"Tis the season to be wary": Silent Push tracks Russia-linked threat actor involved in US political spoofing and crypto giveaway scams. Large cluster of IOFA domains discovered.

Executive Summary
Silent Push Threat Analysts are tracking a threat actor, with links to Russia, who is actively deploying domains involved in crypto scams targeting the US Presidential Election, and prominent US tech brands.
The scams involve fake giveaways of Bitcoin and Ethereum cryptocurrency. Users are being asked to send coins to an attacker-controlled wallet, with the promise of double the amount of coins being returned to them.
Our research has unearthed a large number of websites featuring prominent US political figures, business leaders and global brand names advertising the fake giveaways, with counterfeit legal letters from US Government agencies attached to the domains to add legitimacy to the scam.
Individuals targeted include Former President Donald Trump, Vice President Kamala Harris, Apple CEO Tim Cook, Elon Musk, MicroStrategy co-founder Michael Saylor, Former Congressman Gene Green, Former Congressman Pete Olson, Peggy Kim (SEC), and Kerry O’Brien (FTC).
Brands and political institutions targeted include Apple, SpaceX, Donald Trump for President 2024 Campaign, MicroStrategy, Cardona Foundation, U.S. House of Representatives, U.S. Securities and Exchange Commission, and the U.S. Federal Trade Commission.
Background
Over the last 6 months, numerous reports have been published of websites using the image and likeness of Elon Musk and Donald Trump to propagate crypto scams, including AI deepfake videos.
Threat actors have hacked the YouTube channels of prominent social media personalities, and international sporting events, before posting videos promoting the scam to millions of subscribers.
Tracking the campaign
While investigating an unrelated campaign, our Threat Analysts discovered Indicator of Future Attack (IOFA) domains registered to the Russian email address [email protected], that suggested involvement in the aforementioned scams.
We executed an advanced content lookup using Silent Push Web Scanner, and what we knew about the deployment, management and on-page content of the aforementioned infrastructure, that revealed a cluster of live scam domains with the following shared characteristics:
- Registered to [email protected]
- Hosted behind Cloudflare
- Similar themes, revolving around cryptocurrency, US financial/tech organizations, and the upcoming US Presidential Election (e.g. trumpdebate24[.]com), with matching body content
- Pages hidden behind a CAPTCHA
- Some pages featuring a chat function
One of the sites in the cluster features Russian language content – cryptologic[.]online – but seemingly isn’t involved in directly spoofing any organizations or individuals.
Analyzing domain content
Although some domains in the cluster have been identified as malicious and taken down by Cloudflare, there are still a number of domains live as of writing.
Here’s a sample of domains from the cluster, spoofing well-known US politicians, and business leaders:
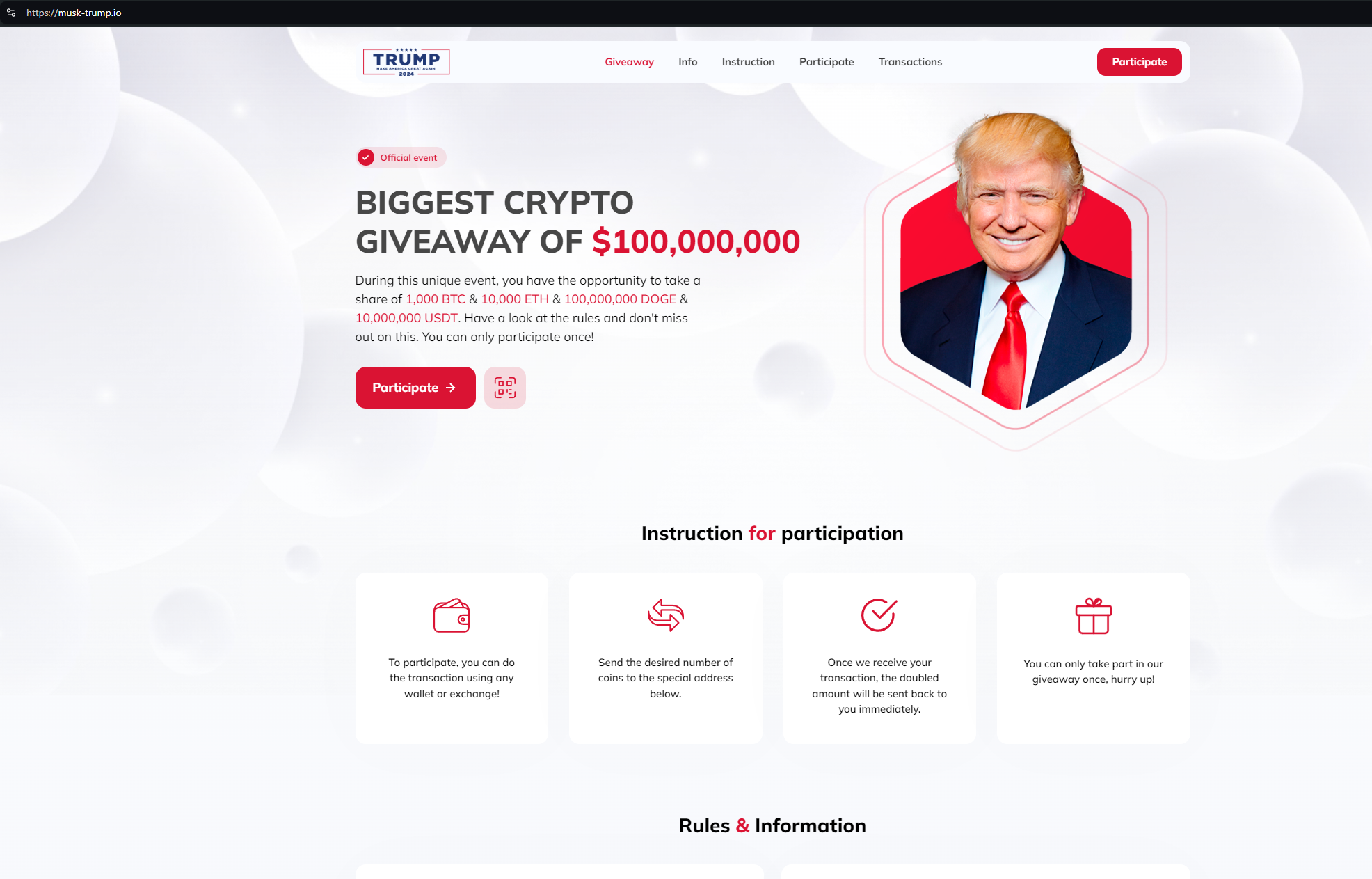
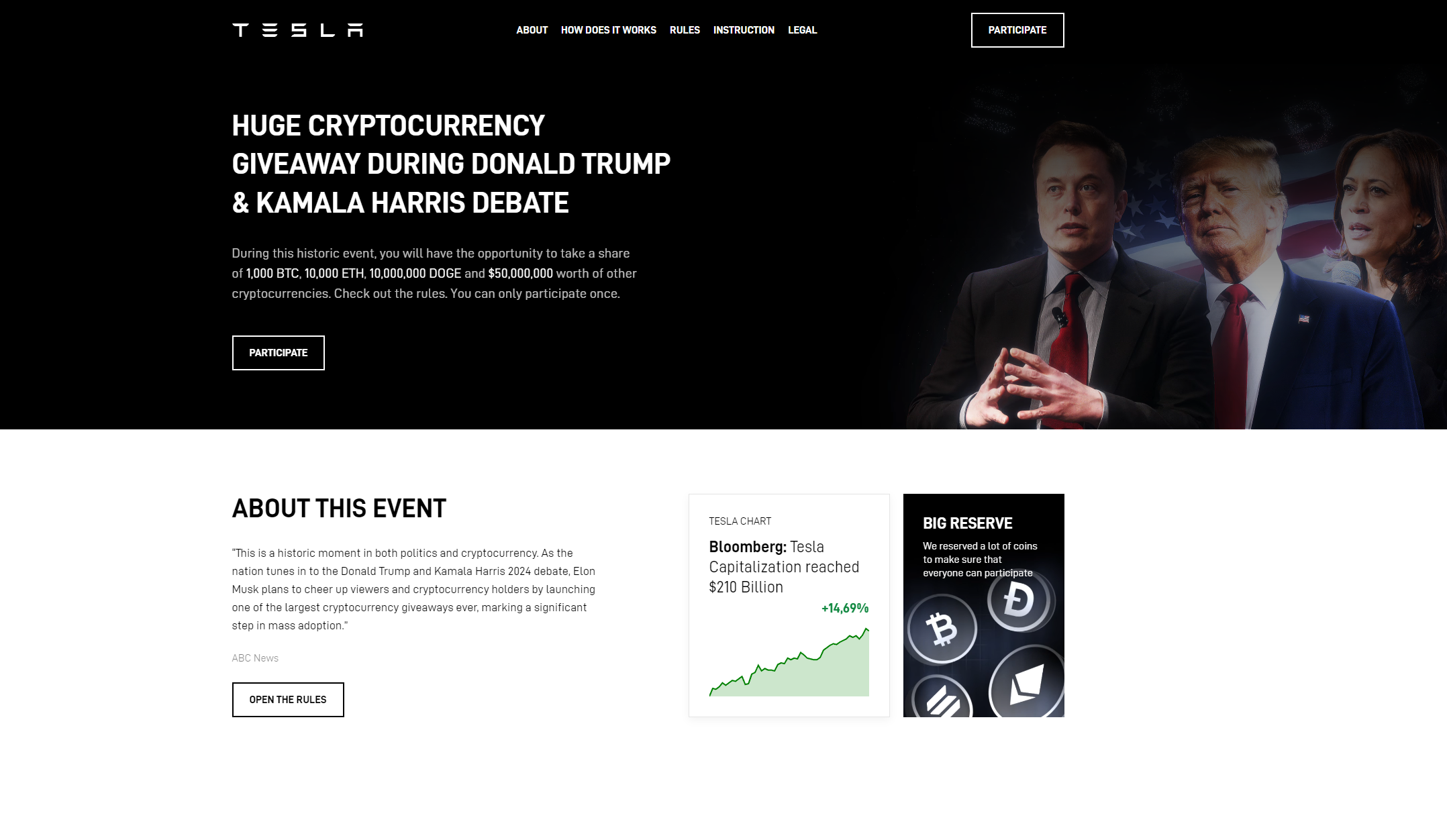
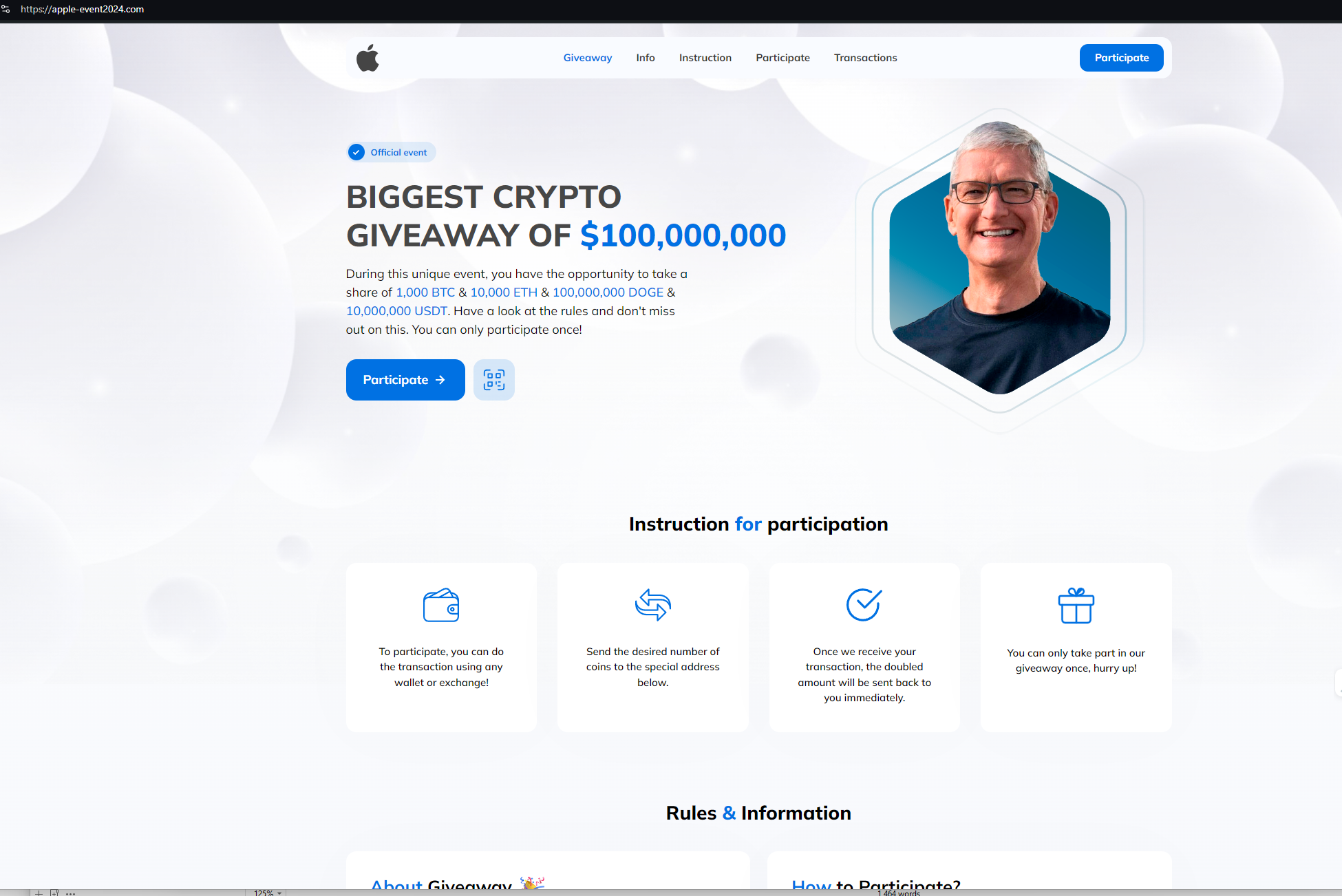
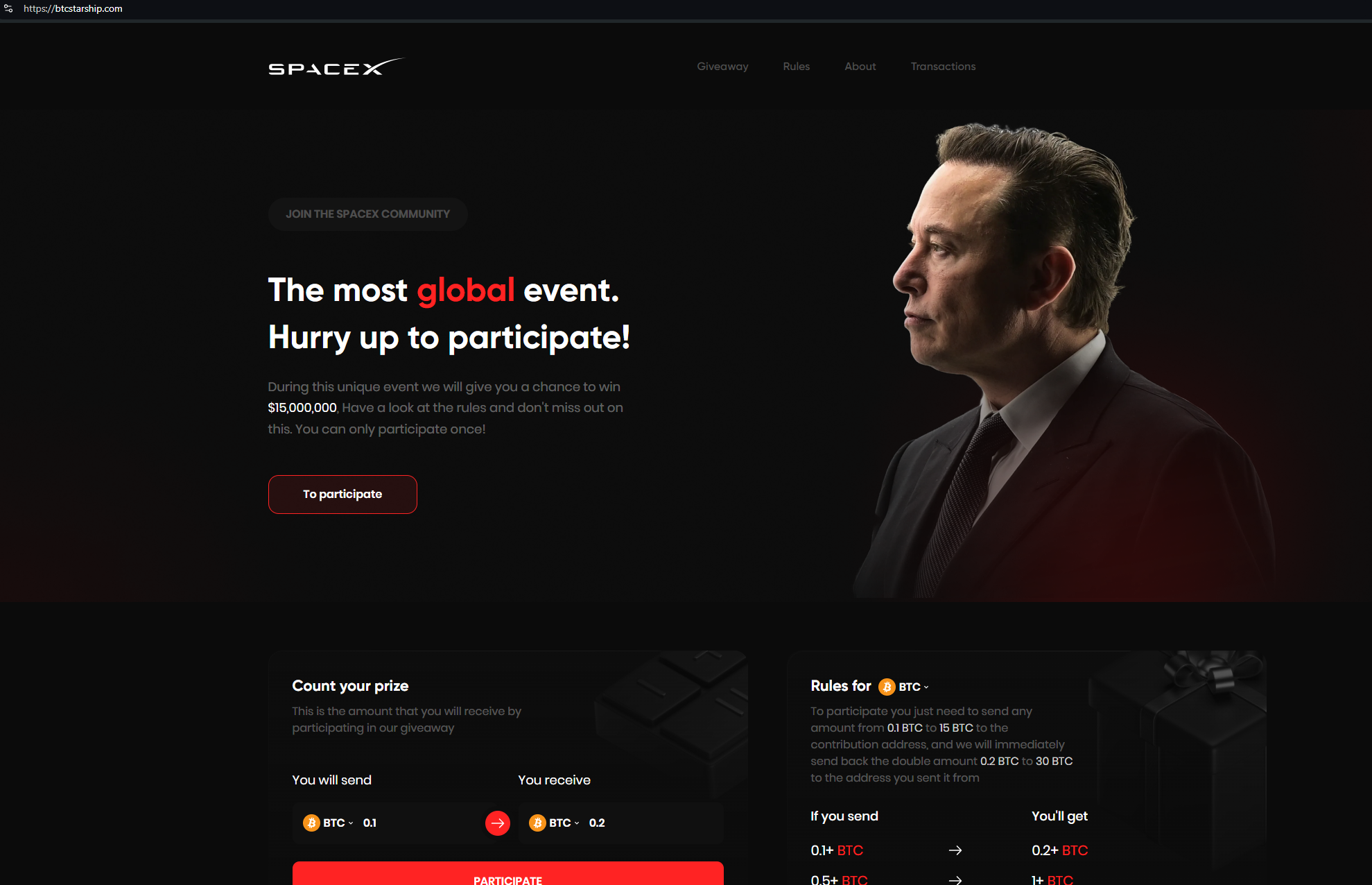
Following the link on trump-debate[.]com, users are asked to participate in a “giveaway” by sending Ethereum coins to the wallet address 0x207Fe723F8B0d864A4Ae4e3B5F064883F207c642.
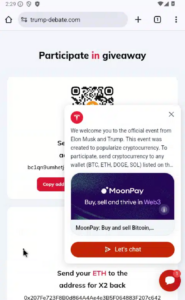
Initiating the transfer via chat functionality
Some domains also feature a chat function, that gives specific instructions on how to send transfer coins, prior to receiving “payment” from the scammers.
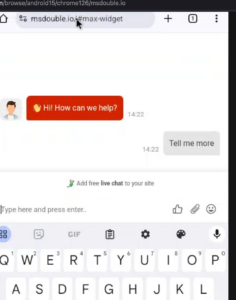
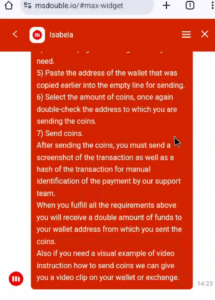
Fraudulent domain footer content
Several domains we encountered featured footer content that included fake legal letters from US regulatory bodies, legitimizing the proposed “giveaways” as sanctioned by the SEC, FTC and DOJ.
Here’s an example letter from debate[.]gives, involved in Tesla and US political debate spoofing:
![Legal “disclaimer” on debate[.]gives](https://www.silentpush.com/wp-content/uploads/image-115.png)
![Fake FTC letter @ debate[.]gives](https://www.silentpush.com/wp-content/uploads/image-116.png)
![Fake DOJ letter @ debate[.]gives](https://www.silentpush.com/wp-content/uploads/image-117.png)
Mitigation
Our Analysts are constructing a Silent Push IOFA Feed containing all the scam domains gathered during our investigation.
Enterprise users can ingest this data into their security stack to inform their detection protocols, or use it to pivot across attacker infrastructure using the Silent Push Console and Feed Analytics screen.
Register for Community Edition
Throughout our investigation, we used the Silent Push Web Scanner to search for matching content elements and linked DNS infrastructure.
Web Scanner is available free as part of a Silent Push Community Edition subscription. Sign-up here.
IOFAs
- trumpdebate24[.]com
- cryptologic[.]online
- musk.trump[.]io
- apple-event2024[.]com
- btcstarship[.]com
- debate[.]gives
- 0x207Fe723F8B0d864A4Ae4e3B5F064883F207c642


