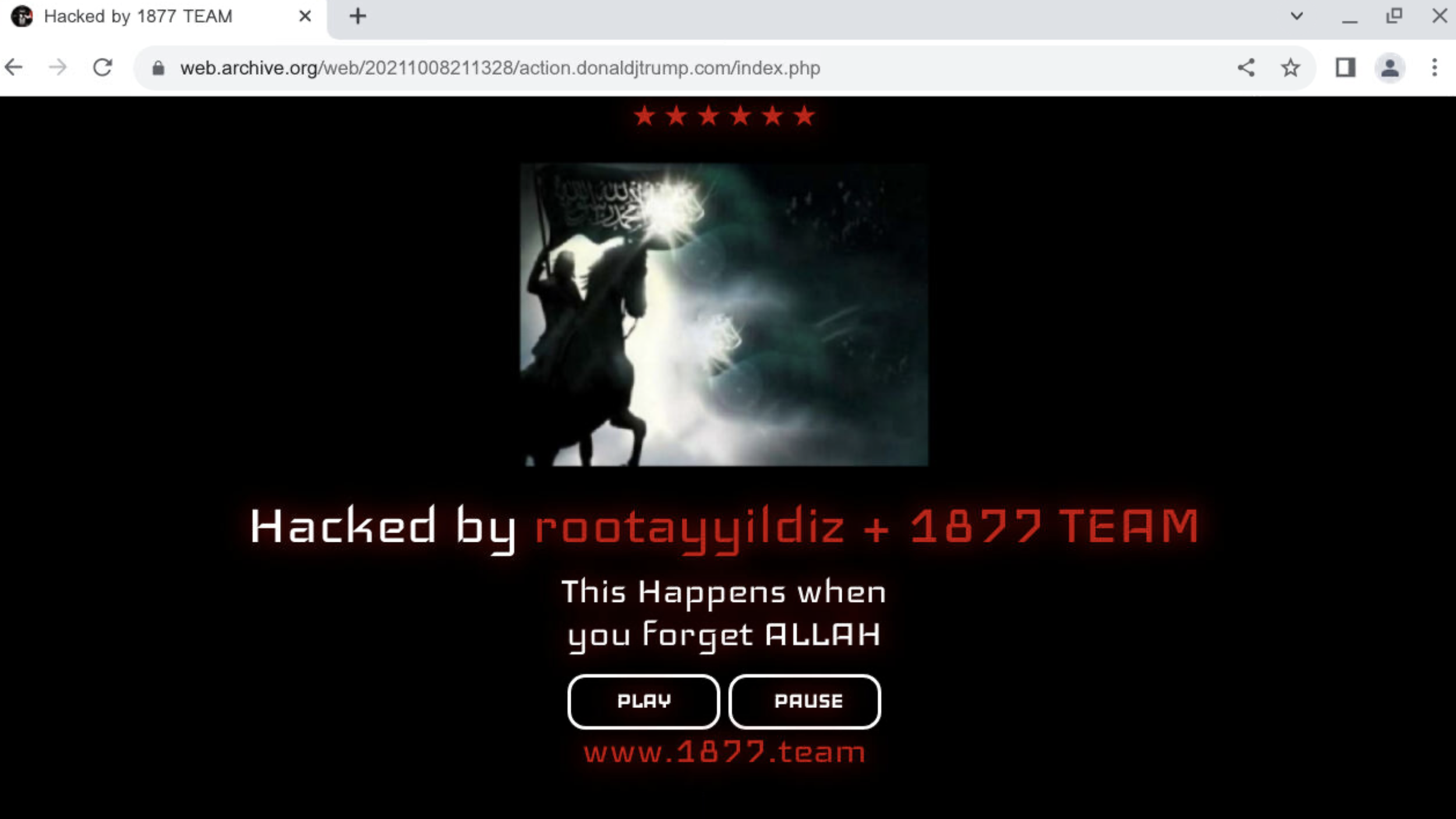
The group claims to have defaced various infrastructure outside of the Middle East, including the websites of Donald J. Trump, CRDB Bank, the Philippines Government, and the Nigerian, Honduran, Indian, and Venezuelan Governments.
These attacks are confirmed and can be viewed on archive[.]org.
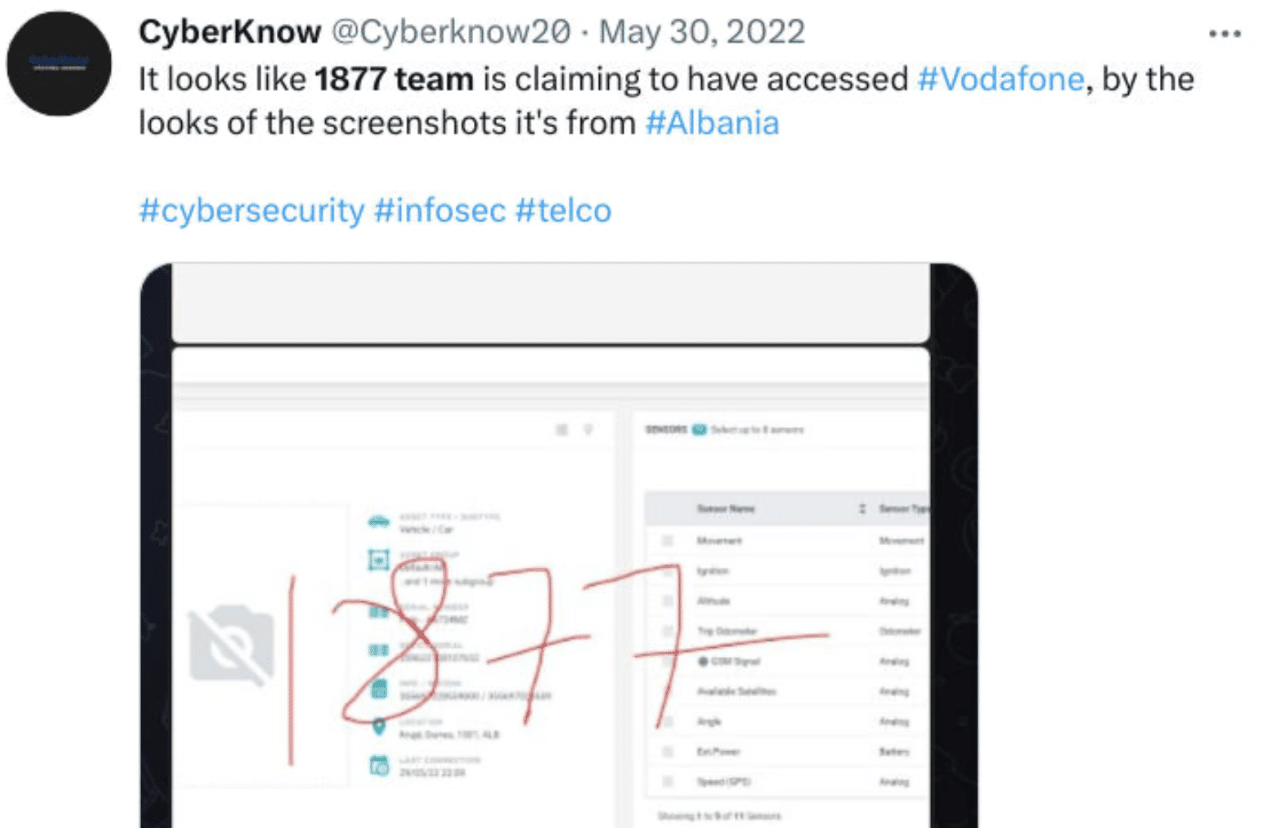
The group also claims to have carried out additional unverified attacks, such as defacement of the Berkeley University website earlier this year, and being linked to an alleged breach of Vodafone, possibly in Albania.
Group infrastructure
Public infrastructure
All subdomains/domains are currently hosted on 185.11.145[.]254.
We’ve not yet discovered any noteworthy information on other IP addresses that previously hosted these subdomains/domains.
- 1877[.]to – English-speaking underground forum
- 1877[.]team – Kurdish-speaking underground forum
- 1877[.]krd – Kurdish-speaking blog
- zone.1877[.]team – defacement archive website
- social.1877[.]team – social media platform
- tube.1877[.]to – video sharing platform
- shop.1877[.]to – hacking tools marketplace
- tools.1877[.]to – free hacking resources
Exposed infrastructure
The threat actor briefly exposed an IP address containing malware samples, exploit panels, log files, and other data.
Pivoting on the IP addresses’ SSL certificate returned related infrastructure.
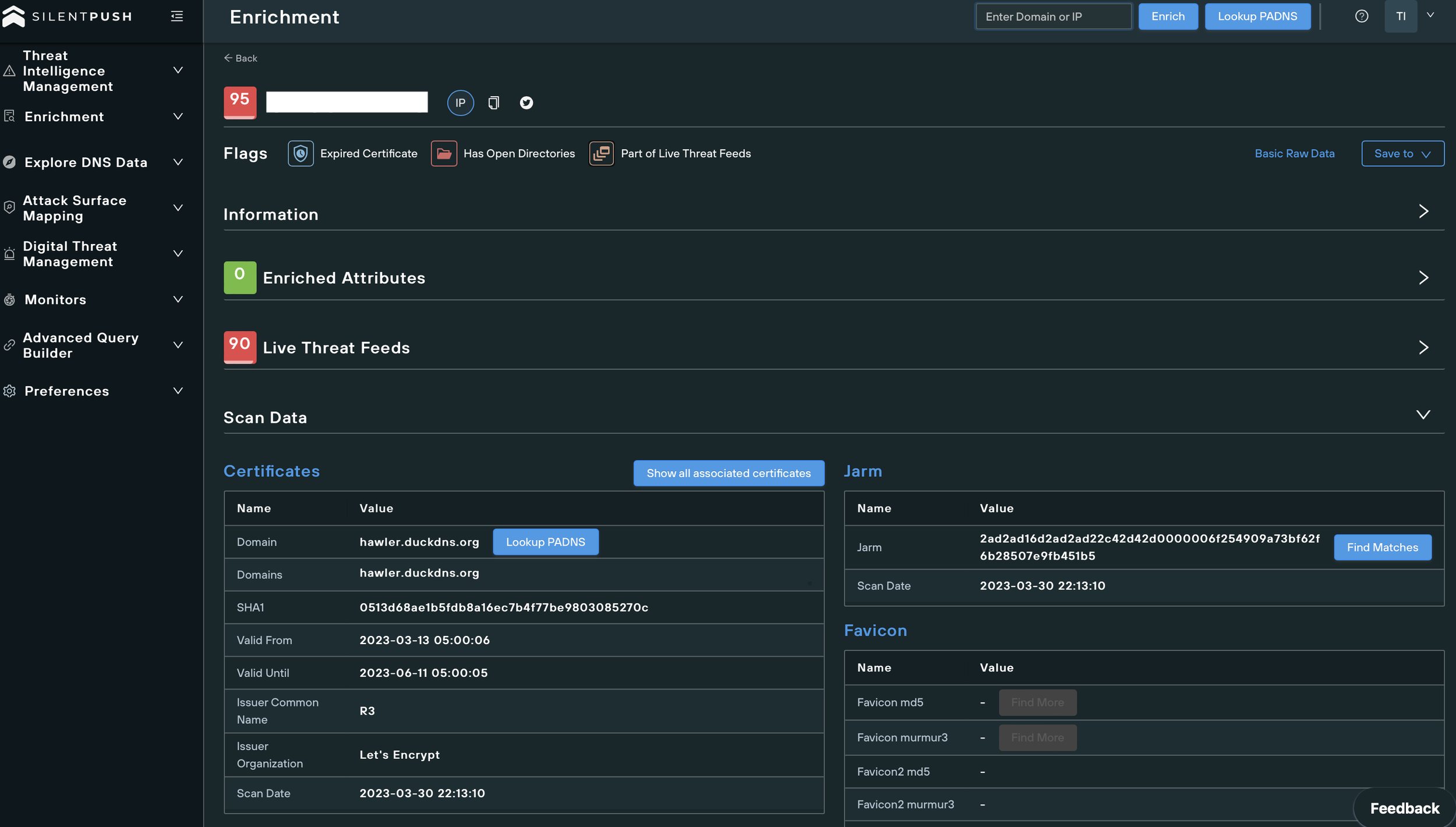
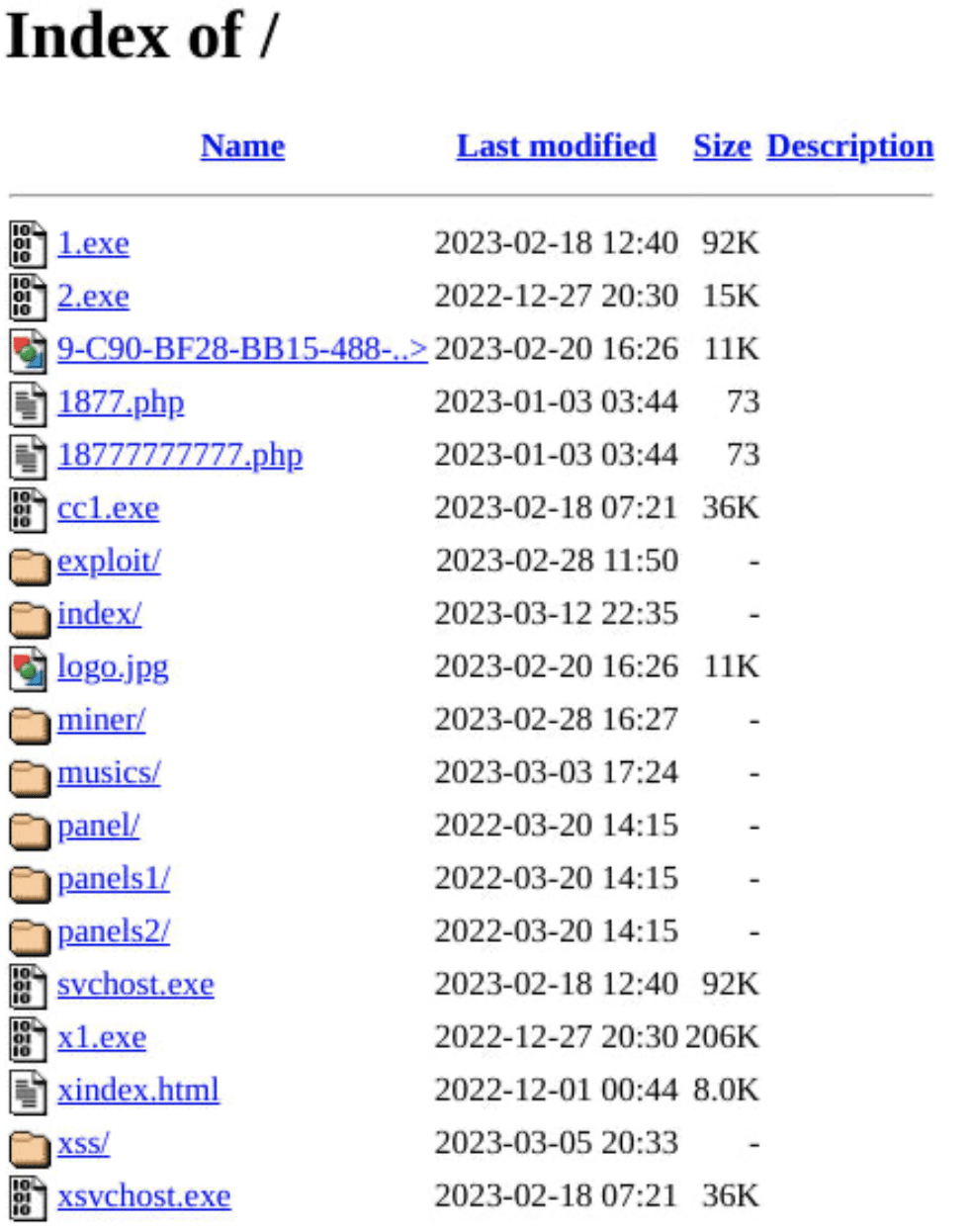
Malware samples
The samples on the open directory were Redline Stealer, RemCos RAT, and ClipBanker.
All samples attempt to connect to the same C2 servers:
- C2 IPs
- 203.156.136[.]113
- 5.206.227[.]115
- C2 domains
- hawler.duckdns[.]org
- overthinker1877.duckdns[.]org
Searching the hashes on VirusTotal showed that several scanners picked up these samples this month, with the last submission date only a few days before the publication of this article, indicating that the threat actor is actively launching malicious campaigns.
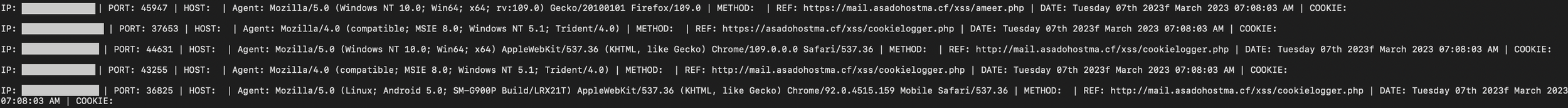
Log file
The entries in the log file result from a PHP cookie stealer — (…)/xss/cookielogger[.]php — that the attackers use in XSS injections.
The file displays hundreds of IP addresses from potential victims, but the cookie values are missing and likely stored using a different method.
Takeaways
The 1877 Team does not yet qualify as an Advanced Persistent Threat. Though the group’s malicious activity has broadened in scope, it is uncertain how disruptive and successful these attacks have been.
The group continuously improved its tactics and implemented numerous new attack vectors. If this behaviour continues, their threat level and reputation will likely increase over time.
It’s impossible to predict whether this threat actor will evolve into an adversary capable of launching sophisticated attacks such as ransomware and cyber espionage, and if so, when. However, given the group’s public presence and close relationship with more advanced entities, the resources and knowledge needed to develop these attack vectors are within reach.
Silent Push categorizes the 1877 Team as an emerging threat that is worthy of attention. The hackers appear intent on positioning themselves as a notable menace, and will likely continue operations that further this goal.
The contents of this report were uncovered using the Silent Push platform.
Sign up for the free Community App to take advantage of our vast array of threat defense tools now.
IOCs
We’ve created a custom feed tracking the 1877 Team’s activity and infrastructure. Silent Push Enterprise Users can search and monitor the IOCs related to this threat actor using the tag sp-blog-2023-05-01.
View our complete list of available threat feeds here.
IP addresses
C2
- 203.156.136[.]113
- 5.206.227[.]115
Other IP addresses
- 185.11.145[.]254
Domains
C2
- hawler.duckdns[.]org
- overthinker1877.duckdns[.]org
Other domains
- 1877[.]to
- 1877[.]team
- 1877[.]krd
- zone.1877[.]team
- social.1877[.]team
- tube.1877[.]team
- shop.1877[.]team
- tools.1877[.]team
- 4567987654345265[.]tk
- asadohostma[.]cf
- asadohostma[.]tk
- balotelaras[.]gq
- bjigcdrfbbcx[.]ml
- bjigcdrfbbcx[.]tk
- bruthoosbxyxio[.]gq
- bsidbxiooohzu[.]ga
- bsidbxiooohzu[.]gq
- bsidbxiooohzu[.]ml
- buhgdkurd444[.]ga
- coalermallwive[.]ga
- forever0g[.]tk
- ghiiidueebsxiis[.]ml
- ghiiidueebsxiis[.]tk
- hsushzidooonsnx[.]gq
- htetryfugyioiyut[.]ml
- huncho[.]ml
- jfueytg7yghg[.]ga
- jihugkyfjtdsrytsrd[.]cf
- jihugkyfjtdsrytsrd[.]gq
- makolo[.]ml
- oiuryhgyefdter[.]gq
- salogo[.]gq
- steetdre6iazwed[.]tk
- stiwebbro[.]ml
- stupuviijvftuiu[.]cf
- tgfr43e98uj43ef[.]ml
- torontos[.]ga
- unconditional[.]gq
- vanuboutst[.]cf
- vanuboutst[.]ml
- wpojgbjffy444[.]cf
- www.4567987654345265[.]tk
- www.asadohostma[.]cf
- www.asadohostma[.]tk
- www.balotelaras[.]gq
- www.bjigcdrfbbcx[.]ml
- www.bjigcdrfbbcx[.]tk
- www.bruthoosbxyxio[.]gq
- www.bruthoosbxyxio[.]tk
- www.bsidbxiooohzu[.]ga
- www.bsidbxiooohzu[.]gq
- www.buhgdkurd444[.]ga
- www.coalermallwive[.]ga
- www.forever0g[.]tk
- www.ghiiidueebsxiis[.]ml
- www.hawler.duckdns[.]org
- www.hsushzidooonsnx[.]gq
- www.htetryfugyioiyut[.]ml
- www.huncho[.]ml
- www.jagajaga[.]ga
- www.jfueytg7yghg[.]ga
- www.jihugkyfjtdsrytsrd[.]cf
- www.jihugkyfjtdsrytsrd[.]gq
- www.linkup[.]pics
- www.oiuryhgyefdter[.]gq
- www.salogo[.]gq
- www.steetdre6iazwed[.]tk
- www.stiwebbro[.]ml
- www.stupuviijvftuiu[.]cf
- www.tgfr43e98uj43ef[.]ml
- www.torontos[.]ga
- www.ukyudrst.zyns[.]com
- www.vanuboutst[.]cf
- www.wpojgbjffy444[.]cf
- www.yjksvjdbjdbjjda[.]cf
- www.yjksvjdbjdbjjda[.]ga
- www.yjksvjdbjdbjjda[.]ml
- www.yjksvjdbjdbjjda[.]tk
- yjksvjdbjdbjjda[.]cf
- yjksvjdbjdbjjda[.]ga
- yjksvjdbjdbjjda[.]ml
- yjksvjdbjdbjjda[.]tk
Domains using DDNS services
- facebookmessages.serveuser[.]com
- facebooktie.faqserv[.]com
- hawler.duckdns[.]org
- hunchoooof.2waky[.]com
- jhssales.dynamic-dns[.]net
- juyhtrdwski.sexidude[.]com
- kjuhygtrfdewsa.onedumb[.]com
- mail.bsabshjlinacafs.serveuser[.]com
- mail.facebookmessages.serveuser[.]com
- mail.guyyyeyb.youdontcare[.]com
- mail.inlinkedlnmessagesdigiter.serveuser[.]com
- mail.jhdfgdjkdg.dynamic-dns[.]net
- mail.jhuyghft.dynamic-dns[.]net
- mail.juyhtrdwski.sexidude[.]com
- mail.kasawaraswgu.yourtrap[.]com
- mail.mnfdxcvbn.cleansite[.]info
- mail.ohssbxxwaqmbccxk.x24hr[.]com
- mail.oiytiuopiuy.almostmy[.]com
- mail.roboroboo.dumb1[.]com
- mail.rywrhsg.dns05[.]com
- mail.sdhgdfth.zzux[.]com
- mail.snhyjhakua.x24hr[.]com
- mangersales.zyns[.]com
- nmjvutdwrw.dns04[.]com
- saqwijfde4ojhbyvubi.b0tnet[.]com
- servercheck.zyns[.]com
- supplypurchase.dns04[.]com
- tradefaregoods.dns04[.]com
- ukyudrst.zyns[.]com
- www.dxfcvhhgfgcv.dnsfailover[.]net
- www.gartytrgfredsw.sexidude[.]com
- www.gatasawatoyo.dumb1[.]com
- www.hgtgerfdrty.onedumb[.]com
- www.hunchifigkf.wikaba[.]com
- www.hunchooo.zzux[.]com
- www.incxzsdcuuwqag.serveuser[.]com
- www.inlinkedlnmessagesdigiter.serveuser[.]com
- www.jhdfgdjkdg.dynamic-dns[.]net
- www.jhuyghft.dynamic-dns[.]net
- www.jnhbvgcfxdzsdzdsxd.dns2[.]us
- www.juyhtrdwski.sexidude[.]com
- www.kbbkbkuu.dynamic-dns[.]net
- www.linkedlndeed.fartit[.]com
- www.marketingadmin.port25[.]biz
- www.mnjgyutjfo.longmusic[.]com
- www.mssjhgwe.toh[.]info
- www.servercheck.zyns[.]com
- www.sxdfcghvjhbkkredirec.serveusers[.]com
- www.uqjswjwswsjwsh.serveuser[.]com
- www.uytresgfgh.changeip[.]co
Malware samples
- 148264565031a8ebb6887a1395a2247a
- b3503746bb7f1d30755c9f4a26ce0a2c
- 99e19c4a4a8a972005902bf6129867e9
- 334c23c94f9c6587e2afd0689796daa8791fda9b823b23836893b86f5cce849f
- 683fa1e449da9b71d0cafefb107efd97f0f8163f844dd837d12c354c2b901b93