Now in Splunkbase version 2 of our add-on with enrichment for Splunk Enterprise
Log analyzers such as Splunk play a key role in enterprise-level cybersecurity operations by collecting large amounts of data across multiple threat environments, but deciding what to do with reams of traffic logs from different geographic locations can often be a daunting task.
The Silent Push plugin for Splunk Enterprise allows organizations to leverage the data collection and analysis capabilities of both platforms, and correlate information to produce actionable insights that vastly improve threat awareness, and general WAN security.
Let’s delve a little deeper into the front-end functionality, and take a look at how both platforms interact with one another.
Core functionality
Before you install the plug-in from Splunkbase, you’re going to need four things to get you started:
● An active Splunk Enterprise instance.
● Your Splunk Enterprise admin credentials.
● Your Splunkbase credentials.
● A Silent Push account, and an API key.
So, what does the plug-in actually do? On a basic level, the plug-in analyses data received by Splunk based on a group of parameters defined in Silent Push – also known as “filter profiles” – which is then stored within Splunk in a series of parameter-specific data dumps known as “indexes”.
The plug-in contextualizes suspect data as an “observable” (otherwise known as an IoC, or “indicator of compromise”), and aggregates a threat score based upon individual parameters within the observable.
Once the data has been collected, users are able to perform adaptive responses that trigger further actions within Splunk Enterprise, providing an end-to-end threat detection and management service.
Users are able to automatically correlate data between Splunk and Silent Push in the form of “notables”, that can be visually displayed in custom dashboards from within Splunk Enterprise.
Data enrichment and enhanced threat scoring
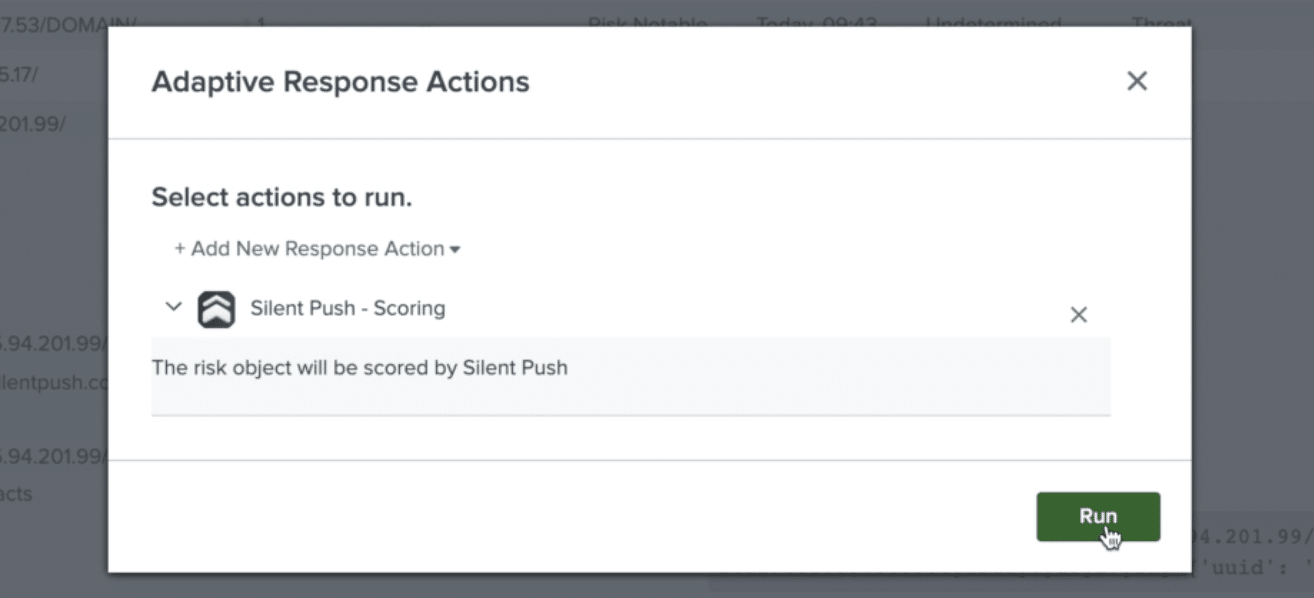
When dealing with large amounts of data, visualization is key. Plug-in users are able to create custom search objects that query indexes for observables based on data reputation, severity, threat urgency and geographic location – all gathered from Silent Push.
Once Silent Push has provided additional context, and the data has been refined to a set of variables, users are able to mine indexes and perform two key actions (alongside standard actions such as NS lookups and ping), courtesy of the plug-in:
- Enriching – Risk objects are subject to granular analysis by Silent Push, which outputs all manner of enriched data not previously displayed by Splunk Enterprise. This is where the plug-in comes into its own and goes over and above what is expected of an industry-standard log analyzer.
- Scoring – The plug-in re-scores the risk object via a tailored algorithm. In order to prevent unnecessary actions, this only occurs when an object’s risk score is lower than the proposed Silent Push risk score.
Data enrichment is a key part of Silent Push’s offering, and contains a whole host of additional data, including granular ASN analysis, threat rankings, reputational data, subnet info and a lot more. Once the data has been enriched and scored, it’s passed through to an index within Splunk for further analysis, and for the user to do with it as they please.
Sticking with the trend of integration, data enrichment and scoring can be performed from within Splunk Enterprise’s Incident Review dashboard – a central hub for IM-related activities – and can either be carried out manually, or scheduled as a recurring task.
Key benefits
The Silent Push plug-in satisfies a pressing need for enterprise organizations to harness the power of multiple detection and analysis platforms to enhance their WAN security operation, without any added subscription costs or costly manual interventions.
In the global threat detection sphere, context is king. Physical and logical resources are at an all time high, and it’s simply not enough for threat analysts to be provided with vast amounts of data, without the facility to drill down into specific variables that enable organizations to tailor their cybersecurity operation to unique threat environments.
Take a closer look
To find out more about the Silent Push Splunk Enterprise plug-in, visit the info page on Splunkbase or take an in-depth look at its functionality in the accompanying knowledge base article.



