Priority Use Cases
for SOC, IR and CTI Teams
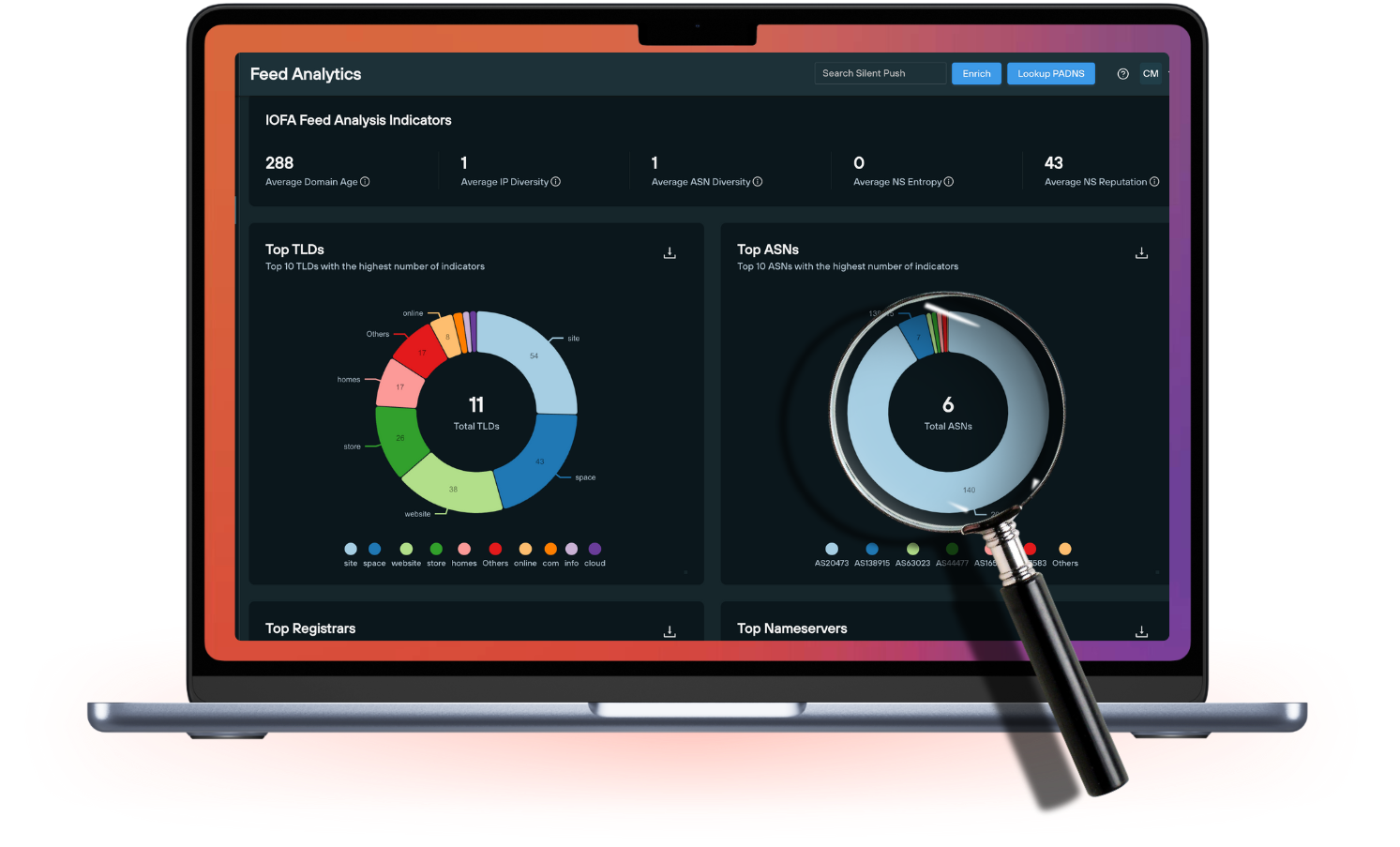
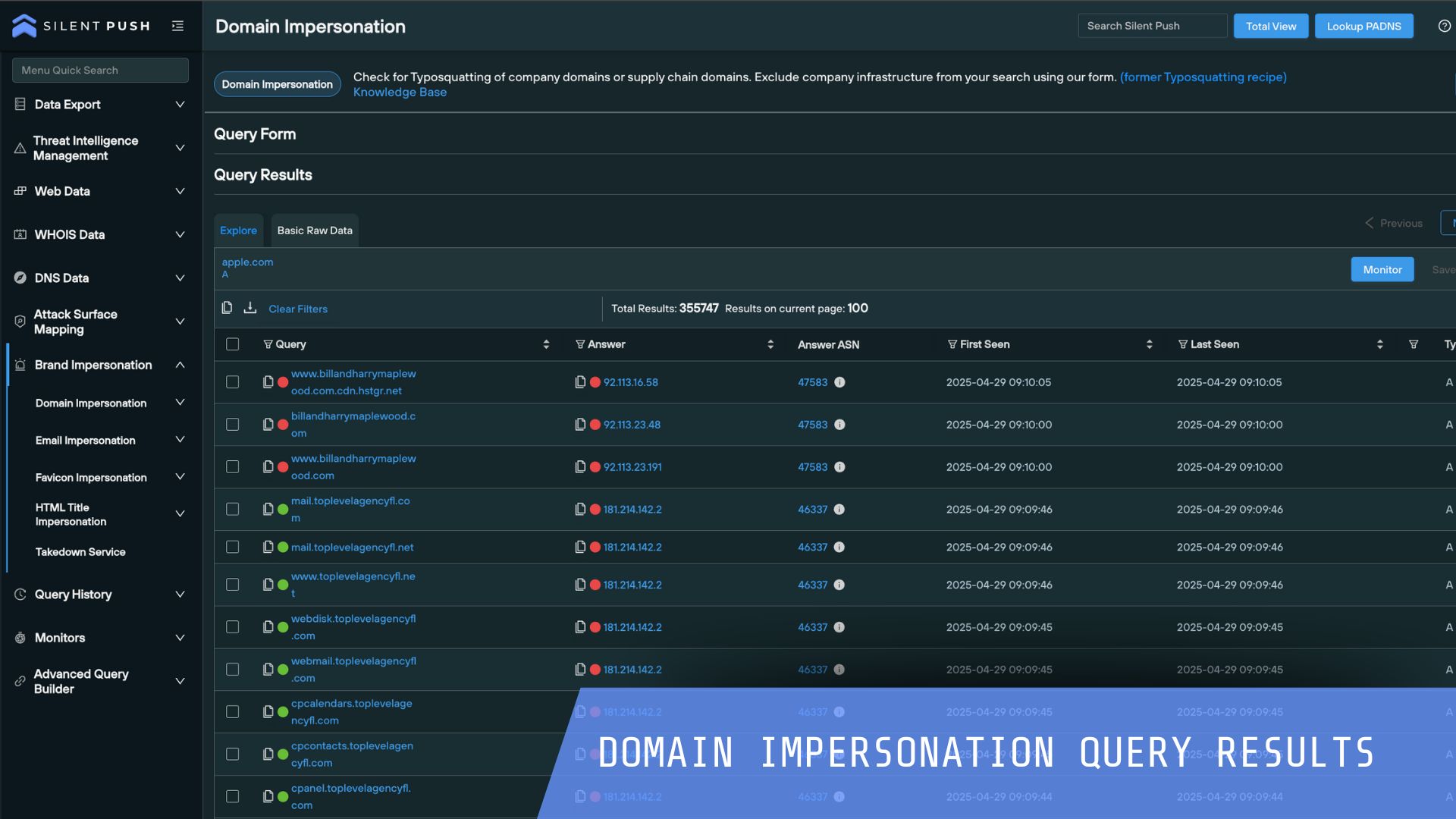
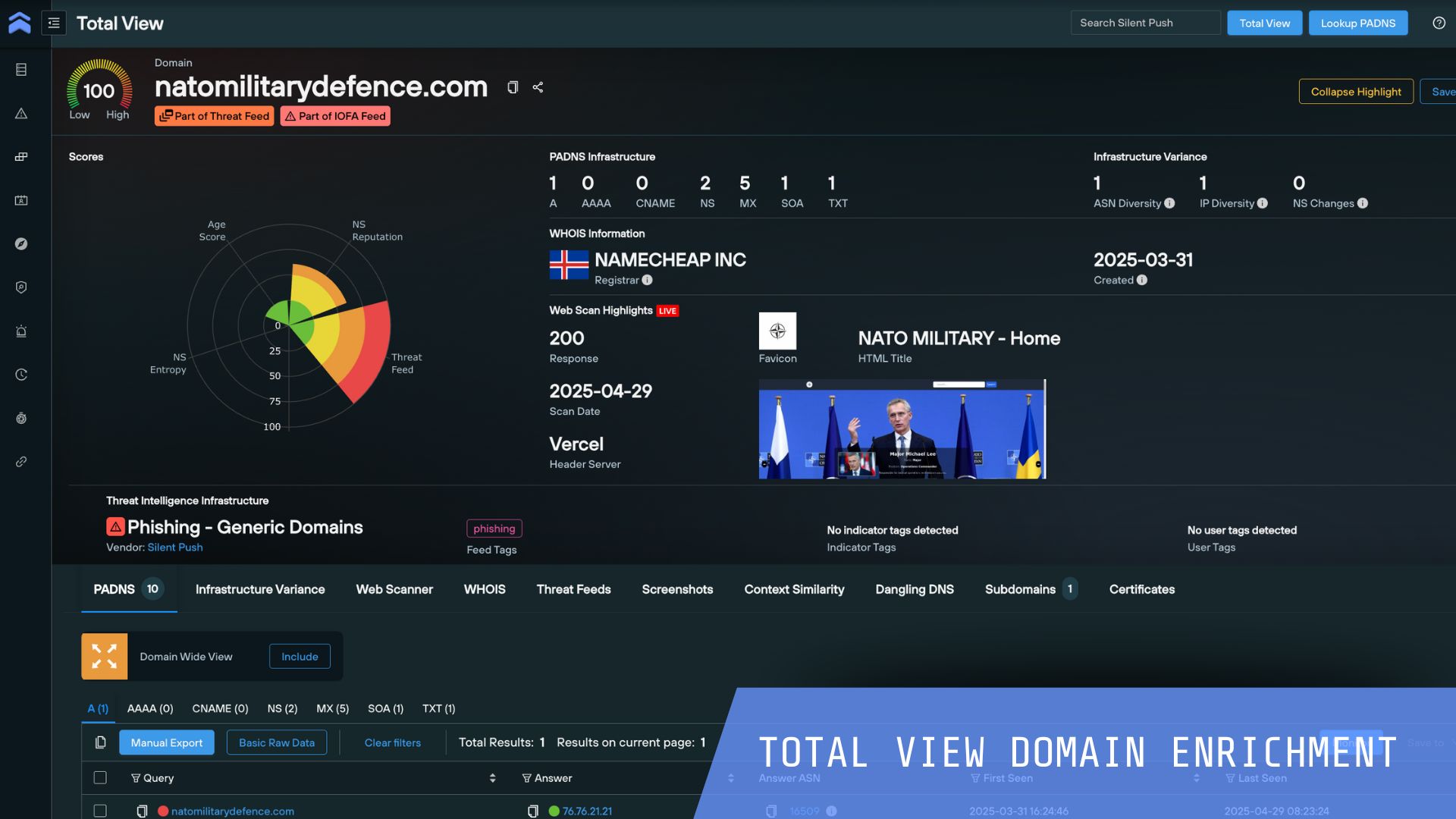
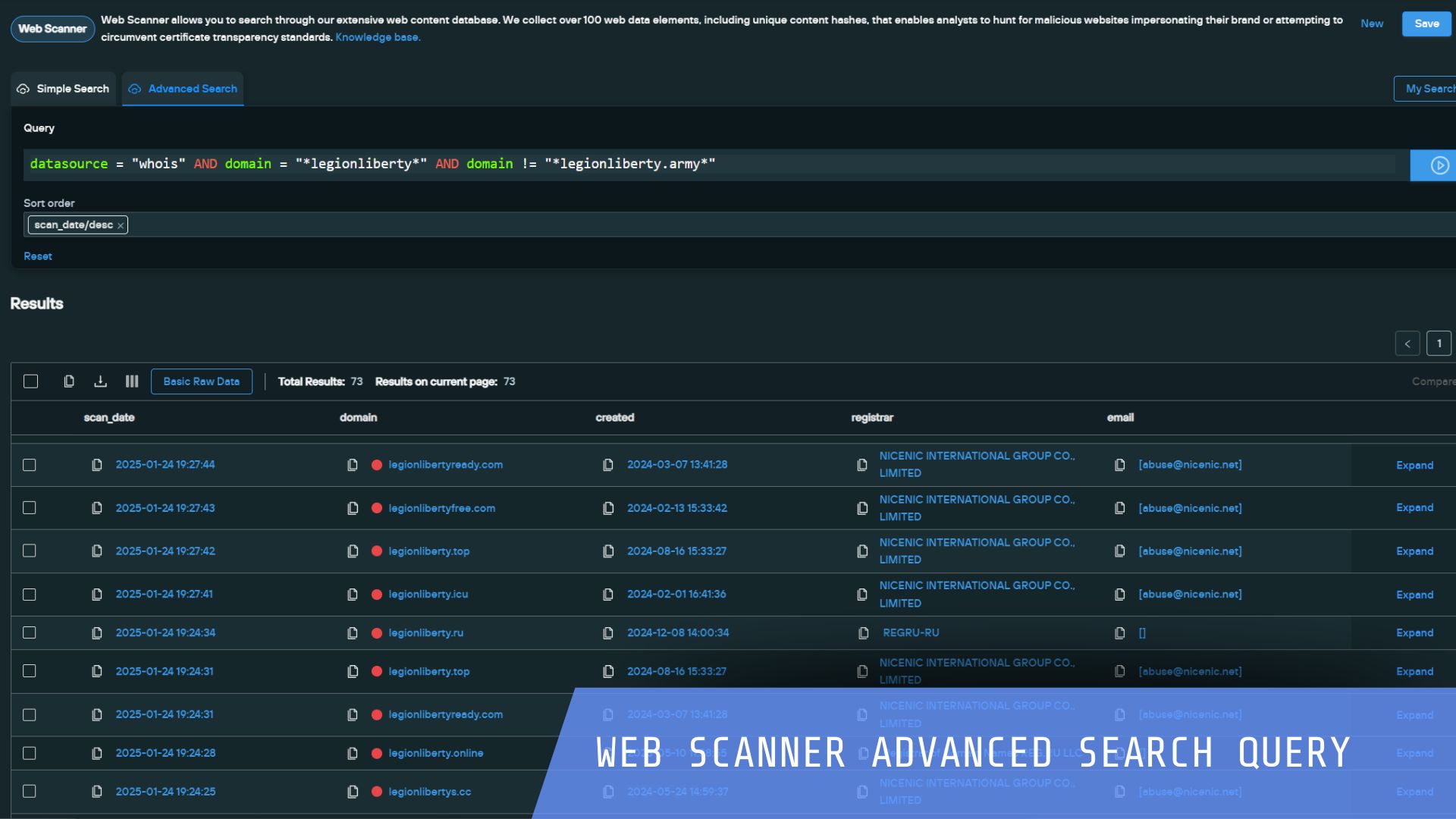
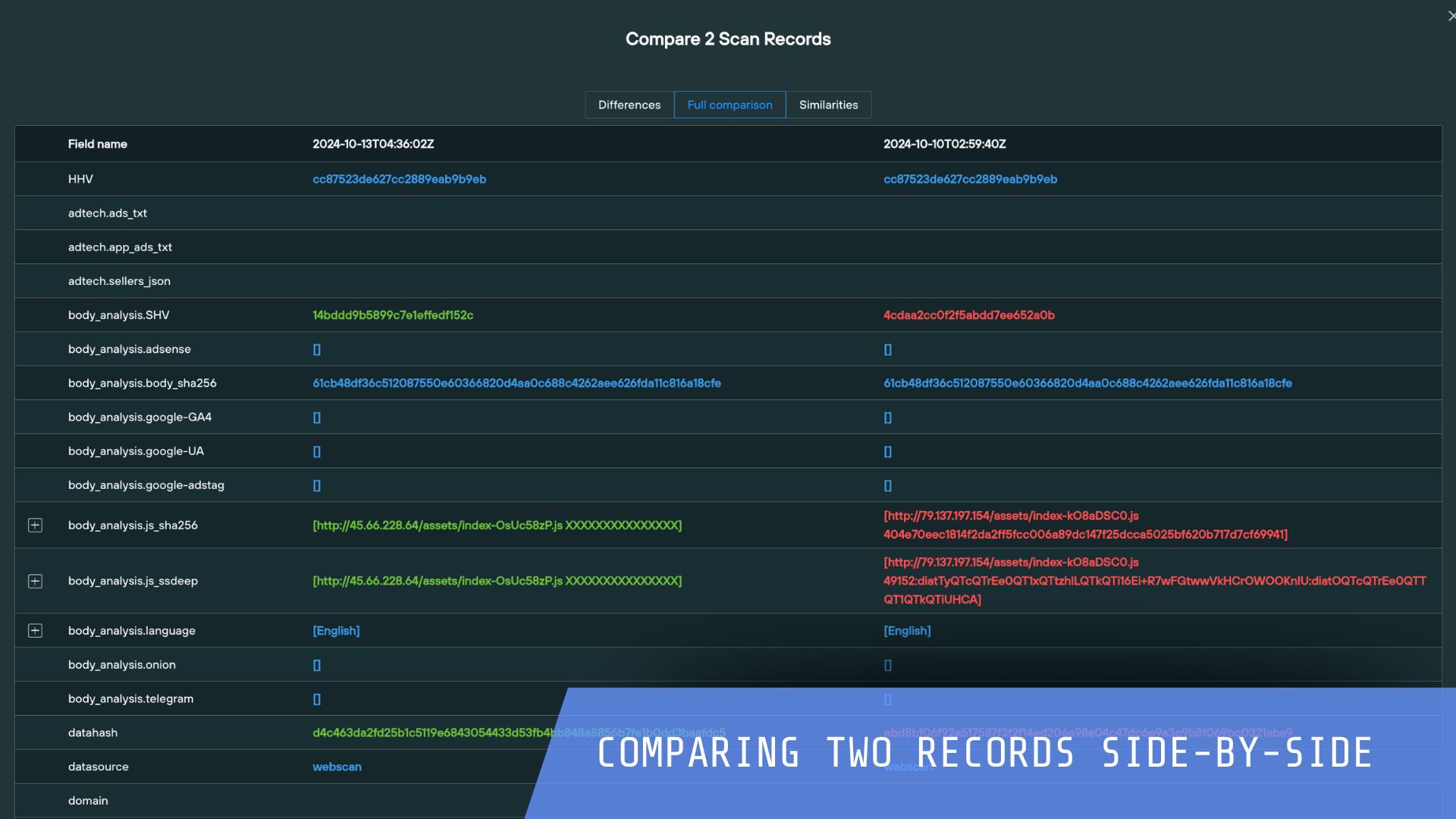
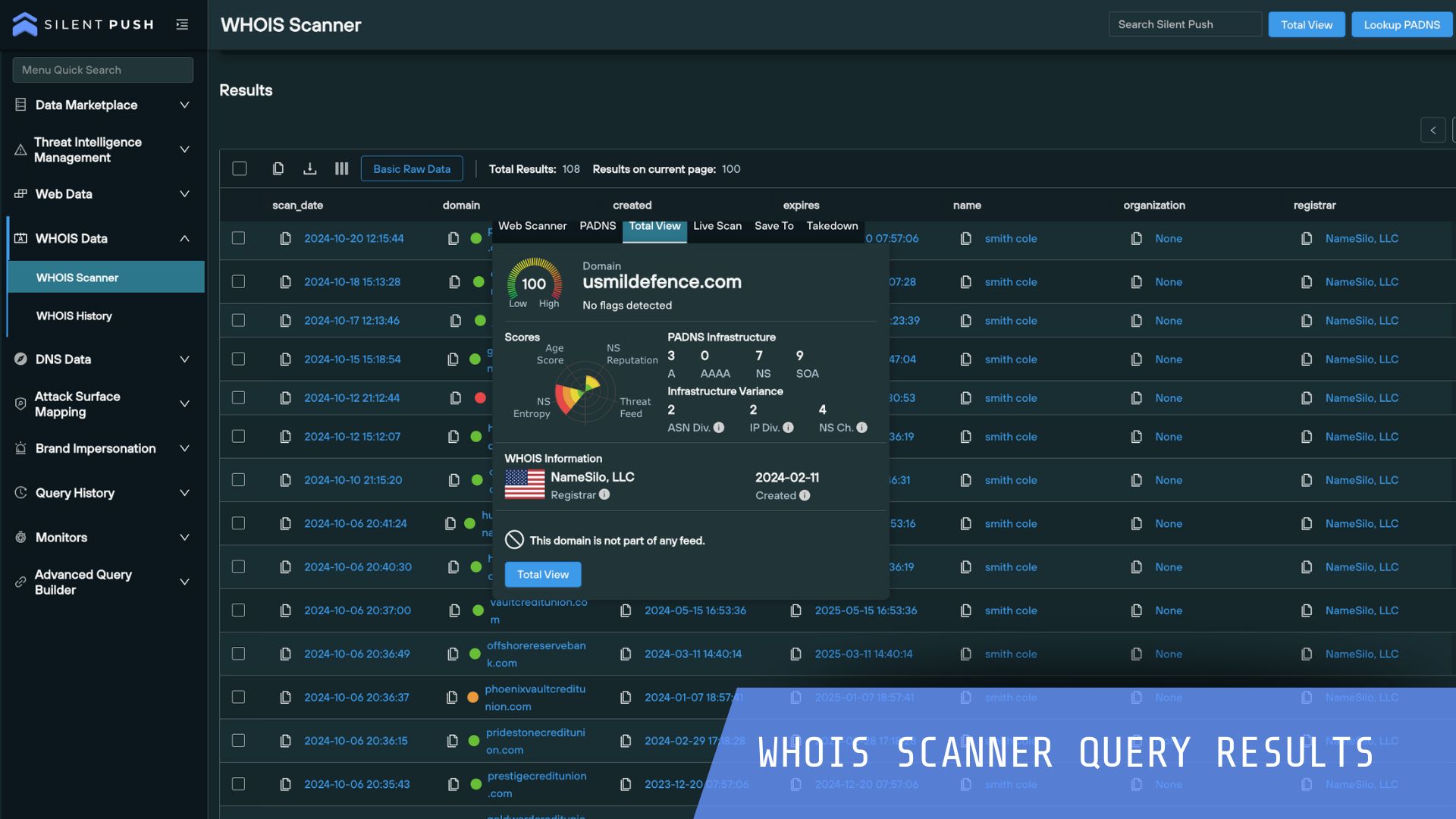
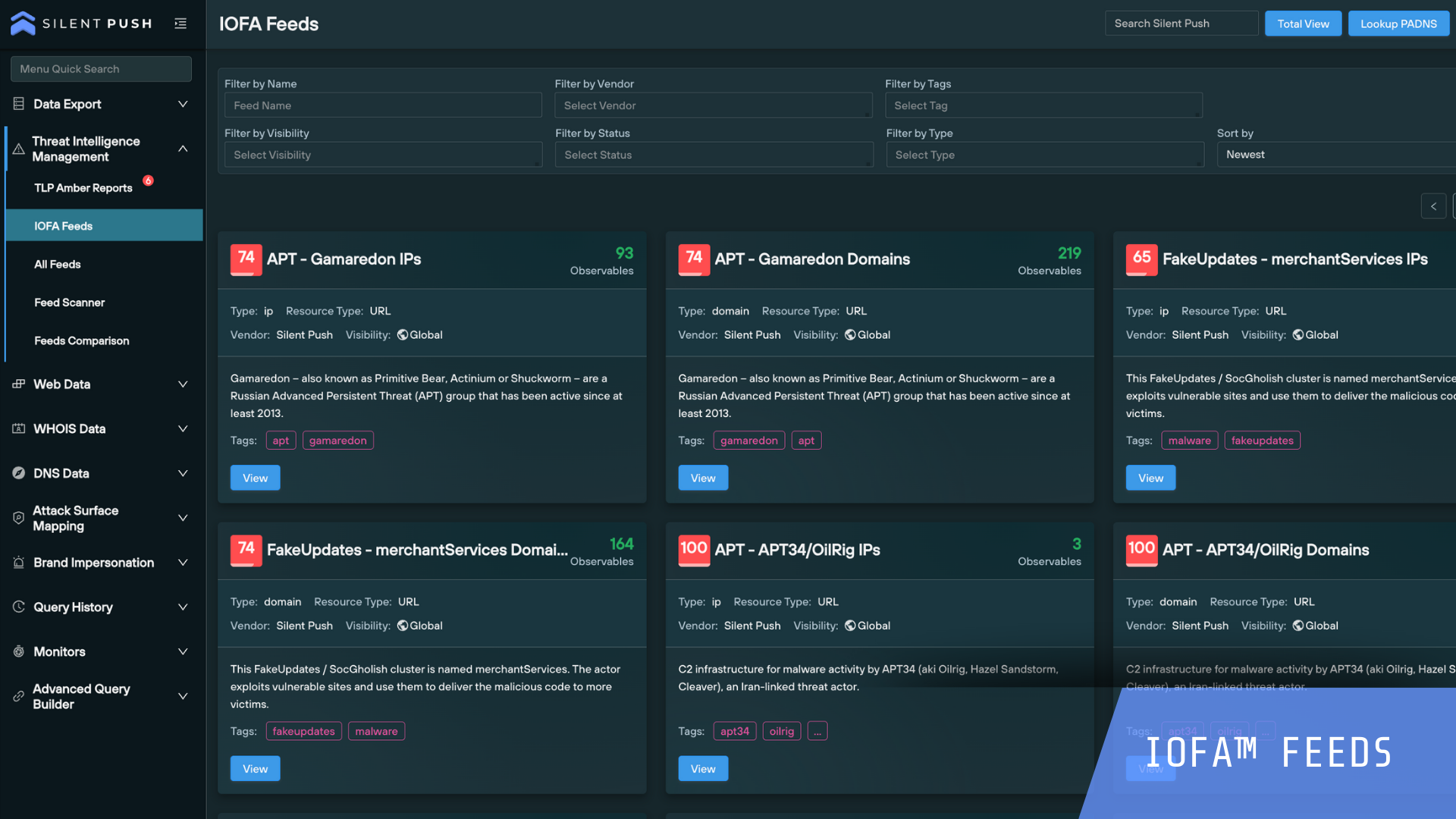
Silent Push helps you to defend against known and hidden threats and proactively block attacks quickly with Indicators of Future Attack™. Review the most common use cases security teams action to protect their organization.